|
Lecture 14 141 A Method for Obtaining Digital Signatures and
This paper describes public key cryptography and presents a method for implementing privacy and account- ability More specifically the authors use the |
|
A Method for Obtaining Digital Signatures and Public-Key
An electronic checking system could be based on a signature system such as the above It is easy to imagine an encryption device in your home terminal allowing |
What is the process of digital signature?
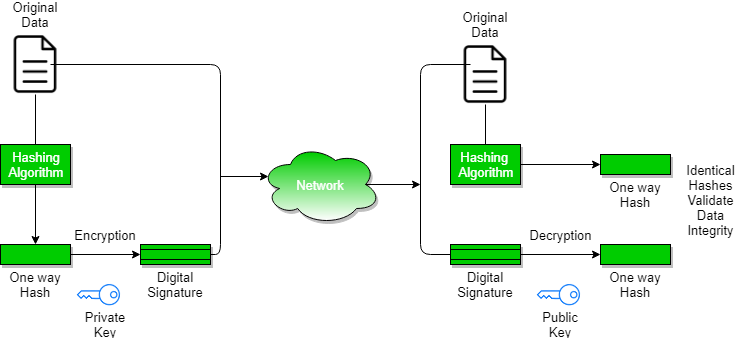
Digital signatures work by proving that a digital message or document was not modified—intentionally or unintentionally—from the time it was signed.
Digital signatures do this by generating a unique hash of the message or document and encrypting it using the sender's private key.What are the techniques of digital signature?
Digital signatures rely on asymmetric cryptography, also known as public key cryptography.
An asymmetric key consists of a public/private key pair.
The private key is used to create a signature, and the corresponding public key is used to verify the signature.There are two possibilities, sign-then-encrypt and encrypt-then-sign.
The receiver after receiving the encrypted data and signature on it, first verifies the signature using sender's public key.
After ensuring the validity of the signature, he then retrieves the data through decryption using his private key.
What are the three types of digital signatures?
What are the three different types of electronic signatures?
Simple electronic signatures (SES) SES is the easiest type of e-signature to manage, but it's also the one that provides the least validation overall. Advanced electronic signatures (AES) Qualified electronic signatures (QES)|
A Method for Obtaining Digital Signatures and Public-Key
A Method for Obtaining Digital. Signatures and Public-Key Cryptosystems. R.L. Rivest A. Shamir |
|
A Method for Obtaining Digital Signatures and Public-Key
A Method for Obtaining Digital. Signatures and Public-Key Cryptosystems. R.L. Rivest A. Shamir |
|
A method for obtaining digital signatures and public-key cryptosystems
Key Words and Phrases: digital signatures public- key cryptosystems |
|
A Method for Obtaining Digital Signatures and Public-Key
Key Words and Phrases: digital signatures public-key cryptosystems |
|
A Method for Obtaining Digital Signatures and Public- Key
A Method for Obtaining. Digital Signatures and Public-. Key Cryptosystems. R. L. Rivest A. Shamir |
|
A method for obtaining digital signatures and public-key cryptosystems
~_. ~ & ~a ! . ~. ~. A ~ a. ~ . -~ = ~ - : ~: o. = ' ~ " ~ ' . . ~ -. ~. -=."2". ~ . t . ~ ~a. ~ a |
|
Lecture 14 14.1 A Method for Obtaining Digital Signatures and
14.1 A Method for Obtaining Digital Signatures and Public-Key and use this to implement a new encryption and signing method that can be used for secure ... |
|
A Method for Obtaining Digital Signatures and Public-Key
Key Words and Phrases: digital signatures public-key cryptosystems |
|
A Method for Obtaining Digital Signatures and Public-Key
A Method for Obtaining Digital. Signatures and Public-Key Cryptosystems. R.L. Rivest A. Shamir |
|
New Method for Obtaining Digital Signature Certificate using
