 Short Type Questions and Answers on COMPUTER NETWORKING
Short Type Questions and Answers on COMPUTER NETWORKING
COMPUTER NETWORKING. SHORT TYPE QUESTION AND ANSWERS. Prepared by Dr.Subhendu Kumar Rath Dy. Registrar
 2007 END-YEAR COMP306 COMPUTER NETWORKS Time
2007 END-YEAR COMP306 COMPUTER NETWORKS Time
The examination contains 5 questions you must answer all questions. Question 1 is worth 40 marks. The other four questions are worth 30 marks each. The exam
 important questions and answers - subject: computer networks
important questions and answers - subject: computer networks
Also discuss various advantages and disadvantages of each topology. Answer:- ''Computer network'' to mean a collection of autonomous computers interconnected by
 Questions and answers 1 Interact with Information Technology 1
Questions and answers 1 Interact with Information Technology 1
• using a computer to provide students with immediate exam feedback which helps them to focus on and correct incorrect answers while the information is.
 Multiple Choice Questions of Computer Networking
Multiple Choice Questions of Computer Networking
This set of Computer Networks Questions & Answers focuses on “Physical Media”. 1) Which of this is not a guided media ? a) Fiber optical cable b) Coaxial cable.
 Name______________ Student ID___________________
Name______________ Student ID___________________
Jan 10 2013 Introduction to Computer Networks ... You are not allowed to have any oral
 MOCK EXAMINATION Computer Networks
MOCK EXAMINATION Computer Networks
most appropriate answer by placing a tick in the appropriate box. 2. The exam mark is based on the overall number of correctly answered questions. The more.
 VCE VET INFORMATION TECHNOLOGY (Network Administration)
VCE VET INFORMATION TECHNOLOGY (Network Administration)
Oct 31 2003 All written responses must be in English. At the end of the examination. • Place the answer sheet for multiple-choice questions inside the front ...
 Name______________ Student ID___________________
Name______________ Student ID___________________
Jan 9 2020 Introduction to Computer Networks ... You are not allowed to have any oral
 Short Type Questions and Answers on COMPUTER NETWORKING
Short Type Questions and Answers on COMPUTER NETWORKING
COMPUTER NETWORKING. SHORT TYPE QUESTION AND ANSWERS. Prepared by Dr.Subhendu Kumar Rath Dy. Registrar
 CS6511 -COMPUTER NETWORKS QUESTION BANK TWO MARK
CS6511 -COMPUTER NETWORKS QUESTION BANK TWO MARK
protocol peers to implement the communication service. 5. What is LAN? A LAN is a common name used to describe a group of devices that share a geographic
 EXAMINATIONS — 2007 END-YEAR COMP306 COMPUTER
EXAMINATIONS — 2007 END-YEAR COMP306 COMPUTER
COMPUTER NETWORKS. Time allowed: THREE HOURS. Instructions: The examination contains 5 questions you must answer all questions. Question 1 is worth 40
 WINTER– 17 EXAMINATION Subject Name: Computer Network
WINTER– 17 EXAMINATION Subject Name: Computer Network
In some cases the assumed constant values may vary and there may be some difference in the candidate's answers and model answer. 6) In case of some questions
 Computer Science Questions and Answers UNIT-A Chapter - 1
Computer Science Questions and Answers UNIT-A Chapter - 1
Computer Science Questions and Answers. UNIT-A. Chapter - 1 Configuring a Computer. I One Mark Question and Answer. 1. Name the components of CPU.
 MOCK EXAMINATION Computer Networks
MOCK EXAMINATION Computer Networks
The exam mark is based on the overall number of correctly answered questions. The more questions you answer correctly the higher your mark incorrectly answered
 Final Exam & Answer Key TDTS04/TDTS43 (2007 - vt1) Computer
Final Exam & Answer Key TDTS04/TDTS43 (2007 - vt1) Computer
Computer Networks and Distributed Systems Check this exam for completeness. ... Read all questions very carefully and only answer the questions!
