a method for identifying phantom employees is
How do you audit fictitious employees?
How to detect ghost employees
1Run third-party audits.
Partnering with third-party auditors can save thousands of dollars in theft for companies with in-house payroll systems.
2) Investigate employees with low or no tax deductions.
3) Review canceled checks.
4) Examine Social Security numbers.Which of the following is a way to detect phantom employees?
Regularly check payroll records and look for things such as duplicate names, addresses, bank accounts, and Social Security numbers.
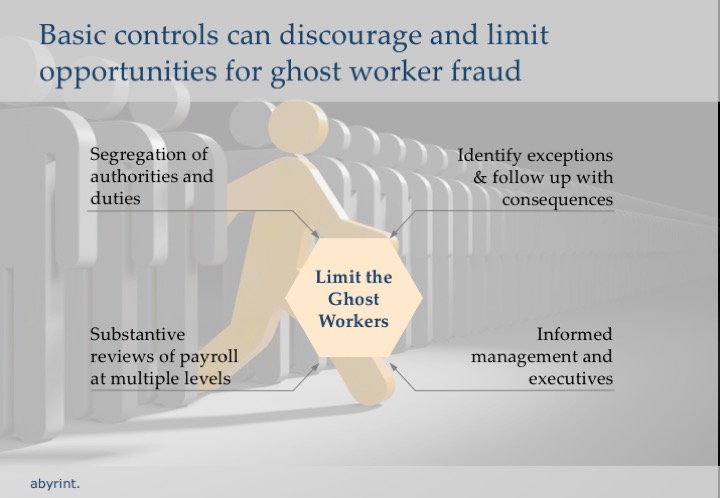
Even if you use direct deposit, try to hand-deliver paychecks every two months and ask for positive identification so you can discover leftover paychecks.Basic controls can discourage and limit opportunities for ghost worker fraud.
Segregation of authorities and duties, substantive reviews of payroll at multiple levels, and informed management and executives can go a long way.
These principles are the same as for general public financial management and budget execution.
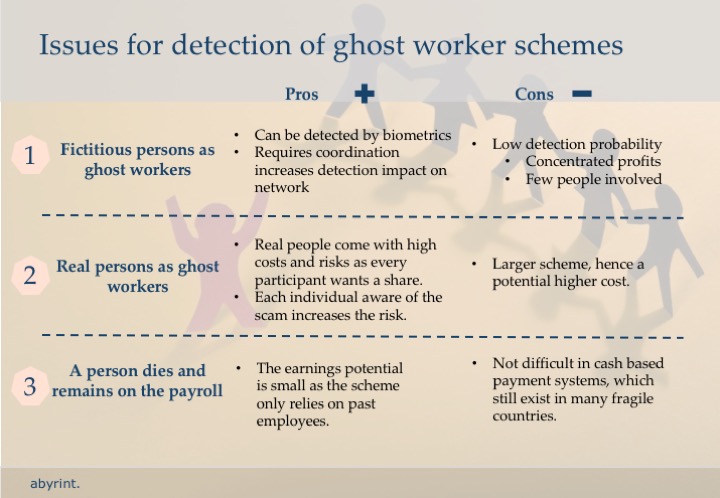
What is a phantom employee?
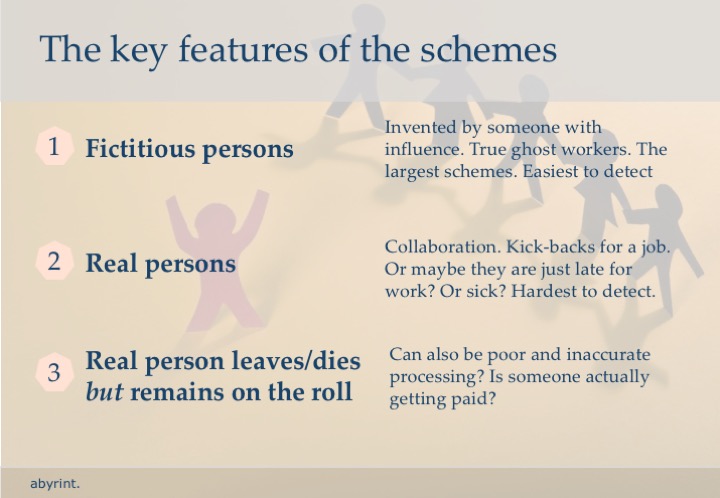
A phantom (ghost) employee is someone on the payroll who doesn't work for the company.
