three tier security checks in governance
|
Pre-Employment Screening Guidance for Applicants
If you do not have National Security Clearance applications are managed through an online government National Security Vetting Solution (NSVS). 3. You will |
|
NATIONAL SECURITY VETTING
There are currently three categories of security clearance: ▫ Counter-Terrorist Check. ▫ Security Check. ▫ Developed Vetting. Checks are carried out only so |
|
Transforming Federal Personnel Vetting
10 апр. 2023 г. • Three-Tier Investigative Model – Three investigative tiers — Low Moderate |
|
DOD Initial Orientation and Awareness Training Student Guide 8/12
12 авг. 2021 г. The Tier 3 and Tier 5 national security background investigations ... Requirements may be different for each agency so check with you Security. |
|
20221031-HMG Personnel Security Controls-V6.0-October 2022.docx
31 окт. 2022 г. There are four different levels of national security vetting clearance: ○. Accreditation Check (AC) / Level 1A (L1A) |
|
GOVERNMENT OF INDIA MINISTRY OF HOME AFFAIRS LOK
30 апр. 2013 г. security and check infiltration along the coastline. A three tier coastal security ring all along our coast is provided by. Marine Police ... |
|
Security Clearance Process: Answers to Frequently Asked Questions
5 окт. 2023 г. 47 For example initial investigations for security clearances are typically a Tier 3 or Tier 5 background investigation. The reimbursable ... |
|
HMG Baseline Personnel Security Standard - GOV.UK
An alternative is to build in to any contract for services a requirement that the same checks made for government employees must first level security features ... |
|
Security Clearance Process: Answers to Frequently Asked Questions
5 окт. 2023 г. 47 For example initial investigations for security clearances are typically a Tier 3 or Tier 5 background investigation. The reimbursable ... |
|
Measuring Security Sector Governance: A Guide to Relevant
It comprises 24 indicators in three fields: the level of ongoing domestic and international conflict; the level of militarisation; and the level of safety and |
|
Government Security Classifications - GOV.UK
