 Mise en place dun pot de miel dans un réseau Wi-Fi
Mise en place dun pot de miel dans un réseau Wi-Fi
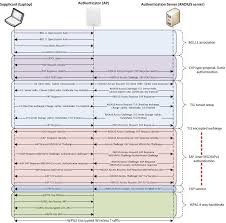
Le honeypot va imiter le fonctionnement d'un programme ou service informatique. http://www.securinets.com/sites/default/files/fichiers_pdf/Honeypot ...
 Mise en place dun pot de miel dans un réseau Wi-Fi
Mise en place dun pot de miel dans un réseau Wi-Fi
L'informatique et Internet sont toujours en grande expansion dans notre société. http://www.securinets.com/sites/default/files/fichiers_pdf/Honeypot% ...
 Chapitre I : Concepts généraux sur les réseaux de capteurs sans fil
Chapitre I : Concepts généraux sur les réseaux de capteurs sans fil
3 juil. 2013 Pour l'obtention du diplôme de Master en Informatique ... avec un Honeypot SECURIDAY 2009 SECURINETS Atelier
[PDF] honeywell ct50 - Anciens Et Réunions
[PDF] honeywell dolphin 75e
[PDF] Honfleur - Bilbomag.fr
[PDF] HONFLEUR - Festival Normandie Impressionniste - Conception
[PDF] Honfleur Le Clos joli, manoir du Parc, domaine de la Michelière - Anciens Et Réunions
[PDF] HONFLEUR. Serge Labégorre à la galerie Bourdette
[PDF] HONG KONG - Décalage Horaire - Un Hôtel
[PDF] Hong Kong - DooDooTravel - Anciens Et Réunions
[PDF] Hong Kong - Islamic Tourism Magazine
[PDF] Hong Kong : un miracle économique qui se poursuit - Énergie Renouvelable
[PDF] Hong Kong et Macau - Anciens Et Réunions
[PDF] HONG KONG EXPRESS, Mme Pui Wah LAU, mise à l`enquête
[PDF] Hong Kong House
[PDF] Hong Kong SAR de la Rpublique populaire de Chine
