security zone design
What are the different types of security zones?
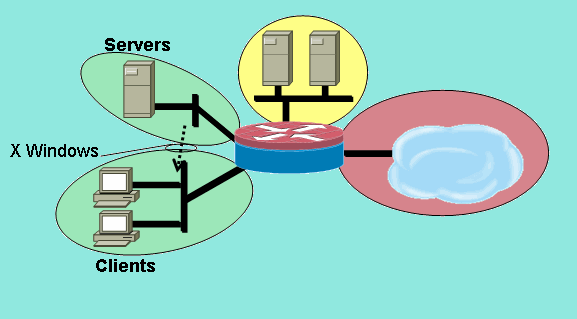
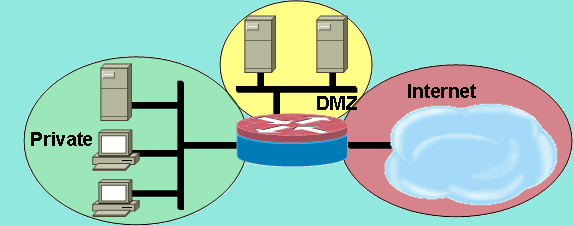
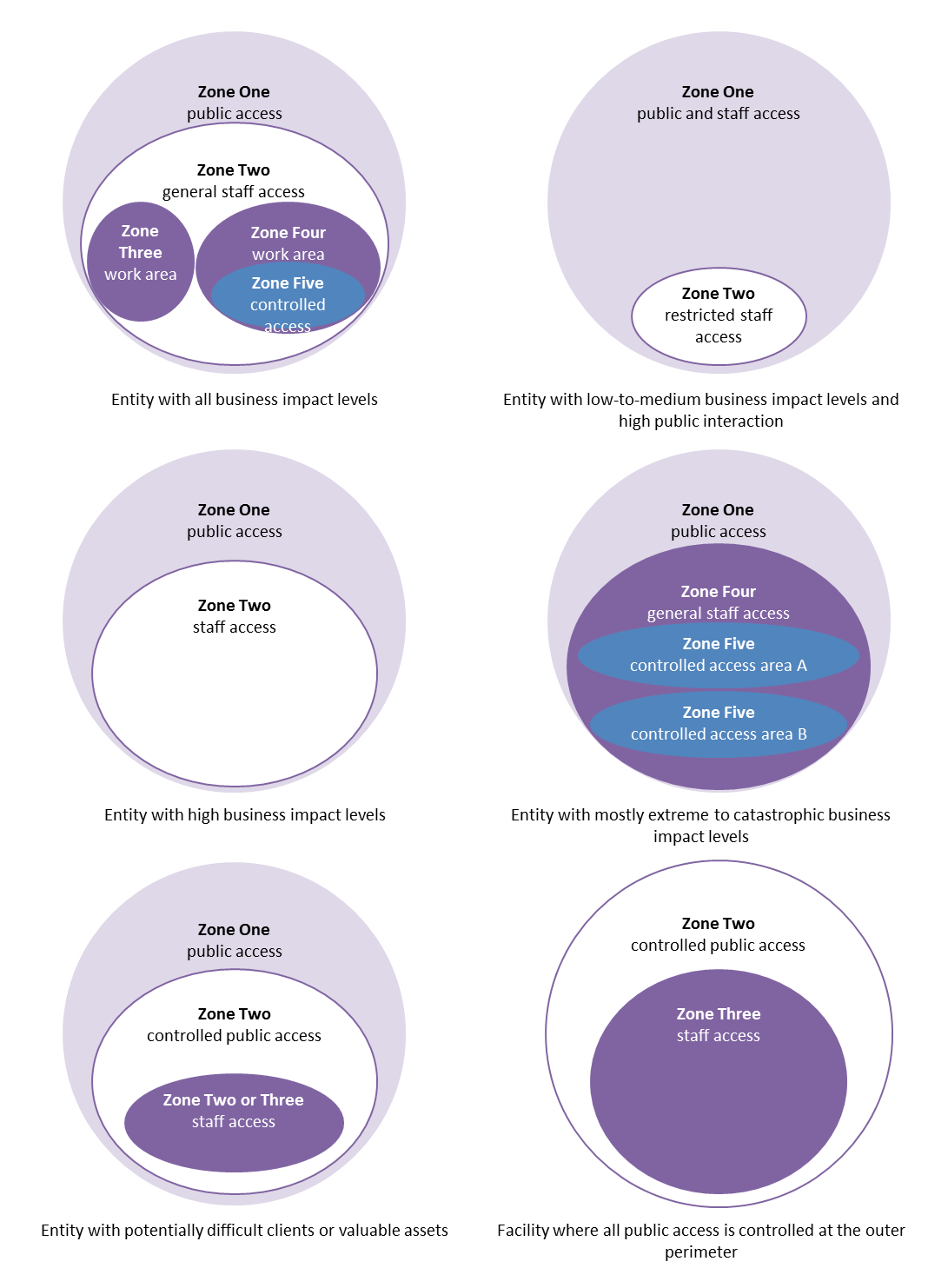
Security zones are isolated by default. Generally, there are three types of security zones: trusted, DMZ, and untrusted. Trusted zone: refers to the network of internal users. DMZ: demilitarized zone, which refers to the network of internal servers. Untrusted zone: refers to untrusted networks, such as the Internet.
