format string attack prevention
|
Preventing Format-String Attacks via Automatic and Efficient
We propose preventing format-string attacks with a combi- nation of static dataflow analysis and dynamic white-lists of safe address ranges. |
|
A Comparison of Techniques to Prevent Format String Attacks
This makes some software very vulnerable to attacks. Format strings vulnerabilities are caused by software programmers who fail to check externally supplied |
| Minos: Control Data Attack Prevention Orthogonal to Memory Model |
|
String Oriented Programming: When ASLR is not enough
Format string exploits are often overlooked Define a way to deterministically exploit format string bugs ... Data Execution Prevention (DEP). |
|
String Oriented Programming: When ASLR is not Enough
26 janv. 2013 tion Prevention (DEP) stack canaries |
|
Prevention and Detection of Stack Buffer Overflow Attacks
12 août 2005 addition to the buffer overflow attack described above a format string attack in C can be used to overwrite the return address. |
|
Proceedings of the 10 USENIX Security Symposium
elaborates on the printf format string vulnerability. Section 3 describes FormatGuard; prevent the attacker from injecting spurious % direc-. |
|
Exploit Prevention Quo Vadis?
That is how the control flow is modified to execute the malicious code. In case of format string vulnerability [24] the attacker can write an almost arbitrary |
| Minos: Control Data Attack Prevention Orthogonal to Memory Model |
|
Software Vulnerabilities Prevention and Detection Methods: A
Keywords: Software vulnerability Prevention/Detection Methods |
|
Preventing Format-String Attacks via Automatic and Efficient
ABSTRACT We propose preventing format-string attacks with a combi- nation of static dataflow analysis and dynamic white-lists of safe address ranges |
|
Exploiting Format String Vulnerabilities - CS155
1 sept 2001 · If an attacker is able to provide the format string to an ANSI C format function in part or as a whole a format string vulnerability is present |
|
Transparent Run-Time Prevention of Format-String Attacks Via
Abstract Format-string attack is one of the few truly threats to software secu- rity Many previous methods for addressing this problem rely on program |
|
Format-String Vulnerability - Fengwei Zhang
Format string attack ? How to exploit the vulnerability printf() scans the format string and prints out each character until “ ” is encountered |
|
Format string attacks - People
26 sept 2011 · Format string bugs allow arbitrary memory writes Conclusion: If an attacker has control over the format-string argument of printf then |
|
Format String Vulnerability and Attack - Yajin Zhou
value of len address of len Addr of format string return address saved ebp ebp of printf High Low Internal pointer maintained by printf Page 8 |
|
Format String Vulnerability printf ( user input ); - Syracuse University
Format String Vulnerability: 1 Format String Vulnerability parameters requested by the format string from the stack control the address |
|
Blind Format String Attacks - Technische Universität München
In addi- tion we show a way to exploit format string vulnerabilities on the heap where we can not benefit from direct destination control i e we can |
|
Format String Vulnerabilities
26 fév 2019 · A Comparison of Techniques to Prevent Format String Attacks Format Strings What is a format string? A format string uses a simple |
|
FormatGuard: Automatic Protection From printf Format String
In June 2000 a major new class of vulnerabilities called “format bugs” was discovered when an vulnerability in WU-FTP appeared that acted almost like a |
How format string attacks can be prevented?
Preventing format string attacks
If possible, make the format string a constant. If the above isn't possible, then always specify a format string as part of the program rather than as an input. You can fix most format string vulnerabilities by simply specifying %s as the format string.What is format string attack in cyber security?
A format string vulnerability is a bug where user input is passed as the format argument to printf , scanf , or another function in that family. The format argument has many different specifies which could allow an attacker to leak data if they control the format argument to printf .What causes format string attack?
The attack could be executed when the application doesn't properly validate the submitted input. In this case, if a Format String parameter, like %x, is inserted into the posted data, the string is parsed by the Format Function, and the conversion specified in the parameters is executed.- While buffer overflow attacks exist due to failure to perform stable bounds checks, format string attacks exist when a developer fails to perform reliable input validation checks.