 Multiple Choice Questions of Computer Networking
Multiple Choice Questions of Computer Networking
1-2 What is a Firewall in Computer Network? A. The physical boundary of This set of Computer Networks Questions & Answers focuses on “Physical Media”.
 Networking Multiple Choice Questions And Answers (PDF) - m
Networking Multiple Choice Questions And Answers (PDF) - m
questions exam's workbook
 Solved Multiple Choice Questions on Computer networking
Solved Multiple Choice Questions on Computer networking
Which of the following TCP/IP protocols is used for transferring files form one machine to another. A) FTP. B) SNMP. C) SMTP. D) RPC. Answers: 1. C)
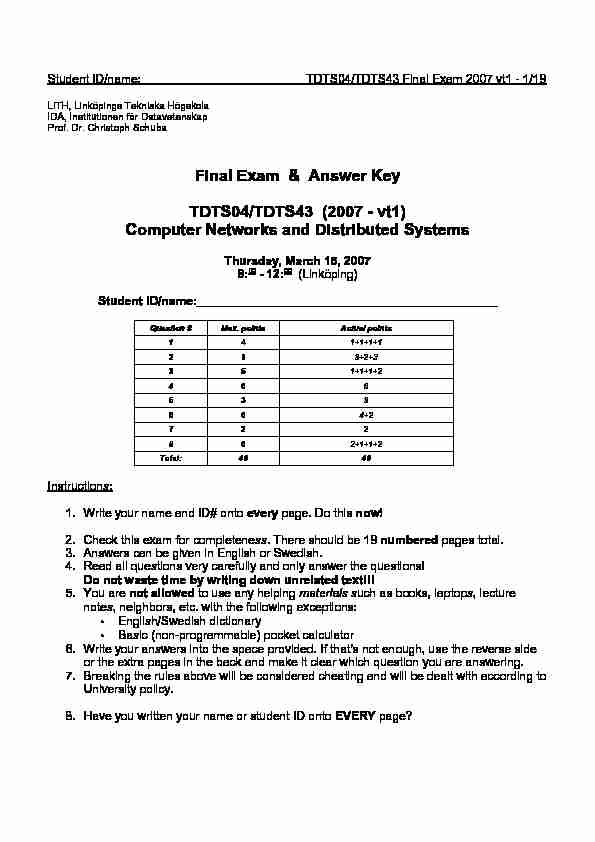 533
533664+2722
862+1+1+2Total:4040Instructions : 1.Write your name and ID# onto every page. Do this now!
2.Check this exam for completeness. There should be 19 numbered pages total.3.Answers can be given in English or Swedish.4.Read all questions very carefully and only answer the questions! Do not waste time by writing down unrelated text!!! 5.You are not allowed to use any helping materials such as books, laptops, lecture notes, neighbors, etc. with the following exceptions:•English/Swedish dictionary•Basic (non-programmable) pocket calculator6.Write your answers into the space provided. If that's not enough, use the reverse side
or the extra pages in the back and make it clear which question you are answering.7.Breaking the rules above will be considered cheating and will be dealt with according to
University policy.8.Have you written your name or student ID onto EVERY page?Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 2 / 19 1. TCP - Congestion Control (5p.)(a) Describe what TCP slow start means. (1 p.)ANSWER: When a TCP connection begins, the value of the congestion window is typically
initialized to 1 maximum segment size (MSS). Because the available bandwidth to the connection may be much larger, the TCP sender increases its rate of sending exponentially by doubling its value of the congestion window rather than increasing it linearly Once the first packet loss is detected , the congestion window is cut in half andsubsequently grows linearly. (b) When a TCP sender receives a triple duplicate ACK, its congestion window (CongWin) is
cut in half, then grows linearly. However, when a TCP sender experiences a timeout event, itemploys a new slow start. Explain the philosophy behind this different treatment of observed data loss. (1 p.)ANSWER:
Triple duplicate ACKS indicate that the network is capable of delivering at least some segments, while a timeout indicates a much more alarming congestion scenario. Therefore, the TCP sender backs off in the latter scenario much more aggressively.Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 3 / 19 (c) Explain the terms additive increase and multiplicative decrease in the context of TCP
congestion control. (1 p.)ANSWER: TCP modifies its transmission rate (i.e., window size) probing for usable bandwidth until loss occurs. In additive increase, TCP increases the CongWin by 1 MSS every RTT until loss is detected. In multiplicative decrease, TCP cuts its CongWin in half afterloss is observed. This results in a saw tooth behavior while probing for bandwidth. (d) Explain what will happen when two applications (one using TCP, the other using UDP) that
