format string overwrite return address
|
Windows 2000 Format String Vulnerabilities
formatted in by printf'ing a format string to a variable. To clarify: For example on Intel |
|
Exploiting Format String Vulnerabilities
1 sept. 2001 In normal buffer overflows we overwrite the return address of a function frame on the stack. As the function that owns this frame returns it ... |
|
Untitled
22 mar. 2017 started format strings exploits ... format string overwrite: setup ... buffer starts 16 bytes above printf return address. |
|
Format String & Double-Free Attacks
argument pointer points to the front of your format string. › Put a %n at the end and overwrite the return address to point at the shellcode in the buffer. |
|
Cornell CS
15 feb. 2001 The exploitation of format string bugs represents a new technique for ... overwrite return addresses on the stack internal linkage tables ... |
|
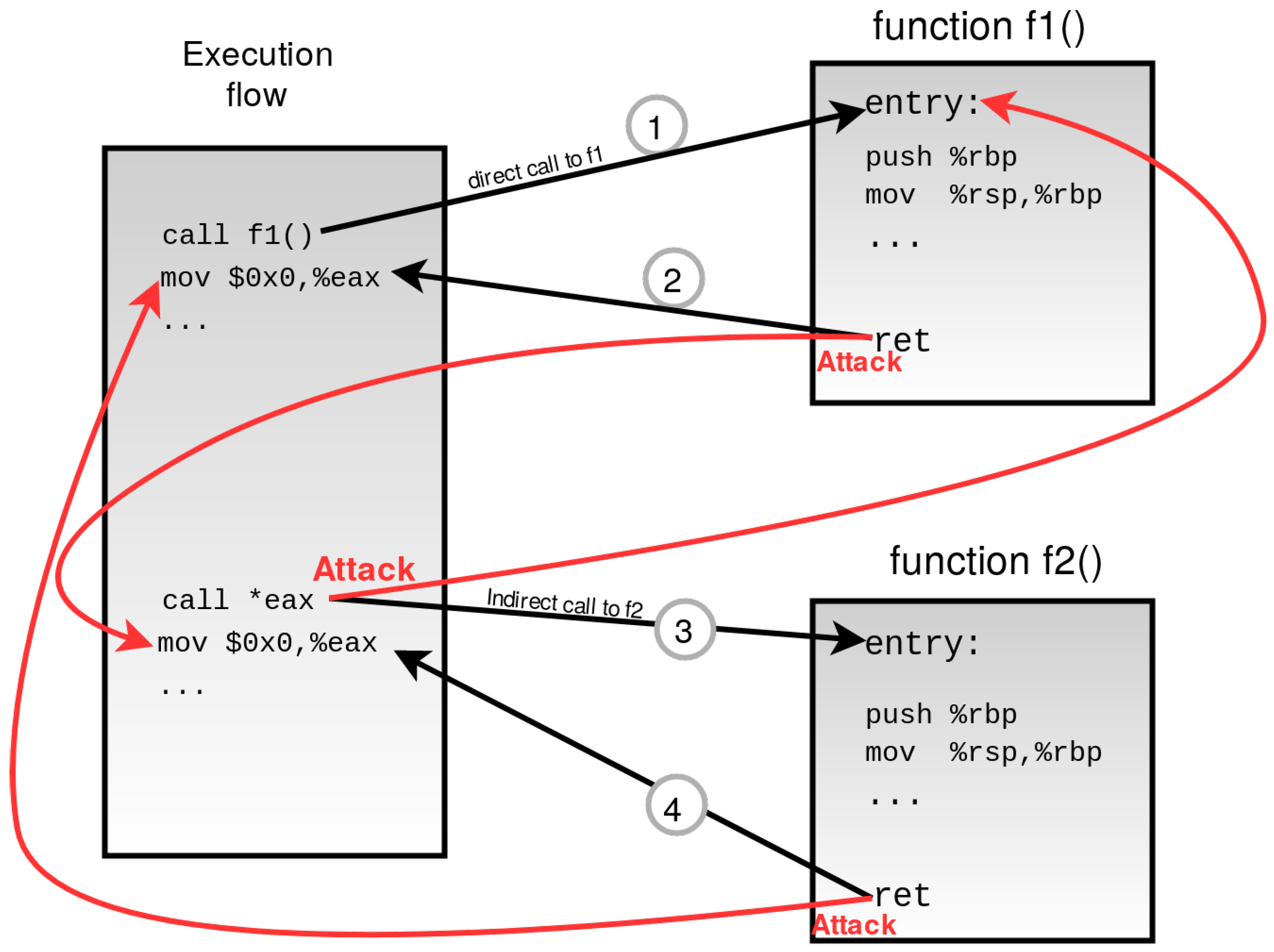
Return-to-libc
if we overwrite the return address with an address to a function in a libc library and overwriting the Remember in the format strings exploit tutorial. |
|
Raluca Popa Spring 2018 CS 161 Computer Security Discussion 1
22 ian. 2018 A format-string vulnerability can allow an attacker to overwrite a saved return address even when stack canaries are enabled. 3. If you have ... |
|
Advanced Format String Attacks
perform string formatting leading to the potential to Point format string at overwrite address and write address of shellcode to end of string. |
|
Attacking the stack
Format string attacks were only discovered (invented?) in 2000 2. overwriting the return address on the stack to this place where the shell code is. |
|
Format Strings Shellcode and Stack Protection - UCSD CSE
Format String Vulnerabilities: Writing ? Value that we really want to overwrite is likely a pointer (like the return address) |
|
Exploiting Format String Vulnerabilities - CS155
1 sept 2001 · In normal buffer overflows we overwrite the return address of a function frame on the stack As the function that owns this frame returns it |
