format string vulnerability in c
|
Format Strings Exploitation Tutorial
several format strings that specifies the output in C and many other Format strings vulnerability exists in most of the printf family below is some. |
|
Exploiting Format String Vulnerabilities
1 sept. 2001 discover format string vulnerabilities in C source code and why this new kind of vulnerability is more dangerous than the common buffer ... |
|
Buffer Overflow and Format String Overflow Vulnerabilities
We describe a simple implementation with which we currently protect vulnerable copy functions in the C library. key words: Buffer overflow; format string |
|
Format-String Vulnerability
becomes part of a format string. 9. What will happen if user_input contains format specifiers? Page |
|
Proceedings of the 10 USENIX Security Symposium
11 mai 2001 Detecting Format String Vulnerabilities with Type Qualifiers. Umesh Shankar ... mat string security vulnerabilities in C programs using. |
|
Format String Vulnerability and Attack
So we need to access the 7th parameter to access the first 4 bytes of buf! Page 11. Second try: access ret. • python -c 'print "% |
|
Les failles Format String.pdf
1 oct. 2010 Celui ci je le prends à part il est vitale pour le succès de notre exploit. Tout d'abord |
|
Detecting Format String Vulnerabilities with Type Qualifiers
11 mai 2001 The C standard library contains a number of other similar primitives that put the programmer at risk for format string bugs. Other examples ... |
|
Preventing Format-String Attacks via Automatic and Efficient
The well-known vulnerabilities of systems implemented in the C programming language are unsurprising when we consider C programming from a security perspective:. |
|
Format String Vulnerabilities
26 fév. 2019 If a argument would be shorter than the width parameter it is padded by spaces (or 0's with a flag). printf?(?"%10d"? |
|
Format-String Vulnerability - Fengwei Zhang
Here printf() has three optional arguments Elements starting with “ ” are called format specifiers ? printf() scans the format string and prints out each |
|
Format String Vulnerability printf ( user input ); - Syracuse University
The function retrieves the parameters requested by the format string from the stack printf ("a has value d b has value d c is at address: 08x\n" |
|
Format String Vulnerability and Attack - Yajin Zhou
So we need to access the 7th parameter to access the first 4 bytes of buf! Page 11 Second try: access ret • python -c 'print " |
|
Exploiting Format String Vulnerabilities - CS155
1 sept 2001 · It will show you how to discover format string vulnerabilities in C source code and why this new kind of vulnerability is more dangerous than |
|
Format String Vulnerability
When printf(fmt) is executed the stack (from low address to high address) contains the following values (4 bytes each) where the first number is the content |
|
Format Strings
2 Format string bugs The attack possibilities come from the way variadic functions are implemented in C Variadic functions are declared by ending the list |
|
Format String Vulnerabilities
26 fév 2019 · If a argument would be shorter than the width parameter it is padded by spaces (or 0's with a flag) printf(" 10d" 1) //prints 9 spaces |
|
Format String Vulnerabilities 1 Fun with printf - Wellesley College
6 avr 2016 · edu/~cs342/papers/formatstring/formatstring-1 2 pdf ) We will experiment with printf using the program test-printf c in figure 1 |
|
Format Strings Exploitation Tutorial
Think of a format string as a specifier which tells the program the format of the output there are several format strings that specifies the output in C and |
|
Preventing Format-String Attacks via Automatic and Efficient
Format-String Attacks Static Analysis White-Lists Dy- namic Checking 1 INTRODUCTION The well-known vulnerabilities of systems implemented in the C |
What is format string vulnerability in C?
A format string vulnerability is a bug where user input is passed as the format argument to printf , scanf , or another function in that family. The format argument has many different specifies which could allow an attacker to leak data if they control the format argument to printf .What is a format string vulnerability?
What is a Format String Vulnerability? Often found in C language programs, it refers to a bug found in the printf() function. It is widely used to transport data, which could be ASCII text strings, to the standard output. When used properly, text strings can lead to effective and automated conversion types.How format string attacks can be prevented?
Preventing format string attacks
If possible, make the format string a constant. If the above isn't possible, then always specify a format string as part of the program rather than as an input. You can fix most format string vulnerabilities by simply specifying %s as the format string.Format Specifiers Used in C
1%c :char single character.2%d (%i) :int signed integer.3%e (%E) :float or double exponential format.4%f :float or double signed decimal.5%g (%G) :float or double use %f or %e as required.6%o :int unsigned octal value.7%p :pointer address stored in pointer.8%s :array of char sequence of characters.
|
Format String Vulnerability printf ( user input ); - Syracuse University
printf ( user input ); The above statement is quite common in C programs In the lecture, we will find out what can go wrong if the |
|
Format String Vulnerabilities and Exploitation - NCC Group Research
Windows 2000 Format String Vulnerabilities By Anybody who has programmed even a little C will have come across the printf() function Indeed the first |
|
Format String Exploitation
several format strings that specifies the output in C and many other programming Format strings vulnerability exists in most of the printf family below is some |
|
Exploiting Format String Vulnerabilities - CS155 Computer and
1 sept 2001 · If an attacker is able to provide the format string to an ANSI C format function in part or as a whole, a format string vulnerability is present By doing so, the behaviour of the format function is changed, and the attacker may get control over the target application |
|
Preventing Format-String Attacks via Automatic and Efficient
exploits, take advantage of this security weakness Previous proposals for addressing format-string attacks (and other vulnerabilities in C) include: software -fault |
|
Format String Attacks
The cause and implications of format string vulnerabilities are discussed Practical fmtme c * Format a value into a fixed-size buffer */ #include int |
|
Lab 10: Format String Vulnerabilities 1 Fun with - Wellesley College
6 avr 2016 · We will experiment with printf using the program test-printf c in figure 1 This program expects argv[1] to be a format string It passes the format |
|
Format String Vulnerabilities - TU Berlin
There is a large set of conversion specifiers (see man 3 printf) A few examples: specifier conversion output passed as c single character value s |
|
Format string attacks - peoplecsailmitedu
Format string bugs allow arbitrary memory writes A format string bug will allow you to Consider the following vulnerable function: void log_user(char * user) |
|
Format String Vulnerability Lab
The printf() function in C is used to print out a string according to a format Its first argument is called format string, which defines how the string should be |

