pwc cybersecurity report 2019
|
PwC Cyber Security
from the cyber security community. In June 2019 PwC reported on a sophisticated espionage campaign targeting ... tit-for-tat cyber attacks |
|
PwC Global Fintech Report 2019
Good cybersecurity hygiene includes a new organisation mind-set the right incentives and consequences |
|
Cyber Threats 2021: A Year in Retrospect
pwc.com/cyber-security in cybersecurity conversations with issues surrounding their ... The analysis in this report was conducted by the PwC Threat. |
|
22nd Annual Global CEO Survey - CEOs curbed confidence spells
Taken as a whole the CEO confidence story is a sobering one. Source: PwC |
|
Global Digital Trust Insights Survey 2021
PwC |
|
Global Annual Review 2022 - A Year of Solving Together
New skills. programme is a US$3 billion investment launched in 2019 and Our 25th Annual Global CEO Survey identifies cybersecurity risk as the top ... |
|
PwC Global Fintech Report 2019
Constructing a tech firewall is just the first line of defence. The second is weaving strong cybersecurity controls into the entire risk management structure. |
|
Cyberhoten mot Sverige 2019
2019 med allt fler attacker mot den egna verksamheten. Jakob Bundgaard ansvarig Cyber Security PwC Sverige ... State of Information Security Survey. |
|
The 2019 Strategy& Digital Auto Report Time to get real
The 2019 Digital Auto Report: addressing market reality. Key facts and main content. 2. ? Eighth annual Digital Auto. Report developed by. Strategy&. |
|
Global Annual Review 2022 - A Year of Solving Together
New skills. programme is a US$3 billion investment launched in 2019 and Our 25th Annual Global CEO Survey identifies cybersecurity risk as the top ... |
|
Cyber Threats 2019: A Year in Retrospect - PwC
This report intends to highlight the most prolific trends PwC observed throughout 2019 and explore their wider impact In 2019 the cyber threat landscape became increasingly complex to navigate: with the proliferation of financially motivated cyber activity intelligence operations navigating the currents of powerful |
|
EY Cybersecurity Report
www pwc com/ng July 2021 The rate at which cybercriminals are launching attacks against companies around the world is alarming These attacks are becoming more frequent such that they can no longer be ignored anymore by business owners and stakeholders Cyber criminals keep advancing with new attack strategies and different attack vectors to |
|
Our Take Navigating the Cyber pass - pwcin
1 PwC 2022 Global Risk Survey - India highlights 2 CERT-In Annual Report 2021 With cyber war becoming the asymmetric weapon of choice for all threat actors India needs to significantly up its cyber investments to create bespoke solutions to safeguard its interests |
|
Securing the Future Cybersecurity Report - pwccomau
cybersecurity-related activity In 2020 alone the industry saw a number of cybersecurity-related attacks (and near misses) which have made the building of cyber resilience and trust within the ecosystem top priorities The key cybersecurity risks and incidents identified in this research include: • Theft of member data that |
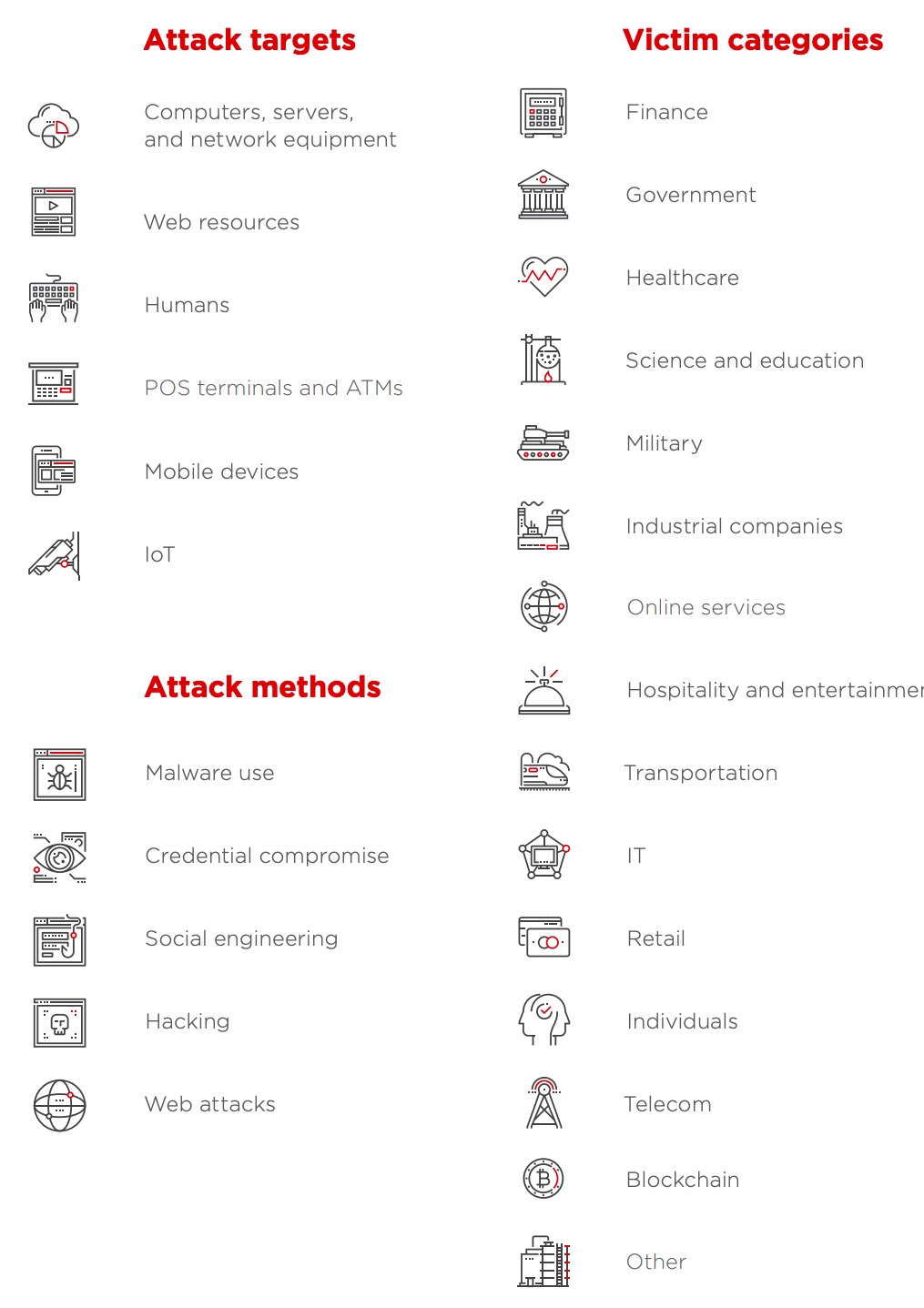
What are the two dimensions of cyber security?
