an empirical analysis of traceability in the monero blockchain
|
A Traceability Analysis of Moneros Blockchain
We evaluate our attacks on the Monero blockchain and show that in 87 of cases the real output being redeemed can be easily identi˙ed with certainty Moreover we have compelling evidence thattwoofourattacksalsoextendtoMoneroRingCTs—thesecond generation Monero that even hides the transaction value |
What are the characteristics of a Monero non-RingCT transaction?
1. Unlinkability: For any two transactions, it should be impossible to deduce that they were sent to the same recipient. 2. Untraceability: Given a transaction input, the real output being redeemed in it should be anonymous among a set of other outputs. Fig. 1. A schematic representation of a simplified Monero non-RingCT transaction.
Is Monero a privacy-centric cryptocurrency?
Monero is a privacy-centric cryptocurrency that allows users to obscure their transactions by including chaff coins, called "mixins," along with the actual coins they spend. In this paper, we empirically evaluate two weaknesses in Monero's mixin sampling strategy.
What is the untraceability guarantee in Monero?
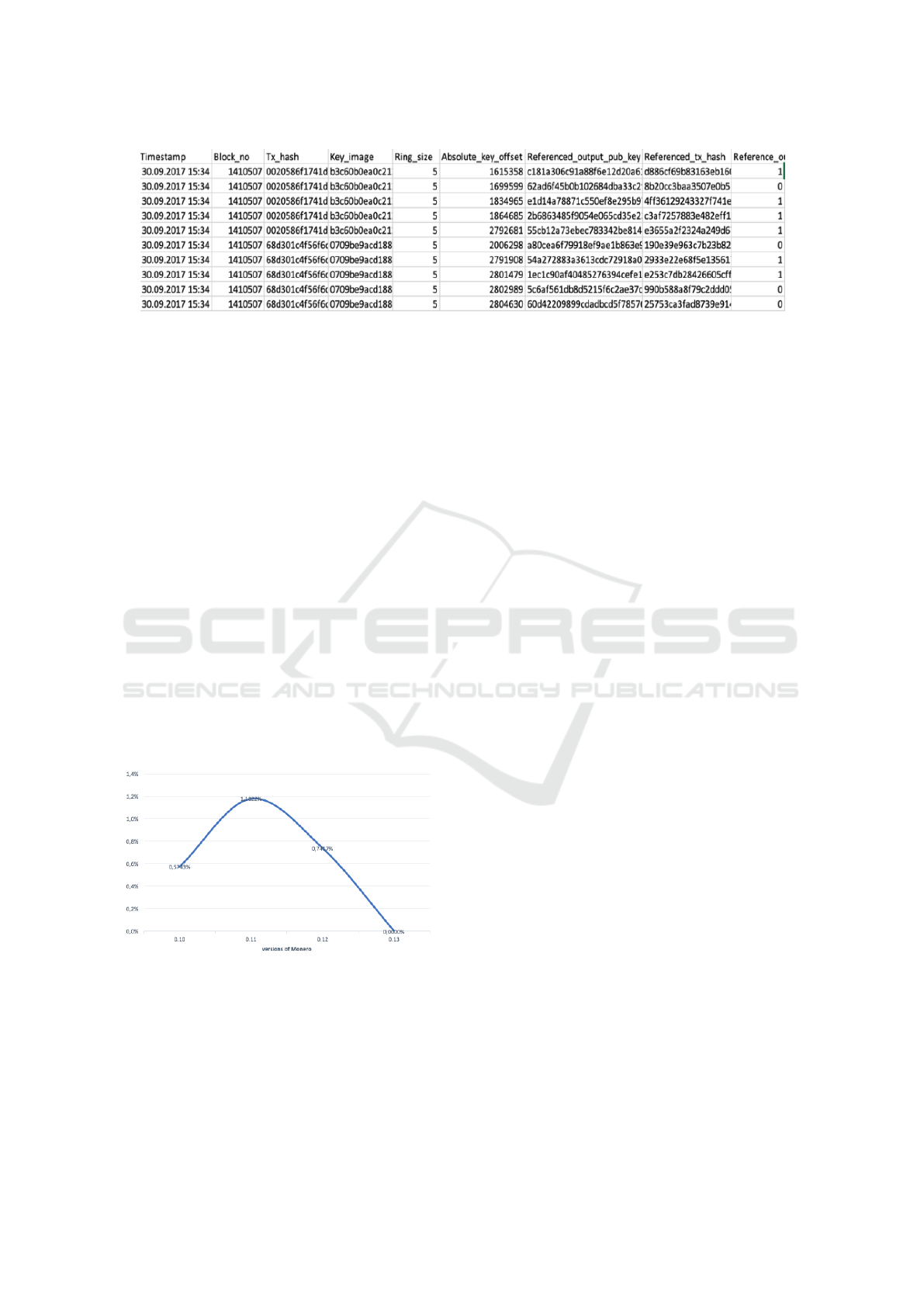
The untraceability guarantee in Monero relies on the assumption that it is hard for an adversary to distinguish a spent TXO from an unspent TXO. In the next section, we develop three heuristics that allow us to test this hypothesis and reduce the anonymity-set size for an input.
