sign extension vulnerability
|
Integer bugs - TOOR - Computer Security
Apr 30 2012 Unsigned integer boundaries (overflow/underflow). Type conversion vulnerabilities: • Signed/unsigned conversions. • Sign extension. |
| Twice the Bits Twice the Trouble: Vulnerabilities Induced by |
|
Secure Coding in C and C++
source of vulnerabilities in C and C++ programs. the signed integer is sign-extended ... Sign-extend to short; convert short to unsigned short. |
|
Protecting Browsers from Extension Vulnerabilities
The most dan- gerous class of extensions (extensions with the privilege to execute arbitrary code) are not permitted in the gallery unless the developer signs a |
|
Armv8.5-A Memory Tagging Extension
important classes of security vulnerability in code written in C-like languages are still violations of memory safety. According to a 2019 BlueHat |
|
O Single Sign-Off Where Art Thou? An Empirical Analysis of Single
Aug 15 2018 systems and the ramifications of potential vulnerabilities. ... single sign-off |
|
C Language Issues
Listings 6 - 14 of subtle vulnerabilities in software that remain unnoticed and uncorrected for ... versions and comparisons sign extension |
|
A Qradar Log Source Extension Walkthrough
Ongoing improvements strive to minimize false positives by including more information such as threat and reputation feeds and host vulnerability data. SIEM |
|
Qualys Web Application Scanning Getting Started Guide
Sep 18 2020 automated vulnerability scanning of web applications for teams using ... Qualys Browser Recorder – This new Chrome extension allows users to ... |
|
An Evaluation of the Google Chrome Extension Security
We ?nd that 40 extensions contain at least onetype of vulnerability Twenty-seven extensions containcore extension vulnerabilities which give an attacker fullcontrol over the extension Based on this set of vulnerabilities we evaluate theeffectiveness of each of the three security mechanisms Our primary ?ndings are: |
Signed/Unsigned Conversions
Most security issues related to type conversions are the result of simple conversions between signed and unsigned integers. This discussion is limited to conversions that occur as a result of assignment, function calls, or typecasts. For a quick recap of the simple conversion rules, when a signed variable is converted to an unsigned variable of the...
Sign Extension
Sign extension occurs when a smaller signed integer type is converted to a larger type, and the machine propagates the sign bit of the smaller type through the unused bits of the larger type. The intent of sign extension is that the conversion is value-preserving when going from a smaller signed type to a larger signed type. As you know, sign exten...
Truncation
Truncationoccurs when a larger type is converted into a smaller type. Note that the usual arithmetic conversions and the integral promotions never really call for a large type to be converted to a smaller type. Therefore, truncation can occur only as the result of an assignment, a typecast, or a function call involving a prototype. Here's a simple ...
What are sign extension errors?
Sign extension errors can lead to buffer overflows and other memory-based problems. They are also likely to be factors in other weaknesses that are not based on memory operations, but rely on numeric calculation. This entry is closely associated with signed-to-unsigned conversion errors ( CWE-195) and other numeric errors.
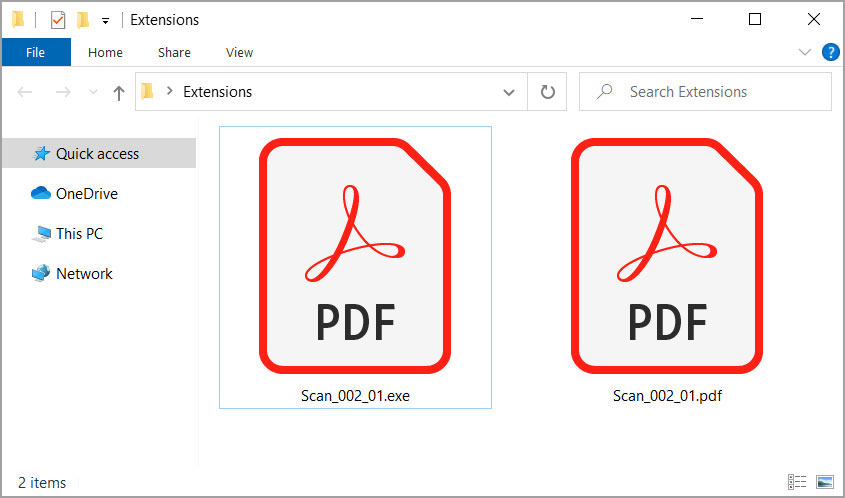
What are the vulnerabilities in PDF files?
A specially crafted PDF document can trigger the reuse of previously free memory, which can lead to arbitrary code execution. An attacker needs to trick the user into opening a malicious file or site to trigger this vulnerability if the browser plugin extension is enabled.
What is a vulnerability signature action?
A vulnerability signature action is set as "alert" while the severity of the signature is critical or high and it is providing coverage for a known CVE. The action should be either reset-both or reset-server or block. There are two conditions when a vulnerability signature action is "alert" and severity "critical" or "high."
What extensions enhance vulnerability detection and correction powers?
Visual Studio Code (VS Code) is arguably the most popular integrated development environment-code editor. In this article, we will be looking at some extensions that enhance our vulnerability detection and correction powers. 1. WhiteSource
|
Twice the Bits, Twice the Trouble: Vulnerabilities Induced by - INDI
Two types of integer signedness issues arise as code is ported from 32-bit to 64- bit platforms First, sign extensions may occur as signed integers are converted to |
|
Secure Coding in C++: Integers - SEI Digital Library - Carnegie
underestimated source of vulnerabilities in software vulnerabilities (even when this behavior is correct) Sign-extend to short; convert short to unsigned short |
|
Secure Coding in C and C++
source of vulnerabilities in C and C++ programs A software vulnerability may result when a program Sign-extend to short; convert short to unsigned short |
|
Chapter 6 - School of Computer Science - Carleton University
25 sept 2019 · 6 6 Buffer overflow exploit defenses and adoption barriers extended (0s fill the high-order bytes); a signed integer is sign-extended (the sign |
|
64-Bit Migration Vulnerabilities - Intelligent System Security
19 août 2016 · Sign extensions In effect, negative numbers are converted into large posi- tive numbers, a possible source for vulnerabilities For the LLP64 data model, new sign extensions occur for conver- sions from int and long to size_t and for LP64 from int to unsigned longand size_t |
|
Integer bugs - TOOR - Computer Security
30 avr 2012 · Type conversion vulnerabilities: • Signed/unsigned conversions • Sign extension • Truncation • Signed/unsigned comparison Heap overflows |
|
Integer overflow, ROP and CFI - CSE 127 Computer Security
Integer Type Conversion ▫ Sign-extension occurs when a value with a narrower , signed type is converted to a wider type ▫ When a value is sign-extended, it |
|
Integers, ROP, and CFI - CSE 127 Computer Security
Sign-extend Safe signed short int unsigned char Truncate to low-order byte Lost signed short int unsigned short int Preserve bit pattern; high-order bit no |
|
C Language Issues - GitHub Pages
14 oct 2006 · of subtle vulnerabilities in software that remain unnoticed and uncorrected for long versions and comparisons, sign extension, and truncation |