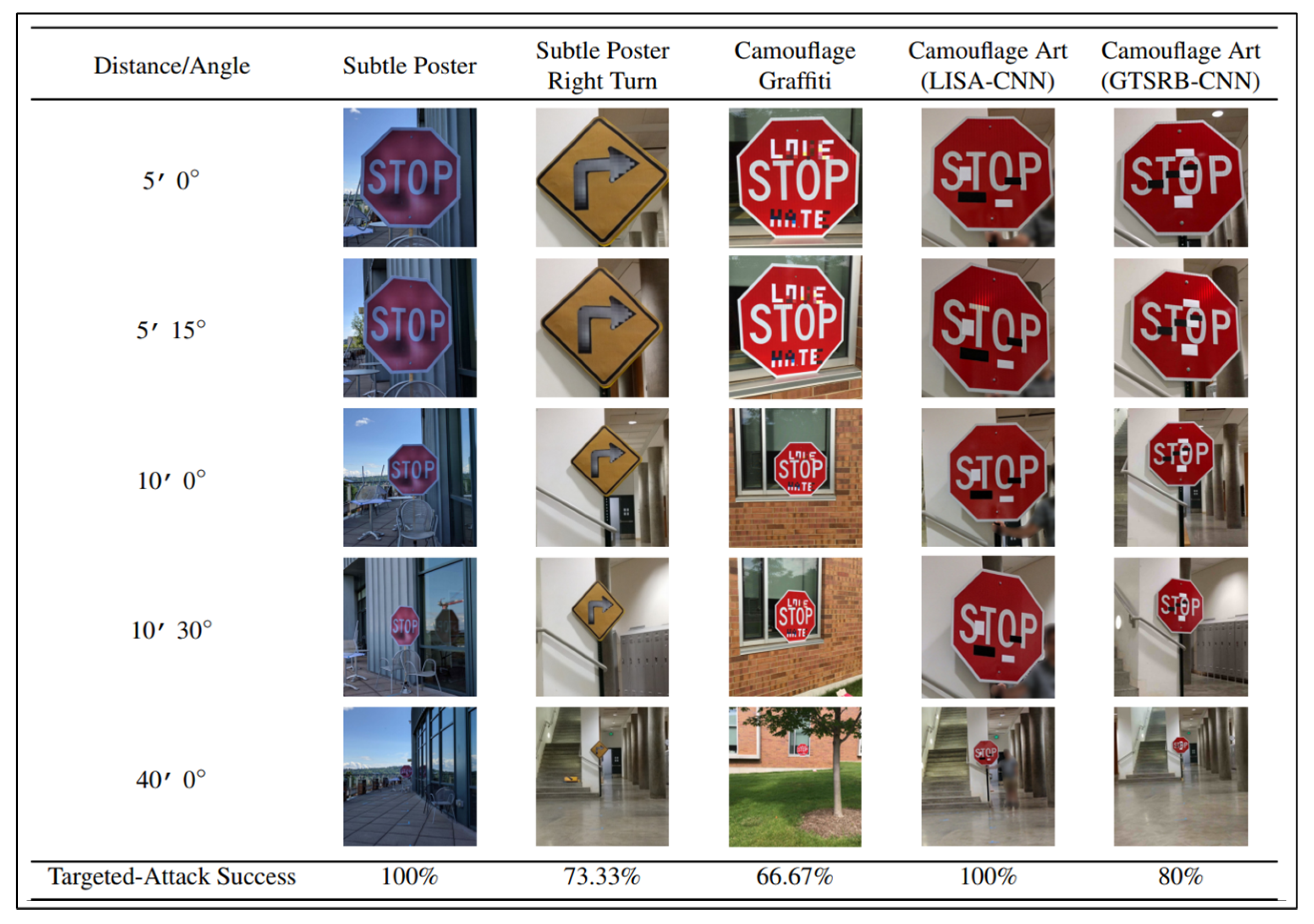
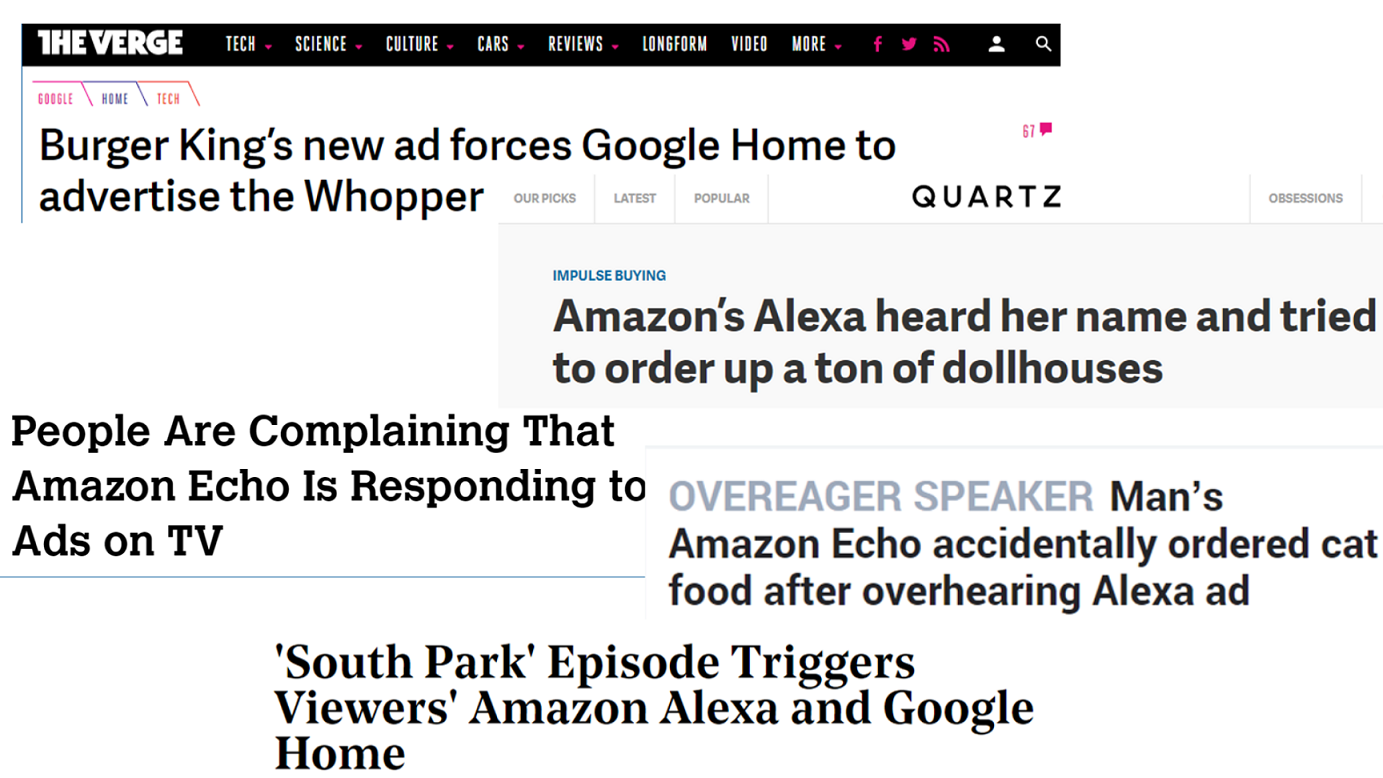
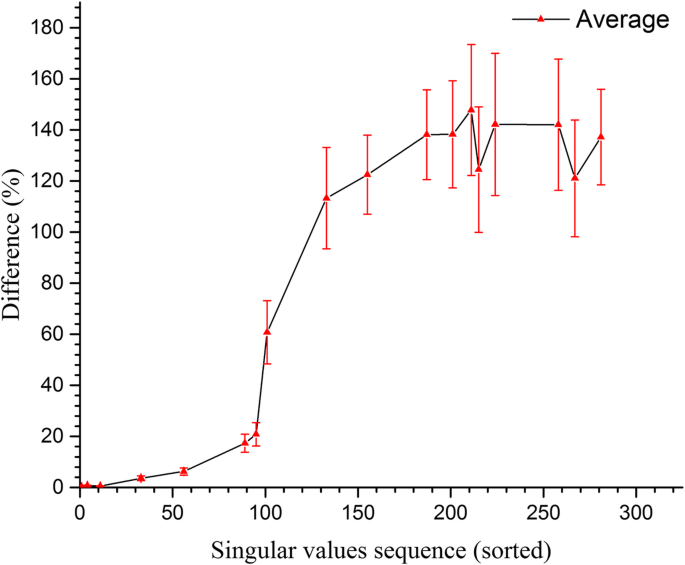
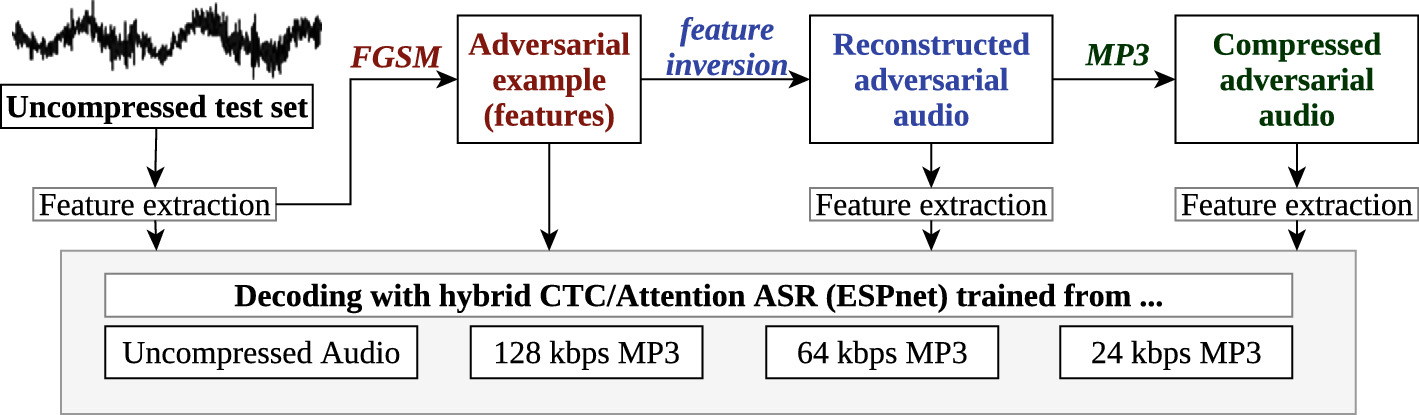
and targeted adversarial examples for automatic speech recognition github
|
Imperceptible Robust and Targeted Adversarial Examples for
12 jui. 2019 Imperceptible Robust and Targeted. Adversarial Examples for Automatic Speech Recognition. Yao Qin |
|
Disappeared Command: Spoofing Attack On Automatic Speech
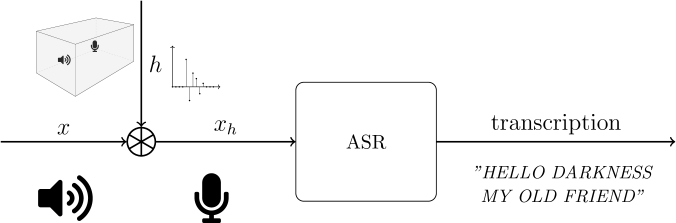
8 jui. 2022 We tested the effective- ness of adversarial examples on the commercial speech recognition APIs of iFlytek Tencent |
|
Evading Logits-Based Detections to Audio Adversarial Examples by
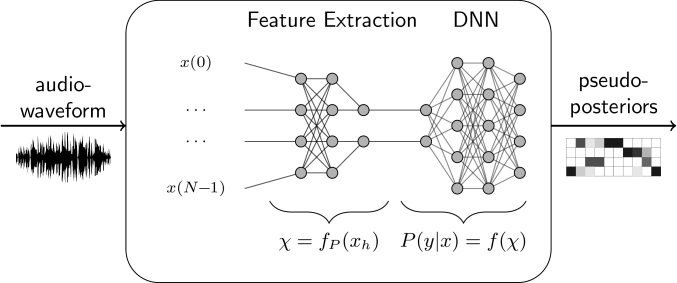
19 sept. 2022 As Automatic Speech Recognition (ASR) models are deployed on systems that directly affect safety such as smart homes and autonomous driving |
|
Robust Audio Adversarial Example for a Physical Attack
19 août 2019 Google Voice application using adversarial examples gener- ... over-the-air condition targeting speech recognition models. |
