format string vulnerability write to address
|
Format Strings Exploitation Tutorial
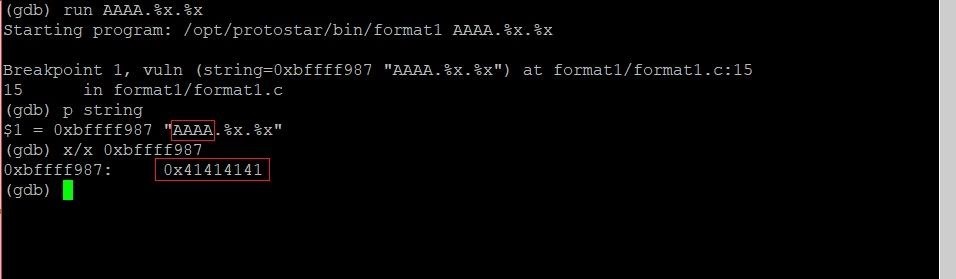
Format strings vulnerability exists in most of the printf family below is some. Try to write byte to DTOR END address using the following input:. |
|
Exploiting Format String Vulnerabilities
1 sept. 2001 Return addresses control of retaddr. Malloc Buffers Malloc data. Management info write to memory. Format strings Output string Format ... |
|
Format String Vulnerability and Attack
value of len address of len. Addr of format string return address saved ebp ebp of printf … … High. Low. Internal pointer maintained by printf. Page 8 |
|
Blind Format String Attacks
tion we show a way to exploit format string vulnerabilities on the heap |
|
Format String Vulnerability
15 oct. 2005 What could we do for a format string vulnerability. ? Read from arbitrary memory address. ? %s format. ? environment variable. ? Write ... |
|
Windows 2000 Format String Vulnerabilities
This is done by substituting format specifiers in the format string for values Using this our program now attempts to write to address 0x78257825 - when ... |
|
Format-String Vulnerability
Format string attack printf() scans the format string and prints out each character until “%” is ... as a memory address and writes into that location. |
|
Advanced Format String Attacks
Multiple Format String Vulnerabilities (BID 40746) our format string format string's address ... Point format string at overwrite address and write. |
|
Format String Vulnerabilities
26 févr. 2019 Unfortunately not every address we want to write to is on the stack. However |
|
Format Strings
The simplest possible exploitation of a format string vulnerability is to leak bytes at the beginning before writing the address. |
|
Format String Vulnerability printf ( user input ); - Syracuse University
The function retrieves the parameters requested by the format string from the stack printf ("a has value d b has value d c is at address: 08x\n" |
|
Format String Vulnerability and Attack - Yajin Zhou
What if we input some special strings into the buffer? • printf(“AAAA 08x 08x 08x 08x 08x 08x 08x 08x |
|
Format-String Vulnerability - Fengwei Zhang