New Method for Obtaining Digital Signature Certificate using Proposed RSA Algorithm. Arvind Negi presents proposed scheme of digital signature algorithm. |
|
A Method for Obtaining Digital Signatures and Public-Key
The general method, under control of the key, enciphers a message M to obtain the enciphered form of the message, called the ciphertext C Everyone can use the same general method; the security of a given procedure will rest on the security of the key Revealing an encryption algorithm then means revealing the key |
|
A Method for Obtaining Digital Signatures and Public-Key - DTIC
3 avr 2020 · A Method for Obtaining Digital Signatures and Public-Key An encryption (or decryption) procedure typically consists of a ЖАИАz ╞ ╟А ╚╩ |
|
Lecture 14 141 A Method for Obtaining Digital Signatures and
14 1 A Method for Obtaining Digital Signatures and Public-Key Cryptosystems This paper describes public key cryptography and presents a method for |
|
Data Encryption and Authetication Using Public Key Approach
cryptography can be used with the shared key cryptography to get the best of Algorithm Encryption/Decryption Digital Signature Key Exchange RSA Y Y Y |
|
Digital Signature Standard (DSS) - NIST Technical Series Publications
Only the user that possesses the private key can perform signature generation A hash function is used in the signature generation process to obtain a condensed |
|
Digital Signatures with Public Key Cryptography
general, the security of symmetric encryption methods is based on keeping the employ digital signatures that are created with public key cryptography using the sender's public key, obtained with information from the sender's certificate |
|
The Exact Security of Digital Signatures- How to Sign with - CORE
It is called a hash oracle and it is accessed via oracle queries: an algorithm can write a stxirig z and get back h(z) in time 12) SECURITY OF SIGNATURE |
|
How to Obtain and Use a Digital Signature - FDOT
➢How to Obtain an ACES Digital Signature through IdenTrust Finalize the Application Process for your Personalized Certification • The Forms that you |
|
How to sign digital streams
are message oriented and require the receiver to process the entire message before being able to Therefore it is infeasible for the receiver to obtain the entire Digital Signatures (see [5, 17]) are the cryptographic answer to the problem of |
|
[PDF] A Method for Obtaining Digital Signatures and Public - People - MIT
A Method for Obtaining Digital Signatures and Public Key Cryptosystems RL Rivest, A Shamir, and L Adleman ∗ Abstract An encryption method is |
|
[PDF] A Method for Obtaining Digital Signatures and Public-Key
The general method, under control of the key, enciphers a message M to obtain the enciphered form of the message, called the ciphertext C Everyone can use the same general method; the security of a given procedure will rest on the security of the key Revealing an encryption algorithm then means revealing the key |
|
[PDF] A Method for Obtaining Digital Signatures and Public-Key
A Method for Obtaining Digital Signatures and Public Key Cryptosystems RL Rivest, A Shamir, and L Adleman* Abstract An encryption method is presented |
