Kerberos: authentification unique - France
|
Authentification unique (SSO) - Evidian
Sommaire Qu'est-ce que l'authentification unique ? L'authentification unique ( en anglais single sign-on ou SSO) permet à Avec des « jetons virtuels » de type Kerberos Cartes de santé CPS (France), NHS (UK) ou UZI-pas (Pays-Bas) |
|
Kerberos et interopérabilité - JRES
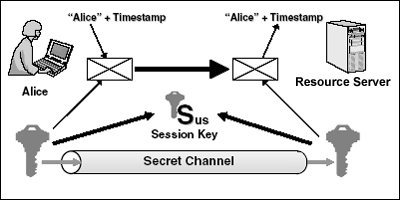
24 mai 2010 · INRIA Saclay - Ile de France Mardi 24 mai Kerberos est un protocole d' authentification, sécurisé, de type SSO Kerberos royaume unique |
|
(Single Sign On) avec EIM - No Slide Title
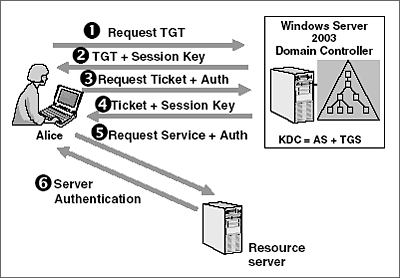
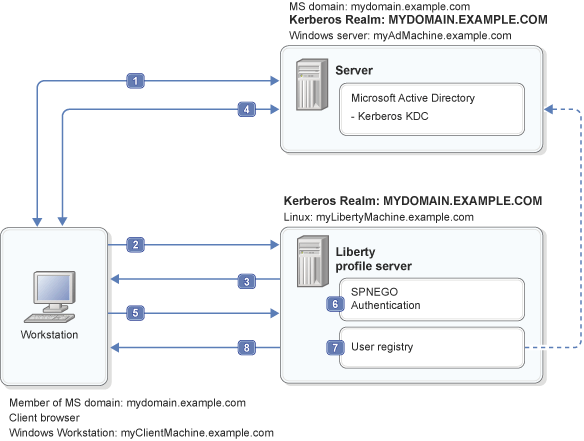
14 mai 2014 · IBM France 2014 IBM Power Systems - IBM i base d'une authentification unique effectuée lors de l'accès initial au réseau Authentification avec Kerberos (Network Authentication Service) – Autorisation avec EIM |
|
La Sécurité des Réseaux Informatique à Base de Kerberospdf
28 III 11 Authentification de Kerberos avec Active Directory Pour contrôler notre domaine avec l'utilisation unique de Kerberos, on choisit le type |
|
Guide de configuration de Dell EMC BoostFS - Dell Technologies
EMC Computer Systems France River Ouest 80 quai BoostFS prend en charge les systèmes Data Domain à nœud unique, ainsi que les systèmes haute authentication kerberos set realm kdc-type windows Vous devriez voir le |
|
EMC® Data Domain® BoostFS - Dell Technologies
EMC Computer Systems France River Ouest 80 quai BoostFS prend en charge les systèmes Data Domain à nœud unique, ainsi que les systèmes BoostFS prend en charge l'authentification Kerberos, qui offre des avantages importants |
|
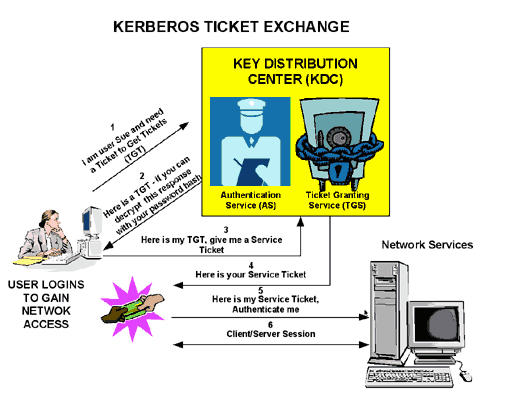
Kerberos et la Sécurité - Actes du SSTIC
Applications Militaires BP 12, 91680 Bruy`eres-le-Chatel, France d'hui, Kerberos est un protocole d'authentification réseau La version envoyé avec la premi`ere requête n'est l`a que pour rendre unique cette requête et sa réponse pour |
|
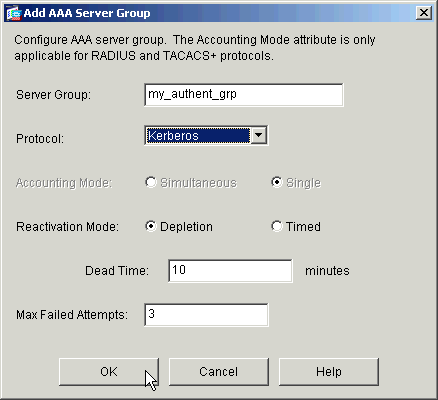
Rapport de certification ANSSI-CSPN-2018/01 Evidian - lANSSI
16 fév 2018 · Identification, authentification et contrôle d'accès 78180 Montigny le Bretonneux, France SSO (Single Sign-On) est un système d'authentification unique Il d'authentification au service KERBEROS Active Directory ; |
|
Cible de sécurité Enterprise SSO v806
24 jan 2017 · 75700 PARIS 07 SP France Emetteur Evidian : Les trois types d'architectures d'un système d'authentification unique sont: • Serveur de SSO d' authentification au service KERBEROS de l'Active Directory ; 2 le service |


![PDF] Cours Sécurité des réseaux Authentification avec Kerberos PDF] Cours Sécurité des réseaux Authentification avec Kerberos](https://upload.wikimedia.org/wikipedia/commons/thumb/b/b5/Kerberos-ruggiero.svg/1200px-Kerberos-ruggiero.svg.png)