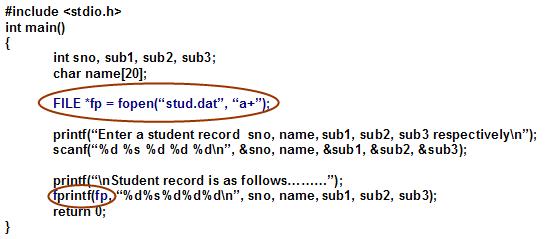
fopen vulnerability php
1.
1.
1`r`: Read-only mode.
Starts at the beginning of the file.2`r+`: Read and write mode.
Starts at the beginning of the file.3`w`: Write-only mode. 4`w+`: Read and write mode. 5`a`: Write-only mode. 6`a+`: Read and write mode.
What is fopen () in PHP?
The fopen() function opens a file or URL.
Note: When writing to a text file, be sure to use the correct line-ending character
Which PHP function is used to open a file?
PHP Open File - fopen()
A better method to open files is with the fopen() function.
What is the difference between fread and fopen in PHP?
The fopen() is a function in PHP, which is used to open a file.
This function is better than read file() to handle the file operations.
The fread() function reads from an open file.
The fread() function halts at the end of the file or when it reaches the specified length which ever comes first.
|
File Operation Induced Unserialization via the “phar://” Stream
30 juil. 2018 "PHP comes with many built-in wrappers for various URL-style protocols for use with the filesystem functions such as fopen() copy() |
|
A SOLUTION TO PHP CODE INJECTION ATTACKS AND WEB
For every three years OWASP rewrites the most common web application security vulnerabilities. Web applications are frequently deployed with the critical |
|
Saphire: Sandboxing PHP Applications with Tailored System Call
known vulnerable web apps and plugins shows that Saphire ple PHP's fopen() |
|
Efficient and Flexible Discovery of PHP Application Vulnerabilities
of PHP vulnerabilities in Web applications. fopen. Based on the applications and the access mode used in this call an attacker can therefore either ... |
|
Webhacking: les failles php.pdf
Le serveur de test est un serveur Apache (php 5.0.4) – MYSQL (4.1.12) tournant sur Win2000 Server. Directives php spécialles: $fp=fopen("index.php"w+);. |
|
Using honeypots to study skill level of attackers based on the
10 oct. 2001 the exploited vulnerabilities in the network ... FTP MYSQL |
|
Practical PHP Security
The fopen() binds a name resource specified by filename to a stream Bypassing authentication mechanism via SQL injection vulnerability. |
|
Hacking Web Sites Insecure Direct Object Reference
For instance http://mysite.com/program.php?page=124 http://www.mysite.com/index.php?viewaccount=23456 ... Presentation of the Vulnerability. |
|
Queens Secure PHP Development Handbook Table of Contents
Security Vulnerabilities o CSRF (Cross Site Request Forgeries) Attacks. ? Description. ? Example. ? Prevention o Remote Code Execution. ? Description. |
|
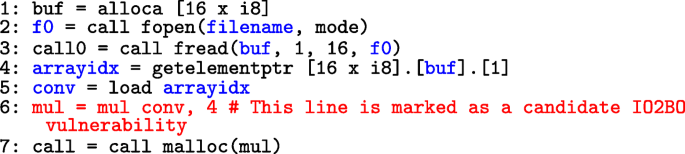
Cefuzz: An Directed Fuzzing Framework for PHP RCE Vulnerability
1 mar. 2022 PHP RCE vulnerabilities. ... (3) A PHP RCE vulnerability directed fuzzing prototype system ... if(@$fp = fopen($filename $openmod)). |
|
PHP unserialization vulnerability - HubSpot
30 juil 2018 · functions such as fopen(), copy(), file_exists() and filesize() "[4] The "php://" wrapper has previously been used in XXE, local file inclusion and |
|
SECURITY VULNERABILITIES IN PHP APPLICATONS
PHP in-built function file_get_contents is used to reads entire file into a string For example following php code will open a file with fopen() and then echo the |
|
A SOLUTION TO PHP CODE INJECTION ATTACKS AND WEB
paper is first to understand the code web application vulnerability related to PHP PHP has a built function fwrite(), this function is used to write the file contents |
|
A New Source Code Auditing Algorithm for Detecting LFI - Root Me
number of security vulnerabilities in PHP scripts, but has a Fopen() - File_get_contents() - For instance, in many situations it would be great to use dynamic |
|
Assault on PHP Applications
13 jui 2009 · Real world examples of vulnerabilities in PHP software are also shown to is an option in PHP (php ini) that allows functions such as fopen(), |
|
PHP Fuzzing In Action - Exploit Database
When we talk about PHP Vulnerability discovery, we forget this Question: file_get_contents fopen file In a general , each "Filesystem Functions" in PHP may |
|
Efficient and Flexible Discovery of PHP Application Vulnerabilities
EVALUATION FOR FOPEN of several AST nodes in order to identify the calls to this function There is no universal sanitizer for the eval |
|
“Its a PHP unserialization vulnerability Jim, but not as we - Black Hat
Exploit vulnerabilities in native code? file:// http:// ftp:// php:// zlib:// data:// glob:// phar:// Remote Input Filtering |


![PDF] Vulnerability analysis of desktop 3D printer software PDF] Vulnerability analysis of desktop 3D printer software](https://i1.rgstatic.net/publication/294086432_Toward_Large-Scale_Vulnerability_Discovery_using_Machine_Learning/links/5afad4460f7e9b3b0bf086d4/largepreview.png)











![PDF] Using a Web Server Test Bed to Analyze the Limitations of Web PDF] Using a Web Server Test Bed to Analyze the Limitations of Web](https://i.ytimg.com/vi/8YXTZXbOlGk/mqdefault.jpg)


![PDF] Detection of vulnerabilities and automatic protection for web PDF] Detection of vulnerabilities and automatic protection for web](https://vk9-sec.com/wp-content/uploads/2021/01/word-image-26.png)

![Top PDF Bypass DEP By Using ROP and ASLR [Kancho] pdf - 1Library Top PDF Bypass DEP By Using ROP and ASLR [Kancho] pdf - 1Library](http://blog.clever-age.com/wp-content/uploads/2014/00/png/image01-3.png)






![Top PDF Bypass DEP By Using ROP and ASLR [Kancho] pdf - 1Library Top PDF Bypass DEP By Using ROP and ASLR [Kancho] pdf - 1Library](https://www.howtoforge.com/images/c_cplusplus_tutorial/18_files.jpg)