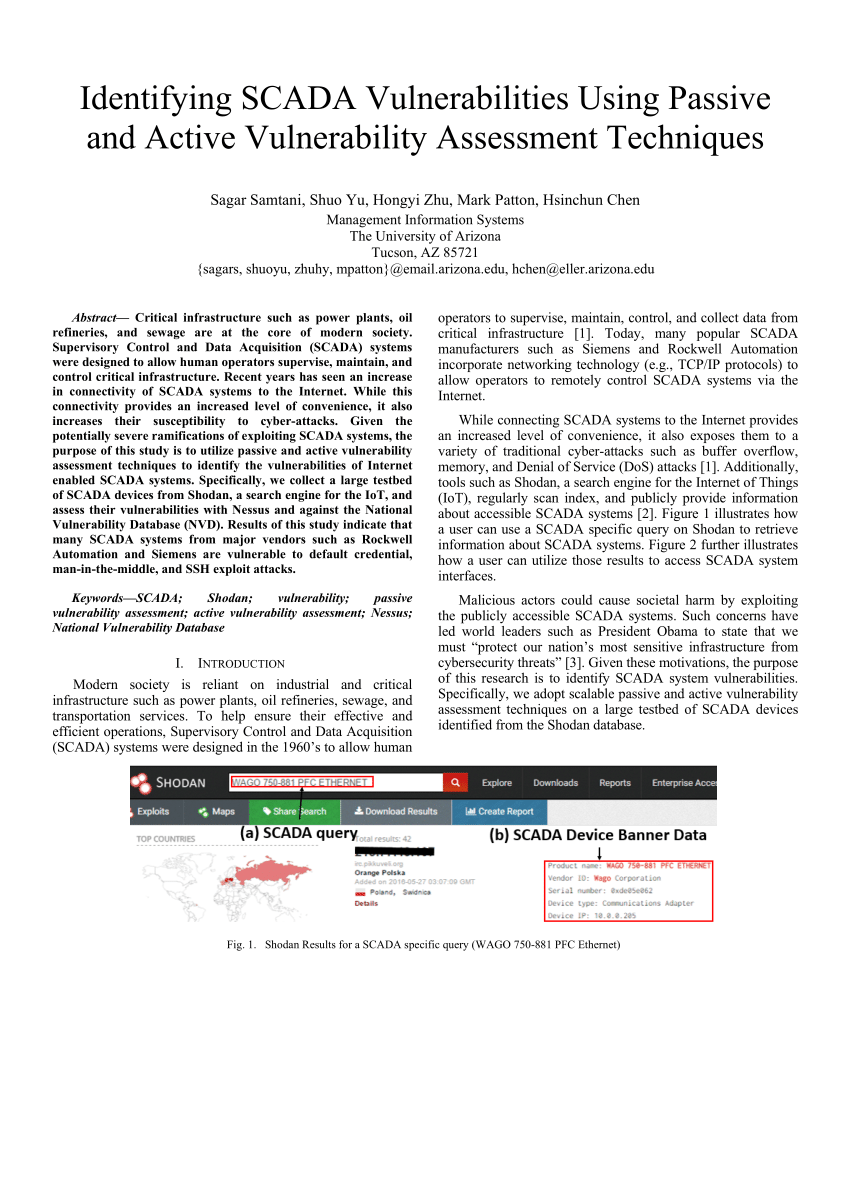
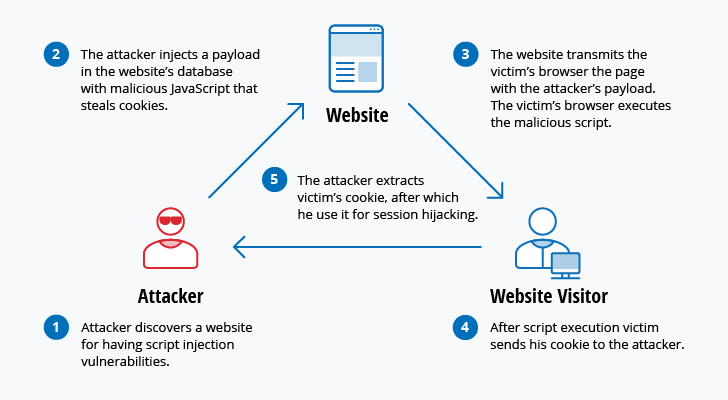
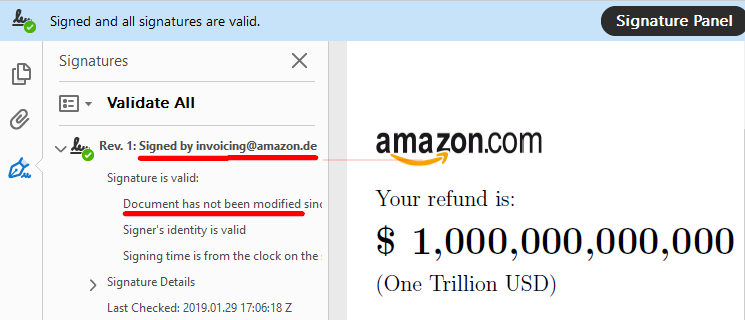
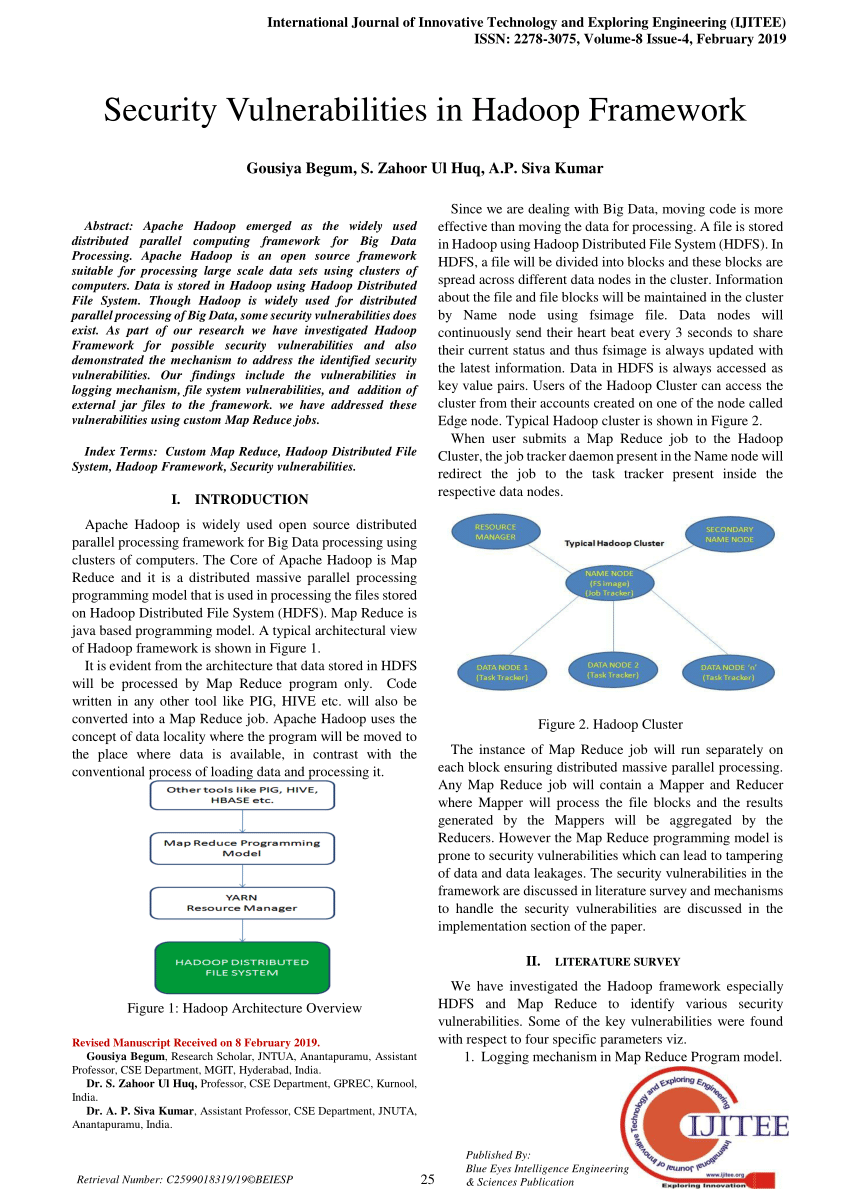
c data type vulnerabilities
|
Vulnerabilities in C/C++ programs – Part II
Vulnerabilities in C/C++ programs – Part II TDDC90 – Software Security Ulf A similar class of vulnerabilities are sign errors – mixing signed and unsigned |
|
Secure Coding in C and C++: A Look at Common Vulnerabilities
The basic_string class is less prone to security vulnerabilities than C-style strings C-style strings are still a common data type in C++ programs |
|
C Language Issues
The vulnerabilities resulting from type conversions are often fascinating because they can be subtle and difficult to locate in source code and |
Is C Secure or not?
