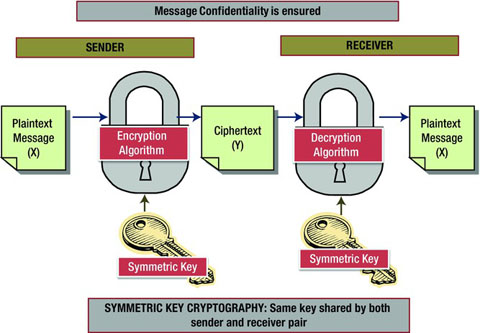
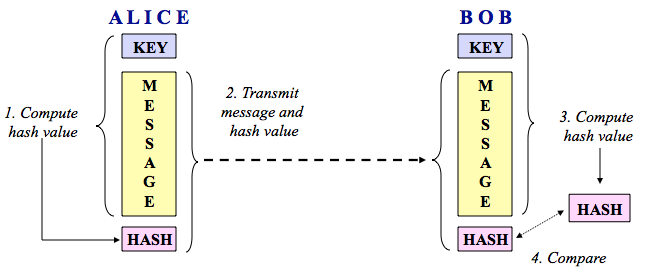
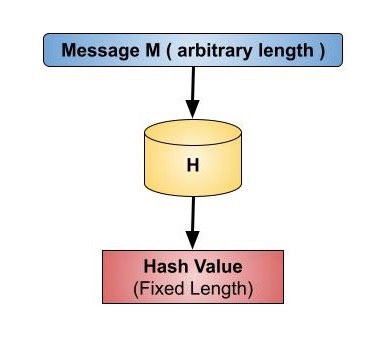
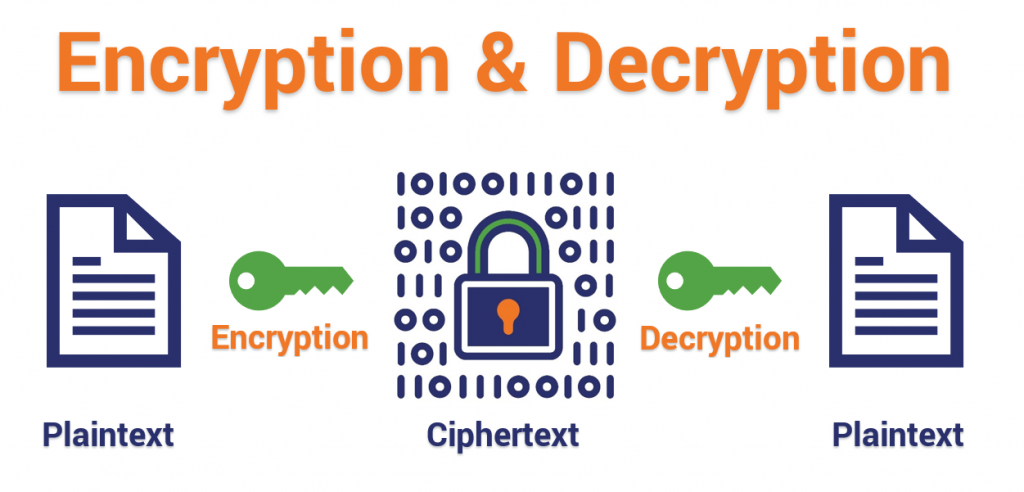
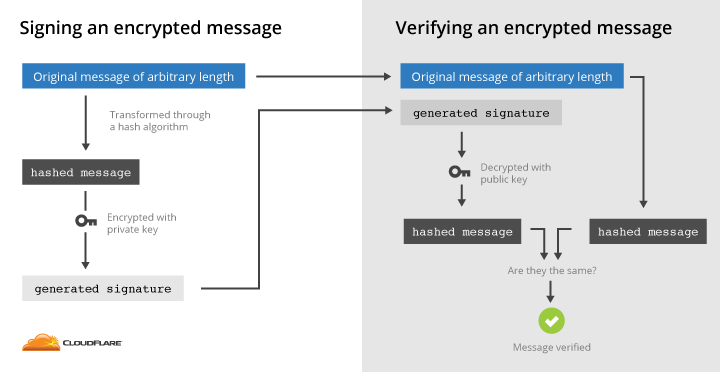
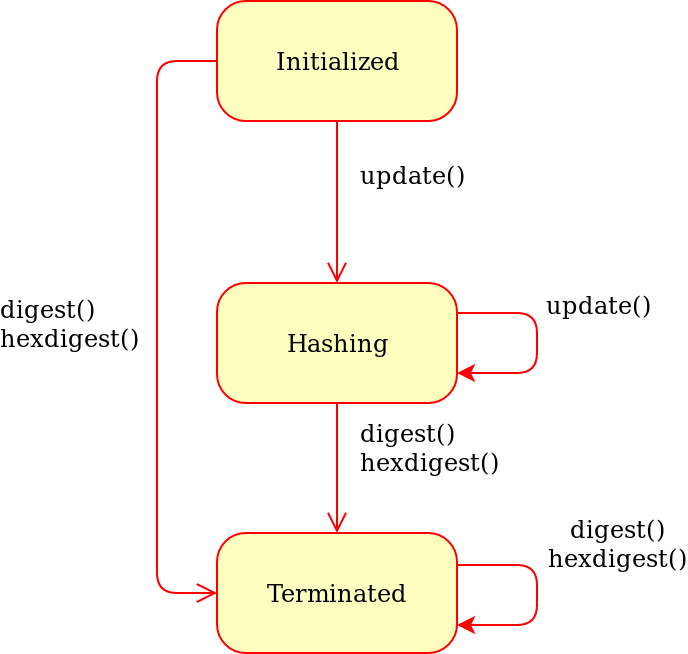
public key cryptography with a cryptographic hash
|
An220253 - using the crypto module in traveo ii family
15 fév. 2021 Digital signatures are widely used and often based on RSA and a hash function with cryptographic strength. The Public-Key Cryptography Standards ... |
|
Cryptographic hash functions and MACs Solved Exercises for
of cryptographic hash functions and message authentication codes (MAC). encryption algorithm E is a public key encryption |
|
Public Key Cryptography and Cryptographic Hashes
Public Constants: prime p integer g ? 0 |
|
Universal Hash Proofs and a Paradigm for Adaptive Chosen
12 déc. 2001 We present several new and fairly practical public-key encryption schemes and prove them secure against adaptive chosen ciphertext attack. One ... |
|
MiMC: Efficient encryption and cryptographic hashing with minimal
our proposal for both block ciphers and cryptographic hash functions is is frequently encountered in many public-key cryptographic algorithms and pro-. |
|
A Family of Fast Syndrome Based Cryptographic Hash Functions
Unlike most other public key cryptosystems the encryption function of the. McEliece cryptosystem [10] (or of Niederreiter's version [14]) is nearly as fast as |
|
Quantum Resistant Public Key Cryptography: A Survey
It derives its security strength from the irreversibility of an arbitrary one- way function f. f may be a cryptographic hash function |
|
Public key infrastructure for air traffic management systems
(under public key). OR. Cryptographic Building Blocks. Cryptographic Schemes. Hash. Function. Asymmetric. Encipherment. (under private key). AND. Encryption. |
|
Lecture 5 - Public Key Cryptography Prof. Daniel Votipka Fall 2021
Crypto. Confidentiality: Encryption and Decryption. 3. Private Key. Stream. Cipher. Block. Cipher Properties of good cryptographic hash functions:. |
|
SBU CSE508: Public Key Cryptography - Stony Brook University
