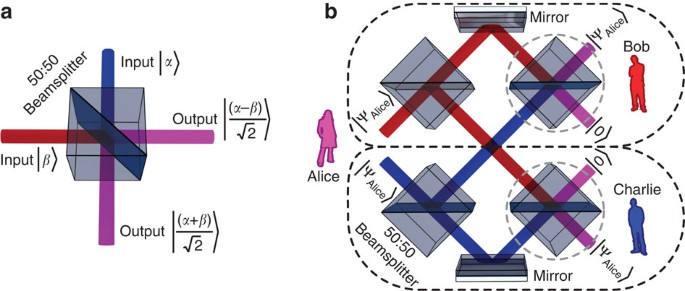
a method for obtaining digital signatures and public key cryptosystems bibtex
|
A Method for Obtaining Digital Signatures and Public-Key
At the heart of our proposal is a new encryption method This method provides an implementation of a “public-key cryptosystem” an elegant concept invented by |
What are the methods of digital signature in cryptography?
Digital signatures rely on asymmetric cryptography, also known as public key cryptography.
An asymmetric key consists of a public/private key pair.
The private key is used to create a signature, and the corresponding public key is used to verify the signature.What is the formula for digital signature in cryptography?
To calculate the value of s, you use the formula s = [K-1(h+x .
R)mod q].
It then packages the signature as {r,s}.
The entire bundle of the message and signature {M,r,s} are sent to the receiver.The Digital Signature Algorithm (DSA) is a public-key cryptosystem and Federal Information Processing Standard for digital signatures, based on the mathematical concept of modular exponentiation and the discrete logarithm problem.
DSA is a variant of the Schnorr and ElGamal signature schemes.
|
Double-Speed Barrett Moduli
constituents of most public-key cryptosystems. Amongst the numerous As an example of the proposed techniques the Elliptic Curve Digital Signature. |
|
Digital Signature Standard (DSS)
Approved cryptographic algorithms and techniques include those that are ANS X9.31-1998 Digital Signatures Using Reversible Public Key Cryptography for ... |
|
FIPS 186-3 Digital Signature Standard (DSS)
03-Jun-2009 Approved cryptographic algorithms and techniques include those that are ... ANS X9.31-1998 Digital Signatures Using Reversible Public Key ... |
|
Fast Multiparty Threshold ECDSA with Fast Trustless Setup
A threshold signature scheme enables n parties to share the power to issue digital signatures under a single public key. A threshold t is specified such that |
|
Practical Byzantine Fault Tolerance
A Method for. Obtaining Digital Signatures and Public-Key Cryptosystems. Communications of the ACM 21(2) |
|
Modular Multiplication Without Trial Division Author(s): Peter L
SHAMIR & L. ADLEMAN "A method for obtaining digital signatures and public-key cryptosystems |
|
CacheBleed: A Timing Attack on OpenSSL Constant Time RSA
A method for obtaining digital signatures and public-key cryptosystems. CACM 21:120–126 |
|
Responses to NISTs proposal
Who Holds t:he Keys? I. NIST's Proposal he U.S. Government agency NIST has recently proposed a public key digital signature standard [ |
|
Survey of Computational Assumptions Used in Cryptography Broken
public-key cryptosystem each person gets a pair of keys |
|
Addressing Weaknesses in the Domain Name System Protocol
A Method for Obtaining Digital. Signatures and Public Key Cryptosystems. Communications of the ACM. 21 2 :120 6 |
|
A Method for Obtaining Digital Signatures and Public-Key
A Method for Obtaining Digital Signatures and Public-Key Cryptosystems R L Rivest, A Shamir, and L Adleman ∗ Abstract An encryption method is |
|
A Method for Obtaining Digital Signatures and Public-Key
An encryption method is presented with the novel property that publicly re- vealing an encryption key does not thereby reveal the corresponding decryption key |
|
Using ASP-Based Message Encryption Project To Teach - CORE
public-key encryption algorithm is the RSA encryption algorithm algorithms are largely used for digital signature and key distribution due [1978], “A Method for Obtaining Digital Signatures All copies must bear this notice and full citation |
|
Chaotic Rivest-Shamir-Adlerman Algorithm with Data Encryption
currently published methods, if the public key is large enough, only someone with knowledge of the prime It may be used to provide both secrecy and digital signatures and its security is based on the Get the cipher text by RSA Encryption using the formula: http://portal acm org/citation cfm?doid= 359340 359342 |
|
RSA Signatures Under Hardware Restrictions - Cryptology ePrint
Digital Signatures; RSA; Hardware Security; Hardware Security Modules; Secure 1Or some other cryptographic key-management solution Permission to for profit or commercial advantage and that copies bear this notice and the full citation on the first algorithm for finding small roots of polynomial equations modulo |
