1 mai 2018 There are three levels of classification: 3. Each classification provides for a baseline set of personnel physical and information security ... |
|
ENISA csirt MATURITY FRAMEWORK UPDATE
2. ENISA CSIRT MATURITY FRAMEWORK. 7. 2.1 3.1 SECURITY INCIDENT MANAGEMENT MATURITY MODEL (SIM3). 7. 2.2 CSIRT MATURITY STEPS – THREE-TIER APPROACH. |
|
Pre-Employment Screening Guidance for Applicants
If you do not have National Security Clearance applications are managed through an online government National Security Vetting Solution (NSVS). 3. You will |
|
Stormshield Endpoint Security Administration guide
12 août 2022 tools to apply different levels of control over how any individual or ... Before installing Stormshield Endpoint Security check that the ... |
|
Position Classification Standards for Security Administration Series
screening access to such areas and implementing related security controls. 3. Positions which are primarily concerned with conducting or supervising ... |
|
EU Grants: HE Programme Guide: V2.0 – 11.04.2022
17 juin 2021 Horizon Europe is divided into three pillars and one part corresponding to ... followed security trainings |
|
NIST SP 800-137 Information Security Continuous Monitoring
Tier 1 is organization Tier 2 is mission/business processes |
|
The relative roles of the three tiers of government—the federal
The relative roles of the three tiers of government—the federal government the state governments |
|
BROCHURE VIGIPIRATE GP
A government plan for vigilance prevention |
|
HMG Personnel Security Controls - GOV.UK
1.2. 5.0. January. 2022. Updated to introduce the Accreditation. Check as a new level of National. Security Vetting. 1 New document. Page 3. 3. Contents. |
|
NIST Risk Management Framework Overview
Jun 9 2014 · All three tiers in the risk management hierarchy Each step in the Risk Management Framework Risk Assessment A three-step process: Step 1: Prepare for the assessment Step 2: Conduct the assessment Step 3: Maintain the assessment In the context of four risk factors: Threats (source and event) Vulnerabilities Likelihoods Impacts |
|
Tiered Approach of NIST SP 800-39 - Rapid7