What is the Cisco Design zone for security?
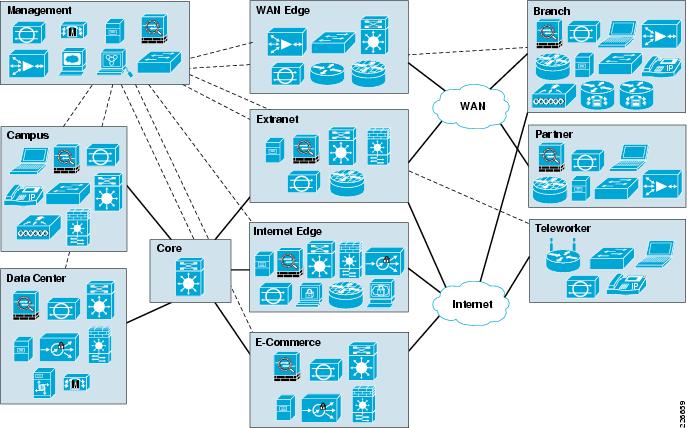
The Cisco Design Zone for security can help you simplify your security strategy and deployment. Find implementation guidance for secure access service edge (SASE), zero trust, remote work, breach defense, and other security architectures. Access best practices, step-by-step design guides, toolkits, related resources, and more.
What is a security zone interface?
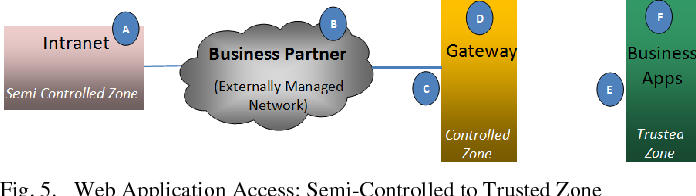
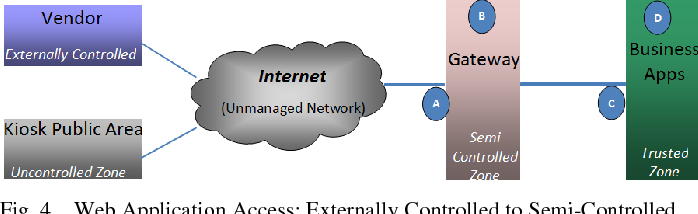
An interface for a security zone can be thought of as a doorway through which TCP/IP traffic can pass between that zone and any other zone. Through the policies you define, you can permit traffic between zones to flow in one direction or in both.
How do I configure a security zone?
