Local Area Networks - ACSAC
|
ACSAC Network Support Project
7 jui 2023 · The test bed activity at Walter Reed demonstrated the efficacy of local area networks ACSAC determined that extensions of this technology |
|
Closed-Circuit Unobservable Voice Over IP
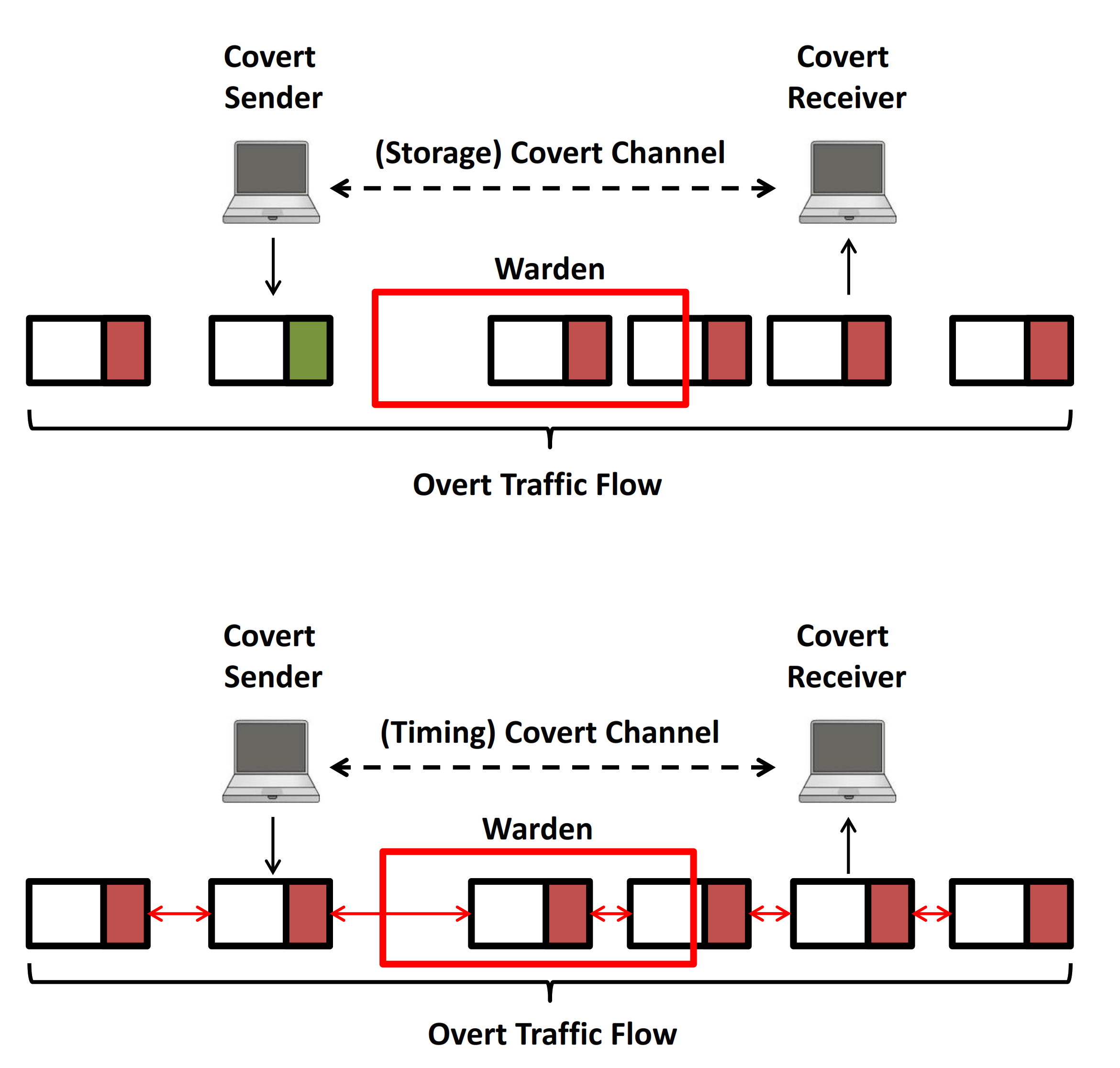
This technique is therefore unusable over the Internet for more than a few users but can be used in a local area net- work to form completely unobservable sets |
|
Smart Cards Biometrics and Tokens for VLANs and Subnet Access
• Network access for the local users starts at the switch port œ If I have ACSAC 12/01 œ slides 8 Authenticated Layer 2 Access VLAN • User's device is |
|
Local Area Network; Handbook;6th Edition
This collective environment in which networking and information tech- nology work together to create LAN-based enterprise networks is the focus of this Local |
|
NUREG/CR-7117 Secure Network Design
A summary of important aspects of the network architecture design follows • The topology of the network should be documented and reviewed; each network device |
|
MAppGraph: Mobile-App Classification on Encrypted Network Traffic
6 déc 2021 · ABSTRACT Identifying mobile apps based on network traffic has multiple bene- fits for security and network management |
|
Annual Computer Security Applications Conference (ACSAC)
17 nov. 2004 Additionally all attendees should understand basic local area network terminology and fundamental networking concepts such as the OSI reference ... |
|
An Intrusion Detection Tool for AODV-based Ad hoc Wireless
Department of Computer Science Mobile ad hoc network routing protocols are highly suscepti- ... techniques to detect MAC spoofing in wireless LANs. In. |
|
S-ARP: a Secure Address Resolution Protocol?
