the concept of having multiple layers of security policies and practices is known as:
|
Recommended Practice: Improving Industrial Control System
policy and procedures process control |
|
Guidelines on firewalls and firewall policy
Computer Security Division concept implementations and technical analysis to advance the ... 3.3 Architecture with Multiple Layers of Firewalls . |
|
AWS Security Best Practices
security policies and processes for your organization's assets on AWS. For more layers of protection beyond those provided by the AWS secure global ... |
|
Authentication and Access to Financial Institution Services and
Implementing layered security to protect against unauthorized access. consistent with the financial institution's internal practices and policies. |
|
Department of Homeland Security Strategic Framework for
of multiple mutually supportive layers of defense in lieu of relying on one practice principles and privacy-focused Departmental policies. |
|
UNODC
Applying techniques (often known as “target hardening techniques”) concept involves the use of multiple “rings” or “layers” of security. The application. |
|
How to Implement Security Controls for an Information Security
in the series Information Security Best Practices for CBRN Facilities |
|
Guide to Industrial Control Systems (ICS) Security
4.4 Define ICS-specific Security Policies and Procedures . Implementing a network topology for the ICS that has multiple layers with the most critical. |
|
Oracle Cloud Infrastructure Security Architecture (PDF)
Services and data span racks of hardware which themselves include multiple layers of redundancy at the node |
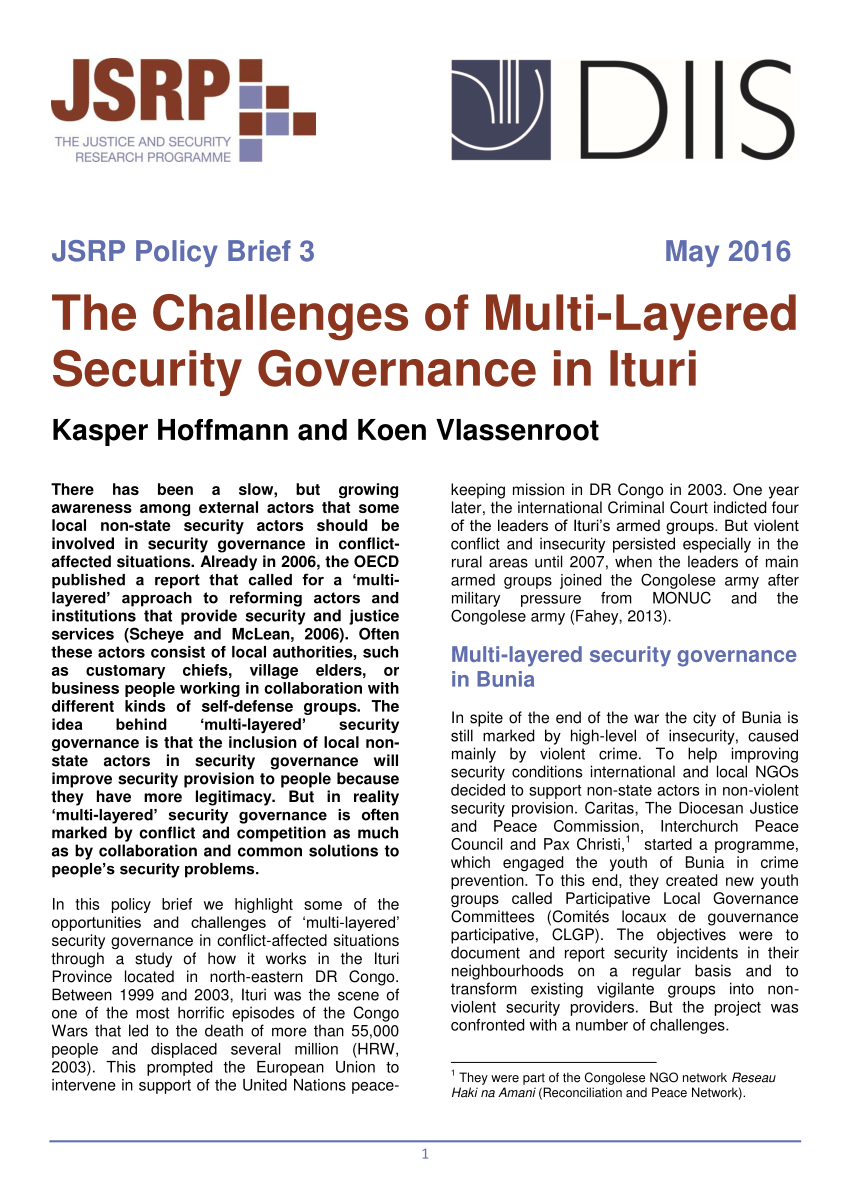
What are the 7 layers of cybersecurity?