Since memory safety bugs are often security issues, memory safe languages are more secure than languages that are not memory safe.
Memory safe languages include Rust, Go, C#, Java, Swift, Python, and JavaScript.
Languages that are not memory safe include C, C++, and assembly.What are the security threats in C?
Buffer overflow is a common security vulnerability in C programming.
What Is Buffer Overflow? Buffer overflow occurs when data is written outside the boundary of the allocated memory.What are the vulnerabilities in C?
Most vulnerabilities in C are related to buffer overflows and string manipulation.
In most cases, this would result in a segmentation fault, but specially crafted malicious input values, adapted to the architecture and environment could yield to arbitrary code execution.C does not have any of these protections: C heap values are created in a type-unsafe way.
C casts, unchecked array accesses, and unsafe deallocation can corrupt memory during its lifetime.
C deallocation is unsafe, and can lead to dangling pointers.
|
Secure Coding in C and C++: A Look at Common Vulnerabilities
The basic_string class is less prone to security vulnerabilities than C-style strings. C-style strings are still a common data type in C++ programs. Impossible |
|
String Vulnerabilities
vulnerabilities than C-style strings. ? C-style strings are still a common data type in C++ programs. ? Impossible to avoid having multiple string types |
|
Two complementary approaches to detecting vulnerabilities in C
30 Jan 2014 4.4 Injecting Data into a C Code for Detecting Vulnerabilities . ... l'arithmétique des pointeurs le manque d'un type de base pour les ... |
|
TDDC90 - C/C++ Vulnerabilities II
Heed compiler warnings! ? Understand sizes and conversion rules for data types! ? Use the type 'size_t' for variables representing lengths of things. |
|
Secure Coding in C++: Integers
software vulnerabilities (even when this behavior Type conversions occur explicitly in C++ as the result ... each variable (c1 and c2) to int size. |
|
An Analysis of C/C++ Datasets for Machine Learning-Assisted
Vulnerability detection datasets are quite different from other types of an astounding 34435% more than Wild C. The wchar_t data type is found in. |
|
Exploiting Format String Vulnerabilities
1 Sept 2001 It is a conversion function which is used to represent primitive C data types in a human readable string representation. They are used in ... |
|
SECURITY POSTURE ASSESSMENT (SPA)
c) Step 3 (security testing and risk analysis) i) conduct vulnerability exploitation and POC; ii) identify the remotely exploitable vulnerability types such |
