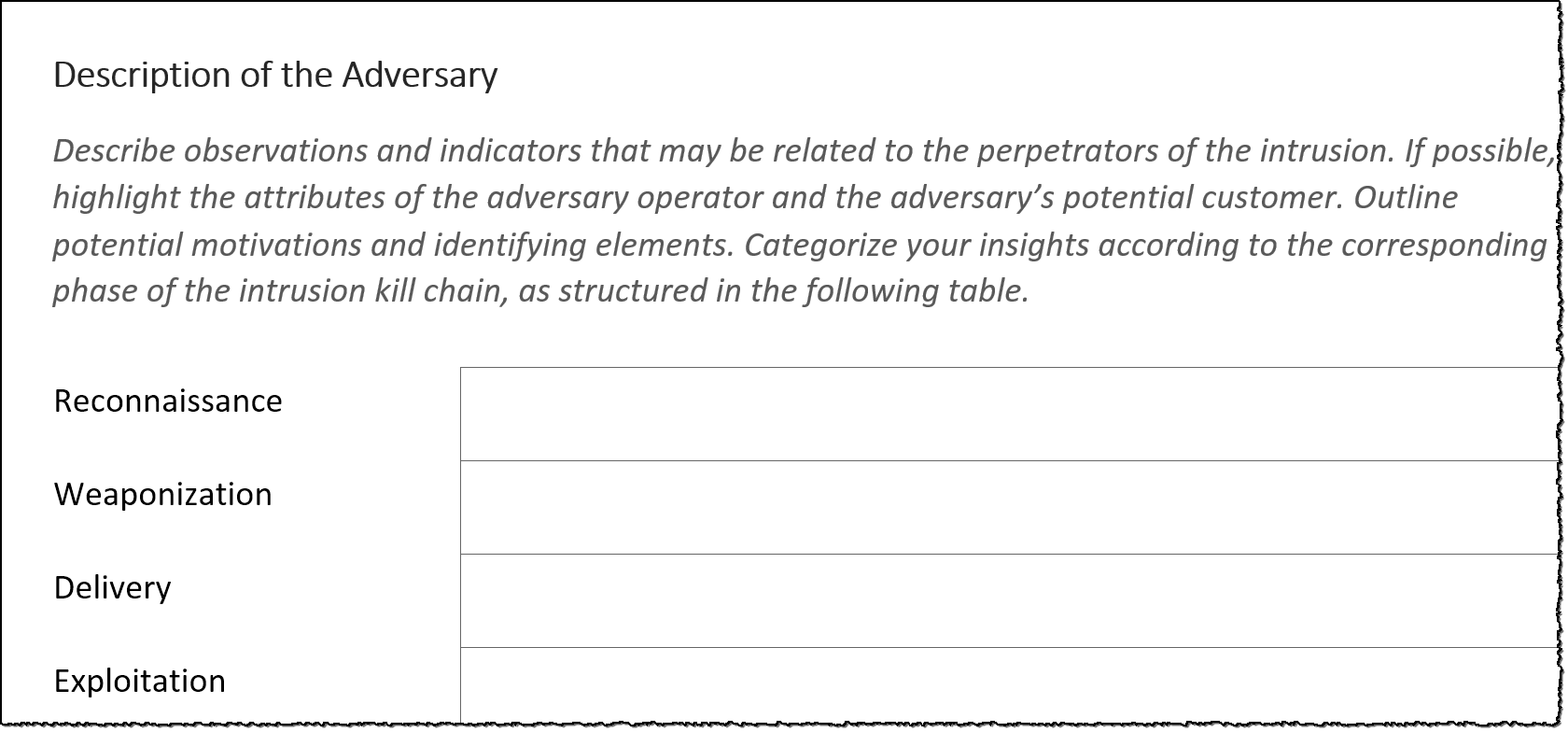
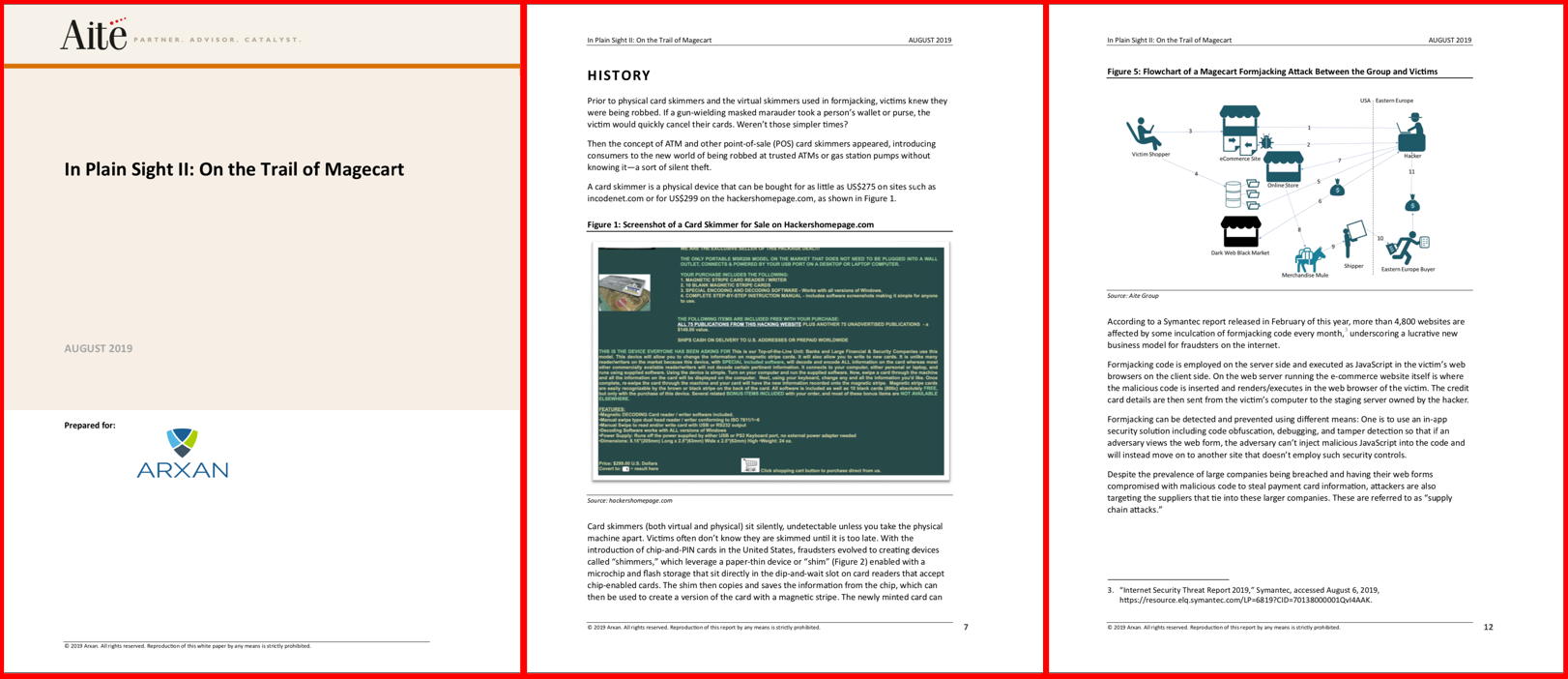
sans top new attacks and threat report
|
SANS 2021 Top New Attacks and Threat Report
SANS 2021 Top New Attacks and Threat Report. Introduction. The media covers many breaches and outages and backward-looking statistics related. |
|
SANS Top New Attacks and Threat Report
databases) and attackers simply move on to the smaller |
|
DomainTools
This SANS whitepaper begins with a baseline of statistics from two of the most reliable sources of breach and malware data then summarizes the expert advice. |
|
Top New Attacks and Threat
In the SANS 2021 Top New Attacks and Threat Report John Pescatore will provide deeper insight into the threats highlighted during the SANS panel discussion |
|
SANS Top New Attacks and Threat Report
SANS has found the Identity Theft Resource Center (ITRC) Annual Breach Report2 the. Microsoft Security Intelligence Report (SIR)3 and the Center for Internet |
|
Stratejm
databases) and attackers simply move on to the smaller |
|
SANS 2021 Top New Attacks and Threat Report
Because the pandemic delayed the RSA Security Conference and the annual SANS New. Attack and Threat panel this year's SANS Attack and Threat report focuses |
|
A SANS 2021 Report: Making Revolutionary Gains in Security on
The SANS 2021 Top New Attacks and. Threat Report3 projected the key. “next wave” attacks that enterprises need to be prepared for: • Software integrity attacks— |
|
2021 SANS Cyber Threat Intelligence (CTI) Survey
have reported that CTI teams primarily consisted of security operations center With the move of news and media reporting as a top collection source for. |
|
A SANS 2021 Survey: OT/ICS Cybersecurity
The operational technology (OT)/industrial control system (ICS) security world continually adapts to meet new challenges and threats. This 2021 SANS OT/ICS |
|
SANS Top New Attacks and Threat Report
SANS Top New Attacks and Threat Report Written by John Pescatore April 2019 Introduction There is no shortage of media coverage of breaches and outages and there are many places to find backward-looking statistics about how many attacks were launched in cyberspace |
|
SANS 2021 Top New Attacks and Threat Report SANS Institute
SANS 2022 Top New Attacks and Threat Report This annual report will provide deeper insight into the threats highlighted during the SANS keynote panel discussion at the RSA® Conference 2022 The paper will include insight from SANS instructors Ed Skoudis Heather Mahalik Johannes Ullrich and |