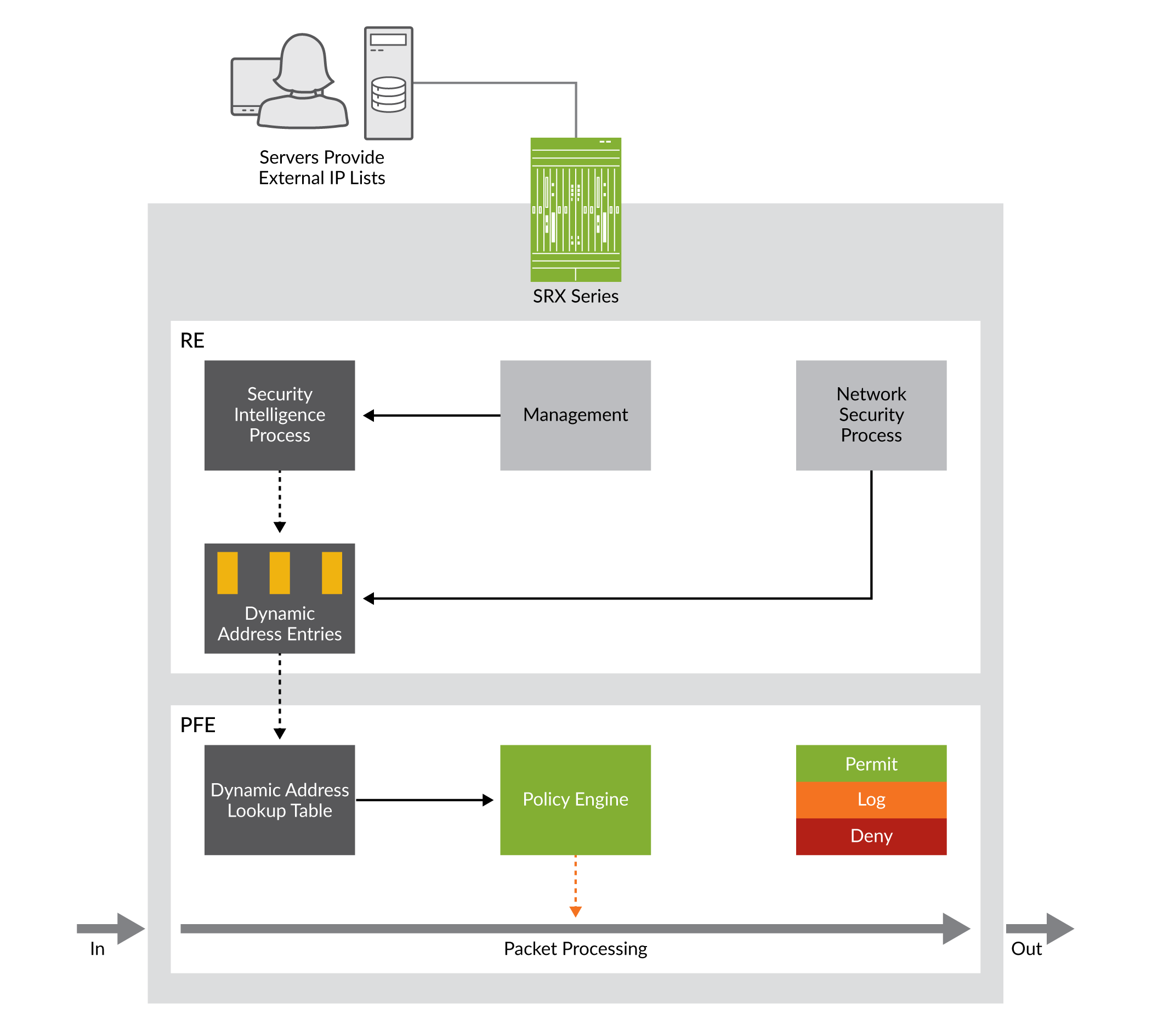
Configure the TCP-Reset parameter for the zone. If you are done configuring the device, commit the configuration. To verify the configuration is working properly, enter the show security zones command. A security zone is a collection of one or more network segments requiring the regulation of inbound and outbound traffic through policies.