|
[PDF] A Method for Obtaining Digital Signatures and Public-Key - dticmil
Apr 3, 2020 · A Method for Obtaining Digital Signatures and Public Key Cryptosystems 5a CONTRACT NUMBER 5b GRANT NUMBER 5c PROGRAM |
|
[PDF] Lecture 14 141 A Method for Obtaining Digital Signatures and
More specifically, the authors use the Diffie and Hellman's concepts of public key crypto systems and use this to implement a new encryption and signing method |
|
[PDF] A Method for Obtaining Digital Signatures and Public-Key - ijoart
IJOART A Method for Obtaining Digital Signatures and Public Key Cryptosystems Using Pell's Equation with Jacobi Symbol 1M Kondala Rao, 2P S Avadhani, |
|
[PDF] Digital signatures with RSA and other public-key - Faculty
ALGORITHM 1 Davida's method for obtaining C a mod n = M 1 Factor C into t > 1 components, obtaining |
|
[PDF] A Matricial Public Key Cryptosystem with Digital Signature
to the owner of the key or to verify digital signatures encryption scheme and a digital signature scheme Finally Method for Obtaining Digital Signatures and |
|
[PDF] SplitKey – A Threshold Cryptography Case Study - NIST Computer
Mar 13, 2019 · Software based 2 out of 2 threshold cryptosystem Based on Rivest, R, Shamir, A, Adleman, L A method for obtaining digital signatures and |
|
A CERTIFIED DIGITAL SIGNATURE Ralph C Merkle Xerox PARC
devices1111 but currently known digital signature methods The new signature method is called a “tree signature G |
- a method for obtaining digital signatures and public-key cryptosystems bibtex
- rsa algorithm
- rsa pdf
- rsa algorithm pdf
- rsa cryptosystem pdf
- public key encryption
- how to calculate mod in rsa algorithm
- public key algorithms
- a method for obtaining and analyzing sensitivity data
- a method for obtaining digital signatures
- a method for obtaining new ideas and solutions
- devise a method for obtaining customer feedback
- a novel heuristic method for obtaining s-boxes
- the method for obtaining the consolidation parameters

Validating digital signatures Adobe Acrobat
Source:https://d3i71xaburhd42.cloudfront.net/43fa769993fd8ba599aac30535ab7778779683fb/6-TableI-1.png
![PDF] A method for obtaining digital signatures and public-key PDF] A method for obtaining digital signatures and public-key](https://0.academia-photos.com/attachment_thumbnails/30452577/mini_magick20190426-19227-11qdv3w.png?1556333448)
PDF] A method for obtaining digital signatures and public-key
Source:https://0.academia-photos.com/attachment_thumbnails/30452577/mini_magick20190426-19227-11qdv3w.png?1556333448
PDF) A method for obtaining digital signatures and public-key
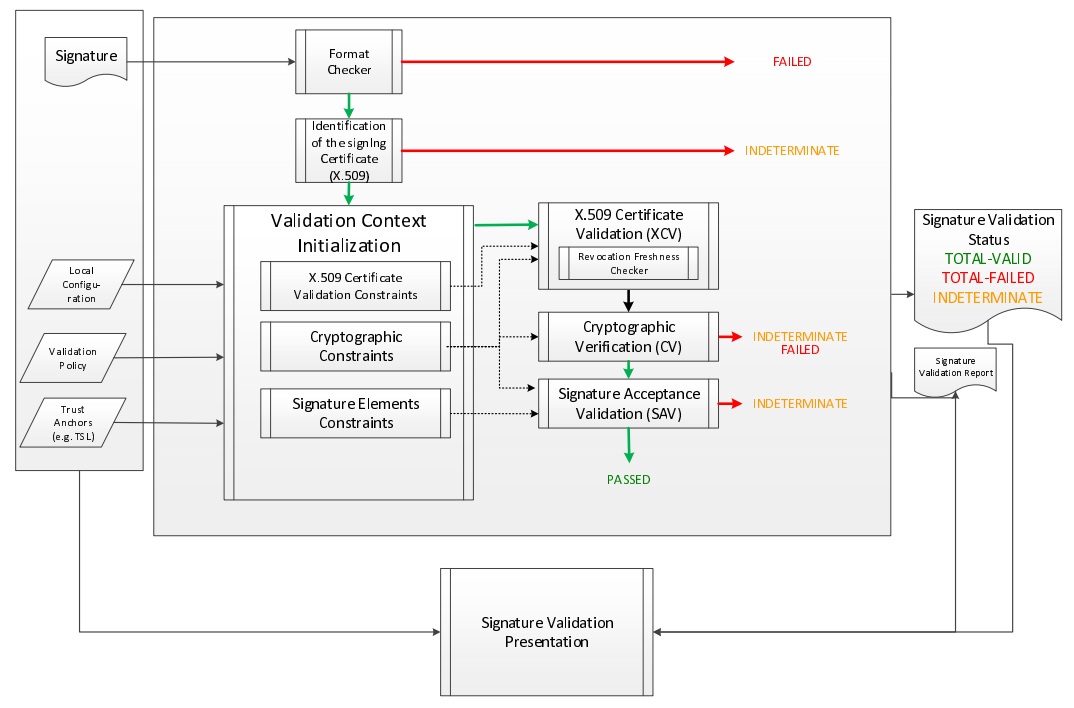
Source:https://ec.europa.eu/cefdigital/DSS/webapp-demo/doc/images/sig_validation_process.jpg

Digital Signature Service
Source:https://helpx.adobe.com/content/dam/help/en/acrobat/using/validating-digital-signatures/jcr_content/main-pars/accordion_container_946017129/accordion-par/accordion_item/accordion-item-par/procedure/proc_par/step_3/step_par/image_copy/add-trusted-certs.png
Validating digital signatures Adobe Acrobat
Source:https://media.geeksforgeeks.org/wp-content/uploads/3-56.png

Digital Signatures and Certificates - GeeksforGeeks