|
A SANS 2021 Report Top New Attacks and Threat
In the SANS 2021 Top New Attacks and Threat Report John Pescatore will provide deeper insight into the threats highlighted during the SANS panel discussion at the 2021 RSA Conference The paper will include practical advice from SANS instructors Ed Skoudis |
|
SANS 2021 Top New Attacks and Threat Report
SANS 2021 Top New Attacks and Threat Report 5 Ed Skoudis: Undermining Software Integrity Ed Skoudis addressed the SolarWinds attack which severely compromised hundreds of companies and government agencies 6 A supply chain attack such as this seeks to attack all the companies that have the compromised company (in this case SolarWinds) |
|
SANS 2022 Top New Attacks and Threat Report
SANS 2022 TOP NEW ATTACKS AND THREAT REPORT Lead Submission The initial installment of leads will be provided within two business days of the live presentation Additional leads will be provided on a regular basis for the first three months following the presentation After three months leads will be provided as requested |
|
Searches related to sans top new attacks and threat report filetype:pdf
Report: The 2019 SANS Top New Attacks and Threat Report will be promoted for 5–6 weeks through a weekly email blast to SANS opt-in audience SANS e-newsletters and social media Webcast: Promotion of the 2019 SANS Top New Attacks and Threat Report will begin once the webcast has been scheduled |
Can I re-post the Sans 2021 top new attacks and threat report?
- No re-posting of papers is permitted In the SANS 2021 Top New Attacks and Threat Report, John Pescatore provides insight into the threats highlighted during the SANS panel discussion at the 2021 RSA Conference. This webcast will include practical advice from the paper, including insights from SANS instructors Ed Skoudis, Heather...
What are SANS Top 20 vulnerabilities?
- The SANS agency will also rank vulnerabilities that are released yearly and calls this the SANS Top 20 Vulnerabilities list. SANS Top 20 is considered to be as a roll of security threats that are in need of urgent patching up by the companies concerned. Security holes in the popular operating systems are sometimes revealed by SANS list.
How many attacks does Sans have?
- Sans has 24 attacks, but a couple of them repeat often. Sans starts off the fight with his "strongest move," which can catch many new players off guard. But it's always going to be the same move so once you learn how to dodge it, you can dodge it as many times as you want.
