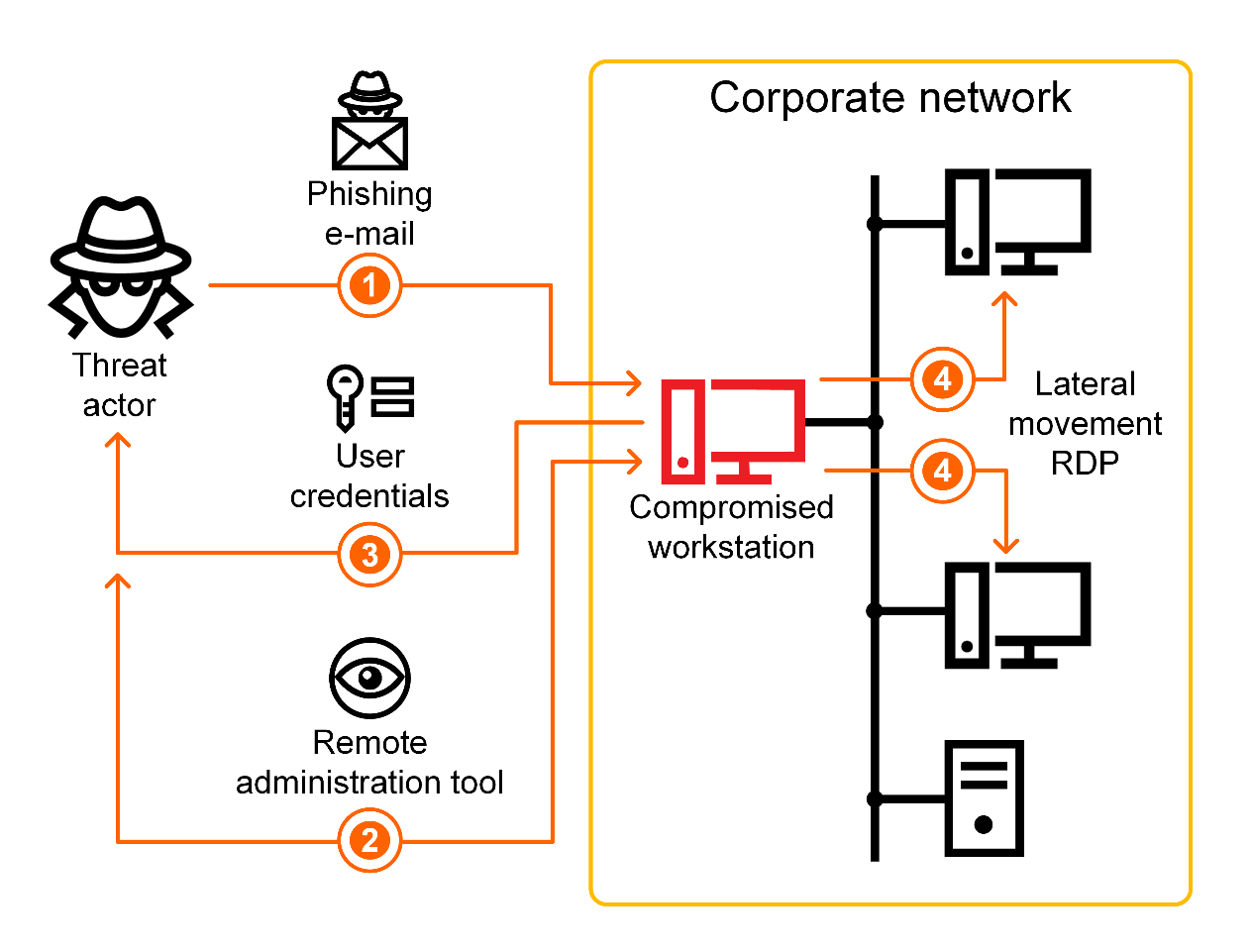
cyber attack vectors 2019
|
Cyber Threats 2019: A Year in Retrospect
Our 2018: A Year in Retrospect report illustrated the rising trend of BEC attacks where a threat actor either hijacks or closely imitates ('spoofs') a |
What are the top 3 attack vectors?
