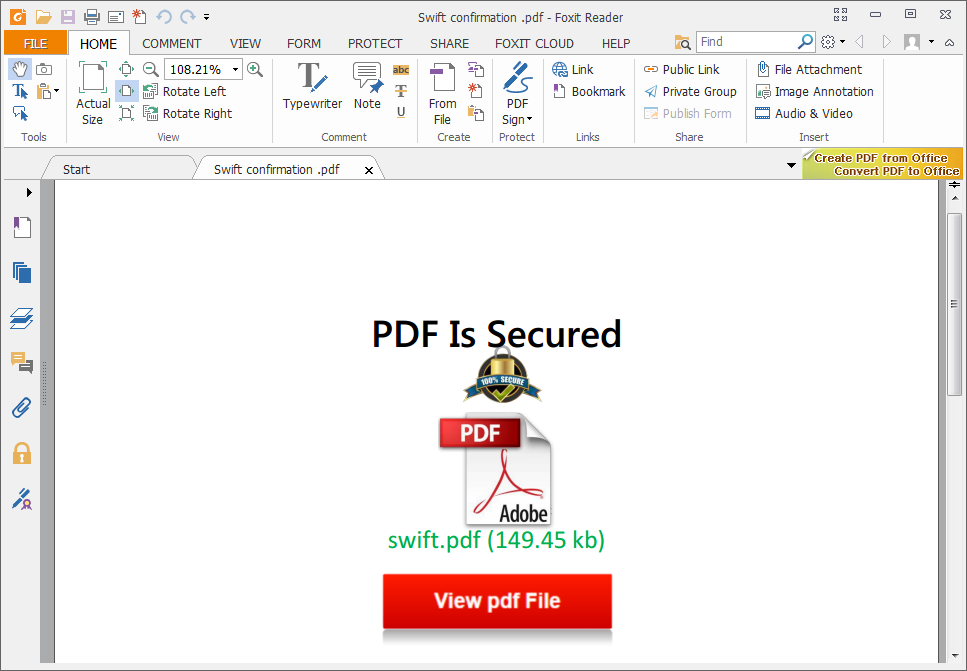
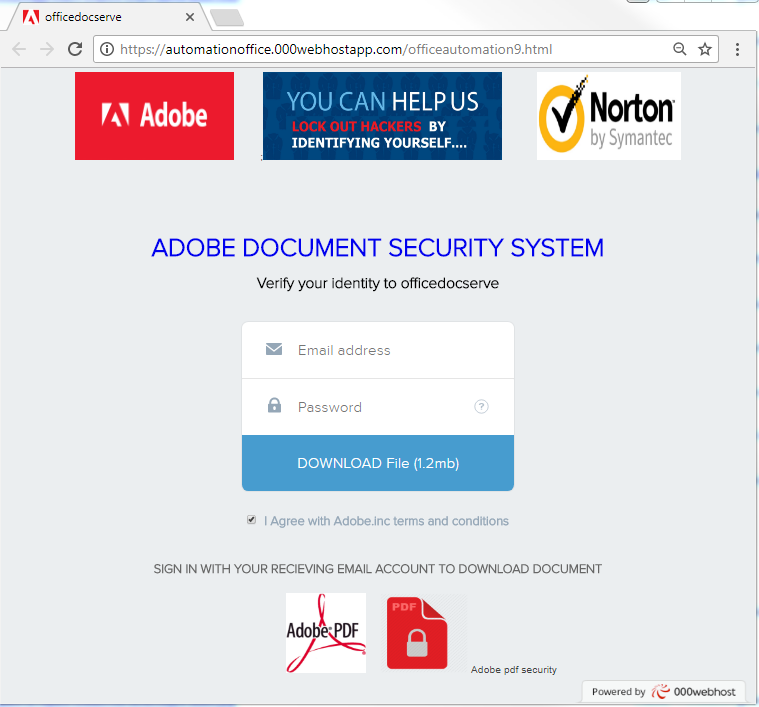
social phishing
|
Social Phishing
www.indiana.edu/~phishing. Page 7. Outline. • Social phishing = id-theft attack exploiting social network context. • How to harvest social networks from the. |
|
Social phishing
Results of the social network phishing attack and control experiment. An attack was “successful” when the target clicked on the link in the email and |
|
Guidance for Organisations on Phishing and Social Engineering
One way in which the risks regarding security of personal data can arise is through what are known as 'phishing' or 'social engineering' attacks. Phishing is an |
|
HHS.gov
18 Aug 2022 According to Carahsoft's 2021 HIMSS. Healthcare Cybersecurity Survey over a 12-month period |
|
Weaponizing data science for social engineering: Automated E2E
We present SNAP_R a recurrent neural network that learns to tweet phishing posts targeting specific users. The model is trained using spear phishing pentesting |
|
Cybersecurity Tips: Social Media and Scams
. To identify phishing on social media look out for: • Poor spelling and grammar. • Threats requiring a sense of urgency. • Spoofed or purported websites |
|
Fact-sheet-implementing-phishing-resistant-mfa-508c.pdf
Phishing. Phishing is a form of social engineering in which cyber threat actors use email or malicious websites to solicit information. For example in a |
|
The Weaponization of Social Media Spear Phishing and
While email remains the preferred medium to conduct spear-phishing attacks social media has opened up new attack vectors for politically motivated cyberattacks |
|
Social Phishing
12 Dec 2005 Phishing is a form of social engineering in which an attacker attempts to fraudulently acquire sensitive information from a victim by ... |
|
The Influences of Social Networks on Phishing Vulnerability
Phishing is a form of electronic deception in which an attacker tries to cause the recipient to do something or disclose data that they likely would not |
|
Social Phishing
Dec 12 2005 Social Phishing. ?. Tom Jagatic |
|
Weaponizing data science for social engineering: Automated E2E
Weaponizing data science for social engineering: Automated E2E spear phishing on Twitter. John Seymour and Philip Tully. {jseymour ptully}@zerofox.com. |
|
Guidance for Organisations on Phishing and Social Engineering
One way in which the risks regarding security of personal data can arise is through what are known as 'phishing' or 'social engineering' attacks. Phishing is an |
|
Social Phishing
Social Phishing. Tom Jagatic. Nate Johnson. Markus Jakobsson. Filippo Menczer. Dept. of Computer Science. School of Informatics. |
|
Social phishing
Results of the social network phishing attack and control experiment. An attack was “successful” when the target clicked on the link in the email and |
|
2019 PHISHING TRENDS AND INTELLIGENCE REPORT
We help enterprises protect their employees customers |
|
Social engineering & phishing
SOCIAL. ENGINEERING. The “ishings”. Other types. Phishing. Honey Trap. Spear Phishing. Watering Hole. Whaling. Scareware. Vishing. Pretext (pretending to be. |
|
HHS.gov
Aug 18 2022 According to Carahsoft's 2021 HIMSS. Healthcare Cybersecurity Survey |
|
ENISA ETL2020 - Phishing
credentials credit card information |
|
TRICK YOU
Defending Against Phishing & Social Engineering Attacks. A Resource Guide from the PCI Security Standards Council. Hackers use phishing and other social |
|
(PDF) Social phishing - ResearchGate
PDF Several suspected Internet users called pishers post a friendly e-mail for other users aiming at acquiring sensitive information from a victim |
|
Social phishing - ACM Digital Library
Phishing is a form of deception in which an attacker attempts to fraudulently acquire sensitive information from a victim by impersonating a trustworthy |
|
Social Phishing - Indiana University Bloomington
Social phishing = id-theft attack exploiting social network context • How to harvest social networks from the Web • An experiment • Results |
|
Social Phishing - Semantic Scholar
This research examines the design and development of algorithms that takes as input empirical data and outputs patterns and predictions for future data |