The DOD RMF governance structure implements the three-tiered approach to cybersecurity risk management described in NIST SP 800-39 synchronizes and integrates RMF activities across all phases of the IT life cycle and spans logical and organizational entities DOD RMF Guidance |
|
Implementation of Federal Investigative Standards Tiered
Tiered Investigations Three basic reasons for conducting background investigations National Security – access to classified Suitability / Fitness for government employment Personal Identity Verification in support of credentialing Homeland Security Presidential Directive 12 (HSPD-12) |
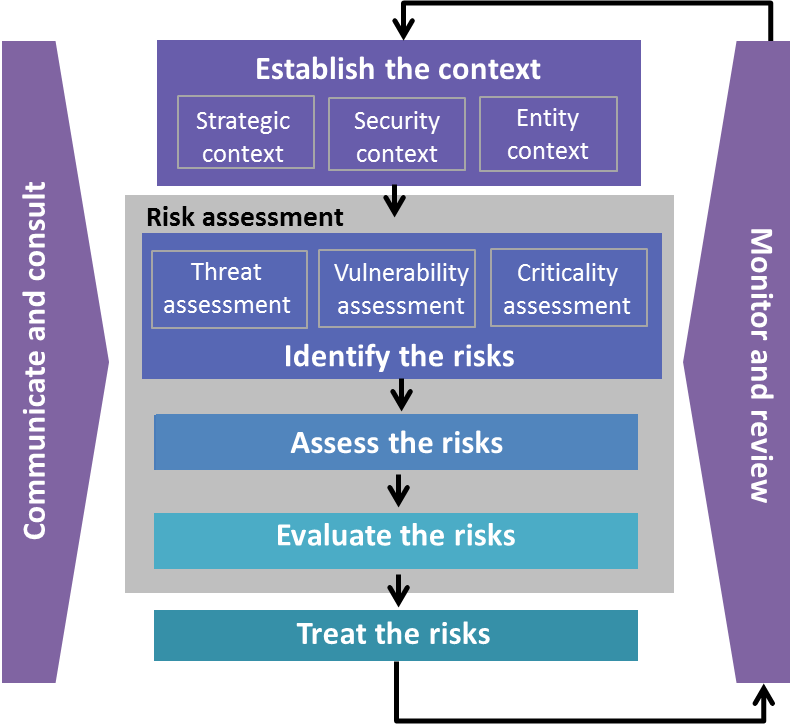
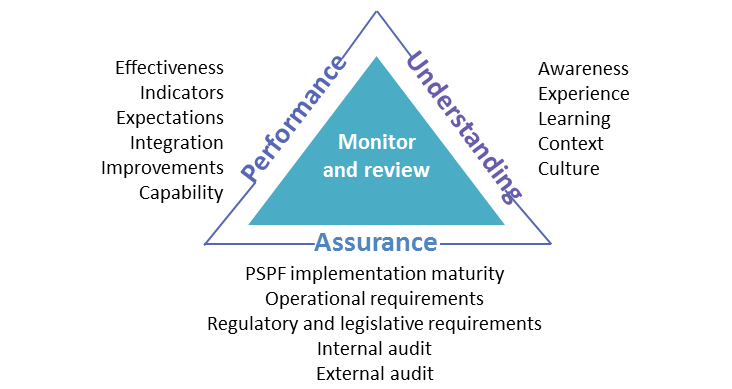
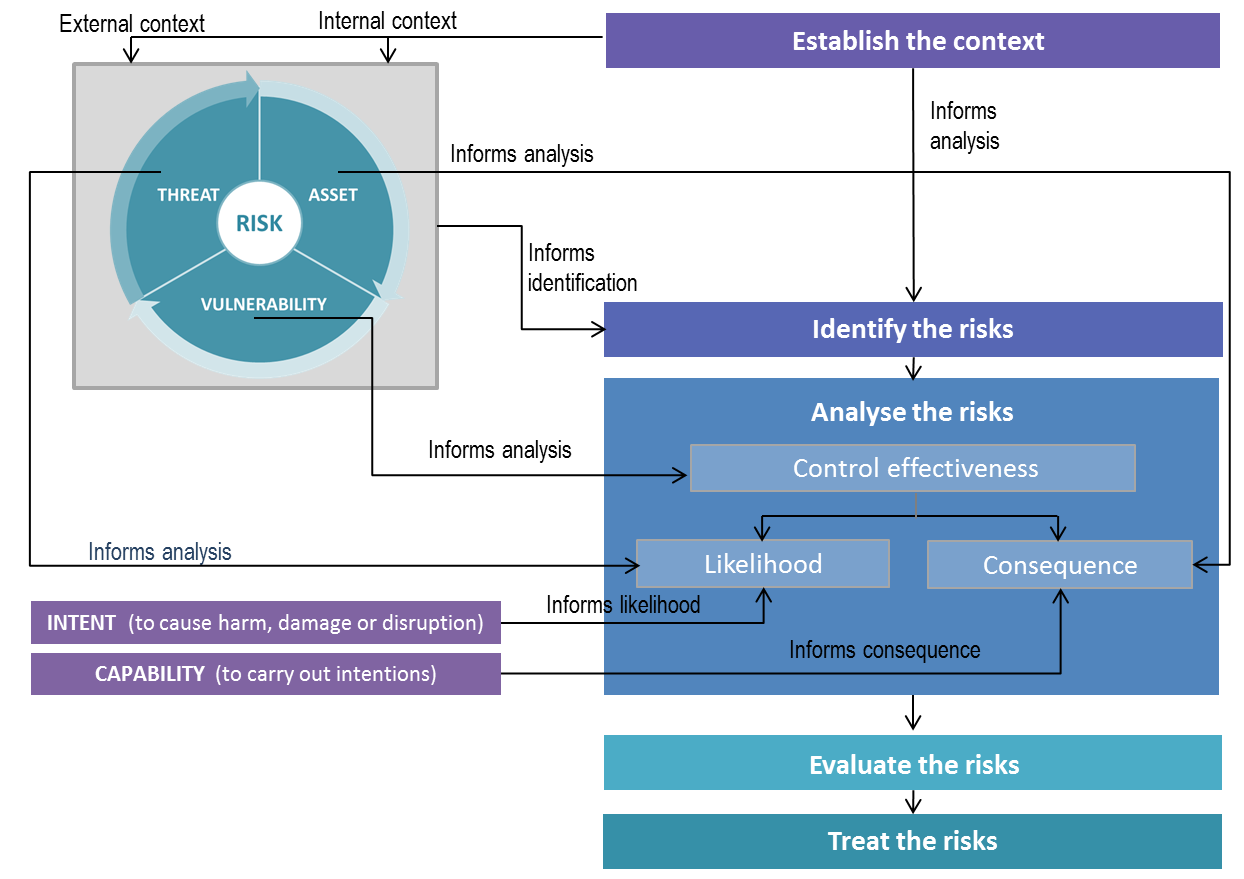
Risk Management
Risk management is a continuous process that is accomplished throughout the life cycle of a system and should begin at the earliest stages of program planning. It is used as the foundation of the Risk Management Framework (RMF). The approach is an organized methodology for continuously: 1. Risk Identification: identifying and measuring the unknowns...
Risk Management Framework (RMF) Stated Goals
The goals of the Risk Management Framework as stated by the Defense Security Service (DSS) are: 1. Improve information security 2. Strengthen risk management processes 3. Encourage reciprocity among federal agencies
Risk Management Framework (RMF) Objectives
The objectives of the RMF process include: 1. Incorporating cybersecurity early and robustly in the acquisition and system development life cycle. 2. Implementing a three-tiered approach to risk management that addresses risk-related concerns at the enterprise level, the mission and business process level, and the information system level. 3. Provi...
7 Steps of The Risk Management Framework
The RMF process parallels the defense acquisition process from initiation and consists of seven (7) steps: 1. Step 1: Prepare: Carry out essential activities at the organization, mission and business process, and information system levels of the enterprise to help prepare the organization to manage its security and privacy risks. 1.1. Quick Guide: ...
