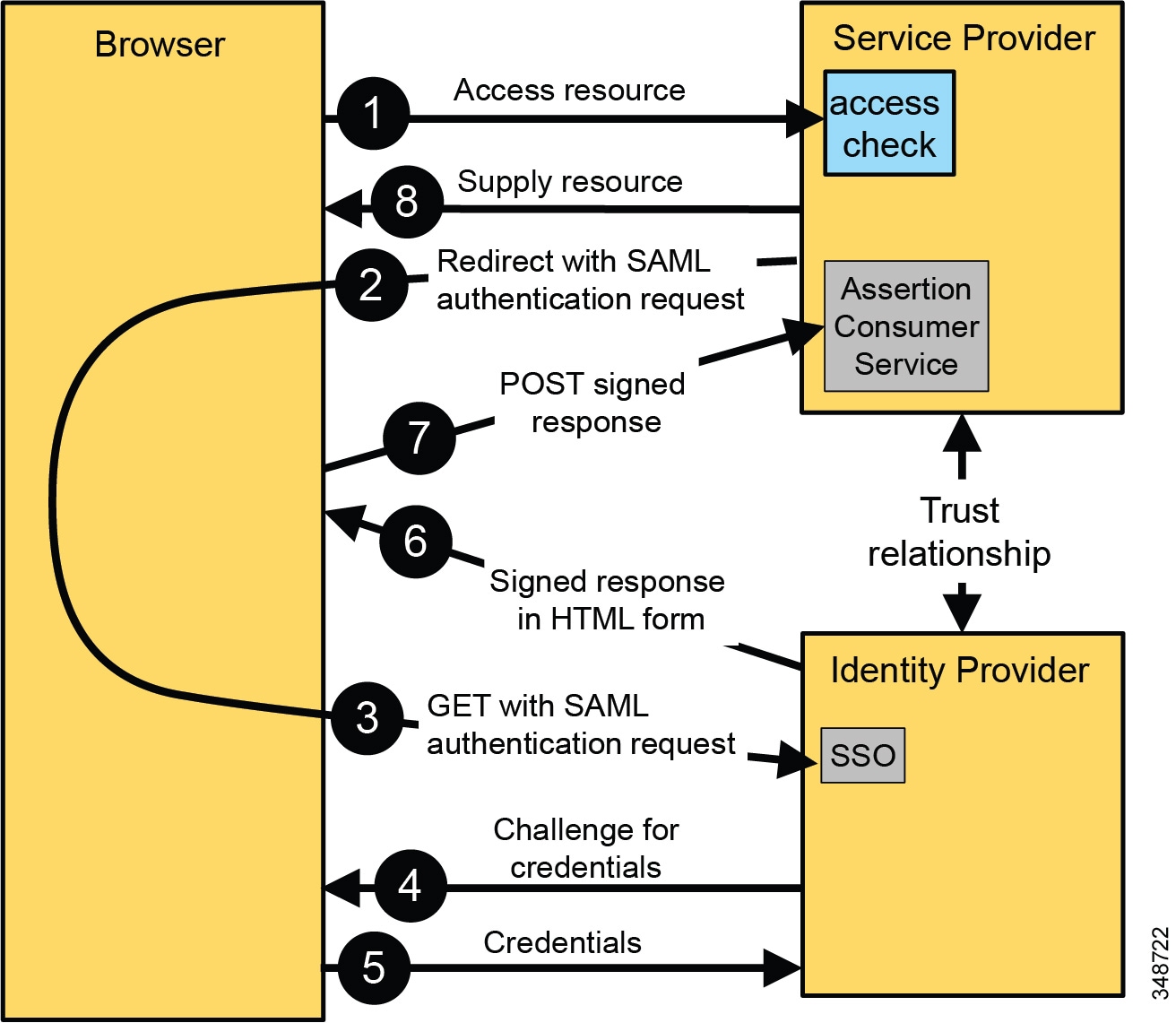
adfs tokenlifetime 0
What is TokenLifetime default 0 in ADFS?
TokenLifetime (Default 0 (which is 10 hours))
This parameter is configurable for each RP.
Whenever a user receives a RP Token, it will expire at some time.
At that time the user will have to go to the ADFS server again an request a new RP token.6 jan. 2012How long is ADFS token-signing certificate?
Objective.
When using ADFS 3.0, the Token-Signing Certificate that is generated during setup is, and can be, a Self-Signed Certificate.
By default, the Token-Signing Certificate will expire 1 year after it is created.What is the lifetime of token in ADFS?
The maximum lifetime of a token is 84 days, but AD FS keeps the token valid on a 14-day sliding window.
