a method for obtaining digital signatures and public key cryptosystems
|
A Method for Obtaining Digital Signatures and Public-Key
Apr 4 2015 · A Method for Obtaining Digital Signatures and Public-Key Cryptosystems R L Rivest A Shamir and L Adleman MIT Laboratory for Computer Science and Department of Mathematics An encryption method is presented with the novel property that publicly revealing an encryption key does not thereby reveal the corresponding decryption key |
|
A method for obtaining digital signatures and public-key
A method for obtaining digital signatures and public-key cryptosystems cryptography digital signatures electronic funds transfer electronic mail factorization |
|
A Method for Obtaining Digital Signatures and Public-Key
A Method for Obtaining Digital Signatures and Public-Key Cryptosystems R L Rivest A Shamir and L Adleman Abstract An encryption method is presented with the novel property that publicly re-vealing an encryption key does not thereby reveal the corresponding decryption key This has two important consequences: 1 |
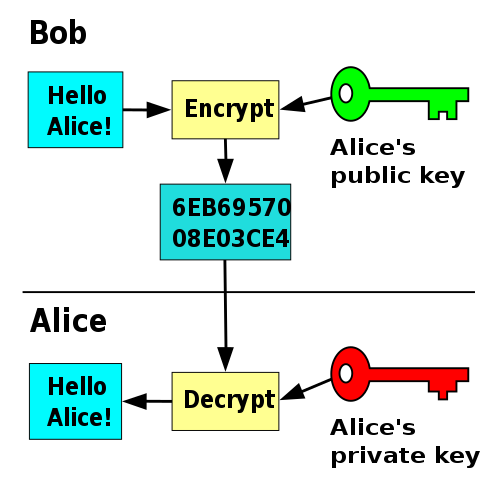
Can a message be signed using a private decryption key?
(2) A message can be “signed” using a privately held decryption key. Anyone can verify this signature using the corresponding publicly revealed encryption key. Signatures cannot be forged, and a signer cannot later deny the validity of his signature. This has obvious applications in “electronic mail” and “electronic funds transfer” systems.
Can a signer decipher a message?
Only he can decipher the message, since only he knows the corresponding decryption key. A message can be “signed” using a privately held decryption key. Anyone can verify this signature using the corresponding publicly revealed encryption key. Signatures cannot be forged, and a signer cannot later deny the validity of his signature.
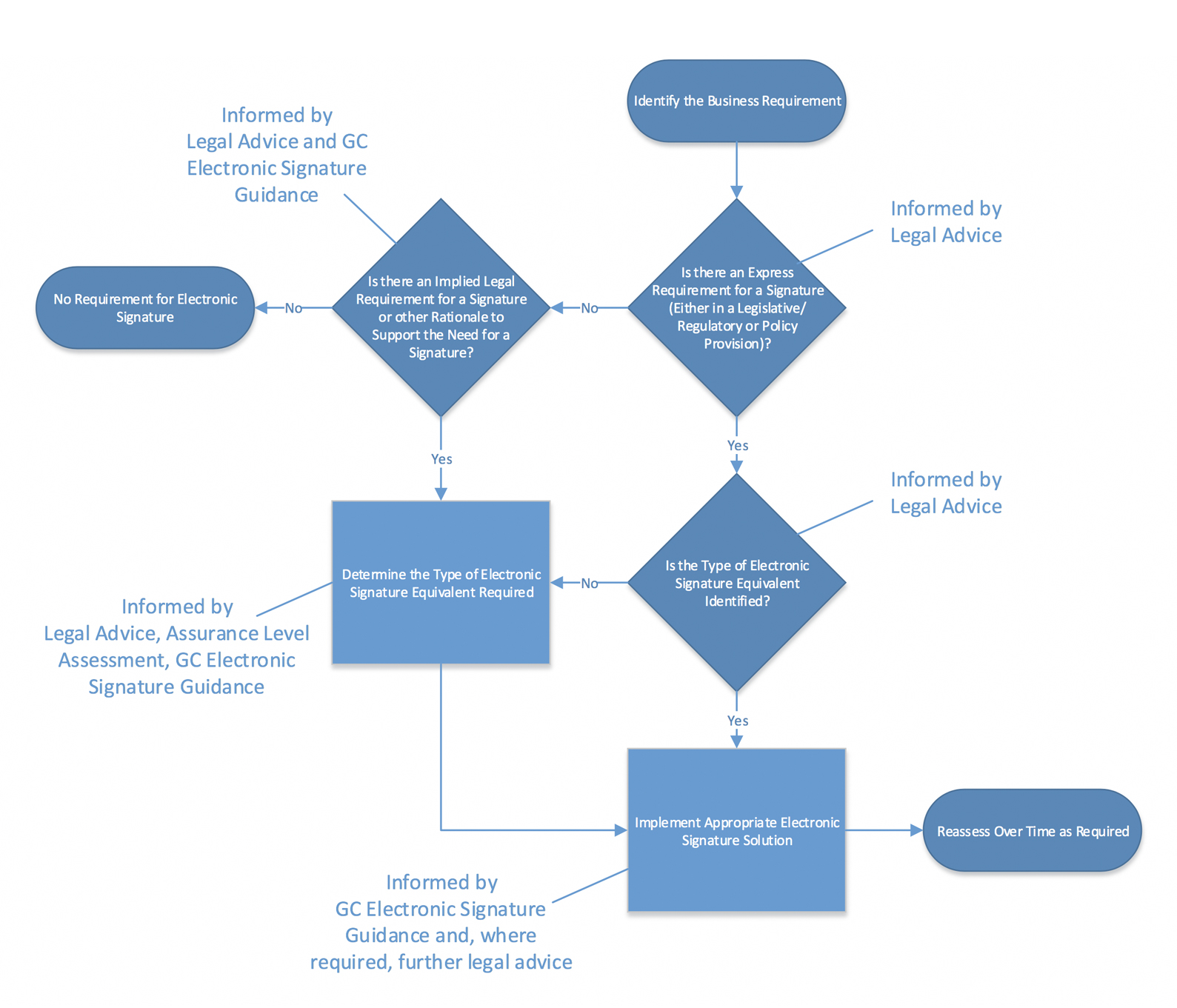
How do you implement a public-key cryptosystem?
To implement signatures the public-key cryptosystem must be implemented with trap-door one-way permutations (i.e. have property (d)), since the decryption algo- rithm will be applied to unenciphered messages. How can user Bob send Alice a \\signed" message Min a public-key cryptosystem?
Does public re-vealing an encryption key reveal the corresponding decryption key?
A Method for Obtaining Digital Signatures and Public-Key Cryptosystems R.L. Rivest, A. Shamir, and L. Adleman Abstract An encryption method is presented with the novel property that publicly re- vealing an encryption key does not thereby reveal the corresponding decryption key. This has two important consequences: 1.
I.Introduction