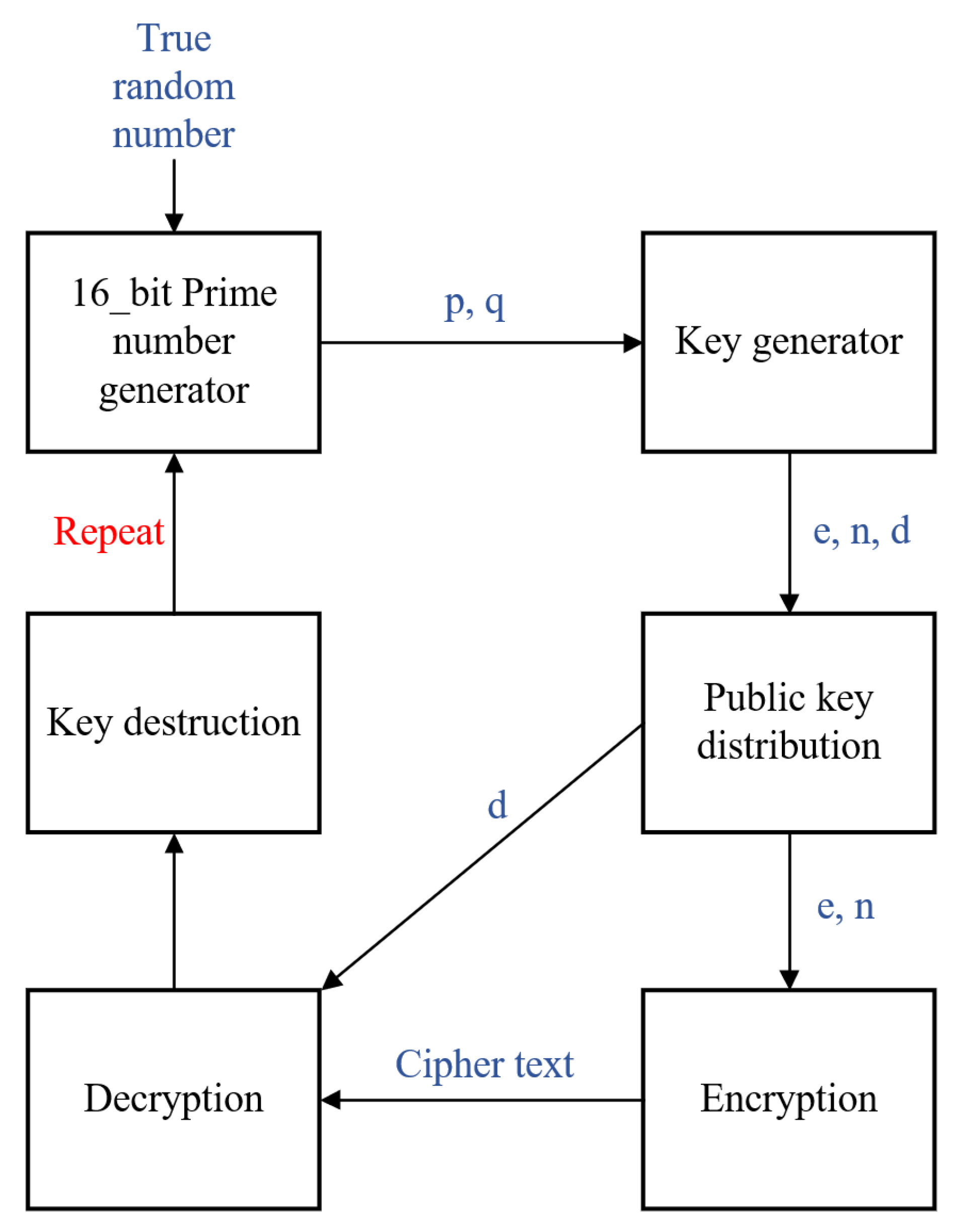





![PDF] Biometric Digital Signature Key Generation and Cryptography PDF] Biometric Digital Signature Key Generation and Cryptography](https://media.springernature.com/m685/springer-static/image/art%3A10.1038%2Fsrep09231/MediaObjects/41598_2015_Article_BFsrep09231_Fig1_HTML.jpg)