Goal: change the value of var variable from 0x11223344 to some other value ? n: Writes the number of characters printed out so far into memory ? printf |
|
Exploiting Format String Vulnerabilities - CS155
1 sept 2001 · Now we write a return address (0xbfffd33c) and exploit it just the old known way as we would do it with any buffer overflow While any format |
|
Format Strings
“Format strings” are the control strings that are passed to the printf() functions are vulnerable whenever the attacker can control the format string |
|
Format String Vulnerability
S6 1 Please write a function that takes a variable number of strings as its arguments and prints out their total length S6 2 Both buffer-overflow and |
|
Format String Vulnerabilities
26 fév 2019 · Unfortunately not every address we want to write to is on the stack However there is something important on the stack that we control What |
|
Format Strings Shellcode and Stack Protection - UCSD CSE
return address and saved frame pointer Format String Vulnerabilities: Writing https://crypto stanford edu/cs155/papers/formatstring-1 2 pdf |
|
Format Strings Exploitation Tutorial
Format strings vulnerability exists in most of the printf family below is some Try to write byte to DTOR END address using the following input: |
|
Format string attacks - People
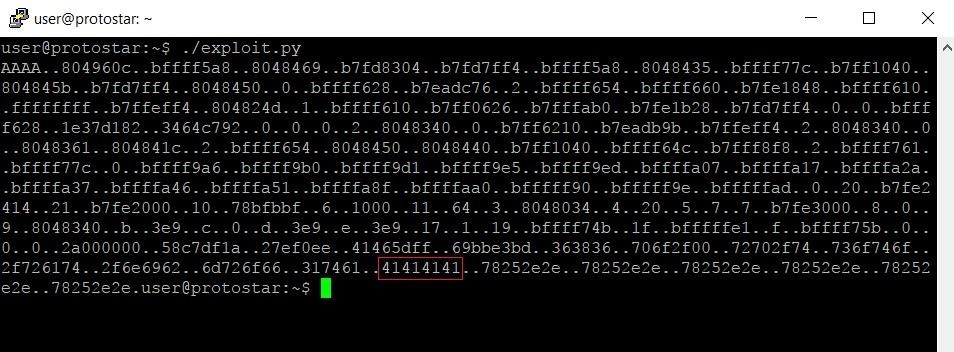
26 sept 2011 · Format string bugs allow arbitrary memory writes In our attack we will show how to modify the value of x at address 0xEC0D to equal |
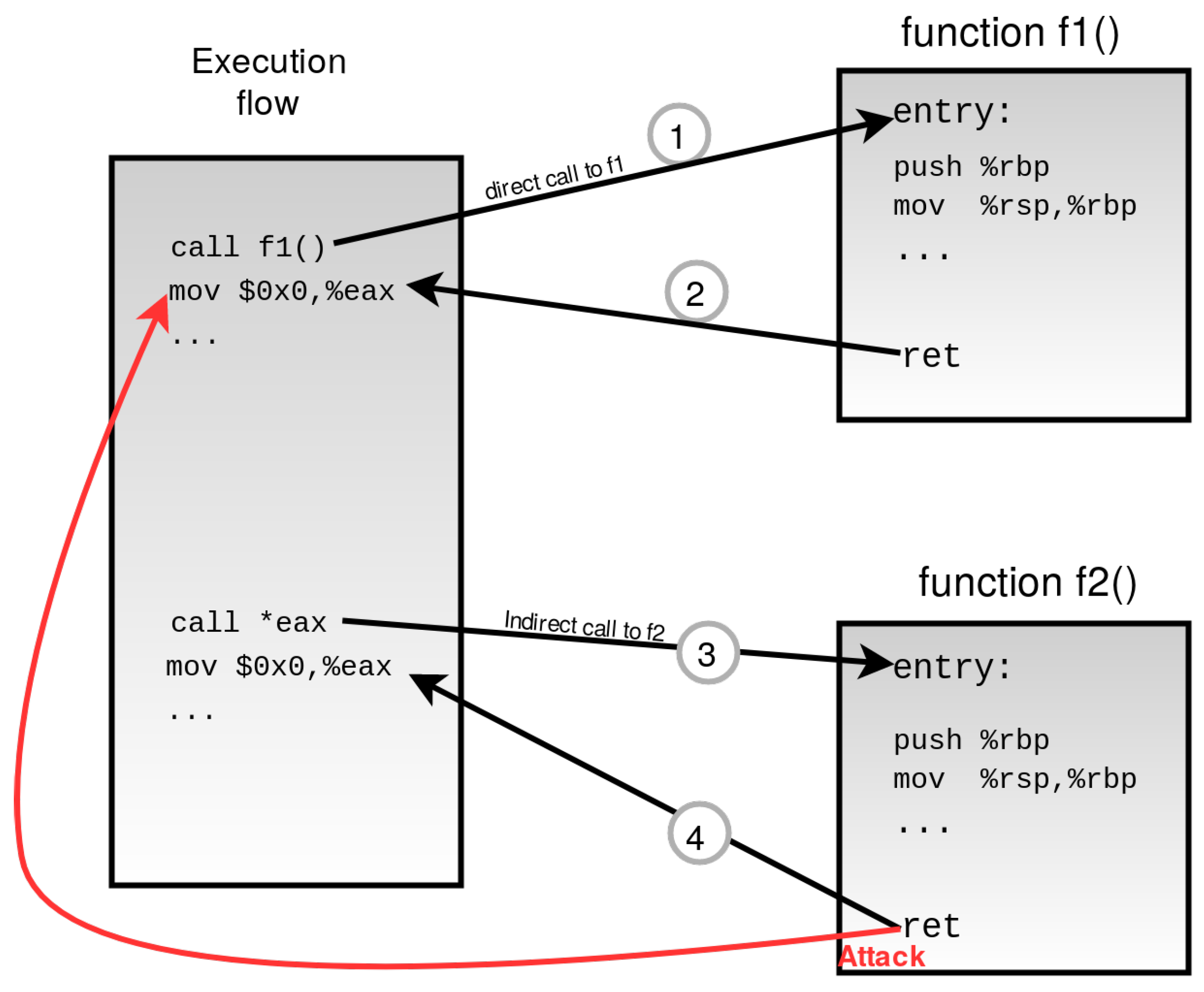
What is a format string vulnerability?
What is a Format String Vulnerability? Often found in C language programs, it refers to a bug found in the printf() function. It is widely used to transport data, which could be ASCII text strings, to the standard output. When used properly, text strings can lead to effective and automated conversion types.What is format string vulnerability in C?
A format string vulnerability is a bug where user input is passed as the format argument to printf , scanf , or another function in that family. The format argument has many different specifies which could allow an attacker to leak data if they control the format argument to printf .How format string attacks can be prevented?
