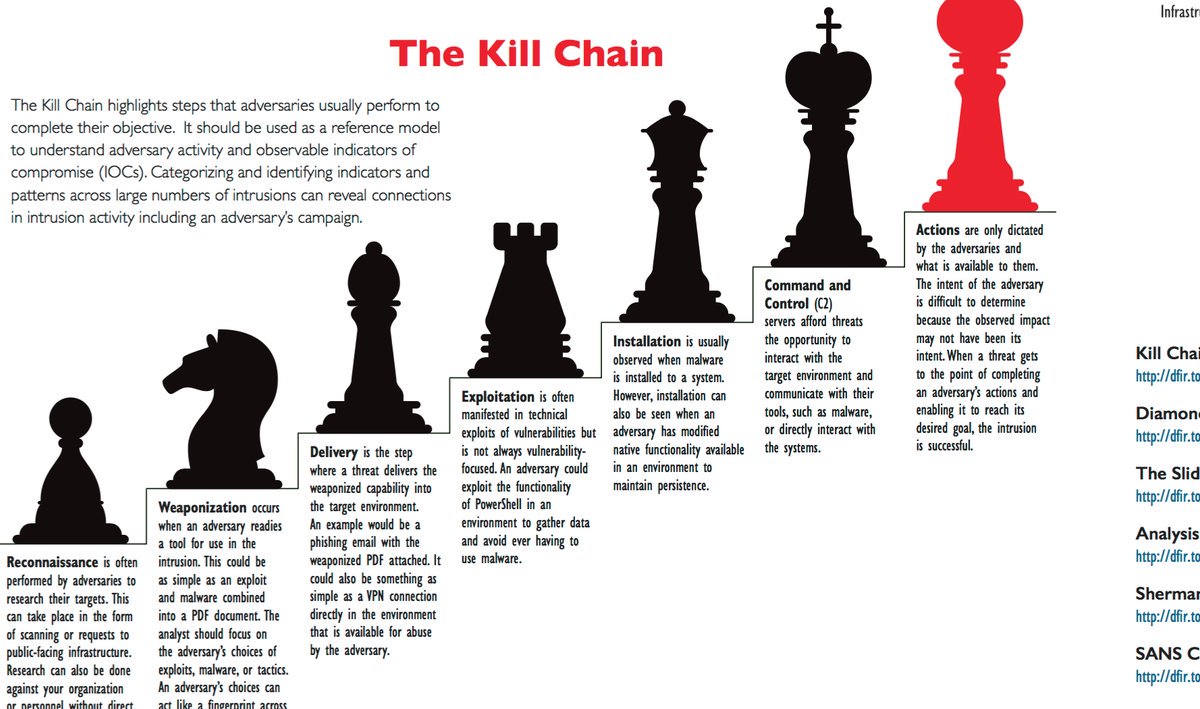
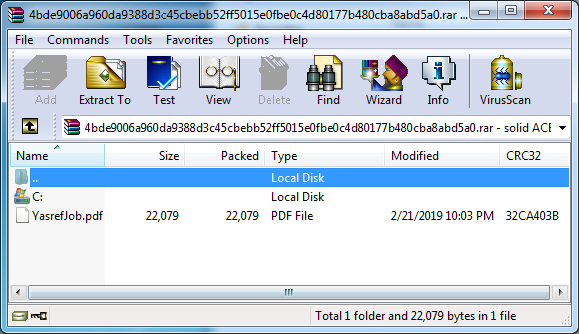
304 not modified exploit
What does 304 not modified mean?
No, a 304 status code is not bad.
It is a response status code that indicates that the requested resource has not been modified since the last time it was accessed and can be used to help reduce bandwidth usage and improve page loading times by allowing cached resources to be reused.How to bypass 304 not modified?
An HTTP 304 not modified status code means that the website you're requesting hasn't been updated since the last time you accessed it.
Typically, your browser will save (or cache) web pages so it doesn't have to repeatedly download the same information.
This is an attempt to speed up page delivery.Is 304 error bad?
The HTTP 304 not modified status code indicates a communication problem between a user's browser and a website's server.
