google cloud intrusion detection
How intrusions are detected in cloud?
At a high level, cloud intrusion detection works much the same as on-premises intrusion detection – by monitoring system activity and analyzing patterns to identify malicious activity.
Cloud IDS provides network threat detection warnings at varying threat severity levels: Critical, High, Medium, Low, and Informational to help you prioritize the most important threats.
What is the intrusion prevention system in Google cloud?
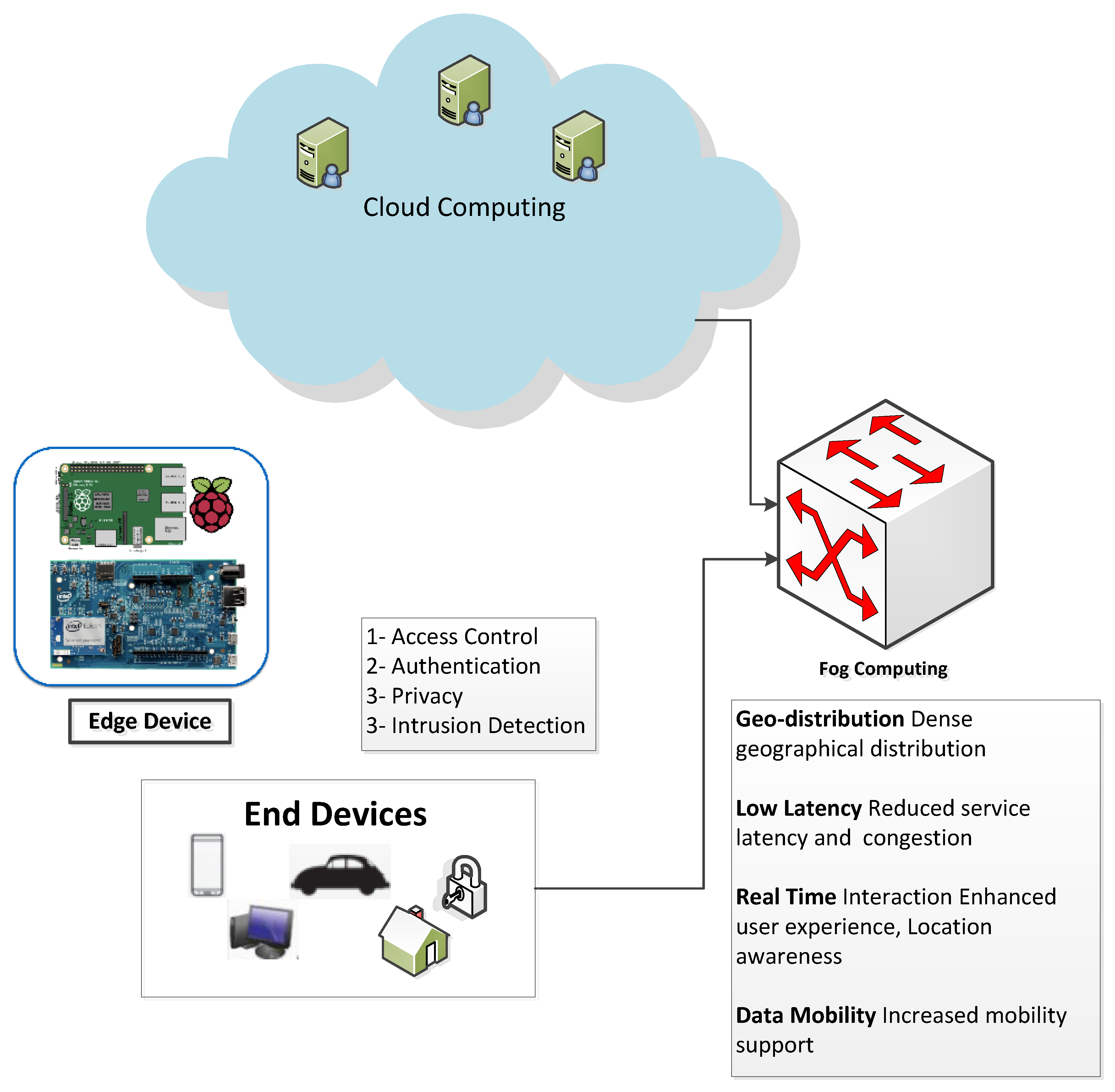
Cloud IDS (Cloud Intrusion Detection System) detects malware, spyware, command-and-control attacks, and other network-based threats.
Its security efficacy is industry leading, built with Palo Alto Networks technologies.
What is the cloud native intrusion detection system provided by Google cloud called?
Cloud IDS is an intrusion detection service that provides threat detection for intrusions, malware, spyware, and command-and-control attacks on your network.
Cloud IDS works by creating a Google-managed peered network with mirrored virtual machine (VM) instances.
|
SCADS: A Scalable Approach Using Spark in Cloud for Host-based
7 janv. 2022 intrusion detection systems deployed on every single host to collect maintain |
|
Securing Cloud Containers through Intrusion Detection and
1 août 2017 Many intrusion detection systems have been introduced to cloud ... Examples include Amazon EC2 Container Service (ECS) Google Kubernetes |
|
Enhancing Data Security in the User Layer of Mobile Cloud
Cloud Intrusion Detection and Prevention System) combines a host-based IDS and successfully to the Google play store despite the protection. |
|
Intrusion Detection Systems in Cloud Computing: A Contemporary
It offers three service models of software as a service (e.g. Google Apps [1]) platform as a service (e.g. Google App Engine [2] |
|
Intrusion Detection System for Cloud Based Software-Defined
OpenDaylight software as an SDN controller hosted at a Google cloud. The proposed IDS uses a GridSearch technique with Support Vector Machine (SVM) to |
|
LAN Intrusion Detection Using Convolutional Neural Networks
30 juin 2022 The suggested approach is analysis using the public dataset CIDDS-001 in a series of experiments on the. Google Cloud Platform. Compared with ... |
|
Distributed Intrusion Detection System for Cloud Environments
final multi-class classification step in order to detect the type of each attack. Various experiment are performed in the Google Cloud Platform in order to |
|
Overview - Snort Intrusion Detection System in Cloud Environment
and application in cloud, we have to develop a new cloud IDS model Keywords : Cloud computing, Snort IDS, Virtualization 1 Ex- Google App Engine |
|
VSRX Virtual Firewall for Google Cloud Platform - Juniper Networks
generation firewall (NGFW) security that includes intrusion prevention system ( IPS), malware protection, app control, and on-demand threat detection The vSRX |
|
Check Point CloudGuard for Google Cloud Platform - Solution Brief
As a Google technology partner, CloudGuard compliments Google Cloud Platform security controls Firewall, Intrusion Prevention System (IPS), Antivirus , and |
|
Security Whitepaper - C2FO
Google Cloud Platform (GCP) Compliance and Infrastructure Intrusion Prevention System (IPS) intrusion detection systems, and other electronic means |