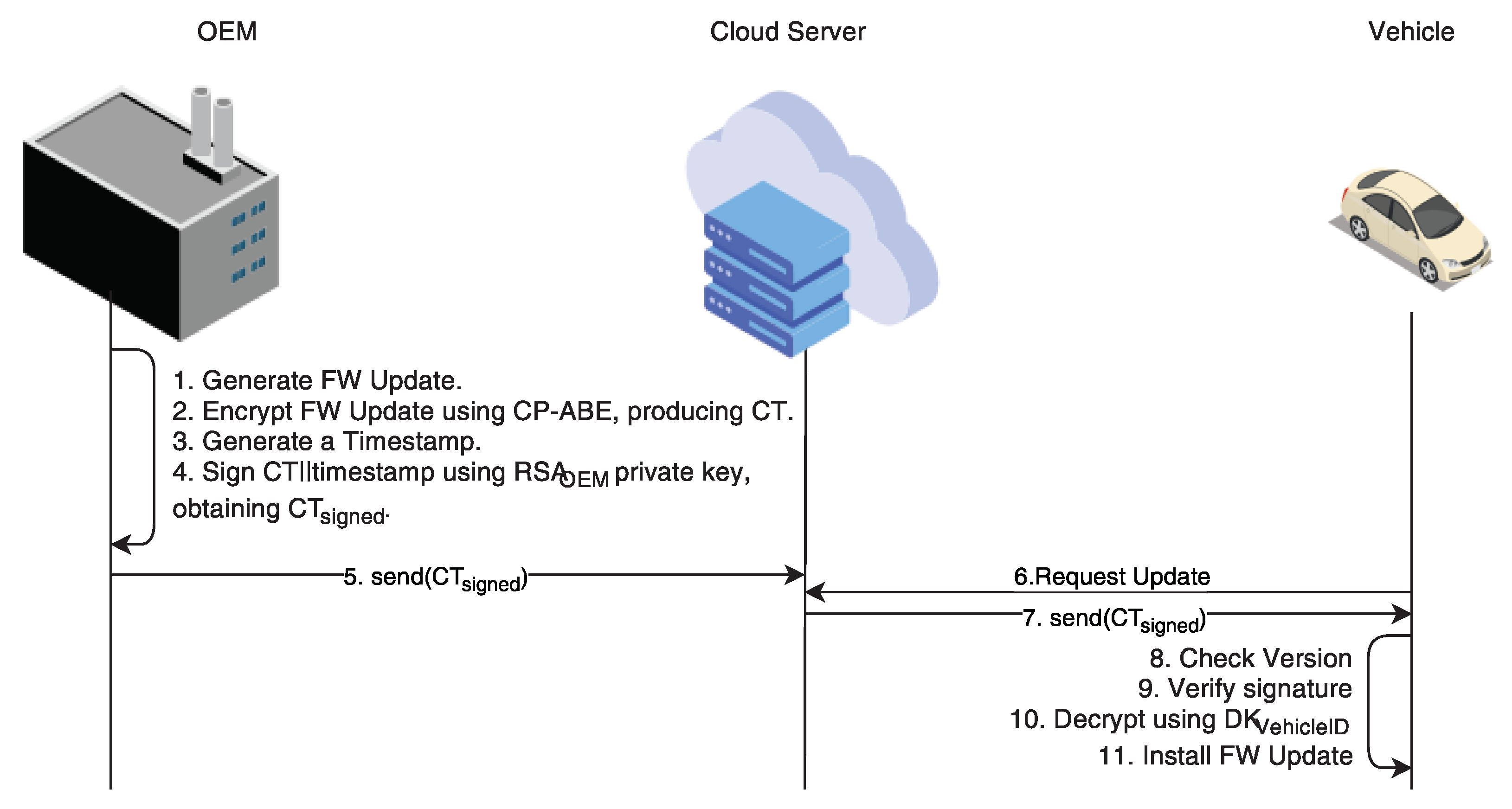

![PDF] Biometric Digital Signature Key Generation and Cryptography PDF] Biometric Digital Signature Key Generation and Cryptography](https://i1.rgstatic.net/publication/327635780_Rabin_Public-Key_Cryptosystem_in_the_Domain_of_Gaussian_Integers/links/5d36e5aea6fdcc370a57a6be/largepreview.png)


![PDF] A CRYPTANALYTIC ATTACK-ON THE LU-LEE PUBLIC-KEY CRYPTOSYSTEM PDF] A CRYPTANALYTIC ATTACK-ON THE LU-LEE PUBLIC-KEY CRYPTOSYSTEM](https://media.springernature.com/original/springer-static/image/chp%3A10.1007%2F978-3-319-48308-5_83/MediaObjects/429937_1_En_83_Fig2_HTML.gif)