Public Key Cryptography Many algorithms with different purposes One common property: pair of keys one public and one secret Session key establishment Exchange messages to create a shared secret key Encryption Anyone can encrypt a message using a recipient’s public key Only the recipient can decrypt a message using their private key |
|
Networks CH 8 Flashcards Quizlet
cryptography particularly on public-key cryptographic systems This paper also introduces adoption challenges associated with post-quantum cryptography after the standardization process is completed Planning requirements for migration to post-quantum cryptography are discussed |
|
Cryptography - Stanford University
Cryptography is the mathematical foundation on which one builds secure systems It studies ways of securely storing transmitting and processing information Understanding what cryptographic primitives can do and how they can be composed together is necessary to build secure systems but not su cient |
|
Crypto II: Public Key Cryptography - University of California
•Cryptography: secure communication over insecure communication channels •Three goals •Con?dentiality •Integrity •Authenticity •Last lecture: symmetric-key -> con?dentiality and authenticity •This lecture: HMAC for integrity public key digital signature certi?cate 3 |
|
Public-Key Cryptography Standards: PKCS - arXivorg
Public key cryptography is based on asymmetric cryptographic algorithms that use two related keys a public key and a private key; the two keys have the property that given the public key it is computationally infeasible to derive the private key A user publishes his/her public key in a public directory such as an LDAP directory and keeps |
|
Searches related to public key cryptography with a cryptographic hash filetype:pdf
An Overview of Public Key Cryptography Martin E Hellman With a public key cryptosystem the key used to encipher a message can be made public without compromising the secrecy of a different key needed to decipher that message I COMMERCIAL NEED FOR ENCRYPTION Cryptography has been of great importance to the mil- |
How does the public-key encrypted message hash provide a better digital signature?