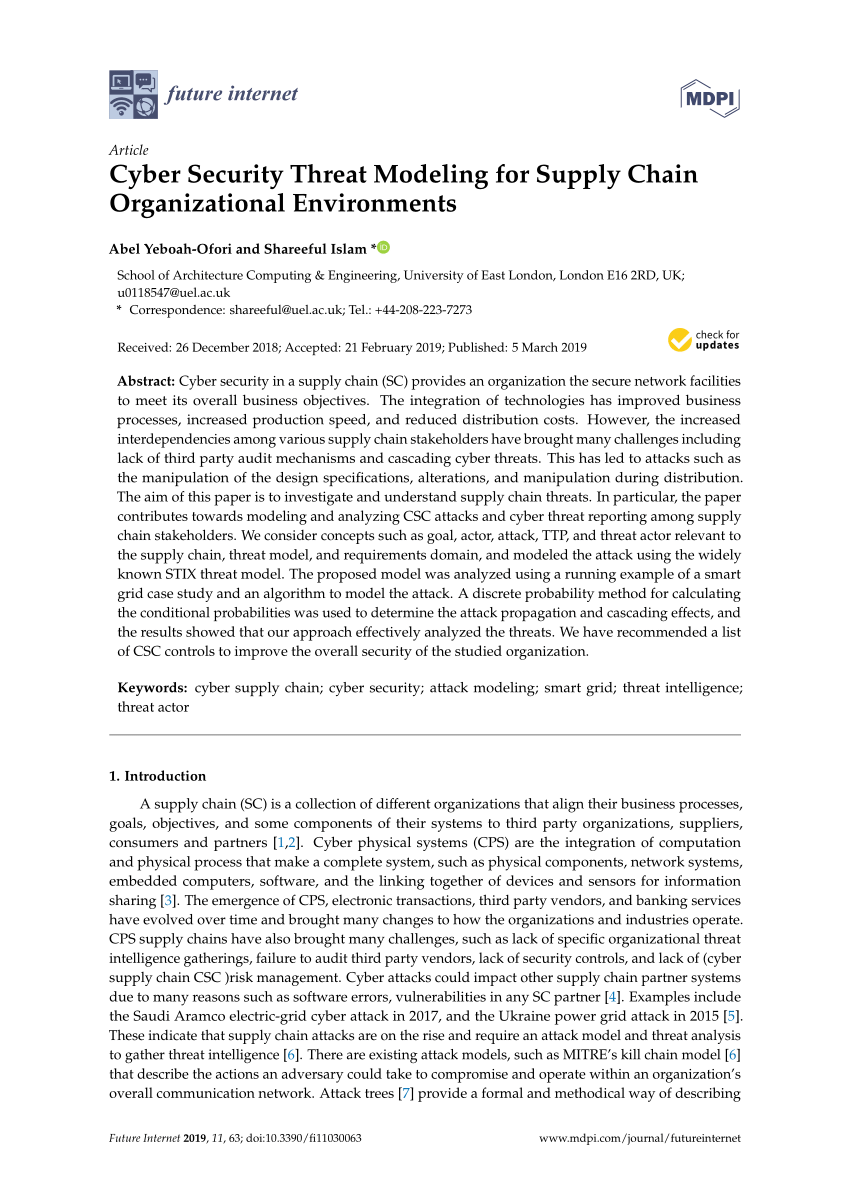
The most common attack vectors include malware, viruses, email attachments, web pages, pop-ups, instant messages, text messages, and social engineering.
What are cyber attack vectors?
An attack vector, or threat vector, is a way for attackers to enter a network or system.
Common attack vectors include social engineering attacks, credential theft, vulnerability exploits, and insufficient protection against insider threats.What is the big data breach in 2019?
In 2019, Paige Thompson, a former Amazon Web Services (AWS) employee, hacked the Capital One servers and gained access to over 100 million customer account records and credit card applications from as far back as 2005.
Of these records, these included: Bank account numbers.
