 Penetration-Testing-Guidance-v1_1.pdf
Penetration-Testing-Guidance-v1_1.pdf
To confirm that the applicable controls required by PCI DSS—such as scope vulnerability management
 european cybersecurity skills framework (ecsf)
european cybersecurity skills framework (ecsf)
This framework is the result of the expert opinion and agreement in the Ad • Penetration testing standards methodologies and frameworks. • Penetration ...
 Joint Advice of the European Supervisory Authorities
Joint Advice of the European Supervisory Authorities
Apr 10 2019 resilience testing framework is a coordinated threat led penetration testing framework in the. EU. This understanding takes into account that ...
 Threat Lead Penetration Testing: TIBER-EU framework
Threat Lead Penetration Testing: TIBER-EU framework
Your own testing cookbook for free: TIBER-EU framework (May 2018). Threat Lead Penetration Testing: TIBER-EU framework. ECB UNRESTRICTED. If the proof of the
 TIBER-EU FRAMEWORK – How to implement the European
TIBER-EU FRAMEWORK – How to implement the European
2.5. Why intelligence-led red team testing? Penetration tests have provided a detailed and useful assessment of technical and configuration vulnerabilities
 CBEST Threat Intelligence-Led Assessments - January 2021
CBEST Threat Intelligence-Led Assessments - January 2021
Dealing with cyber risk is an important element of operational resilience and the CBEST framework is intelligence-led penetration testing which aims to address
 Testing Guide
Testing Guide
Framework. Overview. Phase 1: Before Development Begins. Phase 2: During ... pen-test/2003/May/74. • http://www.techonthenet.com/access/functions/index_.
 Penetration Testing Frameworks and methodologies: A comparison
Penetration Testing Frameworks and methodologies: A comparison
Several pen testing methodologies and frameworks widely available in particular include: Open Source Security Testing Methodology. Manual (OSSTMM) Information
 A guide for running an effective Penetration Testing programme
A guide for running an effective Penetration Testing programme
Some of the principle sources of material reviewed included: • The Open Source Security Testing Methodology Manual (OSSTMM) from. The Institute for Security and
 Buyers Guide Cyber Security Penetration Testing Services Framework
Buyers Guide Cyber Security Penetration Testing Services Framework
This Framework has been set up in order to streamline the process for police forces and other agencies of procuring Pen Test suppliers for their.
 Technical guide to information security testing and assessment
Technical guide to information security testing and assessment
security controls outlined in NIST SP 800-53.3 Another widely used assessment methodology is the. Open Source Security Testing Methodology Manual (OSSTMM).4
 OSSTMM 3 – The Open Source Security Testing Methodology Manual
OSSTMM 3 – The Open Source Security Testing Methodology Manual
Dec 14 2010 This is a methodology to test the operational security of physical locations
 Joint Advice of the European Supervisory Authorities
Joint Advice of the European Supervisory Authorities
Apr 10 2019 cyber resilience testing framework may vary both between and within sectors
 CBEST Threat Intelligence-Led Assessments - January 2021
CBEST Threat Intelligence-Led Assessments - January 2021
Dealing with cyber risk is an important element of operational resilience and the CBEST framework is intelligence-led penetration testing which aims to address
 Selection of penetration testing methodologies: A comparison and
Selection of penetration testing methodologies: A comparison and
Several pentesting methodologies and frameworks widely available in particular include: Open Source Security Testing Methodology Manual (OSSTMM). Information
 Penetration Testing Frameworks and methodologies: A comparison
Penetration Testing Frameworks and methodologies: A comparison
In addition two frameworks OWASP's Testing Guide and. Information System Security Assessment Framework (ISSAF)
 Evil-Twin Framework - A Wi-Fi intrusion testing framework for
Evil-Twin Framework - A Wi-Fi intrusion testing framework for
Keywords: Wi-Fi security
 Penetration Testing Guidance - PCI Security Standards Council
Penetration Testing Guidance - PCI Security Standards Council
There are three types of penetration tests: black-box white-box and grey-box In a black-box assessment the client provides no information prior to the start of testing In a white-box assessment the entity may provide the penetration tester with full and complete details of the network and applications
 IT Security Procedural Guide: Conducting Penetration Test
IT Security Procedural Guide: Conducting Penetration Test
A penetration test can be performed with or without knowledge of the system and involves the execution of a scenario and abuse cases that focus on violating technical administrative and management controls to gain access to the system or data
 OWASP Web Application Penetration Checklist - OWASP Foundation
OWASP Web Application Penetration Checklist - OWASP Foundation
The penetration test starts by gathering all possible information available regarding the infrastructure and applications involved This stage is paramount as without a solid understanding of the underlying technology involved sections may be missed during the testing phase The test should follow all the different phases described below
 Penetration Testing Guidance - PCI Security Standards
Penetration Testing Guidance - PCI Security Standards
The Penetration Testing Execution Standard Documentation Release 1 1 As the standard does not provide any technical guidelines as far as how to execute an actual pentest we have also created a technical guide to accompany the standard itself The technical gude can be reached via the link below: • PTES Technical Guidelines
 The OWASP Testing Project
The OWASP Testing Project
The OWASP testing framework explained Part 2 (due for release Q2 of 2005 covers how to test each software development life cycle phase using techniques described in this document For example Part 2 covers how to test for specific vulnerabilities such as SQL Injection by code inspection and penetration testing Scope of this Document
 le d-ib td-hu va-top mxw-100p>Actionable Penetration Testing - Penetration Testing Services
le d-ib td-hu va-top mxw-100p>Actionable Penetration Testing - Penetration Testing Services
Common Vulnerability Scoring System (CVSS): Provides an open framework for communicating the characteristics and impacts of IT vulnerabilities 1 4 Navigating this Document This document is organized in such a way to help the reader better understand penetration testing in a holistic sense
What are the different types of penetration tests?
- There are three types of penetration tests: black-box, white-box, and grey-box. In a black-box assessment, the client provides no information prior to the start of testing.
What are the goals of penetration testing?
- 2 Penetration Testing Components The goals of penetration testing are: 1. To determine whether and how a malicious user can gain unauthorized access to assets that affect the fundamental security of the system, files, logs and/or cardholder data. 2.
What is the scope of penetration testing guidance?
- Penetration Testing Guidance• March 2015 for its security, the DNS server was included in the scope of the test to determine whether an attacker could compromise the server and redirect traffic intended for the Client’s sites to a malicious intermediary or fraudulent site.
Does penetration testing help identify operational and management vulnerabilities?
- Risk Management Guide for Information Technology Systems, NIST 800-30 1describes vulnerabilities in operational, technical and management categories. Penetration testing alone does not really help identify operational and management vulnerabilities.
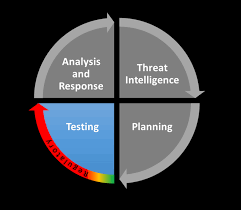 A Framework for the Regulatory use of Penetration Testing in the
A Framework for the Regulatory use of Penetration Testing in the