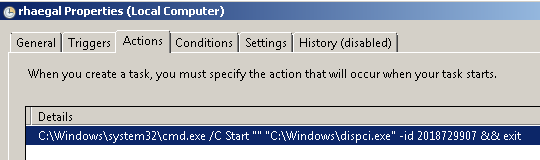
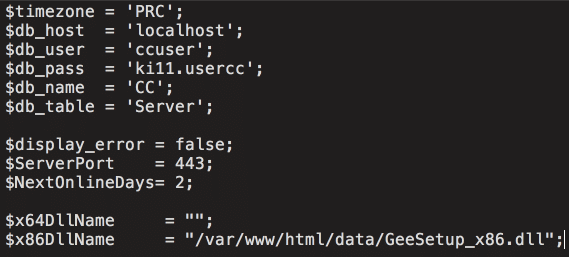
supply chain attack nyetya
|
Cisco Live 2018 Barcelona
Nyetya/Petya Purpose: to determine if target is suitable for attack ... Nyetya. • Supply chain attack with a huge global impact. • Avast CCleaner. |
|
We Keep Your Network Safe
Nyetya / MEDoc. • BadRabbit NotPetya: The Costliest Cyber Attack in History ... attacks. Phishing. Unpatched software. Supply chain attacks. Ransomware. |
|
Technical Compendium - Supply Chain Security in the Cyber Age
15 févr. 2020 One of the most prominent and massive recent attacks on software supply chains is the Nyetya (Cisco. TALOS naming convention) or NotPetya ... |
|
2018 ACR
Security weak spot: the supply chain. The Nyetya campaign was also a supply chain attack one of many that Cisco threat researchers observed in 2017. One. |
|
MITRE
Cyber Resiliency Mitigations for Supply Chain Attacks A recent example of an attack in which the software supply chain was compromised is Nyetya. |
|
MITRE
19 oct. 2017 Cyber Resiliency Mitigations for Supply Chain Attacks ... example of an attack in which the software supply chain was compromised is Nyetya. |
|
INTELLIGENCE
and attack opportunities are expanding just as quickly. TALOS OUT IN FRONT: NYETYA new cryptocurrency mining malware supply chain attacks |
|
Session Presentation
Two such supply chain attacks in 2017 Nyetya and Ccleaner |
|
TALOS INTELLIGENCE-talos_whitepaper
and attack opportunities are expanding just as quickly. Talos Out in Front: Nyetya identifying new cryptocurrency mining malware supply chain attacks ... |
|
ATTACKING FROM INSIDE
Another crucial aspect of a wiper attack is the such as Shamoon2 BlackEnergy and Nyetya/ ... supply chain as an attack vector. This attack. |
|
Supply Chain Attacks and Resiliency Mitigations - MITRE
In this paper cyber resiliency is applied to the problem of mitigating supply chain attacks The adversary's goals for attacking a supply chain are described |
|
Supply Chain Attack Framework and Attack Patterns - MITRE
The framework structures and codifies supply chain attacks using attack patterns that include associated threat and vulnerability information 2 1 2 Expected |
|
Software Supply Chain Attacks
Software Supply Chain Attacks can target products at any stage of the development lifecycle to achieve access conduct espionage and enable sabotage |
|
Technical Compendium - Supply Chain Security in the Cyber Age
15 fév 2020 · Annex II Examples of supply chain attacks and massive recent attacks on software supply chains is the Nyetya (Cisco attack on PDF |
|
Supply chain attacks - ENISA - European Union
29 août 2017 · This note provides an overview of “supply chain attacks” and presents how this attacking technique is related to known cyber-threats |
|
Supply Chain Attacks - Cyber Tec Security
Security Researcher Alex Birsan demonstrated a new kind of Supply Chain attack involving the injection of malicious code in tools used to install |
|
The MeDoc Connection - Cisco Talos Blog
5 juil 2017 · The Nyetya attack was a destructive ransomware variant that affected The investigation found a supply chain-focused attack at M E Doc |
|
Instructions – Supply chain attack - Kyberturvallisuuskeskus
The purpose of these instructions drawn up by the National Cyber Security Centre Finland of the Finnish Transport and Communications Agency Traficom is to |
|
Software Supply Chain Attacks
1) What is a Software Supply Chain Attack? 2) Proven Vectors From Which Attacks Occur 3) Recent Prominent Supply Chain Attacks on Software Malware |
|
Defending Against Software Supply Chain Attacks - CISA
A software supply chain attack occurs when a cyber threat actor infiltrates a software vendor's network and employs malicious code to compromise the |
|
Wiper white paper - AWS
Another crucial aspect of a wiper attack is the fear, uncertainty and such as Shamoon2, BlackEnergy and Nyetya/ NotPetya supply chain as an attack vector |
|
Cisco 2018 Annual Cybersecurity Report
6 fév 2018 · Security weak spot: the supply chain The Nyetya campaign was also a supply chain attack, one of many that Cisco threat researchers |
|
THE RISE OF SUPPLY CHAIN ATTACKS - Events
THE RISE OF SUPPLY CHAIN ATTACKS TV-W04 Director Outreach Cisco Talos #RSAC Nyetya Impact almost certainly used to distribute Nyetya |
|
Forum2017-08-Philippe_Bourgeois-Evolution_Menacespdf - Cert-IST
29 nov 2017 · Ces attaques « sans virus » sont difficiles à détecter ○ Attaque via la « Supply Chain » : en compromettant des logiciels légitimes utilisés par l' |
|
We Keep Your Network Safe - Cisco Live
Nyetya / MEDoc • BadRabbit NotPetya: The Costliest Cyber Attack in History attacks Phishing Unpatched software Supply chain attacks Ransomware |
|
Cisco Live 2018 Barcelona
WannaCry • First of it's kind ransomware worm using great exploits • Nyetya • Supply chain attack with a huge global impact • Avast CCleaner • Another supply |
|
Martin Lee - ICTswitzerland
2017 May WannaCry Self propagating ransomware June Nyetya / NotPetya Supply chain distributed wiper September CCleaner Supply chain attack |
|
Supply Chain Attacks and Resiliency Mitigations - The MITRE
19 oct 2017 · Adversary Advantages Gained Via Supply Chain Attacks of an attack in which the software supply chain was compromised is Nyetya |
|
INTELLIGENCE - Cisco Talos
and attack opportunities are expanding just as quickly TALOS OUT IN FRONT: NYETYA new cryptocurrency mining malware, supply chain attacks, or |
|
Vol 3 Issue 3 - STRATEGIC PERSPECTIVES ON
7 ) ▫ ISSUE 3 STRATEGIC PERSPECTIVES ON CYBERSECURITY MANAGEMENT AND PUBLIC POLICIES attacks We will also learn more about countermeasures that may be used to stop them But digital What Can We Learn From WannaCry and Nyetya? an effort to balance the currently inadequate supply |