The 7 layers of cybersecurity should center on the mission critical assets you are seeking to protect. 1: Mission Critical Assets – This is the data you need to protect* 2: Data Security – Data security controls protect the storage and transfer of data.
What is a layered security model?
A holistic model that uses layers of security to protect mission-critical assets is critical. Even if a phishing campaign is successful or a remote network is compromised, the CISO who implements layered approach will have nets further along that decrease vertical and lateral movement within the network of malicious forces.
What are the key security layers in a defense-in-depth strategy?
As companies grow and the number of devices, applications, and services used across the organization increases, these serve as important security layers in a defense-in-depth strategy: Two-factor authentication (2FA) or multi-factor authentication (MFA)
What is a multi-tiered approach to security in a defense-in-depth system?
The multi-tiered approach to security in a defense-in-depth system incorporates elements from the following areas: Physical controls: Examples include key cards to enter a building or scanners to read fingerprints. Network security controls: This is software that authenticates an employee to enter the network and use a device or application.
Past day
What is Defense in Depth? Defined and Explained | Fortinet
Layered security is having multiple products in place to address one single aspect of security. The products may be very similar and aim to do the same job, but in a layered security strategy, they are both necessary. lgo algo-sr relsrch fst richAlgo" data-380="645fa8a41cfc6">www.fortinet.com › resources › cyberglossaryWhat is Defense in Depth? Defined and Explained | Fortinet www.fortinet.com › resources › cyberglossary Cached
|
Understanding Security Layers - Clarke County School District
Defense in depth means using multiple layers of security to defend your assets That way, even if an attacker breaches one layer of your defense, you have additional layers to keep that person out of the critical areas of your environment |
|
Information Security Essentials for IT Managers: Protecting Mission
with all business units, security managers must work security into the evaluation of the level of security awareness and practice at any organization, application programs and operating systems to support the security policy of the The idea of risk management is that threats of any kind must be identified, classified, and |
|
General Guidelines: Information Security - University of Otago
Information Security is a broad term used to describe the process of keeping sensitive information contains a wide range of best-practices and guidelines to help University It is always tempting to do away with multiple layers of security Know your IT Support staff, and be familiar with University of Otago IT policies |
|
Defense-in-Depth - SEI Digital Library - Carnegie Mellon University
integrity, and availability can lead to a comprehensive security strategy secure/thorough administrative practices (e g , access controls, permissions/ rights, integrity Plans should be well known to all organizational employees and end-users Primarily, policy development is structured around the concept of layers |
|
Security Whitepaper: Google Apps Messaging - Bradley University
The emergence of various “cloud computing” concepts and definitions has environment — often called the “cloud” — allows CPU, memory and storage Google's security vision is formed around a multi-layered security strategy that provides t Publishing new techniques for secure programming to remain current with |
|
Information Systems Security Policy Violation: Systematic - CORE
stated by Morrell, (2008) has been “to advance policy and practice by providing of security policies by internal agents through making effort to identify as many SLR by definition will differ from a traditional literature review in that the scope is highly address a well-known problem in information retrieval described as the |
|
Information Security Policy, Procedures, Guidelines - Oklahomagov
communicate the Policy, procedures, guidelines and best practices to all state agencies unauthorized disclosure or use according to the owning Agency's defined Managing information security within the State can be layered into three types (collectively known along with other unwelcome activity as Net Abuse) The |