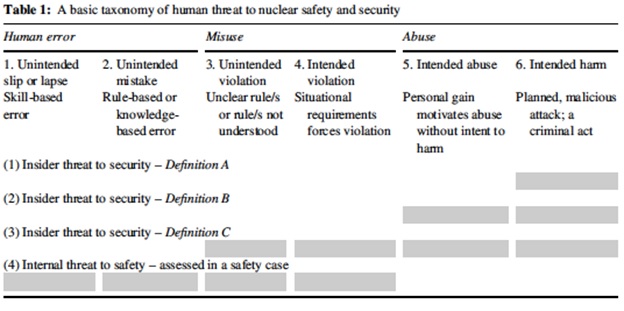
army insider threat
|
INSIDER ATTACKS AS ONE OF THE MAIN THREATS TO
This is essential to building situational awareness and generating Insider Threats warnings that ensure everyone has current threat and risk awareness – |
|
Insider Threat
Army employees must report potential threats to their organization's Insider Threat Program Employees may also consult their security office or supervisor |
|
Army Insider Threat Program
1 juil 2013 · The Army Insider Threat Program is an integrated departmental effort to deter detect and mitigate risk by employees or servicemembers who |
What is an insider threat army?
The potential for an insider who uses his or her authorized access, wittingly or unwittingly, to do harm to Army assets and the security of the United States.
What is an insider threat DoD examples?
This can include damage to the United States through espionage, terrorism, unauthorized disclosure of national security information, or through the loss or degradation of departmental resources or capabilities.
What is an insider threat?
An insider threat refers to a cyber security risk that originates from within an organization.
It typically occurs when a current or former employee, contractor, vendor or partner with legitimate user credentials misuses their access to the detriment of the organization's networks, systems and data.Insider Threat (CI InT) A person, known or suspected, who uses their authorized access to DoD facilities, personnel, systems, equipment, information, or infrastructure to damage and disrupt operations, compromise DoD information, or commit espionage on behalf of an FIE (Foreign Intelligence Entity).
|
Army Insider Threat Program
Army Regulation 381-12 (Threat Awareness and Reporting Program) 4 Oct 10. 2. This directive establishes the Army Insider Threat Program in accordance with. |
|
INSIDER THREAT
Personnel subject to the UCMJ who fail to comply with the reporting requirements of Army Regulation. 381-12 Threat Awareness and. |
|
Insider Threat
Army employees must report potential threats to their organization's Insider Threat Program. Employees may also consult their security office or supervisor. |
|
Insider Threat
You are the first line of defense against insider threats. Help protect our national security by reporting any suspicious behavior that may be related to an |
|
3 1 JUL 2013
SUBJECT: Army Directive 2013-18 (Army Insider Threat Program). 1 . References: 3 1 JUL 2013 a. Presidential Memorandum (National Insider Threat Policy and |
|
Report Suspicious Activity:
ARMY. STRONG®. Indicators of Potential Terrorist. Associated Insider Threat. Indicators of Potential Terrorist. Associated Insider Threat. |
|
Insider Threat Potential Risk Indicators (PRI) - JOB AID
The damage from insider threats can manifest as espionage theft |
|
INSIDER THREAT
In 2014 the National Insider Threat Task Force (NITTF) published its “Guide to Insider Threat Policy and Minimum Standards” to orient U.S. Government ... |
|
Insider Threat Graphic Novella
The story you are about to read is based on threatcasting research from the Army Cyber Institute at West Point and Arizona State. University's Threatcasting Lab |
|
Army Insider Threat Program
The Army's program will strengthen the protection of personnel, information and resources 4 Reference 1 a defines an insider threat as the "threat that an insider |
|
INSIDER THREAT - Armymil
Personnel subject to the UCMJ who fail to comply with the reporting requirements of Army Regulation 381-12 Threat Awareness and Reporting Program |
|
Insider Threat
Be Aware Insider Threat Examples of Reportable Behaviors Information Collection • Keeping classified materials in an unauthorized location (e g , at home) |
|
DOD Insider Threat Trifold - CDSE
All Were Trusted Insiders Keeping DoD's Personnel, Resources, and Capabilities Safe NOTABLE INSIDER THREATS Nidal Hasan □□ Former Army O-4 |
|
Insider Threat Awareness (INT101) Student Guide - CDSE
Recognize insider threat, counterintelligence, and security reporting advantage Although sabotage is often conducted for political or military reasons, other |
|
Insider Threat - Defense Science Board - USD R&E
28 sept 2020 · security objectives or to advance their own military and civil sectors It is long past time for the United States to address the insider threat and |
|
Insider Threats in Partnering Environments - WIRED
First, it aides military leaders and all personnel to be aware of the indicators associated with insider threat activity while serving in a partnering environment |
|
DoD Insider Threat Mitigation - DTIC
The “insider” is anyone who is or has been authorized access to a DoD information system, whether a military member, a DoD civilian employee, or employee of |
|
To Find the Terrorist within the Identification of the US Armys Insider
Prior to the Department of Defense synchronization, the U S Army has proposed changes within their forces to identify and define this insider threat This thesis |