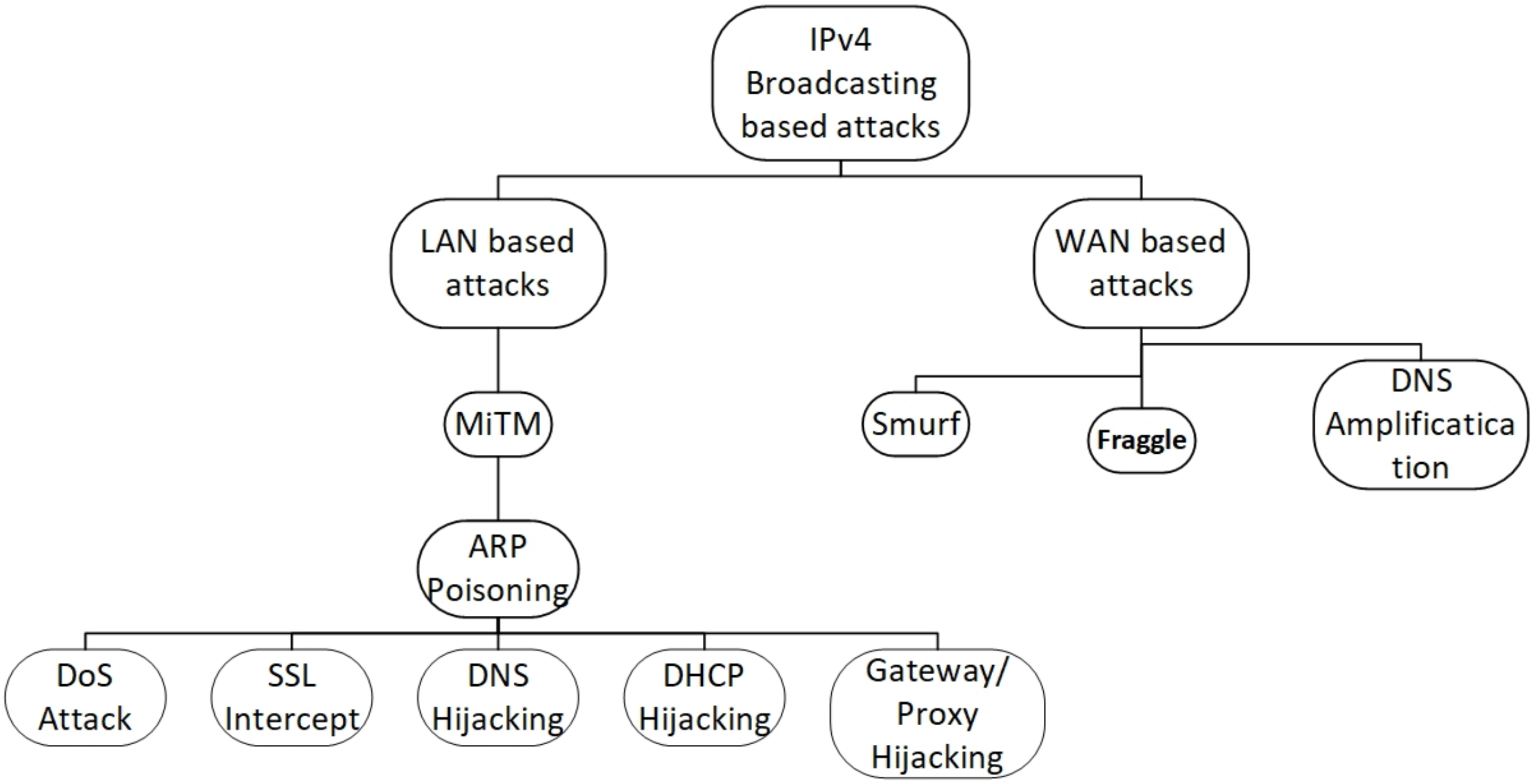
IP over Ethernet networks are the most popular Local. Area Networks nowadays. They use ARP the Address Res- olution Protocol |
|
TARP: Ticket-based Address Resolution Protocol
addresses onto hosts hardware addresses within a local area network. As such its correctness is essential to proper func- tioning of the network. |
|
An Application of Machine Learning to Network Intrusion Detection
in applying these techniques to computer network intrusion detection. In order to find local maxima of the fitness function and hence multiple rules |
|
Closed-Circuit Unobservable Voice Over IP.