Can Monero transactions be traceable?
We formalize a new method for tracing Monero transactions, which is based on analyzing currency hard forks. We use that method to perform a (passive) traceability analysis on data from the Monero, MoneroV and Monero Original blockchains and find that only a small amount of inputs are traceable.
Brute-Force Attack
Brute-force attack is an attack that tries all possible sequence of distinct public-keys to test whether it is valid for the assignments of the real-spends for all transaction inputs. While a sequence of public-keys is valid if it satisfies requirements: (1) the size of the sequence equals to the number of total transaction inputs in the dataset; (
Our Attack
Although the aforementioned brute-force attack is perfect, the complexity is prohibitively high in practice, which is \\(\\mathcal {O}(n)\\). Considering the inefficiency and impracticability of brute-force attack, we propose a new attack called \\(\\textit{closed set}\\), which is more efficient while providing the same result. The proposed \\(\\textit{c
Theorem 1
The aforementioned \\(\\textit{closed set}\\)attack is equivalent to brute-force attack. In other words, for any set of transactions, the impact of our attack on it is identical to the impact of brute-force attack. Due to space limitation, we refer readers to the full version of this paper for the proof of this theorem. link.springer.com
on The Existence of Closed Set: A Theoretical Perspective
As mentioned before, the \\(\\textit{closed set}\\) attack is optimal. This is to say, we can conclude that anonymity of inputs cannot be reduced if no \\(\\textit{closed set}\\) exists. In this section, we estimate the probability that there exists at least one \\(\\textit{closed set}\\)in an ideal scenario, namely, all inputs have a (small) constant numbe
Lemma 2
With all but a small probability \\(2^{-19}\\), there does not exist any closed set in the above dataset if all inputs have 3 mixins and all mixins are sampled uniformly from all keys. The proof of this lemma is given in the full version of this paper. link.springer.com
|
An Empirical Analysis of Traceability in the Monero Blockchain
In the Cryptonote protocol (b) each transaction input identifies a set of coins |
|
An Empirical Analysis of Traceability in the Monero Blockchain
Abstract: Monero is a privacy-centric cryptocurrency that allows users to obscure their transactions by includ- ing chaff coins called “mixins |
|
An Empirical Analysis of Traceability in the Monero Blockchain
Kyle Hogan Jason Hennessey |
|
Short paper: An Empirical Analysis of Monero Cross-Chain
(passive) traceability analysis on data from the Monero MoneroV and An Empirical Analysis of Traceability in the Monero Blockchain. |
|
An Empirical Analysis of Monero Cross-Chain Traceability
4 janv. 2019 0:{b c}. 1:{b c}. 2:{a b c}. 3:{a d e f}. 4:{v w x}. 4:{x y z }. 3:{a e f g} ... Fig. 2: An illustration of the Monero blockchain(. XMR. ) and a ... |
|
Practical Analysis of Traceability Problem in Moneros Blockchain
Abstract: This paper presents an analysis of the cryptocurrency security based on the traceability problem in the Monero. Blockchain. |
|
An Empirical Analysis of Traceability in the Monero Blockchain
An Empirical Analysis of Traceability in the. Monero Blockchain. Abstract: Monero is a privacy-centric cryptocurrency that allows users to obscure their |
|
New Empirical Traceability Analysis of CryptoNote-Style Blockchains
13 août 2018 Abstract. The cascade effect attacks (PETS' 18) on the untraceability of Monero are circumvented by two approaches. The first one is to in-. |