|
Format String Vulnerability printf ( user input ); - Syracuse University
The function retrieves the parameters requested by the format string from the stack printf ("a has value d b has value d c is at address: 08x\n" |
|
Format Strings
“Format strings” are the control strings that are passed to the printf() global canary or overwriting a return address without touching the canary |
|
Format-String Vulnerability - Fengwei Zhang
printf() scans the format string and prints out each character until “ ” is encountered Goal : To modify the return address of the vulnerable code |
|
Slides
1 avr 2017 · started format strings exploits format string overwrite: setup buffer starts 16 bytes above printf return address |
|
Blind Format String Attacks - Technische Universität München
tion we show a way to exploit format string vulnerabilities on the heap overwrite everything between this buffer and the return address |
|
Format String Vulnerabilities
26 fév 2019 · Nice Arbitrary Code Execution It's hard to overwrite the return address like in a buffer overflow Instead we overwrite a entry |
|
Format String & Double-Free Attacks - Repository [Root Me
A simple format string vulnerability: snprintf copies data from the format string until it reaches a ' ' Overwriting the Return Address |
|
Format String Vulnerabilities and Exploitation - NCC Group Research
Windows 2000 Format String Vulnerabilities By David Litchfield For example on Intel they could overwrite a saved return address |
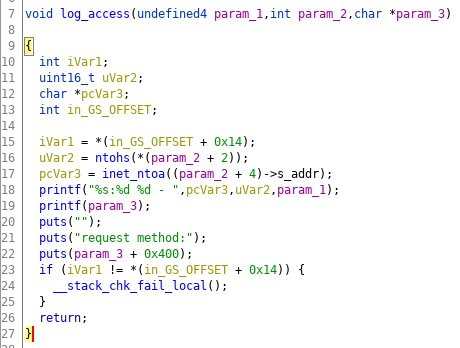
What is a format string vulnerability?
What is a Format String Vulnerability? Often found in C language programs, it refers to a bug found in the printf() function. It is widely used to transport data, which could be ASCII text strings, to the standard output. When used properly, text strings can lead to effective and automated conversion types.- While buffer overflow attacks exist due to failure to perform stable bounds checks, format string attacks exist when a developer fails to perform reliable input validation checks.