are in a local area network or are connected through the In- ternet. 3 Privacy and security issues. As indicated in the previous section three sorts of |
|
Secure and Efficient Tunneling of MACsec for Modern Industrial Use
to one Local Area Network (LAN). Therefore we want to extend MACsec with the ability to tunnel or bridge its traffic between multiple local networks. |
|
S2-CAN: Sufficiently Secure Controller Area Network
Sufficiently Secure Controller Area Network. In Annual Computer Security. Applications Conference (ACSAC '21) December 6–10 |
|
Session Key Distribution Made Practical for CAN and CAN-FD
Automotive Communication Networks. ?. For enabling in-vehicle communication between Electronic Control Units (ECUs). ? Controller Area Network (CAN bus). |
|
Why Information Security is Hard -- An Economic Perspective
ways in which economics and computer security inter- act. 2 Network Externalities. Economists have devoted much effort to the study of networks such as |
|
Annual Computer Security Applications Conference (ACSAC)
17 nov 2004 · We look forward to seeing you at the 20th ACSAC, and hope should understand basic local area network terminology and fundamental |
|
Annual Computer Security Applications Conference (ACSAC)
Wireless LANs The 802 11b (Wi-Fi) Standard Wireless LAN architecture Wi-Fi Security Provisions Open System Authentication Shared Key Authentication |
|
Proceedings 26th Annual Computer Security Applications
And finally, we thank the larger ACSAC community for your continuing support Whether you are scheme, namely local correlation and network correlation |
|
Improve the Network Performance By using Parallel Firewalls - Free
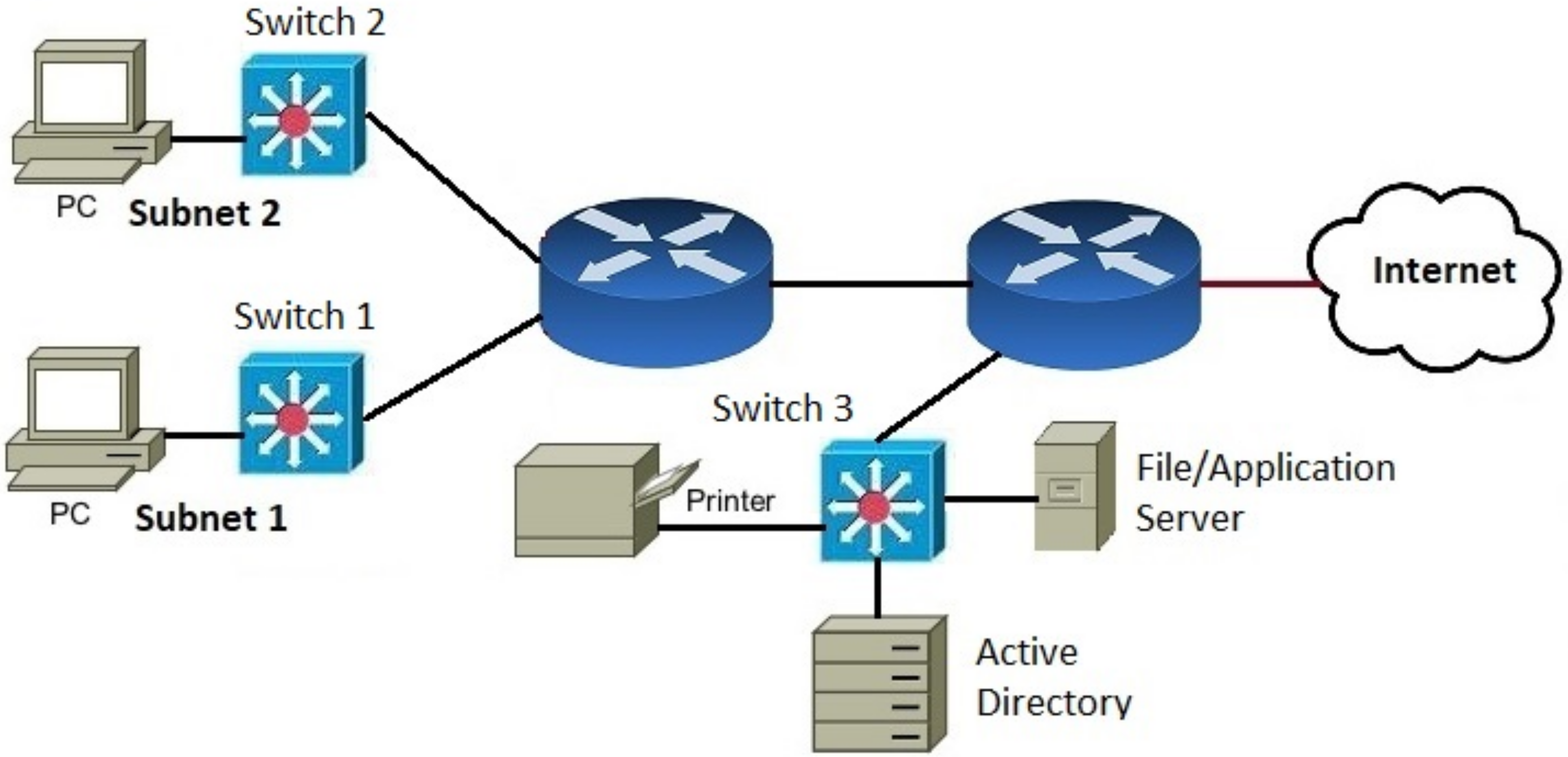
First scenario as shown in Figure 3 that represents a computer network that consists of four LANs connected by a backbone switch Each LAN consists of 100 |
|
Enhancing User Security for Devices in Wireless Personal and Local
talking of wireless personal and local area networks (WPANs) and wireless local area networks (WLAN), because the judgment of the security feeling depends in 26th Annual Computer Se- curity Applications Conference, ser ACSAC |
|
SWAN: A Secured Watchdog for Ad hoc Networks
5 jui 2006 · IJCSNS International Journal of Computer Science and Network Security, VOL 6 No 6, June 2006 209 Mobile ad hoc networks are temporal and local area networks with Security Applications Conference (ACSAC 1997), |