- In what way does the public-key encrypted message hash provide a better digital signature than the public-key encrypted message? 13. A public-key signed message digest is "better" in that one need only encrypt (using the private key) a short message digest, rather than the entire message. Since public
What is a public key in cryptography?
- In a public-key cryptosystem, a public key is a key that can be used for verifying digital signatures generated using a corresponding private key. In some cryptosystems, public keys can also be used for encrypting messages so that they can only be decrypted using the corresponding private key.
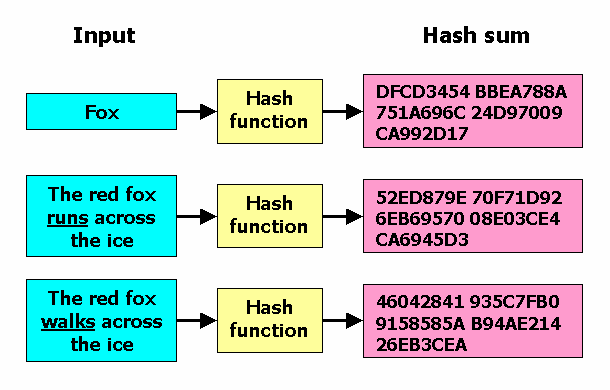
What is a cryptographic hash?
- A cryptographic hash (sometimes called 'digest') is a kind of 'signature' for a text or a data file. SHA-512 generates an almost-unique 512-bit (32-byte) signature for a text.
|
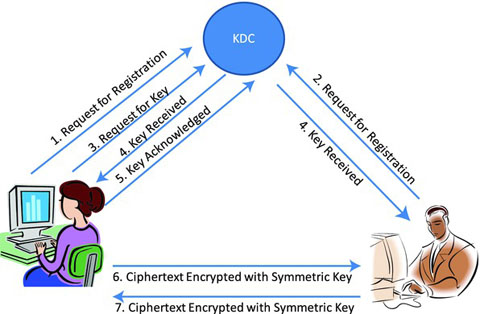
Cryptographic Tools: Shared-Key Cryptography, Hashes, and Digital
The private key cannot easily be determined from the public key o Alice can contact Bob without exchanging keys with him But public-key management is still a |
|
Cryptographic Hash Functions
A cryptographic hash function must have certain properties Why is hashing better than encryption here? Encryption: given plaintext M and public key PK, |
|
Cryptography Overview Cryptography Basic Cryptographic
Establish shared secret key using public-key cryptography ◇ Signed Transmit data using negotiated key, encryption function Cryptographic hash functions |
|
Asymmetric Cryptography Hash Functions Security - Cs Umd
Called asymmetric cryptography because different (non-symmetric) keys are needed for encryption and decryption Also called public- key cryptography |
|
Cryptography - Princeton University Computer Science
Overview • Network security and definitions • Brief introduction to cryptography – Cryptographic hash functions – Symmetric-key crypto – Public-key crypto |
|
Crypto II: Public Key Cryptography - UCR CS
Cryptogtaphic hash functions add conditions "New" cryptographic hash function SHA-3 Definition: a public-key encryption system is a triple of algorithms |
|
Public Key Encryption and Digital Public Key Encryption and Digital
Message authentication code (keyed hash functions) K is the public key, and used for encryption 3 • Public-key systems aka asymmetric crypto systems |
|
Public key encryption algorithm
Three kinds of auxiliary functions are involved in the public key encryption algorithm based on elliptic curves specified in this part: cryptographic hash functions, |
|
Cryptographic Tools
Next, we examine secure hash functions and discuss their use in message authentication The next section examines public- key encryption, also known as |
|
Public-Key Cryptography and Message Authentication
Secure Hash Functions and HMAC • Public-Key Public-Key Cryptography Algorithms Authentication Using Conventional Encryption – Only the sender and |