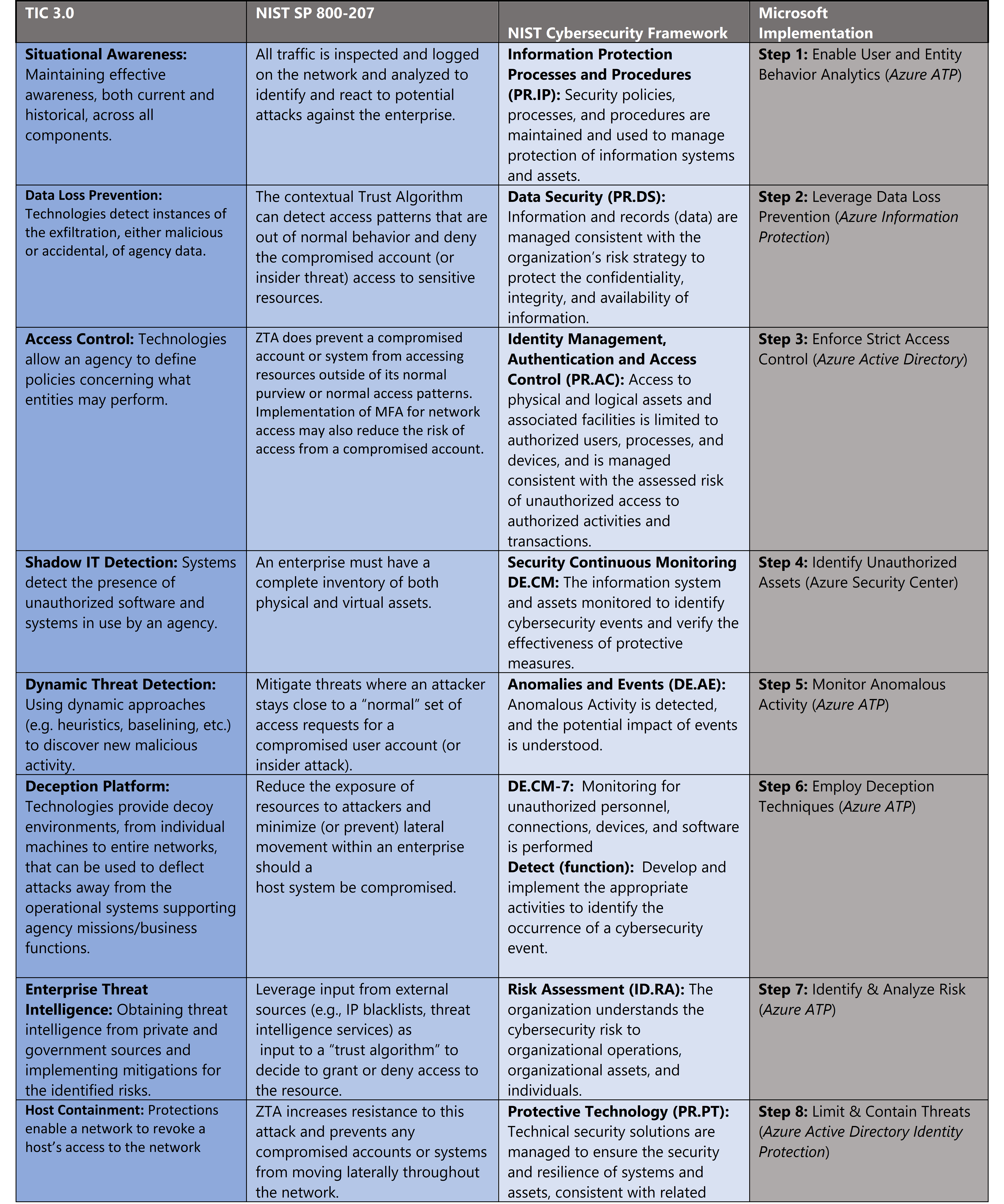






![PDF] A Scenario-Based Approach to Mitigating the Insider Threat PDF] A Scenario-Based Approach to Mitigating the Insider Threat](https://wwwassets.rand.org/content/rand/pubs/research_reports/RR2684/jcr:content/par/product.aspectfit.200x200.jpg/x1565011439050.jpg.pagespeed.ic.EUnMlrTEEj.jpg)









![PDF] A Scenario-Based Approach to Mitigating the Insider Threat PDF] A Scenario-Based Approach to Mitigating the Insider Threat](https://i1.rgstatic.net/publication/337438838_Insider_threats_in_Cyber_Security_The_enemy_within_the_gates/links/5e97623c92851c2f52a62936/largepreview.png)