Programming S.L. Graham, R.L. Rivest* The raof"electronic mail" [10] may soon beupon Techniques Editors us; we must ensure that two important properties of A Method the current "paper mail" system arepreserved: (a) for Obtaining messages are private, and (b) messages can be signed. Digital Signatures and Public- We demonstrate inthis paper tohow bu
Signatures cannot be forged, and asigner cannot later
(a)Deciphering enciphered the form ofa message M denythe validity of his signature. obvious This has applications in "electronic mail" and "electronic funds yields M.Formally, transfer" systems. A message isencrypted by D(E(M)) = M. (I) representing it as a number M,raising M toa publicly specified power and e, then taking theremainder (b) Both E a
whenthe result isdivided bythe publicly specified
(c)By publicly revealing E theuser not does r veal an product, n, of two large secret prime numbers pand q. Decryption is imilar; only a different, secret, power d easy way to compute D. This means that inpractice only he can decrypt messages encrypted with E, or dl.acm.org
security of the system rests in part onthe difficulty of
(d)If a message M isfirst deciphered then enci- and dl.acm.org
V.Our Encryption and Decryption Methods
M= F~(S). Shenow possesses a m sage-signature pair (M, S) Toencrypt a message M with our method, using a with properties similar to those ofa signed paper public en ryption key (e, n), proceed as follows. (Here document. e andn are apair ofpositive int gers.) Bob cannot later deny having sent Alice this mes- First, represent themessage san integer

2

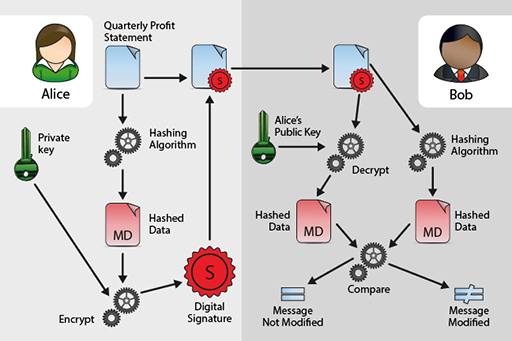
Digital Signatures and Digital Certificates

Digital Signature Algorithm (DSA)
|
A Method for Obtaining Digital Signatures and Public-Key
Key Words and Phrases: digital signatures public-key cryptosystems |
|
A Method for Obtaining Digital Signatures and Public-Key
Key Words and Phrases: digital signatures public-key cryptosystems |
|
A Method for Obtaining Digital Signatures and Public-Key
3 avr. 2022 Key Words and Phrases : digital signatures public-key cryptosystems |
|
A Method for Obtaining Digital Signatures and Public- Key
Key Words and Phrases: digital signatures public- key cryptosystems |
|
A method for obtaining digital signatures and public-key cryptosystems
~_. ~ & ~a ! . ~. ~. A ~ a. ~ . -~ = ~ - : ~: o. = ' ~ " ~ ' . . ~ -. ~. -=."2". ~ . t . ~ ~a. ~ a |
|
A Method for Obtaining Digital Signatures and Public-Key
Key Words and Phrases: digital signatures public-key cryptosystems |
|
A method for obtaining digital signatures and public-key cryptosystems
Key Words and Phrases: digital signatures public- key cryptosystems |
|
A Method for Obtaining Digital Signatures and More Citations