|
Format string overwrite
22 mar 2017 · 20786c3631302520 16 bytes of stack after return address format string overwrite: GOT buffer starts 16 bytes above printf return address |
|
Format String Vulnerabilities and Exploitation - NCC Group Research
output This is done by substituting format specifiers in the format string for values or data For example, on Intel, they could overwrite a saved return address |
|
Format String Vulnerability printf ( user input ); - Syracuse University
parameters requested by the format string from the stack printf ("a has value d Overwrite return addresses on the stack, function pointers, etc – However, the |
|
Exploiting Format String Vulnerabilities - CS155 Computer and
1 sept 2001 · In normal buffer overflows we overwrite the return address of a function frame on the stack As the function that owns this frame returns, it returns |
|
Format String Attacks
6 ABSTRACT The cause and implications of format string vulnerabilities are discussed Overwrite a return address to point to some buffer with shell code in it |
|
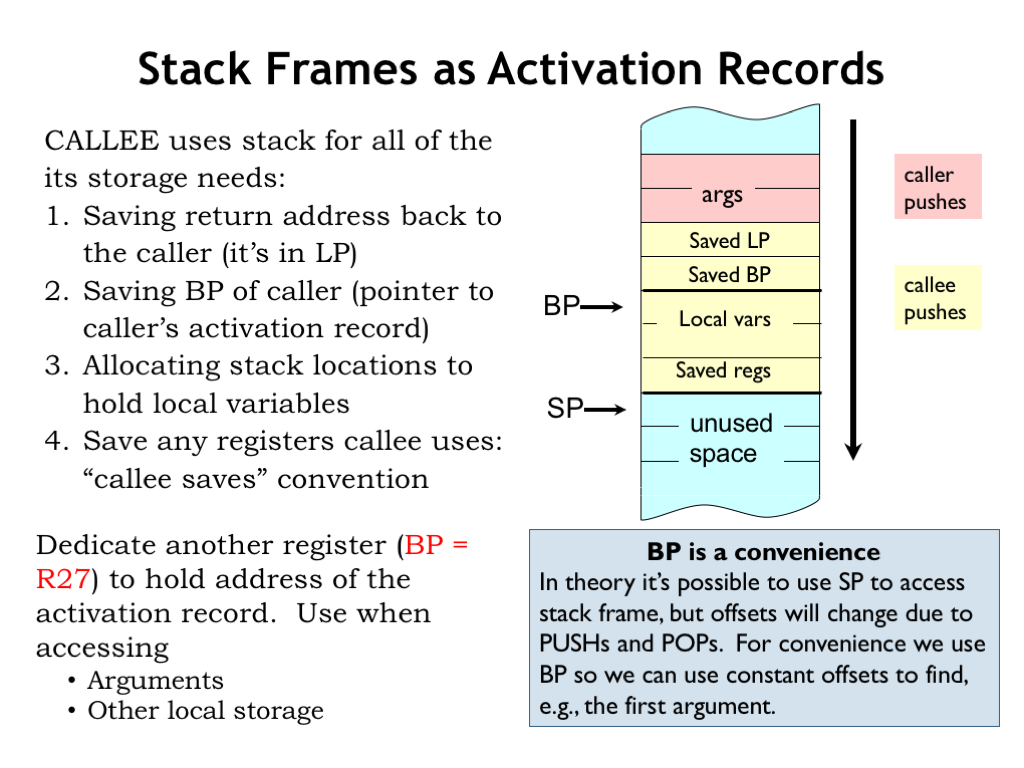
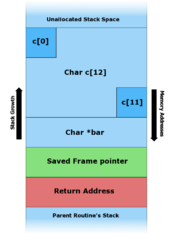
05 - Format Strings, Double-Free
