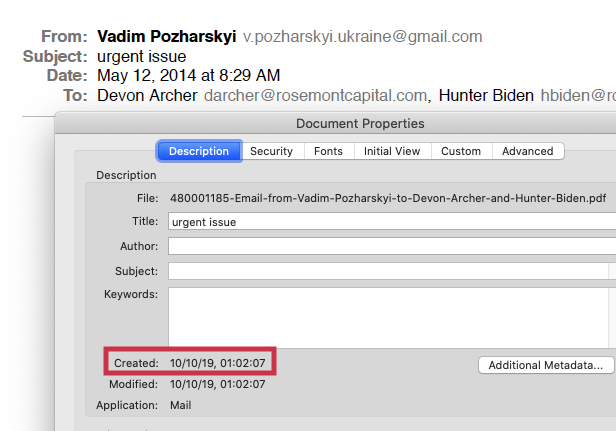
apple law enforcement email contact
|
Legal Process Guidelines
Apple provides responses to the requesting law enforcement agency at the official law enforcement email address of the requesting officer All evidence preservation pursuant to the responses provided by Apple is the responsibility of the requesting law enforcement agency INDEX I General Information II Legal Requests to Apple |
| Legal Process Guidelines |
How do I contact Apple for an emergency inquiry?
If a government or law enforcement agency needs to reach Apple for an emergency inquiry, please contact Apple’s Global Security Operations Center (GSOC) at 001 408 974-2095. This phone number offers language support for multiple languages.
How do I contact Apple support?
For support inquiries, including product related inquiries, issues with your Apple ID, password resets, security and phishing and more, please contact Apple Support (click on Billing & Subscriptions for Apple ID, password, security & phishing issues). Learn about Apple’s idea submission policy.
Does Apple accept government or law enforcement information requests?
II. Apple accepts service of legally valid government or law enforcement information requests by email from government and law enforcement agencies, provided these are transmitted from the official email address of the requesting government or law enforcement agency.
|
Legal Process Guidelines – Apple
If you choose to send an email to this address it must be from a valid and official government or law enforcement email address. Subpoenas |
|
Government / Law Enforcement Information Request - Apple Legal
Apple's Legal Process Guidelines for Government &Law Enforcement outside the United States Official Government or Law Enforcement Email Address:. |
|
France - EMERGENCY Government / Law Enforcement Information
or law enforcement email address to the mailbox: exigent@apple.com with the subject line: “Emergency. Request”. Demande d'informations URGENTE pour une |
|
Legal Process Guidelines - Apple
choose to send an email to this mailbox it should be from a valid and official government or law enforcement email address. Legal requests to Apple should |
|
Law-enforcement-guidelines-emeia.pdf
8 juin 2017 an official government or law enforcement email address to the mailbox: apac_police_requests@apple.com. EMEIA (Europe Middle-East |
|
English - EMERGENCY Government / Law Enforcement Information
or law enforcement email address to the mailbox: exigent@apple.com with the subject line: “Emergency. Request”. Government or Law. Enforcement Agency. |
|
Government/Law Enforcement Information Request Demande d
received from the requesting officer's official government or law enforcement email address. Demande d'informations des autorités chargées de l'application |
|
Apple Privacy
This email address is intended solely for use by law enforcement and government agents. If you choose to send an email to this address it must be from a valid |
|
Outside US Guidelines June 2017 (3) 2017.06.23
23 juin 2017 enforcement email address to the mailbox: lawenforcement@apple.com. APAC (Asia Pacific). Government and law enforcement agencies in the Asia ... |
|
Legal-process-guidelines-apac.pdf
Law enforcement agents in Japan and APAC submitting a legal request to Apple should transmit it directly from their verified law enforcement email address to:. |
|
Government / Law Enforcement Information Request - Apple
Agency Name: Requesting Officer Name Title/Rank: Official Government or Law Enforcement Email Address: Phone: Case Context Case Date Location: |
|
Legal Process Guidelines - Apple
Apple accepts service of legally valid government or law enforcement information requests by email from government and law enforcement agencies, provided |
|
Government/Law Enforcement Information Request - Apple
received from the requesting officer's official government or law enforcement email address Demande d'informations des autorités chargées de l'application de |
|
US LE Guidelines_FINAL_20150916pages - Apple
Law enforcement officers submitting a legal request to Apple should transmit it directly from their official law enforcement email address to the mailbox subpoenas |
|
APAC LE Guidelines for Localizationpages - Apple
enforcement email address Law enforcement agents in Japan and APAC submitting a legal request to Apple should transmit it directly from their verified law |
|
Government / Law Enforcement Information Request - Apple
from the requesting officer's official government or law enforcement email address Solicitud de información de agencias gubernamentales y autoridades |
|
Government / Law Enforcement Information Request - Apple
Beamter Name Title/Rank / Name und Titel/Dienstgrad: Official Government or Law Enforcement Email Address / Offizielle E-Mail-Adresse der Dienststelle: |