Names.
|
Cyber Attack Trends: 2019 Mid-Year Report
Many of such MageCart style attacks utilize similar supply chain attack vectors. The sharp increase in supply chain attacks has brought the US Department of |
|
SANS 2019 State of OT/ICS Cybersecurity Survey - Forescout
For 2019 the leading vectors are physical |
|
ENISA ETL2020 - DDoS
The observations of attack vectors in Q3 2019 were similar with SYN floods the top vector followed by UDP |
|
MDCG 2019-16 Rev.1
Cybersecurity Requirements included in Annex I of the Medical Devices Regulations The list of known vulnerabilities and attack vectors is the basis for ... |
|
Ninth annual cost of cybercrime study - unlocking the value of
Technology Vision 2019 Accenture. https://www.accenture.com/us-en/insights/technology/cybersecurity-digital-ecosystem. 3. Securing the digital economy |
|
2019 Cyber Threatscape Report I Accenture
As threat actors face effective defenses to tried and tested attack vectors they adapt and switch to try out new tactics |
|
Vector Cybersecurit Symposium 2019 - Challenges in Automotive
3 avr. 2019 Challenges of Automotive Cybersecurity for Automated Driving |
|
Cyber Risks to Next Generation 9-1-1 November 2019
they also represent new vectors for attack that can disrupt or disable PSAP Cybersecurity1 risks occur when a threat exploits a vulnerability ... |
|
ENISA ETL2020 - Malware
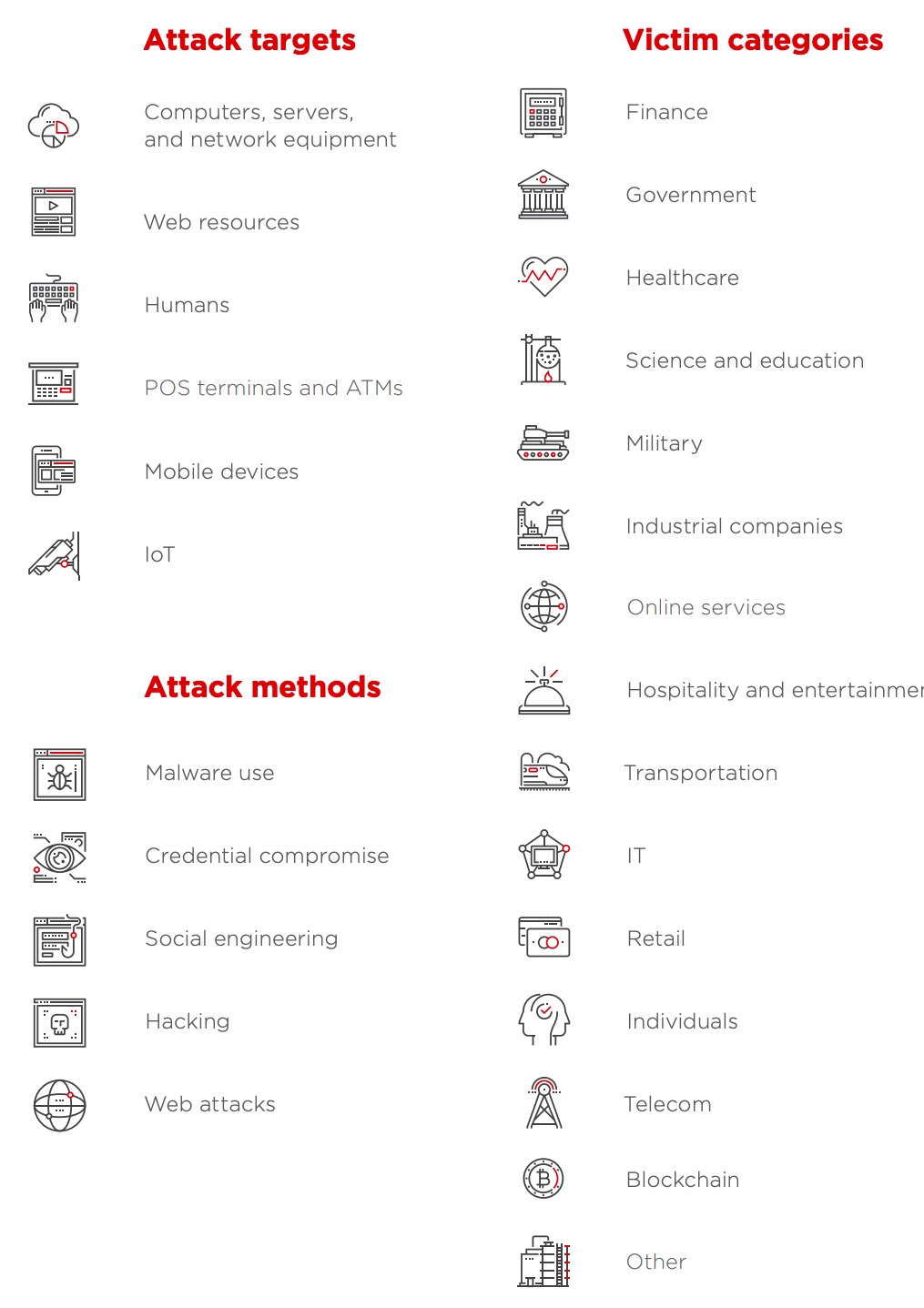
Malware is a common type of cyberattack in the form of malicious software. Web and e-mail protocols were the most common initial attack vectors. |
|
State of Cybersecurity 2019
The following are the key survey findings about cybersecurity attacks awareness and governance: •. Consistency reigns across threat actors and attack vectors. |
|