Risk Management Framework (RMF) Levels
The DoD RMF governance structure implements a three-tiered approach to cybersecurity risk management. 1. Tier 1 Strategic Level:Addresses risk management at the DoD enterprise level. At this tier, the DoD Chief Information Officer (CIO) directs and oversees the cybersecurity risk management of DoD IT. The Risk Executive Function is performed by the...
Risk Management Framework (RMF) Roles and Responsibilities
There are various roles and responsibilities for the development and execution of the risk management framework in any program. These roles and responsibilities are detailed in the RMF Roles and Responsibilities Crosswalk.
What is tier one of information security risk management?
Tier one provides context for all activities related to information security risk management. (This relates to the first phase of ISO 31000 risk management cycle.) This tier is the basis of enumerating, defining and prioritizing the business processes that are needed to fulfill the organization’s mission.
What is a Tier 1 risk executive function?
Tier 1 Strategic Level: Addresses risk management at the DoD enterprise level. At this tier, the DoD Chief Information Officer (CIO) directs and oversees the cybersecurity risk management of DoD IT. The Risk Executive Function is performed by the DoD Information Security Risk Management Committee (ISRMC).
What is a good governance structure for managing risk?
A good governance structure for managing risk is to establish three lines of defense. Briefly, the first line of defense is the function that owns and manages risk. Within the first line of defense, businesses can set up control functions (e.g., IT control, which reports to the IT department) to facilitate the management of risk.
What are the different types of security standards?
Security standards (e.g., US National Institute of Standards and Technology [NIST], ISO) Security products and tools (e.g., antivirus [AV], virtual private network [VPN], firewall, wireless security, vulnerability scanner) Web services security (e.g., HTTP/HTTPS protocol, application program interface [API], web application firewall [WAF])
|
SECURITY ISSUES AND COUNTERMEASURES OF THREE TIER
In [1] Manish Gupta et al developed an ontological framework to differentiate the existing countermeasures under three categories namely prevent, detect and |
|