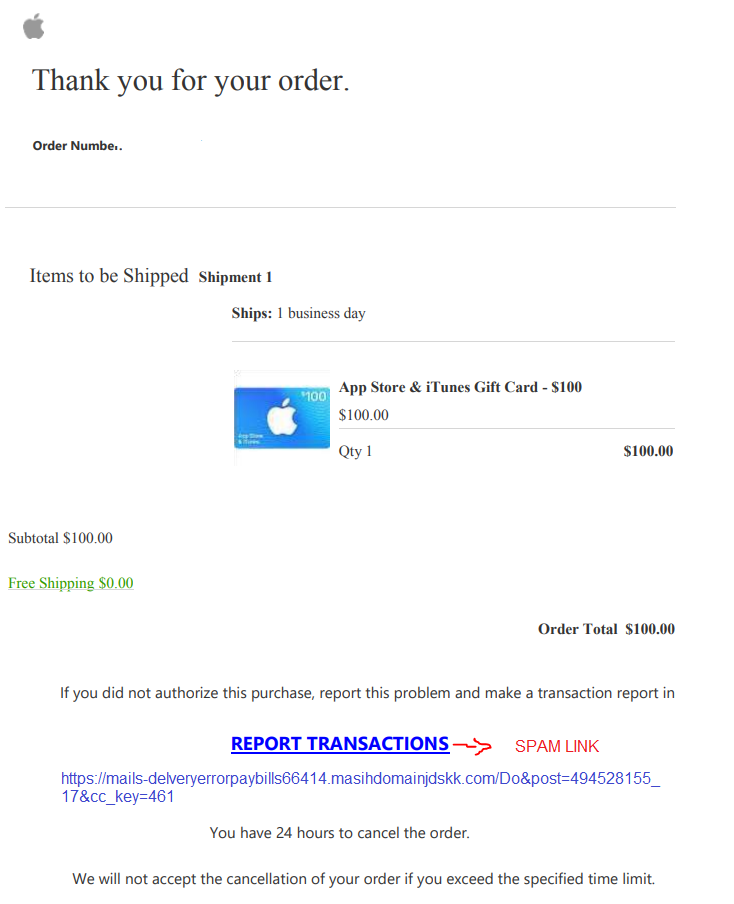


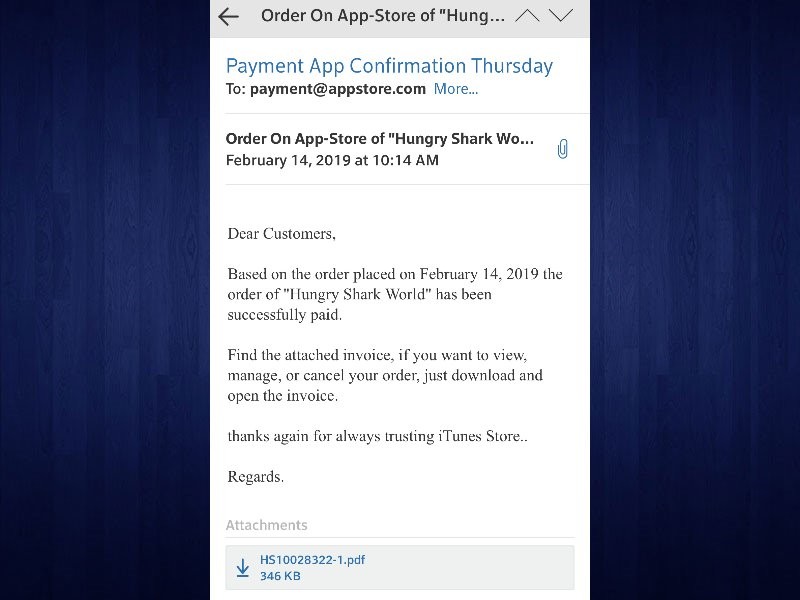


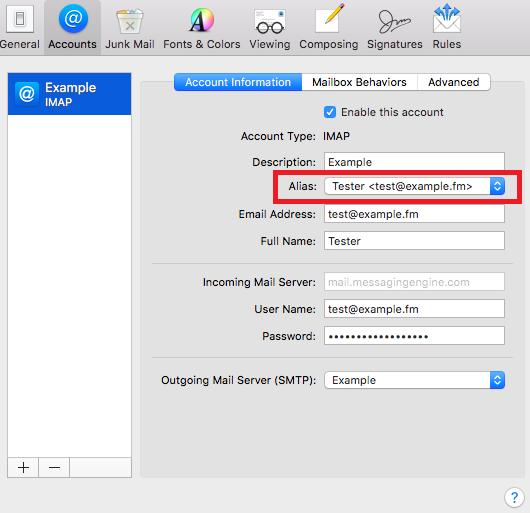




/article-new/2020/07/apple_bitcoin_hack.jpg?lossy)










/article-new/2020/10/magsafe1.jpg?lossy)