|
Detecting Vulnerabilities in C Programs Using Trace-Based Testing
proach can handle new types of vulnerabilities by simply formulating new security requirements about the type and size of the declared program variable. |
|
Mitigating Information Leakage Vulnerabilities with Type-based Data
age vulnerabilities (or info leaks) remain a major security threat. Modern systems software is riddled c) TDI: In this paper we present Type-based Data. |
|
TDDC90 - C/C++ Vulnerabilities II - IDALiUse
A similar class of vulnerabilities are sign errors – mixing signed and unsigned data types in an unsafe way 3 // Reads 'size' bytes from file 'f' into buffer 'out' void |
|
String Vulnerabilities - School of Computing and Information
vulnerabilities than C-style strings ○ C-style strings are still a common data type in C++ programs ○ Impossible to avoid having multiple string types in a |
|
Software Vulnerabilities
Software vulnerability enables the attacker to run with privileges of malicious web contents exploit vulnerabilities in When assigning to a different data type |
|
Analysis of Field Data on Web Security Vulnerabilities
critical web application vulnerabilities: SQL Injection and XSS It analyzes the specifies how data types and data structures are managed and constructed by |
|
Pinpointing Vulnerabilities - Computer Science, FSU - Florida State
effectively pinpoint various types of memory vulnerabilities and has low performance sends data outside (e g , send, sendmsg, write), the vulnerability is likely |
|
Memory Corruption Vulnerabilities, Part II - Penn State University
Overflowing Heap Critical User Data ○ Overflow the buffer on the heap so that the function pointer is changed to an arbitrary address /* record type to allocate |
|
Source Code Patterns of Buffer Overflow Vulnerabilities in Firefox
C/C++ does allow the assignment of variables with different data types It will interpret the bits according to the new variable type For example, if a negative value |
|
Format String Vulnerabilities and Exploitation - NCC Group Research
The “ n” specifier, when used, will write the number of characters actually formatted in by printf'ing a format string to a variable To clarify: The “ n” format |



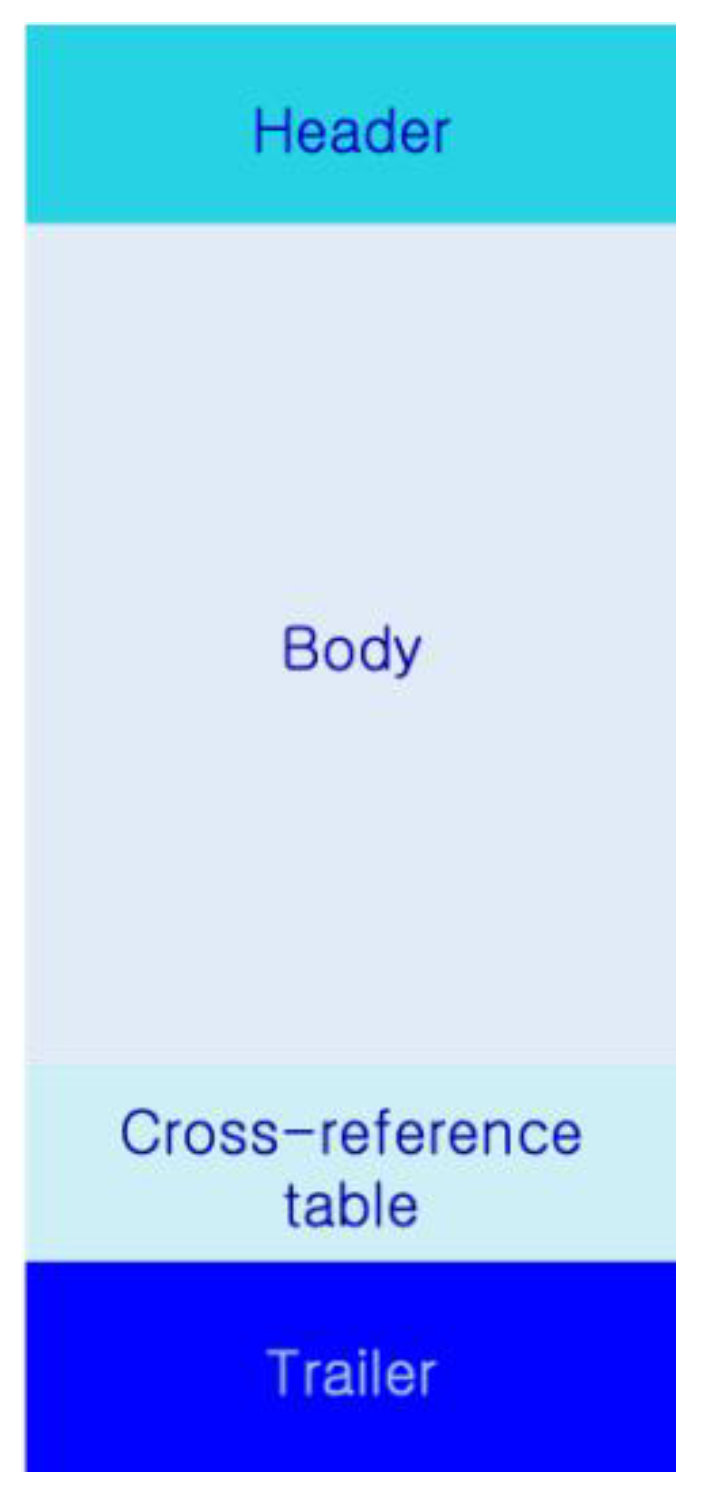
![PDF File Format: Basic Structure [updated 2020] - Infosec Resources PDF File Format: Basic Structure [updated 2020] - Infosec Resources](https://ars.els-cdn.com/content/image/3-s2.0-B9780124201149000083-f08-10-9780124201149.jpg)