Parameters Return Address Saved Frame Pointer Local Variables Saved Registers Page 7 › Arguments are pushed to the stack in reverse order › snprintf copies data from the format string until it Overwriting the Return Address |
|
Format String Exploitation
Format strings vulnerability exists in most of the printf family below is some Notice that the items the program returns are values and addresses saved on the the second half of the address from the first same as the single byte overwrite |
|
Blind Format String Attacks - TUM
tion, we show a way to exploit format string vulnerabilities on the heap, where we can not overwrite everything between this buffer and the return address |
|
Format Strings, Shellcode, and Stack Protection - CSE 127
Format String Vulnerabilities: Writing ▫ Value that we really want to overwrite is likely a pointer (like the return address) – How to write a large 4-byte integer |
|
Attacking the stack
Format string attacks were only discovered (invented?) in 2000, after people 2 overwriting the return address on the stack to this place where the shell code is |
![MOSUT] Format String Attacks MOSUT] Format String Attacks](https://image.slidesharecdn.com/aj-140116200425-phpapp01/95/mosut-format-string-attacks-14-638.jpg?cb\u003d1389904660)
![MOSUT] Format String Attacks MOSUT] Format String Attacks](https://image.slidesharecdn.com/aj-140116200425-phpapp01/95/mosut-format-string-attacks-13-638.jpg?cb\u003d1389904660)
![MOSUT] Format String Attacks MOSUT] Format String Attacks](http://etutorials.org/shared/images/tutorials/tutorial_149/NSA_1319.gif)






![MOSUT] Format String Attacks MOSUT] Format String Attacks](https://slideplayer.com/slide/17744430/105/images/3/StackGuard+Sometimes+called+Stack+Canaries%2C+or+Cookies.jpg)

![MOSUT] Format String Attacks MOSUT] Format String Attacks](https://tuonilabs.files.wordpress.com/2017/05/screenshot.png?w\u003d840)

![MOSUT] Format String Attacks MOSUT] Format String Attacks](https://i1.rgstatic.net/publication/311515579_Memory_Corruption-Basic_Attacks_and_Counter_Measures/links/584a893d08aeb19dcb7583a2/largepreview.png)

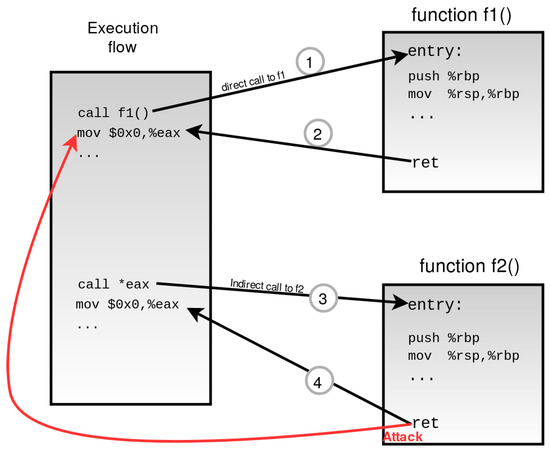
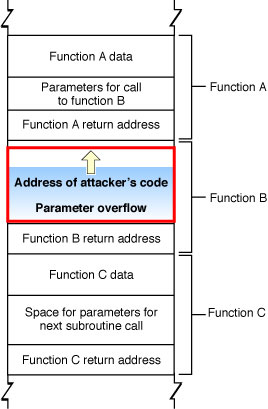




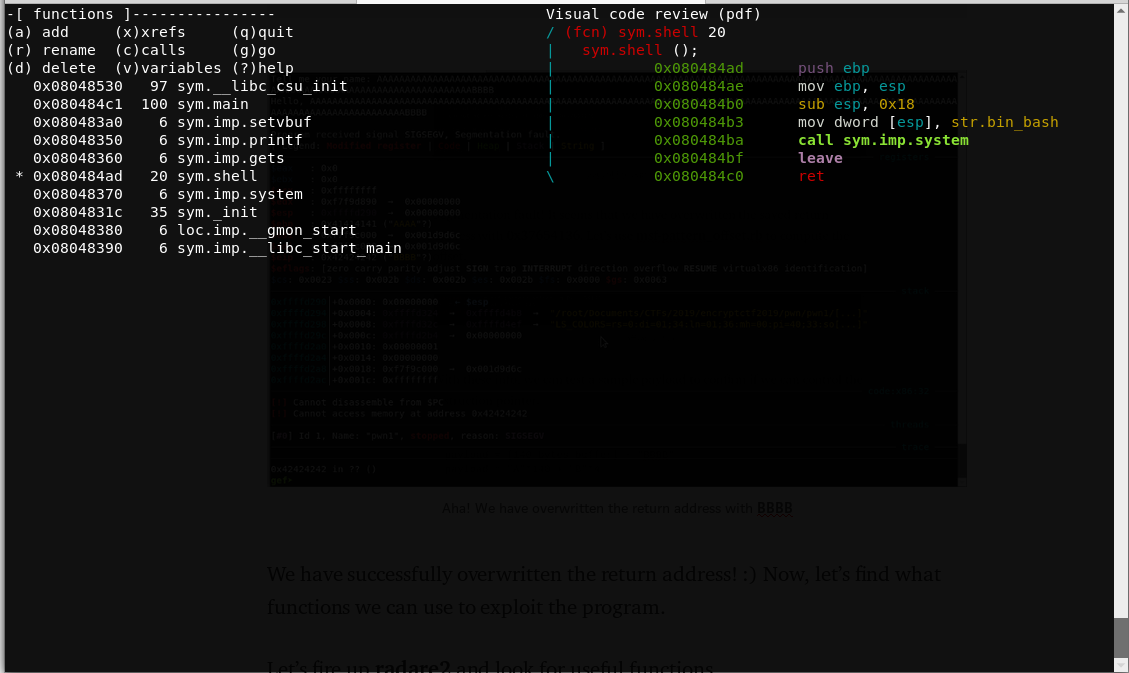

![MOSUT] Format String Attacks MOSUT] Format String Attacks](http://www.kutayzorlu.com/wp-content/uploads/2019/06/kutayzorlu_security_-1.png)








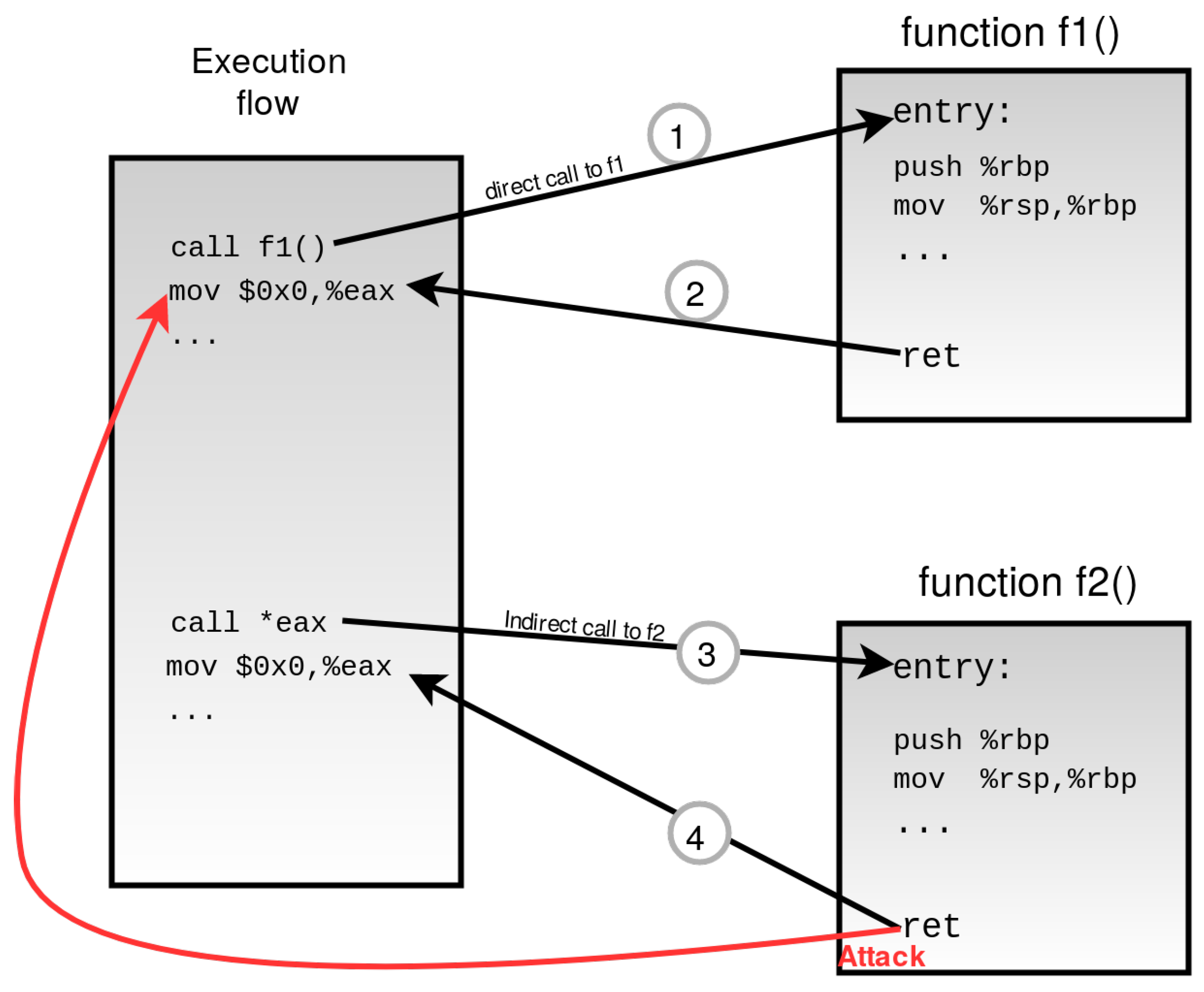



![MOSUT] Format String Attacks MOSUT] Format String Attacks](https://jhalon.github.io/images/gctf18-pwn2-8.png)