If the refresh token is valid for 8 hours, which is the regular SSO time, a new refresh token isn't issued.13 fév. 2024An authentication token is created, and is passed to different applications for seamless logins.
Within these tokens are claims about the identity of the user.
Therefore, while SSO is the process of authenticating across applications, ADFS is the technology that enables it.
Overview
You can specify the lifetime of an access, ID, or SAML token issued by the Microsoft identity platform. You can set token lifetimes for all apps in your organization, for multitenant (multi-organization) applications, or for service principals. We currently don't support configuring the token lifetimes for managed identity service principals. In Microsoft Entra ID, a policy object represents a set of rules that are enforced on individual applications or on all applications in an organization. Each policy type has a unique structure, with a set of properties that are applied to objects to which they're assigned. You can designate a policy as the default policy for your organization. The policy is applied to any application in the organization, as long as it isn't overridden by a policy with a higher priority. You also can assign a policy to specific applications. The order of priority varies by policy type. For examples, read examples of how to configure token lifetimes. learn.microsoft.com
License requirements
Using this feature requires a Microsoft Entra ID P1 license. To find the right license for your requirements, see Comparing generally available features of the Free and Premium editions. Customers with Microsoft 365 Business licenses also have access to Conditional Access features. learn.microsoft.com
Token lifetime policies for access, SAML, and ID tokens
Access tokens Clients use access tokens to access a protected resource. An access token can be used only for a specific combination of user, client, and resource. Access tokens cannot be revoked and are valid until their expiry. A malicious actor that has obtained an access token can use it for extent of its lifetime. Adjusting the lifetime of an access token is a trade-off between improving system performance and increasing the amount of time that the client retains access after the user's account is disabled. Improved system performance is achieved by reducing the number of times a client needs to acquire a fresh access token. The default lifetime of an access token is variable. When issued, an access token's default lifetime is assigned a random value ranging between 60-90 minutes (75 minutes on average). The default lifetime also varies depending on the client application requesting the token or if Conditional Access is enabled in the tenant. For more information, see Access token lifetime. SAML tokens SAML tokens are used by many web-based SaaS applications, and are obtained using Microsoft Entra ID's SAML2 protocol endpoint. They are also consumed by applications using WS-Federation. The default lifetime of the token is 1 hour. From an application's perspective, the validity period of the token is specified by the NotOnOrAfter value of the element in the token. After the validity period of the token has ended, the client must initiate a new authentication request, which will often be satisfied without interactive sign in as a result of the Single Sign On (SSO) Session token. The value of NotOnOrAfter can be changed using the AccessTokenLifetime parameter in a TokenLifetimePolicy. It will be set to the lifetime configured in the policy if any, plus a clock skew factor of five minutes. The subject confirmation NotOnOrAfter specified in the element is not affected by the Token Lifetime configuration. ID tokens ID tokens are passed to websites and native clients. ID tokens contain profile information about a user. An ID token is bound to a specific combination of user and client. ID tokens are considered valid until their expiry. Usually, a web application matches a user's session lifetime in the application to the lifetime of the ID token issued for the user. You can adjust the lifetime of an ID token to control how often the web application expires the application session, and how often it requires the user to be re-authenticated with the Microsoft identity platform (either silently or interactively). learn.microsoft.com
Token lifetime policies for refresh tokens and session tokens
You cannot set token lifetime policies for refresh tokens and session tokens. For lifetime, timeout, and revocation information on refresh tokens, see Refresh tokens. Important As of January 30, 2021 you cannot configure refresh and session token lifetimes. Microsoft Entra no longer honors refresh and session token configuration in existing policies. New tokens issued after existing tokens have expired are now set to the default configuration. You can still configure access, SAML, and ID token lifetimes after the refresh and session token configuration retirement. Existing token's lifetime will not be changed. After they expire, a new token will be issued based on the default value. learn.microsoft.com
Configurable token lifetime properties