- with two dimensions — the impact of an attack and the likelihood of an exploit. If an organization or firm exposes its information assets due to poor cybersecurity hygiene resulting from a weak dev. ops process, then it doesn’t take much resources from an attacker to exploit that weakness. With the advent of web scanners and dark web, the
What is NIST Cybersecurity Report DevOps?
- 6 EY Cybersecurity Report Dev.ops in a NIST context NIST highlights five essential efforts for cybersecurity in which firms and organizations are to partake. It begins with NIST’s cybersecurity
What is continuous deployment in EY Cybersecurity Report 5?
- EY Cybersecurity Report 5 Following continuous delivery, dev.ops’ continuous deployment will seek to deploy the tested and delivered software. Continuous deployment will thus automatically deploy the delivered software without an actual person acting as a gatekeeper.
How can EY help with cybersecurity?
- and profiles Governance structure Training and metrics Implemented security xxxxxxxxx Requirement EY has long been operating a cybersecurity service to offer advisory and assurance related services to a myriad of firms, thereby helping mitigate the risks within information systems development, security designs and cybersecurity hygiene.
|
Download report Cyber Threats 2019: A Year in Retrospect - PwC
well as publicly available information from the cyber security community This report intends to highlight the most prolific trends PwC observed throughout 2019 |
|
Cyber Threats 2020: A Year in Retrospect - PwC
17 déc 2020 · In July 2020, the UK's National Cyber Security Centre (NCSC) reported that 2019: A Year in Retrospect' report, PwC assessed that multiple |
|
The future of cyber survey 2019 - Deloitte
As one of the leading and largest cybersecurity risk advisory practices globally, our team of more than 4,000 cyber risk professionals continues to walk alongside |
|
Cloud Security Report - PwC
Cloud Security Report 2019 www pwc com “Software as a Service” are being taken based on rational and empirical evidence, cybersecurity questions are |
|
Organisations that embed cybersecurity into their business - PwC
17 mai 2019 · better outcomes and outperform their peers, according to PwC's May 2019 Digital Trust Insights · Survey The global survey of more than 3,000 |
|
The journey to digital trust - PwC
Survey (GSISS) as a trusted resource to navigate the cyber risk landscape As cybersecurity, privacy and data ethics become increasingly 2019 PwC |
|
Cybersecurity: are you asking the right questions? - PwC China
translate into a cybersecurity spend of 10 or more of their IT budget 1 1 Source: PwC 2019 Digital Trust Insights Survey 2 Source: PwC COVID-19 CFO Pulse |
|
2019 Global Cyber Risk Perception Survey - Microsoft
– 55 said government needs to do more to protect organizations against nation -state cyber-attacks Page 5 Cybersecurity Culture and Resilience Many |
|
Cyber Security Breaches Survey 2019 - Govuk
3 avr 2019 · 2019 The Cyber Security Breaches Survey is a quantitative and qualitative survey of UK businesses and charities For this latest release, the |
|
PwCs 2019 Annual Corporate Directors Survey - Círculo de Directores
Source: PwC, 2019 Annual Corporate Directors Survey, October 2019 Boards are also becoming confident about their approach to cybersecurity oversight |