By falsifying personnel or payroll records, a fraudster can issue paychecks to this phantom employee.
Then, the fraudster, or even an accomplice, can cash or deposit these paychecks.
- Regular payroll audits.
- Cross-verification.
- Employee verification.
- Monitor employee turnover.
- Use technology.
|
Public Sector Savings and Revenue from Identification Systems:
The World Bank Group's Identification for Development (ID4D) initiative uses against the national ID database removing some 4 |
|
Intra Legem PHANTOM STOCKS OPTIONS
09-Jan-2016 These incentives and benefits include employee stock options and stock purchase plans stock appreciation rights |
|
Findings from a rapid review of literature on ghost workers in the
The following diagram shows the methodology applied to identify relevant literature for the rapid review. Literature search. The following databases were |
|
1) Forensic Accounting is defined as: a. The practice of applying
The use of law enforcement to subpoena financial records to determine Ghost employee scheme ... 76) Reporting of identified frauds is covered as per. |
|
A guide to its prevention detection and investigation
Some easy-to-implement fraud prevention techniques Ghost employee. Commission schemes. Workers compensation ... it is impossible to identify if current. |
|
Indian Accounting Standard (Ind AS) 102 Share-based Payment
payment transactions whether or not the entity can identify specifically than the fair value of those equity instruments |
|
Chapter 2 - Methods of Enquiry in Psychology.PMD
For finding out internal consistency the test is divided into two equal halves employing odd- even method (items 1 |
|
Identifying red flags Make your data speak
Phantom employees. Double payment. Missing inventory. Process failures. Split purchase orders. Fraud. Unknown risk. Irregularities. |
|
Payroll Audit
01-Dec-2021 timekeeping system is the method by which an organization tracks the ... To identify ghost employees we tested for indicators of ghosts by ... |
|
Internal Controls Over Creation of Ghost Employees OIG - WMATA
3 août 2017 · performed did not identify any evidence of payroll fraud through the use of fictitious protection to WMATA's preventive controls over ghost employees During NEO, the new hire's identity is verified through the I-92 process |
|
Fraud - PwC Australia
Some easy-to-implement fraud prevention techniques 3▫ Proactive fraud Personal purchases Ghost employee Identifying high fraud risk areas is the first |
|
Employee fraud - CPA Australia
records and having the salary of these “ghost” employees paid into the question unusual accounting methods or unnecessary complexity in an accounting transaction or excessively identifying other computers/equipment the employee |
|
Fraud risk management: a guide to good practice - CIMA
a more stringent approach to preventing, detecting and responding to fraud 6 and employees, e g financial statement fraud; selling counterfeit goods as genuine Fictitious (or ghost) employees on the payroll • Falsifying work hours to |
|
INTERNAL CONTROLS AND FRAUD DETECTION - Florida School
9 jui 2017 · Capability limitations of traditional data analytics methods and how to overcome Real world examples of indications of fraud identified using Potential Ghost Employee: Address is a Hotel, SSN Pattern or Other IDs are |
|
FINANCIAL CONTROL SYSTEM INNOVATIONS AND - IJSER
can be identified easily through the payroll reconciliation and staff evaluation method The second most common type of payroll fraud is “ghost employees |
|
Payroll Monitoring Overview - Pierre Consulting
Ghost employee schemes - adding fictitious (ghost) employees to the payroll Changes in taxation methods Identify any differences in the method used to |