Cyber Attack Trends: 2019 Mid-Year Report
The first half of 2019 demonstrated that no environment is immune to cyber attacks The supply chain attack vector has been a growing trend for a while but the |
|
Cyber Security Report 2020 - National Technology Security
7 REVIEW OF 2019 CYBER THREAT PREDICTIONS While email is the top attack vector, bad actors are using a variety of tricks to give up |
|
2019 Cyber Threatscape Report I Accenture
As threat actors face effective defenses to tried and tested attack vectors, they adapt and switch to try out new tactics, techniques and procedures (TTPs) And this |
|
Cyber Attack Trends Analysis Report
In this first installment of the 2019 Security Report we review the latest threats facing organizations in the With data drawn from our ThreatCloud World Cyber Threat Map and our with more than one significant goal or attack vector |
|
McAfee Labs Threats Report August 2019
In the first quarter of 2019, ransomware attacks grew by 118 , new attack vectors being utilized by various actors and against cyberattacks via IoT |
|
State of Cybersecurity Report 2019 - Wipro
corrupted pen drive, charging IoT devices are common vectors for malware proliferation The financial loss due to cybersecurity incidents in the energy, natural |




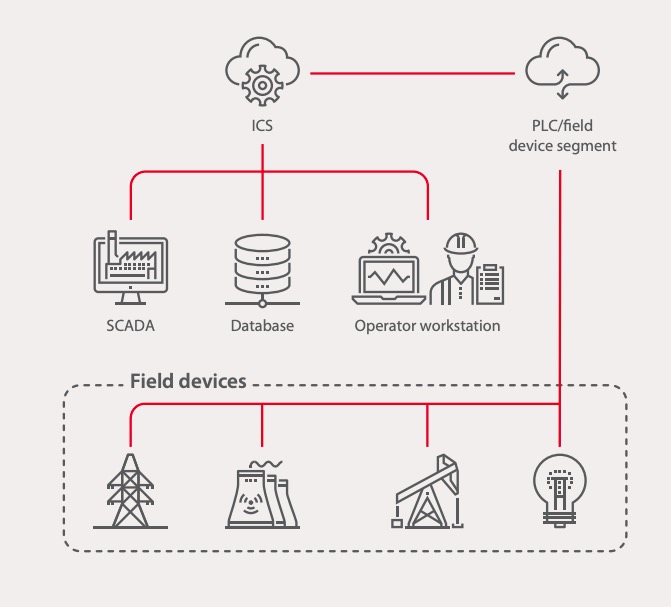





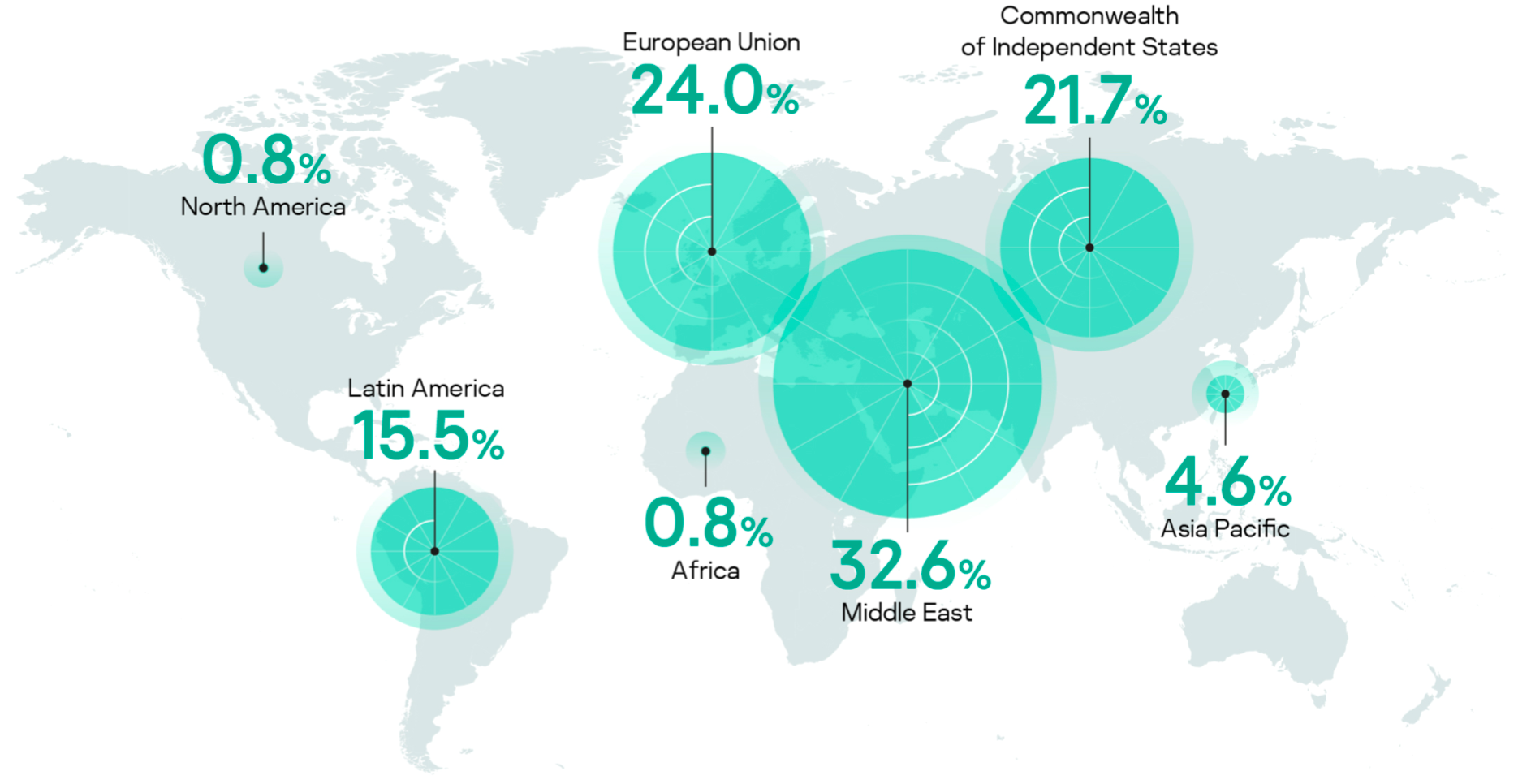





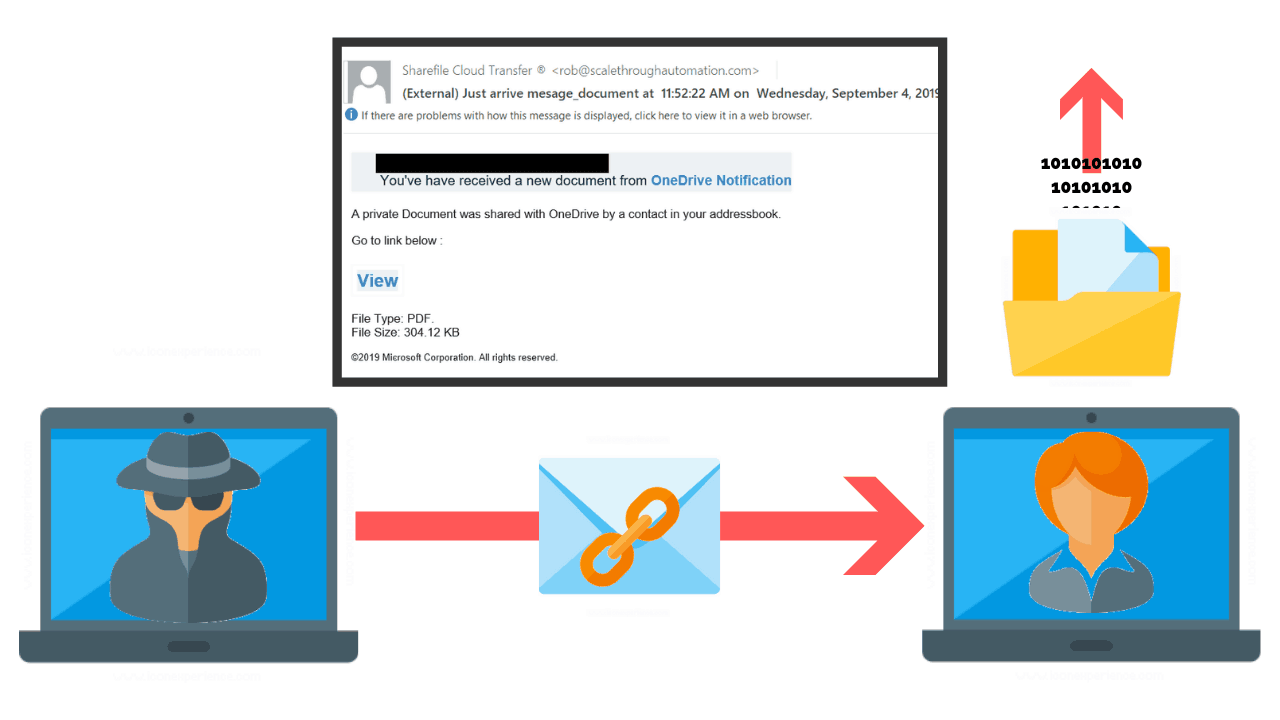

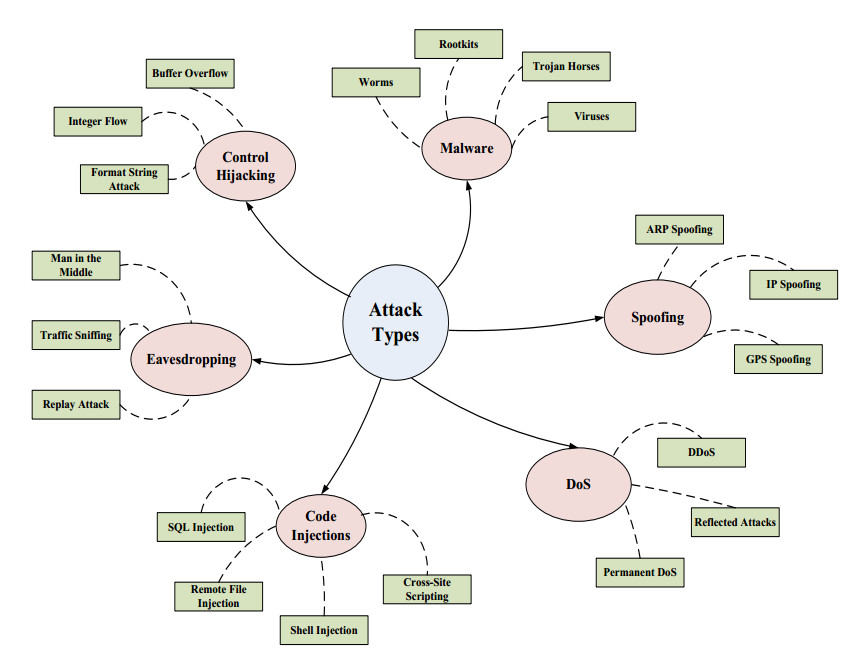



![300+ Terrifying Cybercrime \u0026 Cybersecurity Statistics [2021 EDITION] 300+ Terrifying Cybercrime \u0026 Cybersecurity Statistics [2021 EDITION]](https://i1.rgstatic.net/publication/338668641_Cyber_security_risks_in_globalized_supply_chains_conceptual_framework/links/5e2678ae92851c89c9b5ac66/largepreview.png)