|
Preventing Format-String Attacks via Automatic and Efficient
We propose preventing format-string attacks with a combi- nation of static dataflow analysis and dynamic white-lists of safe address ranges The dynamic nature |
|
Format String Vulnerability printf ( user input ); - Syracuse University
Format String Vulnerability: 1 Format parameters requested by the format string from the stack printf ("a has 2 Attacks on Format String Vulnerability To avoid long format strings, we can use a width specification of the format indicators |
|
Automated Format String Attack Prevention for Win32/X86 - ACSAC
Lisbon casts the format string attack prevention problem as an input argument list bound checking problem To reduce the run-time checking overhead, Lisbon |
|
String Oriented Programming Exploring Format String Attacks
Additional protection mechanisms prevent many existing Format string exploits are often overlooked Stack-based buffer overflow as initial attack vector |
|
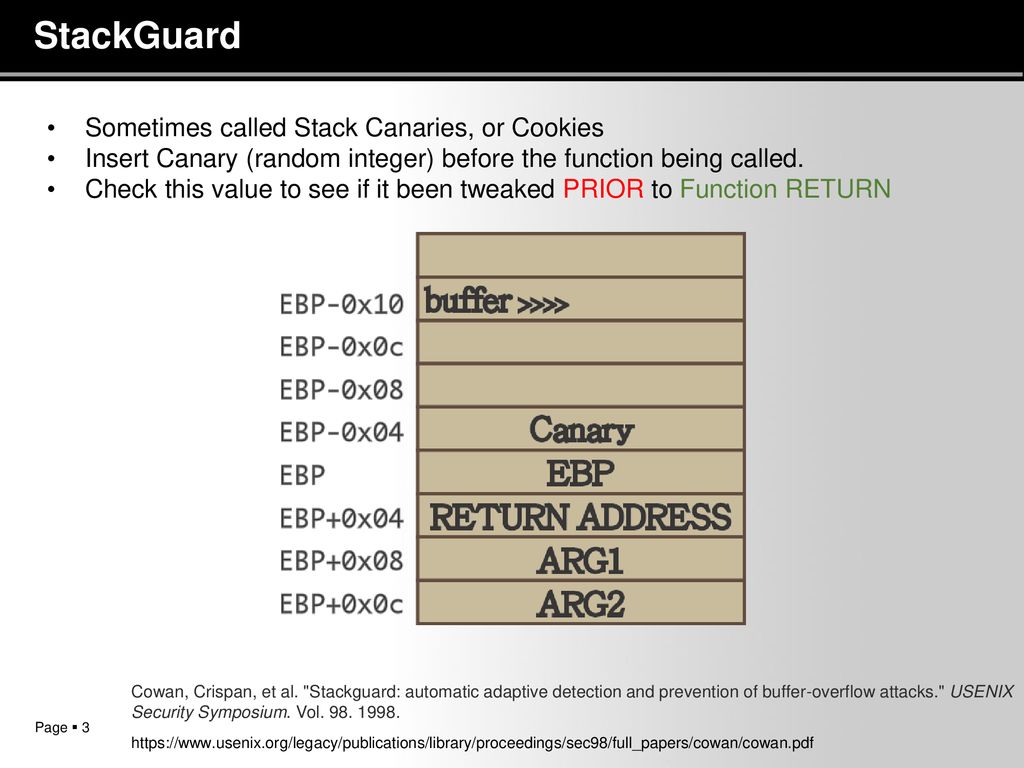
Automatic Protection From printf Format String Vulnerabilities
FormatGuard then aborts the process to prevent the attacker from taking control, similar to the way StackGuard handles buffer overflow attacks [8, 6] 3 3 |
|
Coalesce Model to Prevent Format String Attacks - International
against to Format String vulnerabilities can avoid result due to working of Format eight novel approaches to prevent format string attacks and combination of |
|
Transparent Run-Time Prevention of Format-String Attacks Via
Transparent Run-Time Prevention of Format-String Attacks Via Dynamic Taint and Flexible Validation Zhiqiang Lin, Nai Xia, Guole Li, Bing Mao, and Li Xie |
|
動態格式化字串攻擊偵測方法之研究
In order to prevent format string vulnerabilities, the behavior of accessing argument, he can exploit format string vulnerabilities to attack programs by providing |
|
Software Vulnerabilities - Information Security CS 526
Format string attack • Integer Software vulnerability enables the attacker to run with privileges of Input checking would prevent that, but not this – IIS first |









![Top PDF History of Buffer Overflow [lucid78] pdf - 1Library Top PDF History of Buffer Overflow [lucid78] pdf - 1Library](https://i1.rgstatic.net/publication/337429710_Exploiting_stack-based_buffer_overflow_using_modern_day_techniques/links/5e6820034585153fb3d5ce40/largepreview.png)