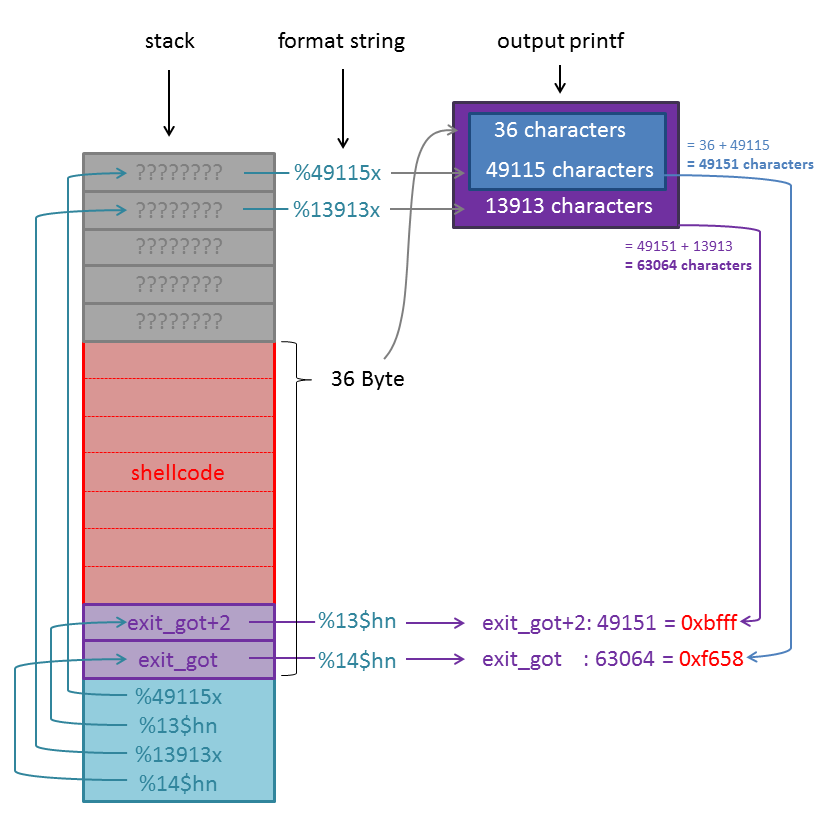
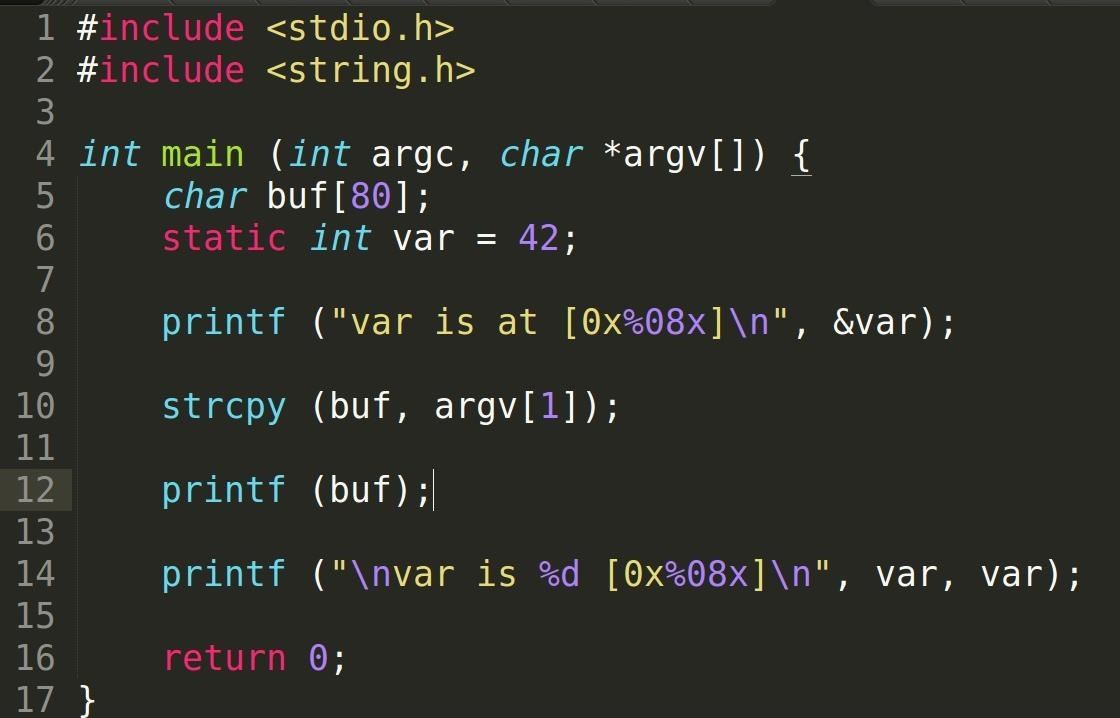
format string vulnerability solution
|
Format-String Vulnerability
Format String. ? Access optional arguments. ? How printf() works. ? Format string attack. ? How to exploit the vulnerability. ? Countermeasures. |
|
Exploiting Format String Vulnerabilities
01-Sept-2001 special situations to allow you to exploit nearly any kind of format string vulnerability seen until today. As with every vulnerability it was ... |
|
Proceedings of the 10 USENIX Security Symposium
elaborates on the printf format string vulnerability. Section 3 describes FormatGuard; our solution to this problem. We present security testing in Section |
|
FormatGuard: Automatic Protection From printf Format String
elaborates on the printf format string vulnerability. Section 3 describes FormatGuard; our solution to this problem. We present security testing in Section |
|
Buffer Overflow and Format String Overflow Vulnerabilities
Numerous incidents of buffer overflow attacks have been reported and many solutions have been proposed but a solution that is both complete and highly |
|
Format Strings Exploitation Tutorial
bytes till the format string to memory. Table 1-1 Format Strings. Format String Vulnerability: Format strings vulnerability exists in most of the printf |
|
Proceedings of the 10 USENIX Security Symposium
11-May-2001 Detecting Format String Vulnerabilities with Type Qualifiers. Umesh Shankar ... The solution to this problem is type inference. In this. |
|
Libsafe 2.0: Detection of Format String Vulnerability Exploits
06-Feb-2001 The latest version of libsafe version 2.0 |
|
Libsafe 2.0: Detection of Format String Vulnerability Exploits
06-Feb-2001 The latest version of libsafe version 2.0 |
|
Attacking the stack
Leaking data with format string attack int main( int argc char** argv) int pincode = 1234; printf(argv[1]);. } This program may leak information from the |
|
Format-String Vulnerability - Fengwei Zhang
Elements starting with “ ” are called format specifiers ? printf() scans the format string and prints out each character until “ ” is encountered ? printf() |
|
Exploiting Format String Vulnerabilities - CS155
1 sept 2001 · It will show you how to discover format string vulnerabilities in C source code and why this new kind of vulnerability is more dangerous than |
|
CompSecAttackLabs/Lab 7 Format String Vulnerabilitypdf at master
Format String Vulnerability/Lab 7 Format String Vulnerability pdf Go to file · Go to file T; Go to line L; Copy path; Copy permalink |
|
Format String Vulnerability printf ( user input ); - Syracuse University
The function retrieves the parameters requested by the format string from the stack printf ("a has value d b has value d c is at address: 08x\n" |
|
Format String Vulnerabilities
26 fév 2019 · Section 0x350 has a detailed overview of format string vulnerabilities ? (Most) original papers (I could find) on the topic |
|
Format String Vulnerability
Both buffer-overflow and format-string vulnerabilities can lead to the modification of the return address field but the ways how the field is modified are |
|
Format String Vulnerability Lab - SEED Labs
12 jan 2020 · Different val- ues can make the solutions different Please pick a value between 0 and 300 for this lab The DUMMY SIZE value for this lab is: |
|
Format Strings Shellcode and Stack Protection - UCSD CSE
Actually little-endian https://crypto stanford edu/cs155/papers/formatstring-1 2 pdf Exploiting Format String Vulnerabilities by scut / team teso |
|
Format string attack - OWASP Foundation
