public key algorithms
|
Post-quantum algorithms for digital signing in Public Key
30 juin 2017 Support for post-quantum digital signature algorithms in Public Key Infrastructure products could easily be achieved since many algorithms ... |
|
Quantum Resistant Public Key Cryptography: A Survey
E.3 [Data]: Data Encryption—Public key cryptosystems. General Terms. Algorithms Security. Keywords. Quantum computers |
|
Power Analysis for Secret Recovering and Reverse Engineering of
Reverse Engineering of Public Key Algorithms. Frederic Amiel1? |
|
Certificateless Public Key Cryptography
21 oct. 2003 Identity-based public key cryptography (ID-PKC) first proposed by Shamir [32] |
|
Efficient side-channel testing for public key algorithms: RSA case study
This paper proposes an approach to validate that implementations of public-key cryptography have moderate resistance to side-channel analysis using RSA-CRT as |
|
RFC 8709: Ed25519 and Ed448 Public Key Algorithms for the
This algorithm only supports signing and not encryption. Standard implementations of SSH implement these signature algorithms. 4. Public Key Format. The "ssh- |
|
Optimal extension fields for fast arithmetic in public-key algorithms
Arithmetic in finite fields is an integral part of many public-key algorithms including those based on the discrete logarithm problem in finite fields |
|
Applying TVLA to Public Key Cryptographic Algorithms
Applying TVLA to Public Key Cryptographic. Algorithms. Michael Tunstall and Gilbert Goodwill. Abstract. Test Vector Leakage Assessment (TVLA) has been |
|
The Complexity of Public-Key Cryptography
27 avr. 2017 We survey the computational foundations for public-key cryptography. We discuss the com- putational assumptions that have been used as bases for ... |
|
PUBLIC-KEY CRYPTOSYSTEM BASED ON ISOGENIES
public-key cryptography elliptic curve cryptosystem |
|
Recommendation for Cryptographic Key Generation - NIST
Oct 6 2016 · algorithm is a mathematical process and the key is a parameter used by that process The National Institute of Standards and Technology (NIST) has developed a wide variety of Federal Information Processing Standards (FIPS) and NIST Special Publications (SPs) to specify and approve cryptographic algorithms for by the use Federal Government |