|
A Fine-Grained Intrusion Response and Recovery - Hal-Inria
26 sept 2019 · Computer Security Applications Conference (ACSAC '19), December 9–13, Internet with multiple Virtual Local Area Networks (VLANs), two |
|
TARP: Ticket-based Address Resolution Protocol - William Enck
addresses onto hosts hardware addresses within a local area network As such, its addresses are external to the local network (as determined by the subnet mask) are Application Conference (ACSAC), pages 229–249, Decem- ber 2004 |
![Chapter 12 Local Area Networks - [PPT Powerpoint] Chapter 12 Local Area Networks - [PPT Powerpoint]](https://reader024.documents.pub/reader024/reader/2021010820/56814e90550346895dbc390a/r-3.jpg?t\u003d1613870280)
![Chapter 12 Local Area Networks - [PPT Powerpoint] Chapter 12 Local Area Networks - [PPT Powerpoint]](https://d3i71xaburhd42.cloudfront.net/ec98dc94f3ae10ef45e5a9d2f393830644ce4571/3-Figure3-1.png)
![PDF] Wired versus wireless security: the Internet WAP and iMode PDF] Wired versus wireless security: the Internet WAP and iMode](https://onlinelibrary.wiley.com/cms/asset/7fb47d65-c3ed-4b1c-aec2-dd1488e00815/sec993-fig-0001-m.jpg)














![PDF] Wired versus wireless security: the Internet WAP and iMode PDF] Wired versus wireless security: the Internet WAP and iMode](https://onlinelibrary.wiley.com/cms/asset/60ada147-fa68-4379-94a3-44a2636fa163/sec1313-fig-0002-m.jpg)



![PDF] Wired versus wireless security: the Internet WAP and iMode PDF] Wired versus wireless security: the Internet WAP and iMode](https://i1.rgstatic.net/publication/2567025_Enhanced_Wired_Equivalent_Privacy_for_IEEE_80211_Wireless_LANs/links/541756940cf2218008bee3c6/largepreview.png)



![PDF] Wired versus wireless security: the Internet WAP and iMode PDF] Wired versus wireless security: the Internet WAP and iMode](https://i1.rgstatic.net/publication/221046246_Friends_of_An_Enemy_Identifying_Local_Members_of_Peer-to-Peer_Botnets_Using_Mutual_Contacts/links/0046351e7bd11cb7b0000000/largepreview.png)







![PDF] Wired versus wireless security: the Internet WAP and iMode PDF] Wired versus wireless security: the Internet WAP and iMode](https://ars.els-cdn.com/content/image/1-s2.0-S2352864820302649-fx1.jpg)








![PDF] Wired versus wireless security: the Internet WAP and iMode PDF] Wired versus wireless security: the Internet WAP and iMode](https://ars.els-cdn.com/content/image/1-s2.0-S1389128612003568-gr2.jpg)