|
What is a social engineering attack?
Phishing is a form of social engineering Phishing attacks use email or malicious websites to solicit personal information by posing as a trustworthy |
|
Social Phishing - Markus Jakobsson
12 déc 2005 · Phishing is a form of social engineering in which an attacker attempts to fraudulently acquire sensitive information from a victim by |
|
Phishing and Social Media - Cofense
In spear phishing social engineering is the use of known social behaviors and patterns to make targets more likely to take a suggested course of action |
|
Social Media Phishing - UConn Health
Social Media Phishing is as the name suggests - Phishing on social media sites like Facebook and LinkedIn • Spelling errors are telltale signs of a scam |
|
Phishing Awareness - Valdosta State University
Attackers may gather personal information (social engineering) about their targets to increase their probability of success This technique is by far the most |
|
The Influences of Social Networks on Phishing Vulnerability - DTIC
In an attempt to reduce the overall success rate of a phishing attack this paper applies the foundations of social network analysis to identify how social |
What is social phishing?
In-App Phishing
All social media platforms provide some form of direct messaging between users. This functionality lets scammers create fake profiles and impersonate a victim's friends or family. Fraudsters exploit the direct channel and the user's trust to make up a phony situation and ask for help.What are the 4 types of phishing?
The 5 Most Common Types of Phishing Attack
Email phishing. Most phishing attacks are sent by email. Spear phishing. There are two other, more sophisticated, types of phishing involving email. Whaling. Whaling attacks are even more targeted, taking aim at senior executives. Smishing and vishing. Angler phishing.What is an example of social media phishing?
For example, one phishing attack involved a message telling users that WhatsApp was creating a 'Gold' service. The link in the message led users to a malicious website, however, the scam still spread across the social network, generally via large group chats.- Phishing email consequences can include identity theft, financial loss, and damage to reputation. Hackers have also been proficient in using social media to run their phishing schemes. By means of social engineering, they trick unsuspecting victims into sharing sensitive information.
|
Mécanismes de Social Engineering (phishing) : étude technique et
Le phishing est une technique de Social Engineering employée par ces pirates Il est utilisé pour subtiliser Le phishing : une méthode d'ingénierie sociale |
|
Social Phishing - Indiana University Bloomington
Cybersecurity: Can phishing attacks become more effective (dangerous) by exploiting context information about targets (victims)? social phishing Page 9 Page |
|
Understanding phishing techniques - Deloitte
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers This occurs when an attacker |
|
Phishing Is No Longer Just Email: Its Social Akamai
It will enable the enterprise to keep pace with today's evolving threat landscape, including the social phishing phenomena we explore in this white paper The |
|
Phishing (hameçonnage ou filoutage) - Economiegouvfr
Soyez vigilants sur les informations que vous communiquez Il peut s'agir d'un faux message, SMS ou appel téléphonique de banque, de réseau social, |
|
The Influences of Social Networks on Phishing Vulnerability - DTIC
potential to threaten national security In an attempt to reduce the overall success rate of a phishing attack, this paper applies the foundations of social network |
|
LES DANGERS DU PHISHING - Kaspersky
Le phishing correspond à l'attaque suprême d'ingénierie sociale Auparavant, la plupart des attaques d'ingénierie sociale étaient effectuées en « one-to-one » |











![PDF] Cybersecurity Threats Malware Trends and Strategies by Tim PDF] Cybersecurity Threats Malware Trends and Strategies by Tim](https://www.ncsc.gov.uk/static-assets/images/phishing_infographic_final.jpg)