|
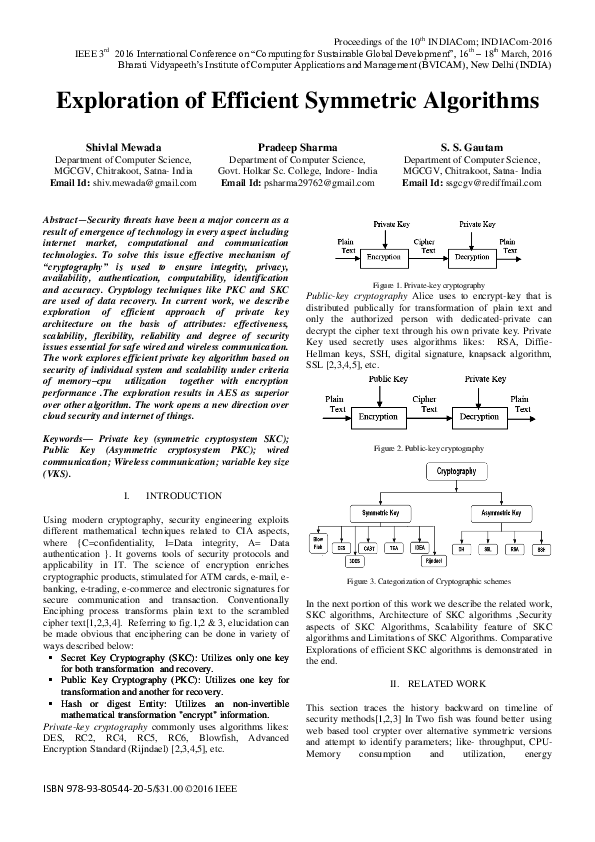
Lecture 12: Public-Key Cryptography and the RSA Algorithm
public-key algorithm IMPORTANT: Note that public-key cryptography does not make obsolete the more traditional symmetric-key cryptography Because of the greater computational overhead associated with public-key crypto systems symmetric-key systems continue to be widely used for content encryption |
|
What is a Public Key and How Does it Work? - SearchSecurity
Public key algorithms RSA: encryption and digital signature Diffie-Hellman: key exchange DSA: digital signature Elliptic curve: encryption and digital signature Number theory underlies most of public key algorithms Prime numbers The Chinese Remainder Theorem (CRT) Discrete Logarithms 2 Applications Encryption/decryption |
|
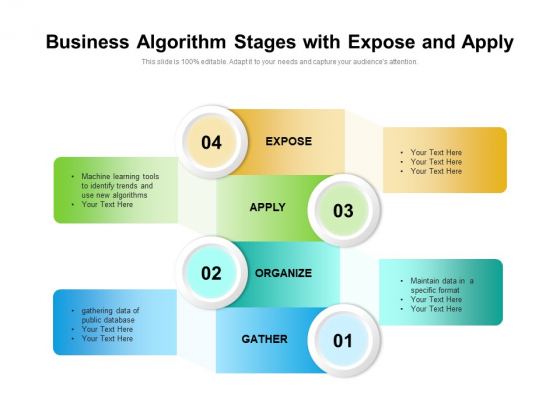
Public Key Algorithms - Department of Computer Science
RSA Algorithm Generate private and public key: choose two large primespandq about 256 n=p q(512 bits) don’t revealpandq factoring 512 bit number is hard public key:erp (n)=(p 1)(q 1)à 1 private key:d=(emo d (n)àhd; n encryption:ofm< n:c=mmo dn d decryption:m=cmo dn veri?cation:m=smo dn(signatures) bits he; n (77 digits) 8 each RSA exam |
|
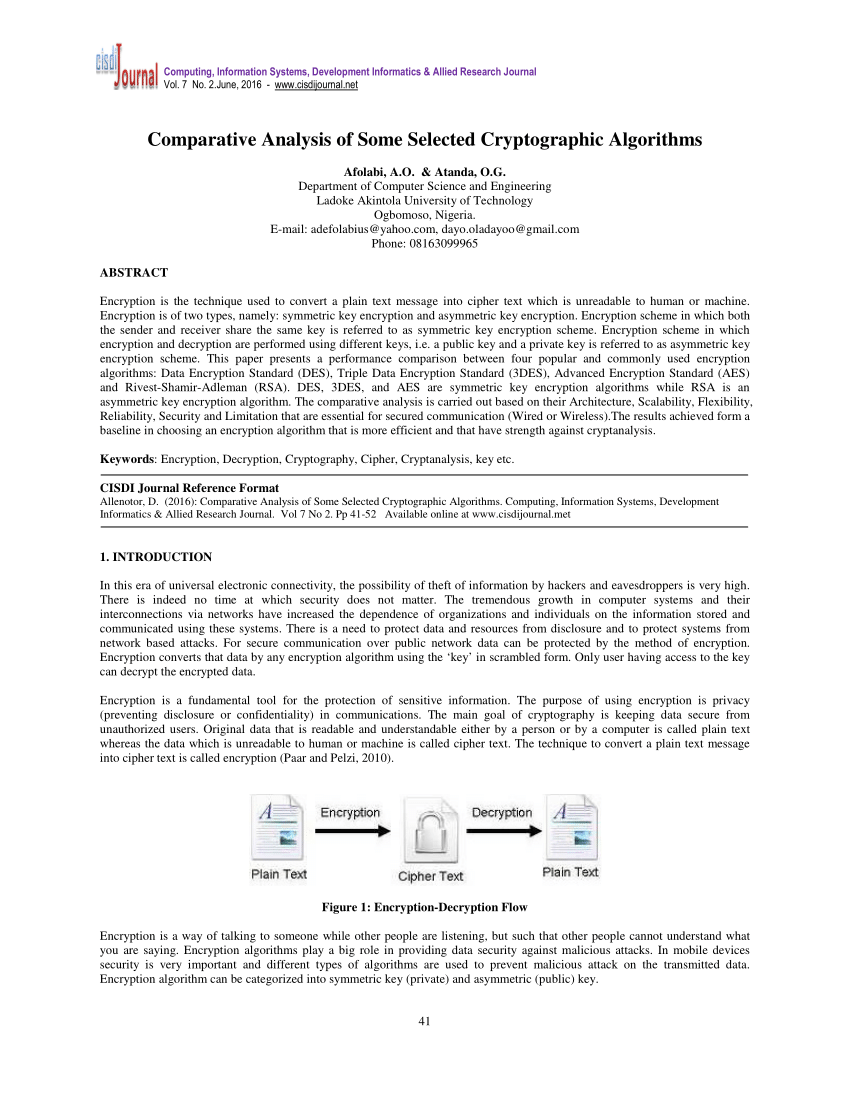
Cryptography - Stanford University
In the public-key setting Alice has a private key known only to her and a public key known to everybody including Eve; Bob too has his own private key and a public key known to everybody In this setting private and authenticated communication is possible without Alice and Bob having to meet to agree on a shared secret key |
|
Searches related to public key algorithms filetype:pdf
Sep 7 2022 · A: A CRQC if built would be capable of undermining the widely deployed public-key algorithms currently used for asymmetric key exchanges and digital signatures with potentially devastating impact |
What are the most common algorithms used to generate a public key?