|
A Traceability Analysis of Moneros Blockchain
17 avr. 2017 The signer is hence anonymous in the ring that forms its anonymity-set. In order to see how Monero employs ring signatures let us consider an ... |
|
On Defeating Graph Analysis of Anonymous Transactions
11 avr. 2022 Since efficient graph analysis could be performed on transaction ... “An Empirical Analysis of Traceability in the Monero Blockchain”. In:. |
|
An Empirical Analysis of Linkability in the Monero Blockchain
13 avr 2017 · The Monero software allows users to configure the de- fault number of mixins to include in each transaction Most Monero transaction inputs ( |
|
An Empirical Analysis of Monero Cross-Chain Traceability
(passive) traceability analysis on data from the Monero, MoneroV and Monero Original blockchains and find that only a small amount of inputs are traceable |
|
A Traceability Analysis of Moneros Blockchain - NUS Computing
To this end, we develop three attack routines and evaluate them on the Monero blockchain data Monero designers and developers are aware of the theoretical |
|
A Traceability Analysis of Moneros Blockchain - Cryptology ePrint
17 avr 2017 · It is important to note that Monero designers and developers are aware of the theoretical possibility of our attacks [9] and have put in place some |
|
Alt-Coin Traceability
18 mai 2020 · Zero mixin chain analysis: Start with transactions that use zero mixins, where the empirical analysis of traceability in the monero blockchain” |
|
Practical Analysis of Traceability Problem in Moneros Blockchain
The analysis of the existing sizes of ”Ring Signature” in transactions in subsequent versions of the Monero network has proven that the minimum required size for a |
|
Monero Cross-Chain Traceability - reposiTUm - TU Wien
II Empirical Analysis of Monero Traceability 33 6 Monero then, Blockchain analysis techniques such as the multiple input heuristic and change heuristics |
|
Slides - Malte Möser
26 fév 2019 · Based on An Empirical Analysis of Traceability in the Monero Blockchain, joint work with Kyle Soska, Ethan Heilman, Kevin Lee, Henry Heffan, |
|
Monero Cross-Chain Traceability - TU Wien
19 sept 2018 · Contents xiii I Cryptocurrency Analytics: Theoretical Background 1 1 Introduction II Empirical Analysis of Monero Traceability 33 6 Monero |
![PDF] An Empirical Analysis of Linkability in the Monero Blockchain PDF] An Empirical Analysis of Linkability in the Monero Blockchain](https://d3i71xaburhd42.cloudfront.net/1b5b3717d32027c3583c535932da3a8d7e1b6c6f/2-Figure2-1.png)
![PDF] An Empirical Analysis of Linkability in the Monero Blockchain PDF] An Empirical Analysis of Linkability in the Monero Blockchain](https://d3i71xaburhd42.cloudfront.net/1b5b3717d32027c3583c535932da3a8d7e1b6c6f/5-Figure3-1.png)
![PDF] An Empirical Analysis of Linkability in the Monero Blockchain PDF] An Empirical Analysis of Linkability in the Monero Blockchain](https://d3i71xaburhd42.cloudfront.net/1b5b3717d32027c3583c535932da3a8d7e1b6c6f/7-Table2-1.png)
![PDF] An Empirical Analysis of Linkability in the Monero Blockchain PDF] An Empirical Analysis of Linkability in the Monero Blockchain](https://i1.rgstatic.net/publication/341724427_Blockchain_is_Watching_You_Profiling_and_Deanonymizing_Ethereum_Users/links/5f86a96da6fdccfd7b5fc8c8/largepreview.png)








![PDF] New Empirical Traceability Analysis of CryptoNote-Style PDF] New Empirical Traceability Analysis of CryptoNote-Style](https://i1.rgstatic.net/publication/328571978_Monero_Cross-Chain_Traceability/links/5bd626ca4585150b2b8d5fcc/largepreview.png)