A Method for Obtaining Digital Signatures and. More Citations 2 A new approach to gather more citations ... signatures and public-key cryptosystems. |
|
A Method for Obtaining Digital Signatures and Public-Key
Key Words and Phrases: digital signatures public-key cryptosystems |
|
Lecture 14 14.1 A Method for Obtaining Digital Signatures and
More specifically the authors use the Diffie and Hellman's concepts of public key crypto-systems and use this to implement a new encryption and signing method |
|
A Method for Obtaining Digital Signatures and Public-Key
An encryption (or decryption) procedure typically consists of a general method and an encryption key The general method, under control of the key, enciphers a message M to obtain the enciphered form of the message, called the ciphertext C |
|
A Method for Obtaining Digital Signatures and Public-Key - DTIC
3 avr 2020 · A Method for Obtaining Digital Signatures and Public-Key Cryptosystems 5a CONTRACT NUMBER 5b GRANT NUMBER 5c PROGRAM |
|
Lecture 14 141 A Method for Obtaining Digital Signatures and
More specifically, the authors use the Diffie and Hellman's concepts of public key crypto-systems and use this to implement a new encryption and signing method |
|
A Method for Obtaining Digital Signatures and More Citations - The
Solving a discrete logarithm problem with auxiliary input on a 160-bit elliptic curve In Public Key Cryptography - PKC 2012, volume 7293 of Lecture Notes in |
|
A Method for Obtaining Digital Signatures and Public-Key
A Method for Obtaining Digital Signatures and Public-Key Cryptosystems R L Rivest, A Shamir, and L Adleman* Abstract An encryption method is presented |
|
Data Encryption and Authetication Using Public Key Approach - CORE
Applications for Public-Key Cryptosystems: Refer table shown below Algorithm Encryption/Decryption Digital Signature Key Exchange RSA Y Y Y Y can be obtained from the equation, through which a value of (x, y) can be extracted |
|
Digital Signatures with Public Key Cryptography
Symmetric cryptography, often called "shared secret" or "secret key" cryptography, uses the same mathematical function or algorithm to encrypt and decrypt a |
|
Data Encryption and Authetication Using Public Key Approach
Applications for Public-Key Cryptosystems: Refer table shown below Algorithm Encryption/Decryption Digital Signature Key Exchange RSA Y Y Y Y can be obtained from the equation, through which a value of (x, y) can be extracted |
|
1 What is a public key cryptography? - IGNTU
Out of all cryptographic primitives, the digital signature using public key The process of obtaining Digital Certificate by a person/entity is depicted in |