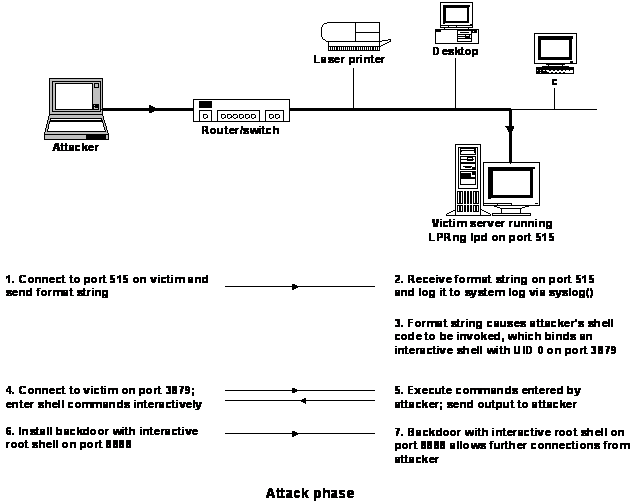
![Exploiting Format String Vulnerabilities [vangelis]pdf Exploiting Format String Vulnerabilities [vangelis]pdf](http://etutorials.org/shared/images/tutorials/tutorial_149/NSA_1318.gif)


![PDF] Automated Format String Attack Prevention for Win32/X86 PDF] Automated Format String Attack Prevention for Win32/X86](https://i1.rgstatic.net/publication/220631563_Finite_state_machine_based_approach_to_prevent_format_string_attacks/links/02e7e537dd16282643000000/largepreview.png)



![PDF] Automated Format String Attack Prevention for Win32/X86 PDF] Automated Format String Attack Prevention for Win32/X86](http://etutorials.org/shared/images/tutorials/tutorial_149/NSA_1319.gif)









![PDF] Automated Format String Attack Prevention for Win32/X86 PDF] Automated Format String Attack Prevention for Win32/X86](https://mk0resourcesinf5fwsf.kinstacdn.com/wp-content/uploads/1-416.png)
![PDF File Format: Basic Structure [updated 2020] - Infosec Resources PDF File Format: Basic Structure [updated 2020] - Infosec Resources](https://0.academia-photos.com/attachment_thumbnails/46749848/mini_magick20190208-3153-9rrmmk.png?1549691966)




![PDF] Automated Format String Attack Prevention for Win32/X86 PDF] Automated Format String Attack Prevention for Win32/X86](https://data01.123dok.com/thumb/q2/n2/n92q/Pki4ZiPT5VIqTD1so/cover.webp)