Source:https://thumbnails-visually.netdna-ssl.com/TheHistoryofDigitalSignatures_52fd2cb426457_w1500.jpg
a method for obtaining digital signatures and public key cryptosystems bibtex
[PDF] Review Article A Security Scheme for Dependable Key Insertion in
- military cryptography
- cryptology before computers
- data encryption
- encryption before computers
- application of cryptography in military
- ancient cryptography
- code-breaking history
- cryptography - wikipedia
- a method for obtaining and analyzing sensitivity data
- a method for obtaining digital signatures
- a method for obtaining new ideas and solutions
- devise a method for obtaining customer feedback
- a novel heuristic method for obtaining s-boxes
- the method for obtaining the consolidation parameters
a method for obtaining digital signatures and public key cryptosystems pdf
[PDF] The first ten years of public-key cryptography - Department of
- a method for obtaining digital signatures and public-key cryptosystems bibtex
- rsa algorithm
- rsa cryptosystem pdf
- rsa pdf
- public key cryptography
- rsa algorithm pdf
- public key algorithms
- public key cryptography with a cryptographic hash
- a method for obtaining and analyzing sensitivity data
- a method for obtaining digital signatures
- a method for obtaining new ideas and solutions
- devise a method for obtaining customer feedback
- a novel heuristic method for obtaining s-boxes
- the method for obtaining the consolidation parameters
a method for stochastic optimization adam
[PDF] Adaptive Methods for Nonconvex Optimization - NIPS Proceedings
- adam: a method for stochastic optimization citation
- adam: a method for stochastic optimization iclr 2015
- adam: a method for stochastic optimization iclr 2015 bibtex
- adam a method for stochastic optimization iclr citation
- adam a method for stochastic optimization google scholar
- adam a method for stochastic optimization openreview
- adam optimizer wiki
- adam optimizer keras
- a method for stochastic optimization
- a method for stochastic optimization iclr
- a method for stochastic optimization adam
- a method for stochastic optimization kingma
- a method for stochastic optimization pdf
- adam a method for stochastic optimization bibtex
- adam a method for stochastic optimization iclr
- adam a method for stochastic optimization citation
a method for stochastic optimization kingma
Effective neural network training with a new weighting - IEEE Xplore
- adam: a method for stochastic optimization iclr 2015
- adam: a method for stochastic optimization citation
- adam: a method for stochastic optimization iclr 2015 bibtex
- adam a method for stochastic optimization iclr citation
- rmsprop
- adam a method for stochastic optimization google scholar
- adam optimizer wiki
- adam a method for stochastic optimization openreview
- a method for stochastic optimization
- a method for stochastic optimization iclr
- a method for stochastic optimization adam
- a method for stochastic optimization kingma
- a method for stochastic optimization pdf
- adam a method for stochastic optimization bibtex
- adam a method for stochastic optimization iclr
- adam a method for stochastic optimization citation