want to send as much data as possible compete for bandwidth. (1 p.)ANSWER: Because TCP adjusts to the amount of resources that are available and UDP sends as much data as possible, the TCP connection will back off, giving up almost the entire network bandwidth to the application using UDP.Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 4 / 19 2. Routing (8 p.)(a) Link State Routing (3 p.)Complete the following table, using Dijkstra's algorithm.Compute the shortest path from node A to all network nodes.Note: Possible ties must be broken in favor of the leftmost column.StepN'D(B),p(B)D(C),p(C)D(D),p(D)D(E),p(E)D(F),p(F)0A
1 2 3 4ANSWER:StepN'D(B),p(B)D(C),p(C)D(D),p(D)D(E),p(E)D(F),p(F)0A5, A5, A5, A5, A1, A1AF3, F5, A5, A3, Fdone2AFBdone4, B5, A3, F3AFBE4, B5, Adone4AFBECdone5, ABC
D E A F 1 1 222 55
5 51
Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 5 / 19 (b) Distance Vector Routing (2 p.)Consider the network shown below and assume that each node initially knows the costs to
each of its neighbors. Use the distance vector algorithm and complete the entire distancetable below as it would look like at node 2 after the algorithm has converged.Make sure to consider the Poison Reverse algorithm in your calculation!! That means some of
the entries might have the cost ∞! Distance Vector table at node 2Cost to destination node012345DistanceVector
from neighbor0 1 3 4 5 ANSWER:Distance Vector table at node 2Cost to destination node012345DistanceVector
from neighbor0012414110∞∞1∞
3∞∞∞0∞3
4112404
5∞∞∞3∞001
324 1 34
1 7 2 1 1 523
Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 6 / 19 (c) Comparison Link State and Distance Vector algorithms (3 p.)Compare the link state and distance vector algorithms with respect to the following categories.
Complete the table below.CriterionLink State AlgorithmDistance Vector AlgorithmMessage complexitySpeed of
convergenceRobustness(what happens if router malfunctions?)- Any node can advertise incorrect path cost- Each node's table is used by others. Therefore, errorspropagate through the network!ANSWER: (give ½ point for each correct entry.)CriterionLink State AlgorithmDistance Vector AlgorithmMessage complexitywith n nodes, E links: O(nE)
messages sent- exchange between neighbors only- convergence time variesSpeed of convergence- O(n2) algorithm requires O(nE)messages- may have oscillations- convergence time varies- may create routing loops- count-to-infinity problemRobustness(what happens if
router malfunctions?)- node can advertise incorrect link cost- each node computes only its own table- Any node can advertise incorrect path cost- Each node's table is used by others. Therefore, errors propagate through the network!Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 7 / 19 3. Network Address Translation and Peer-to-peer Computing (5 p.)Suppose a peer with user name Alice discovers through querying that a peer with user name
Bob has a file she wants to download. Also suppose that Bob is behind a NAT whereas Alice is not. Let 138.76.29.7 be the WAN-side address of the NAT and let 10.0.0.1 be the internal IPaddress for Bob. Assume that the NAT is not specifically configured for the P2P application.(a) Explain why Alice's peer cannot initiate a TCP connection to Bob's peer, even if Alice
knows the WAN-side address of the NAT, 138.76.29.7. (1 p.)ANSWER:Consider what happens when Alice attempts to establish a TCP connection with Bob..