|
SoK: A Modularized Approach to Study the Security of Automatic
30 juil. 2021 Targeting at the neural networks in acoustic model the attackers can craft adversarial examples to mislead ASR. |
|
Advbox: a toolbox to generate adversarial examples that fool neural
26 août 2020 misclassified samples were named as Adversarial Examples. ... robust and targeted adversarial examples for automatic speech recognition |
|
Universal adversarial examples in speech command classification
13 fév. 2021 differentiable which is the case of automatic speech recognition. They were able to generate both targeted and untargeted attacks against a ... |
|
Devils Whisper: A General Approach for Physical Adversarial
With the advance of automatic speech recognition (ASR) tech- Recently Taori et al. have made the targeted adversarial attack. |
|
Metamorph: Injecting Inaudible Commands into Over-the-air Voice
26 fév. 2020 mission to attack the neural network of a speech recognition system. ... speaker to play malicious adversarial examples hiding voice. |
|
Characterizing the adversarial vulnerability of speech self
2015) as training validation |
|
Imperceptible, Robust and Targeted Adversarial Examples - ICML
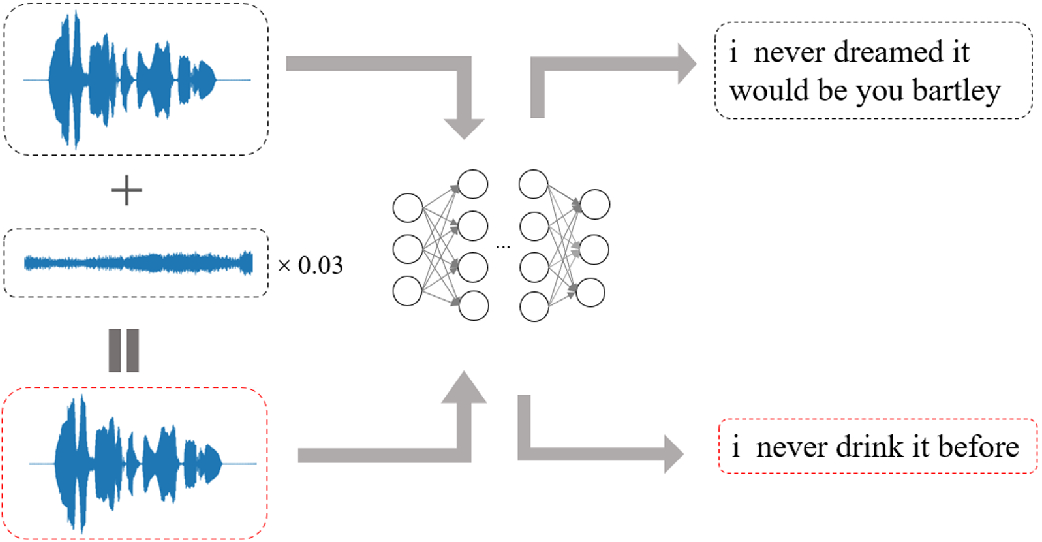
12 jui 2019 · Adversarial Examples for Automatic Speech Recognition Given an input audio , a targeted transcription , an automatic speech Code: https://github com/tensorflow/cleverhans/tree/master/examples/adversarial_asr |
|
Robust Audio Adversarial Example for a Physical Attack - IJCAI
performed an attack on Google Voice application using adversarial examples gener- over-the-air condition, targeting speech recognition models using a recurrent 2Our full implementation is available at https://github com/ hiromu/ robust |
|
Adversarial Examples Against Automatic Speech Recognition
Our attack only changes the least significant bits of a subset of audio clip samples , and the noise does not change 89 the human listener's perception of the |
|
An Overview of Attacks against Automatic Speech Recognition and
improvement in both Automatic Speech Recognition (ASR) and Speaker an adversarial sample that transcribes to the desired target text D Statistical 2019 , available at https://github com/SeanNaren/deepspeech pytorch [27] D Povey, A |
|
Targeted Speech Adversarial Example Generation - IEEE Xplore
examples Specifically, we integrate the target speech recognition network with models and data are publicly available at https://github com/winterwindwang/ SpeechAdvGan speech recognition (ASR) systems are dependent on running |
|
Defending Adversarial Attacks on Cloud-aided Automatic Speech
we propose several proactive defense mechanisms against targeted audio adversarial examples in the ASR systems via code modula- tion and audio |
|
Detecting Adversarial Examples for Speech Recognition via
25 oct 2020 · In the case of ASR systems, the most interesting cases are targeted attacks, in which an attacker aims to force the system into recognizing given target transcriptions in an arbitrary audio github com/rub-ksv/uncertaintyASR |