If you or your users come across this status code on your site, it can block access to your content entirely.14 août 2023
|
United Nations Convention on the Law of the Sea
Non-compliance by warships with the laws and Article 304. ... exploration and exploitation of which shall be carried out for the benefit of. |
|
B COUNCIL REGULATION (EC) No 428/2009 of 5 May 2009 setting
07 Oct 2021 Regulation (EU) No 1232/2011 of the European Parliament and of the ... national general export authorisations issued or modified. The. |
|
REPORT European Union Mediterranean Fisheries and exploited
11 Jun 2004 No structural modifications of fishing gear have been observed in the last ten years. In July – August some boats may utilise a superimposed ... |
|
IOS: Back to the Future
08 Mar 2014 For how long a not very complex vulnerability can remain ... Vendors do not take relevant issues seriously ... HTTP/1.1 304 Not Modified. |
|
Contractual arrangements applicable to creators: law and practice of
the transferee but not always or in all types of contracts. has changed however is the market of exploitation of works. Digital technologies have. |
|
Legislative guide - for the protocol to prevent suppress and punish
Protocol under this article would consequently be modified or interpreted so as to have the same As such vulnerability is not a static |
|
Reducing Term Mismatch Probability by Exploiting Semantic Term
12 Jan 2018 idea of our document modification approach is to deal with mismatched query terms. A mis- matched query term is a query term that does not ... |
|
NON-STANDARD EMPLOYMENT AROUND THE WORLD
development and changed the world of work. Nevertheless much of these gains have not been fully shared |
|
Code Igniter Vulnerability Report
Last Modification. 03/08/17. Requested by. Version Also we show where the vulnerability is in the CI source code and ... 304. => 'Not Modified' |
|
Proceedings of the Joint Workshop on Exploiting Synergies between
Measuring Comparability of Documents in Non-Parallel Corpora for Efficient whether the prepositional phase is modifying the ... Republic pp.304—311. |
|
Bypassing Browser Security Policies For Fun And Profit - Black Hat
18 mar 2016 · Exploit will not function the same between a device and a simulator due to the fact that the memory combined with OEM's modification to android code without security testing may also introduce HTTP/1 1 304 Not Modified |
|
SSRF bible Cheatsheet - OWASP Cheat Sheet Series
Determine host-based auth daemons and try to exploit it File Descriptors PHP (require dlopen, but not exec): https://github com/dhotson/fdopen-php Basically you can use nmap probes but some of them need to be modified for time-based Table of POST redirection: Lib/Status 300 301 302 303 304 305 306 307 |
|
Attack Development for Intrusion Detection Evaluation* - CORE
of the author and are not necessarily endorsed by the United States Air Force Stealthy attacks, modified to be difficult to detect by network intrusion detection Remote-to-Local attack exploits NcFTP's ability to recursively download subdirectories When a user 304 Mar 28 06:19 /export/home/bramy/mailrace c 46825 |
|
Application Vulnerability Description Language v10 - OASIS Open
might use AVDL include (but are not limited to) vulnerability assessment tools, 304 305 306 307 308 309 310 311 It is important to note that the parsed header However, this document itself does not be modified in any way, such as by |
|
Web Application Security - APHRDI
6 oct 2020 · 50 are unsure about the hack 6 C-DAC, Hyderabad Can be changed if application support method interchange 304 - Not Modified |



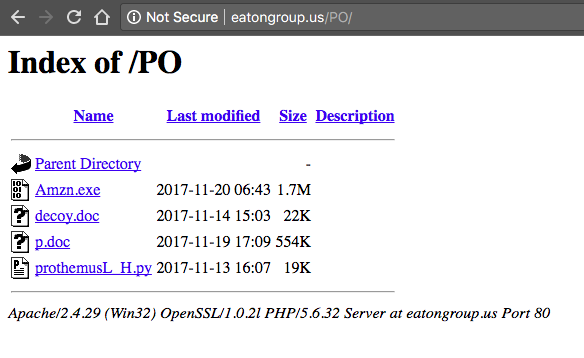





















![vulnsg] PDF Reader - iPad Edition HTTP Directory Traversal vulnsg] PDF Reader - iPad Edition HTTP Directory Traversal](https://img.wonderhowto.com/img/06/17/63493783893112/0/hack-like-pro-embed-backdoor-connection-innocent-looking-pdf.w1456.jpg)