Alice might send a TCP SYN packet with destination address 138.76.29.7 and some destination port number, say, x. When the NAT receives this TCP SYN packet, it doesn't know to which internal host it should direct the packet, since it doesn't have an entry for a connection initiated from the WAN side. Thus the NAT will drop the SYN packet. (b) Now suppose that Bob has established an ongoing TCP connection to another peer, Cindy, who is not behind a NAT. Also suppose that Alice learned from Cindy that Bob has thedesired file and that Alice can establish a TCP connection with Cindy.Describe how Alice can use these two TCP connections (B-C and A-C) to instruct Bob to
initiate a direct TCP connection (without passing through Cindy) back to Alice. (1 p.)ANSWER:There is an existing TCP connection between Alice and Cindy and between Cindy and
Bob. Via these two TCP connections, Alice can send a message to Bob. In particular, Alice can ask Bob to initiate a direct TCP connection from Bob to Alice. Since Bob is initiating this TCP connection, it can be established through Bob's NAT. Once this direct TCP connection is established between Alice and Bob, Alice can ask Bob to send the file over the direct TCP connection.Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 8 / 19 (c) Suppose both Alice and Bob are behind different NATs. Is it possible to devise a technique
that will allow Alice to establish a TCP connection with Bob without application-specific NAT configuration? Explain your answer. (1 p.)ANSWER: It is not possible to devise such a technique. In order to establish a direct TCP connection between Alice and Bob, either Alice or Bob must initiate a connection to the other. But the NATs covering Alice and Bob drop SYN packets arriving from the WAN side. Thus neither Alice nor Bob can initiate a TCP connection to the other if they areboth behind NATs.(d) Give at least two arguments why Network Address Translation technology is still quite
controversial, in spite of having been adopted widely. (2 p.)ANSWER:Possible answers include:•Routers should process only up to layer 3 - layer violation•NAT violates the end-to-end argument, because application designers must take
into account that NAT boxes might be in the communications path betweenparticipating applications. •IP address shortage should have been solved with IPv6 instead of NATs
Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 9 / 19 4. Link Layer (6 p.)Describe the remaining six services provided by the Link Layer. The description for Framing
serves as an example for the level of detail you are expected to provide in your answers.Link Layer ServiceDescriptionFramingAlmost all link layer protocols encapsulate each network-layer
datagram within a link-layer frame before transmission over the link.A frame consists of a data field, in which the network-layer datagram is inserted, and a number of header or trailer fields.The structure of the frame is defined by the link-layer protocol. Link access Reliable deliveryFlow control
Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 10 / 19 Link Layer ServiceDescriptionError detectionError correctionHalf-duplex and full-duplex
Student ID/name: TDTS04/TDTS43 Final Exam 2007 vt1 - 11 / 19 ANSWER: Link Layer ServiceDescriptionFramingAlmost all link layer protocols encapsulate each network-layer datagram within
a link-layer frame before transmission over the link.A frame consists of a data field, in which the network-layer datagram is
inserted, and a number of header or trailer fields. The structure of the frame isdefined by the link-layer protocol. Link access A medium access control (MAC) protocol specifies the rules by which a frame
is transmitted onto the link. For point-to-point links that have a single sender atquotesdbs_dbs7.pdfusesText_5[PDF] computer networking pdf notes
[PDF] computer networks bits pdf download
[PDF] computer networks bits with answers pdf
[PDF] computer networks book
[PDF] computer networks multiple choice questions with answers doc
[PDF] computer networks questions and answers
[PDF] computer notes in marathi free download
[PDF] computer operator and programming assistant
[PDF] computer organisation and assembly language programming notes
[PDF] computer organization and assembly language lecture notes
[PDF] computer organization and assembly language notes pdf
[PDF] computer organization and assembly language programming tutorial pdf
[PDF] computer organization and assembly language virtual university
[PDF] computer programming exam questions and answers