- The most common algorithms used to generate public keys are Rivest-Shamir-Adleman, elliptic curve cryptography and Digital Signature Algorithm. A public key can be given to any person with whom an individual wants to communicate, whereas a private key belongs to the individual it was created for and isn't shared.
What is a public key and how does it work?
- The public key is used to encrypt messages and the private key is used to decrypt messages. The reverse is done to create a digital signature. Only the owner of the key pair knows the private key, but everyone can know the public key.
What are the challenges of public key cryptography?
- While public key encryption is more secure than symmetric encryption, there are a few risks to consider, including the following: Low-quality key. A poorly crafted asymmetric key algorithm -- one that's too short in length, for example -- is a security risk. Lost private key.
What are the benefits of public key cryptography?
- Due to Public key cryptosystem, public keys can be freely shared, allowing users an easy and convenient method for encrypting content and verifying digital signatures, and private keys can be kept secret, ensuring only the owners of the private keys can decrypt content and create digital signatures.
|
Public Key Algorithms
Public key algorithms œ RSA: encryption and digital signature œ Diffie-Hellman: key exchange œ DSA: digital signature œ Elliptic curve: encryption and digital |
|
Public Key Algorithms - Washington University in St Louis
RSA Public Key Encryption 3 Public-Key Cryptography Standards (PKCS) 4 Diffie-Hellman Key Elliptic Curve Cryptography (ECC) 7 Zero-Knowledge |
|
Public Key Algorithms I - LSU CCT - Louisiana State University
Modular arithmetic ❑ RSA ❑ Diffie-Hellman Key Exchange CSC4601 F04 Louisiana State University 9- Public Key Algorithms- 3 Private-Key Cryptography |
|
Data Encryption and Authetication Using Public Key Approach - CORE
years, RSA public key cryptography system could even potentially become obsolete First, let's take a look at the problem itself Encryption algorithms ensure |
|
1 What is a public key cryptography? - IGNTU
Unit- III Syllabi: Public key cryptography principles 1 Public key cryptography algorithms 2 digital signatures, digital Certificates 3 Certificate Authority and key |
|
Public Key Cryptography Public Key Algorithms - Computer Science
The RSA Algorithm Choosing public and private keys • Let k be the key length then choose two large prime numbers p and q of bit lengths k/2, for example 512 |
|
Data Encryption and Authetication Using Public Key Approach
Overview of Public Key Cryptography: It uses two keys, one is called Private Key and another one is called a Public key The public key encrypt the message and sent to the recipient for decryption of the message using the private key |
|
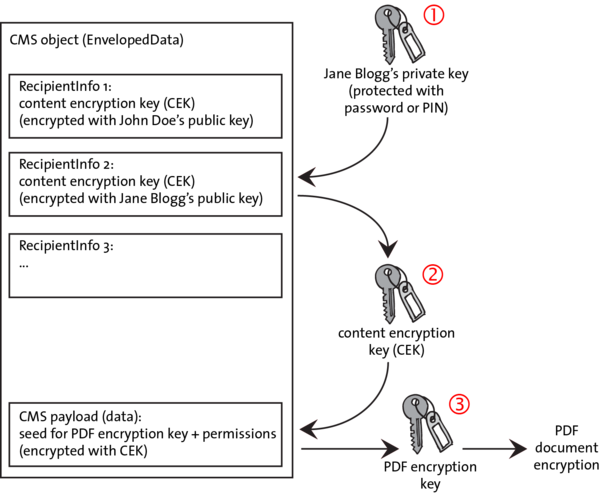
Public-Key Cryptography - NTU
(a) Encryption with public key Plaintext input Transmitted ciphertext Plaintext output Encryption algorithm (e g , RSA) Decryption algorithm Bob's private key |
|
Introduction to Public-Key Cryptography
Main Security Mechanisms of Public-Key Algorithms: Key Establishment There are protocols for establishing secret keys over an insecure channel Examples for |
























.jpg)


![PDF] Automating Open Source Intelligence: Algorithms for OSINT (Comp PDF] Automating Open Source Intelligence: Algorithms for OSINT (Comp](https://image.isu.pub/191118115718-da846d6b596797e1a391cb06f93619af/jpg/page_1.jpg)