Lesson 3: Common Mistakes and Best Practices for Designing Network Security Zones

Firewall Security Zones – Zone based Policy Firewall ZPF

Oracle Cloud Infrastructure Security Zones: Overview
|
Security Zone Infrastructure for Network Security Intelligence Centers
research on designing NSICs [2 3] |
|
Securely Traversing IACS Data Across the IDMZ Design and
CPwE IDMZ Overview. Overview of CPwE IDMZ including discussion of Holistic Industrial Security |
|
Secure Cloud for Azure (IaaS) - Design Guide - Cisco
This design guide aligns with the Cisco® Secure Cloud Architecture guide. Management zone is segmented using Azure Network Security Groups. |
|
Building a Scalable and Secure Multi-VPC AWS Network Infrastructure
10-Jun-2020 management (IAM) governance |
|
Secure Remote Worker - Design Guide - Cisco
The design for remote access VPN connections includes Cisco AnyConnect Secure Mobility Client Cisco Duo |
|
Secure Cloud for AWS (IaaS) - Design Guide - Cisco
Secure Cloud for AWS (IaaS) Design Guide. DevOps remotely accessing the management zone for workload management/update/patching purposes ... |
|
Networking and Security in Industrial Automation Environments
Safety Zone—Safety in the Industrial Automation Control System . Industrial Networking and Security Design for the Cell/Area Zone . |
|
A Logic-Based Network Security Zone Modelling Methodology
network security requirements is driven by security zoning a well-known defense in depth strategy for network security design [1]. Security zones |
|
IAEA Nuclear Energy Series Computer Security Aspects of Design
Systems at Nuclear Facilities which focuses on computer security design Other key concepts described are computer security levels |
|
AWS Security Best Practices
Systems can span multiple Availability Zones and we recommend that you design your systems to survive temporary or prolonged failure of an Availability Zone in |
|
A Logic-Based Network Security Zone Modelling - ThinkMind
network security requirements is driven by security zoning, a well-known defense in depth strategy for network security design [1] Security zones constitute the |