A token lifetime policy is a type of policy object that contains token lifetime rules. This policy controls how long access, SAML, and ID tokens for this resource are considered valid. Token lifetime policies cannot be set for refresh and session tokens. If no policy is set, the system enforces the default lifetime value. learn.microsoft.com
Policy evaluation and prioritization
You can create and then assign a token lifetime policy to a specific application and to your organization. Multiple policies might apply to a specific application. The token lifetime policy that takes effect follows these rules: •If a policy is explicitly assigned to the organization, it's enforced. •If no policy is explicitly assigned to the organization, the policy assigned to the application is enforced. •If no policy has been assigned to the organization or the application object, the default values are enforced. (See the table in Configurable token lifetime properties.) A token's validity is evaluated at the time the token is used. The policy with the highest priority on the application that is being accessed takes effect. All timespans used here are formatted according to the C# TimeSpan object - D.HH:MM:SS. So 80 days and 30 minutes would be 80.00:30:00. The leading D can be dropped if zero, so 90 minutes would be 00:90:00. learn.microsoft.com
REST API reference
You can configure token lifetime policies and assign them to apps using Microsoft Graph. For more information, see the tokenLifetimePolicy resource type and its associated methods. learn.microsoft.com
Cmdlet reference
These are the cmdlets in the Microsoft Graph PowerShell SDK. learn.microsoft.com
Next steps
To learn more, read examples of how to configure token lifetimes. learn.microsoft.com
|
Implementing a Zero Trust approach with Azure Active Directory
This white paper is a reflection on the term Zero Trust (Networks) – as perceived Active Directory Federation Services (ADFS) a server role of Windows ... |
|
ADFS and Web Application Proxy ADFS intranet scenarios
ADFS SSO cookie and RP token lifetime Set-AdfsRelyingPartyTrust -TokenLifetime [minutes] ... $certFile = '\dcpublicadfs-{0}-#01.cer' -f $domain. |
|
Remediation and Hardening Strategies for Microsoft 365 to Defend
9 ene 2021 Steal the Active Directory Federation Services (AD FS) token-signing ... Since AD FS v3.0 (Windows Server 2012 R2+) a group managed service ... |
|
Deploying OAuth with Cisco Collaboration Solution Release 12.0
(Information on how to change token lifetime is covered later in this paper). Account Credentials. If all UC services are enabled for OAuth (including Cisco |
|
VMware Docs
11 abr 2019 For information about configuring SCCM for zero touch ISO images ... Obtain the appropriate Active Directory Federated Services (ADFS) ... |
|
VSphere Authentication - VMware vSphere 7.0
27 jul 2022 Configure vCenter Server Identity Provider Federation for AD FS 114 ... Level 2 : level 0 + Account disabled flag Account. |
|
VSphere Authentication - VMware vSphere 7.0
16 sept 2021 Directory Federation Services (AD FS) and vCenter Single ... For example AD FS. ... Level 2 : level 0 + Account disabled flag |
|
Citrix-cloud.pdf
25 jul 2022 0 - Installation completed successfully ... Use federation to an identity provider of your choice including ADFS Okta |
|
CIS Microsoft Azure Foundations Benchmark
15 feb 2019 authentication information' is not set to "0" (Not Scored) . ... Azure AD authentication supports ADFS (domain federation) or native. |
|
VSphere Security - VMware vSphere 6.0
4 oct 2017 Services (ADFS) SAML service provider you have to edit the ... The number must be greater than 0. ... Maximum bearer token lifetime. |
|
ADFS and Web Application Proxy ADFS intranet scenarios - Ondrej
ADFS 1 0 Windows 2003 R2 included runs in IIS SAML 1 1 ADFS 1 1 Windows 2008 ADFS SSO cookie and RP token lifetime ▫ Default ADFS SSO cookie |
|
CLAIMS -BASED IDENTITY AND ACCESS CONTROL - Microsoft
For example, if ADFS sets the SAML token lifetime to ten minutes, and the LogonTokenCacheExpirationWin- dow property in SharePoint is set to two minutes, |
|
Configuring Claims-based Authentication for Microsoft Dynamics
Configure the AD FS server for claims-based authentication By using Windows PowerShell, you can change the TokenLifetime property for the relying party |
|
Relativity Authentication v10 - Relativity Documentation
1 6 2 Configuring ADFS as a SAML 2 0 identity provider 28 o Implicit flow tokens must match Relativity's token lifetime of 10 hours (600), after which the user |
|
Deploying OAuth with Cisco Collaboration Solution Release 120
(Information on how to change token lifetime is covered later in this paper) Account Credentials If all UC services are enabled for OAuth (including Cisco Unity |
|
For Microsoft - OnTime Group Calendar
It will install a Windows service 'OnTimeMS ACS' that offers ADFS logon authentication Token expiry – the OnTime users authentication token lifetime in days |
|
IOT Identity Management Team - 2021 - INgov
Azure AD integrated applications including Office 365 as well as ADFS, MFA, Azure token lifetime evaluation, conditional access, least privilege access and |
|
StoreFront 1912 - Citrix Product Documentation
3 mar 2020 · Microsoft ADFS v4 0 (Windows Server 2016) à l'aide de liaisons SAML uniquement (et non Définissez tokenLifeTime sur la valeur souhaitée |














%20Servers.png)