Government Security Classifications - Govuk
1 mai 2018 · Executive Summary HMG information assets may be classified into three types: OFFICIAL, SECRET and TOP SECRET Each attracts a baseline set of security controls providing appropriate protection against typical threats |
|
Government Security Classification Scheme (Updated April - Govuk
2 avr 2014 · 3 The GSC introduces a 3 tier security classification policy of recruitment checks (e g the Baseline Personnel Security Standard (BPSS) or |
|
THREE TIER SECURITY PATTERN FOR CLOUD SYSTEMS
Three Tier Security System will be introduced, Government service is how the new technology can be checked against the one stored in the database |
|
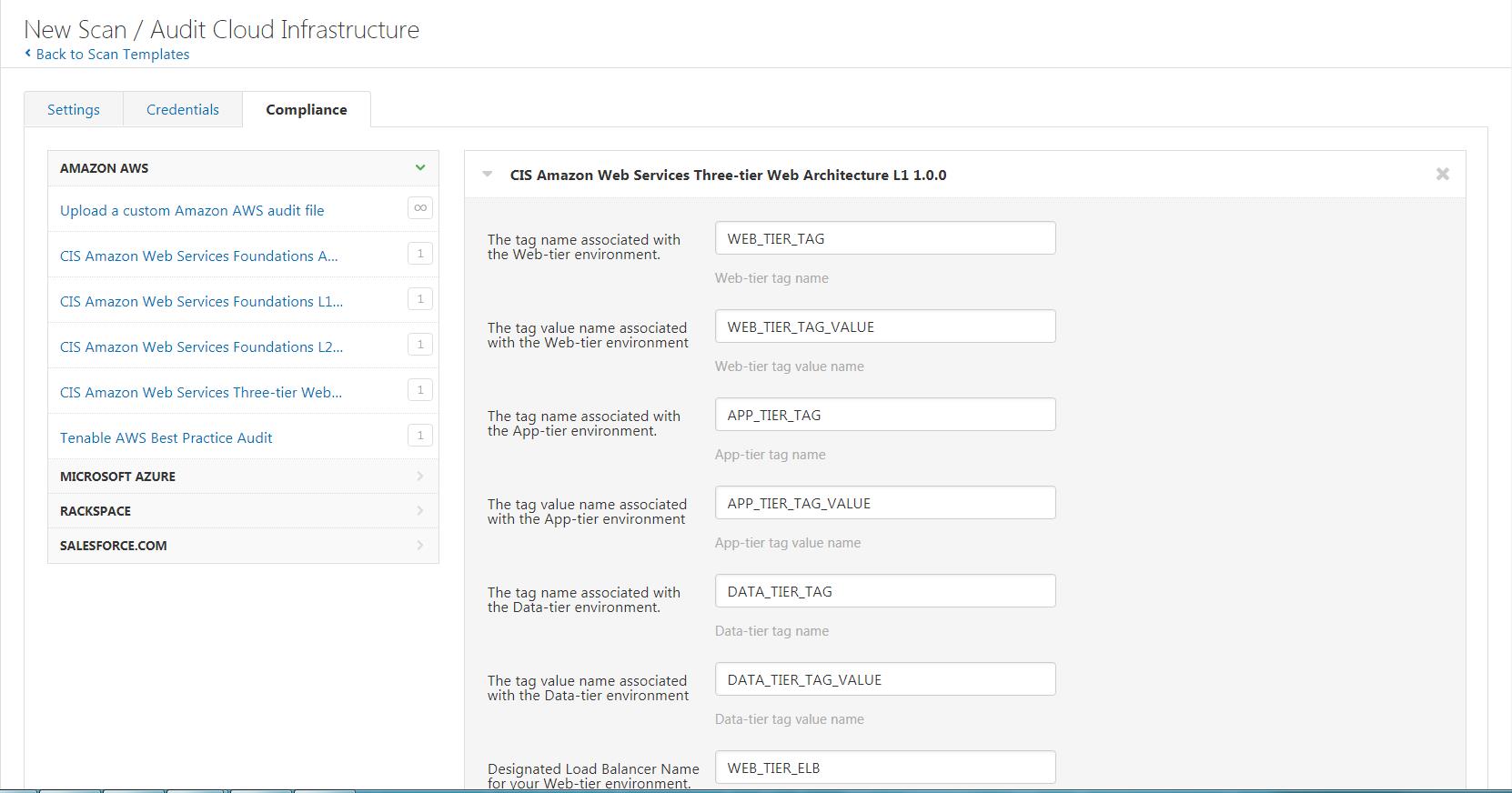
CIS Amazon Web Services Three-tier Web Architecture - Awsstatic
9 nov 2016 · 1 10 Ensure Web Tier ELB have the latest SSL Security Policies posture for a three-tier Web architecture deployed to the Amazon Web Note the EBS volume id's, Instance id's, Availability Zones, and check if Encrypted the threat that a government uses a subpoena or warrant to get access to a |
|
Web Application Security Standard
Information Officer (or designee) and/or the IT and Data Governance Trustees should be consulted “Tier 1 – mission critical” Web Applications represent core functions that Unknown data formats or requests are checked against the allow list, Security testing should occur during different phases of the Software |
|
PSR Overview booklet - Protective Security Requirements
The PSR's core policies cover four key areas: security governance, personnel security, information Tier 3 provides detailed management protocols and guidance to support your When necessary, your people must get a security clearance |
|
Security Controls Based Cloud Adoption for Government Workloads
benefits of commercial cloud services until an broadly divided into three tiers of impact Tier 3 High impact, sensitive government projects or related highly |
|
Receive and Maintain Your National Security Eligibility - CDSE
security clearance eligibility levels are: Federal Investigative Standards (FIS), a new five–tiered Federal Government employment, and eligibility for |
|
Introduction to the Risk Management Framework - CDSE
unified information security framework for the Federal government Finally, Tier 3 addresses risk management at the System Level Knowledge Check 1 |