What is a SANS Top 25 report?
- They represent the bare minimum to comply with for anyone putting in place a secure development lifecycle. The SANS Top 25 report is based on outdated statistics and should no longer be used. Instead, we recommend using the CWE Top 25 reports. Security reports rely on the rules activated in your quality profile to raise security issues.
|
Cyber Security Report 2020 - National Technology Security
In this 2020 Cyber Security Annual Report, we provide you with a timeline of 4 “ Hacker Breaches Dozens of Sites, Puts 127 New Million Records Up for Sale,” by Swati While email is the top attack vector, bad actors are using a variety of tricks 102 “More Malspam Pushing Formbook,” SANS ISC InfoSec Forums, 2019 |
|
2020 SANS Cyber Threat Intelligence (CTI) Survey - ThreatConnect
Respondents report that requirements are primarily updated in an ad hoc manner rather than on a scheduled (yearly, monthly or weekly) basis But the good news |
|
INTERNET SECURITY THREAT REPORT 2015 - ITU
Distributed by INTERNET SECURITY THREAT REPORT 2015 malware estimated at almost 1 million new variants every day • Increasing Top 5 Web Attack Toolkits 42 Timeline of Many organizations, such as the SANS Institute, U S |
|
2020 Cyber Threatscape Report I Accenture
The cyber threat intelligence team, referred to in this report as Accenture CTI, provides IT Sophisticated threat actors are employing new TTPs to help achieve their long- standing objectives of With game-changing ransomware attacks, such as the good threat intelligence was a priority to tackle the relentless pressure |
|
Web Attacks: The Biggest Threat to Your Network
Attacks such as SQL injection and Cross-Site Scripting (XSS) are responsible for some of the largest security breaches in history, including the top three credit |
|
The SANS Institute Top 20 Critical Security Controls - CUCAIER
mitigate probable attacks and protect critical information In today's What are the SANS Top 20 Critical Security Controls? In 2008, the SANS Enables administrators to configure asset scanning and reporting using sites and asset groups Enables you to limit administrative privileges by monitoring the network for new |
|
Report on Cybersecurity Practices - FINRAorg
information at broker-dealers that create a variety of new avenues for attack The SANS Top 20 focuses “first on prioritizing security functions that are effective |