|
The Fundamentals of Network Security Design - Neon Knight
A bad idea 27 Virtual Desktop Infrastructure 29 ZONED SECURITY ARCHITECTURE DESIGN 30 Understanding the Traffic 31 Zone based Firewall Policy |
|
The Principles of Network Security Design - AMAN System
When designing the network security system, the following fundamental IT systems infrastructure into security zones and controlling commu- nication between |
|
Security standard SS-018: Network Security Design - Govuk
14 jan 2019 · networks (e g , the Internet) MUST be located in different zones (De-Militarized Zone – DMZ) than internal network devices and computer systems |
|
Network Security Design for Manufacturing - Atlantis Press
That is divides enterprise's network into three zones: Internet zone, office zone, and production zone; Next, introduces the security design method for each zone |
|
SAFE Secure Data Center Architecture Guide - Cisco
1 avr 2018 · Places in the Network: Secure Data Center Contents by applications, zones, and other methods available on Cisco Design Zone |
|
SAFE Overview Guide - Cisco
Cisco Validated Designs address critical security Using the security architecture, a specific design is created large number of security zones ( subnets and |







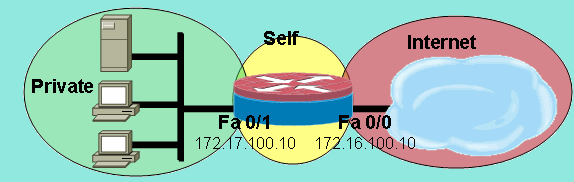
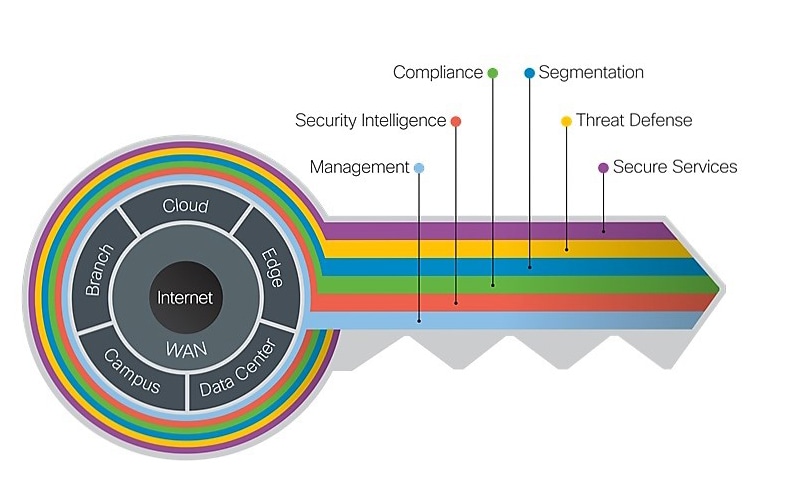
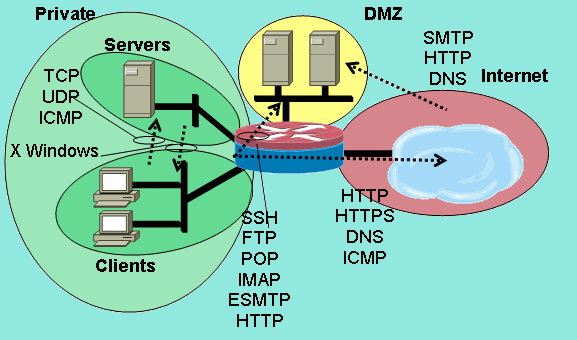
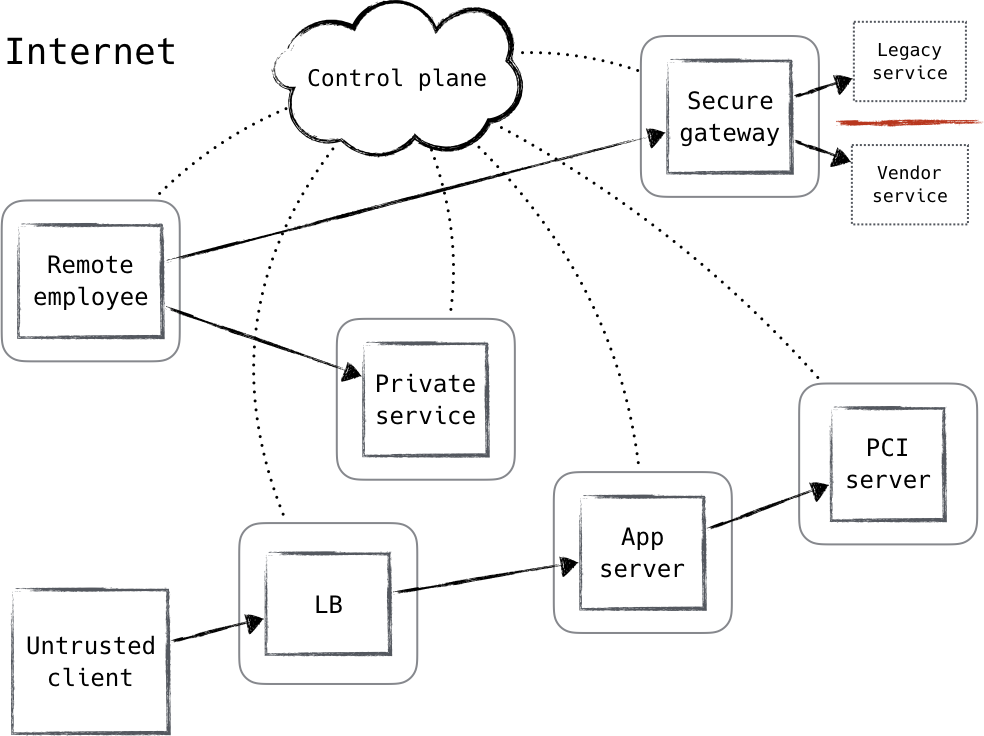
![1 Zero Trust Fundamentals - Zero Trust Networks [Book] 1 Zero Trust Fundamentals - Zero Trust Networks [Book]](https://www.cisco.com/c/dam/en/us/td/i/200001-300000/220001-230000/226001-227000/226757.eps/_jcr_content/renditions/226757.jpg)















![PDF] DeMilitarized Zone: Network Architecture for Information PDF] DeMilitarized Zone: Network Architecture for Information](https://d1.awsstatic.com/Marketplace/scenarios/bi/AWSMPSEC01.46fc03f9e877c3a491eaf6ad163db5d5a55a20ce.png)

![PDF] DeMilitarized Zone: Network Architecture for Information PDF] DeMilitarized Zone: Network Architecture for Information](https://www.oreilly.com/library/view/zero-trust-networks/9781491962183/assets/ztnw_0101.png)