The Format String exploit occurs when the submitted data of an input string is evaluated as a command by the application In this way the attacker could |
|
Preventing Format-String Attacks via Automatic and Efficient
In addition purely static-analysis based techniques like these require changing the code to fix any potential vulnerabilities that are found— which can be |
How format string attacks can be prevented?
Preventing format string attacks
If possible, make the format string a constant. If the above isn't possible, then always specify a format string as part of the program rather than as an input. You can fix most format string vulnerabilities by simply specifying %s as the format string.What is a format string vulnerability?
What is a Format String Vulnerability? Often found in C language programs, it refers to a bug found in the printf() function. It is widely used to transport data, which could be ASCII text strings, to the standard output. When used properly, text strings can lead to effective and automated conversion types.What causes format string vulnerability?
The Format String exploit occurs when the submitted data of an input string is evaluated as a command by the application.- Can we use the StackGuard idea to protected against format-string attacks? No. Format-string, unlike buffer overflow, doesn't modify any of the memory locations leading up to the return address, and only modifies the return address. Therefore the stackguard won't work.
|
Format String Vulnerability Lab - Syracuse University
In this lab, students will be given a program with a format-string vulnerability; their task is to develop a scheme to exploit the vulnerability In addition to the attacks, |
|
Format String Vulnerability printf ( user input ); - Syracuse University
Format String Vulnerability: 1 Format String Vulnerability printf ( user input ); The above statement is quite common in C programs In the lecture, we will find out |
|
Format String Vulnerabilities - TU Berlin
0x80482f0 jan, matthias, julian (sect) Security Lab SoSe 2015 8 / 13 Page 10 Format String Vulnerability Implications (2) Reading memory is nice, but what |
|
Format String Vulnerability Lab
A problem like this is called format string vulnerability program with a format- string vulnerability; their task is to exploit the Please fix the vulnerability in the server program, and recompile it Does the compiler warning go away? Do your |
|
Format String Vulnerability Lab - SEED Labs
12 jan 2020 · program with a format string vulnerability; their task is to exploit the vulnerability to achieve won't be able to use the solutions from the past |
|
Format String Vulnerability
Can we use the StackGuard idea to protected against format-string attacks? 6 4 Please construct one format string to exploit the vulnerability, such that your attack will be successful regardless of describing your solution 6 13 What if we |
|
Preventing Format-String Attacks via Automatic and Efficient
We propose preventing format-string attacks with a combi- nation of static rectly , and all the format-string vulnerabilities disappeared Our tool is available for We have presented a solution to the problem of format- string attacks, by |
|
Format String Attacks
The cause and implications of format string vulnerabilities are discussed four then the solution is quite simple: Pad out the format string until we get the right |
|
Automatic Protection From printf Format String Vulnerabilities
elaborates on the printf format string vulnerability Section 3 describes FormatGuard; our solution to this problem We present security testing in Section 4, com- |