Preventing format string attacks
If possible, make the format string a constant. If the above isn't possible, then always specify a format string as part of the program rather than as an input. You can fix most format string vulnerabilities by simply specifying %s as the format string.- In this way, the attacker could execute code, read the stack, or cause a segmentation fault in the running application, causing new behaviors that could compromise the security or the stability of the system.
|
Format String Vulnerability printf ( user input ); - Syracuse University
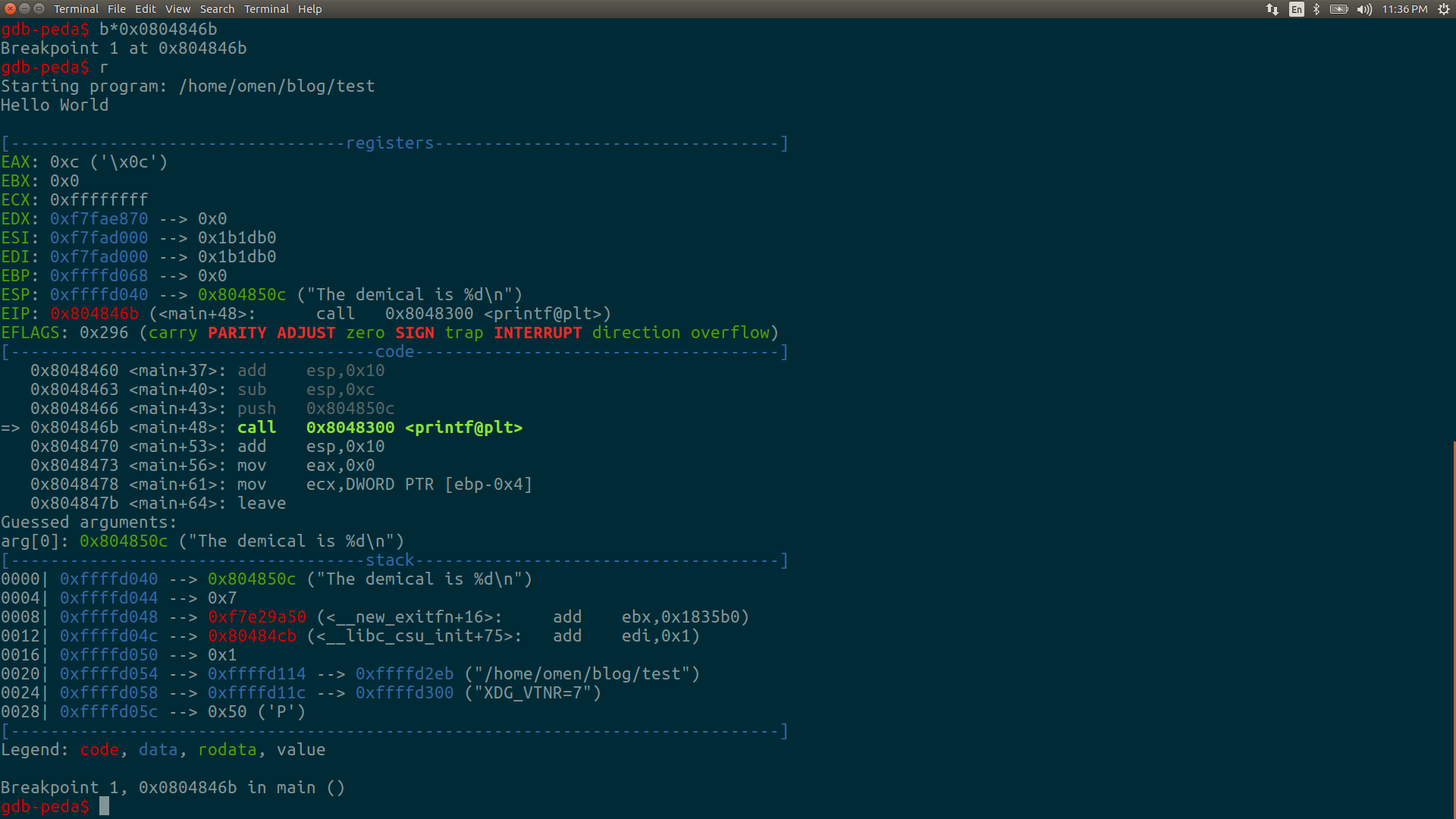
Format String Vulnerability: 1 Format parameters requested by the format string from the stack printf ("a has value d, b has value d, c is at address: 08x\n", a, b, &c); Writing an integer to nearly any location in the process memory |
|
Format String Vulnerabilities and Exploitation - NCC Group Research
Windows 2000 Format String Vulnerabilities By Using this our program now attempts to write to address 0x78257825 - when translated into their character |
|
Format String Exploitation
Format strings vulnerability exists in most of the printf family below is some Now to write address 0xDDCCBBAA 4 writes 1 byte at a time are required shown |
|
Format String Attacks
The cause and implications of format string vulnerabilities are discussed Practical examples programmer writing code His task: to print out output before the n field was encountered is stored at the address passed in the next argument |
|
Exploiting Format String Vulnerabilities - CS155 Computer and
1 sept 2001 · Return addresses control of retaddr Malloc Buffers Malloc data Management info write to memory Format strings Output string Format |
|
Format string attacks - peoplecsailmitedu
Format string bugs allow arbitrary memory writes A format In our attack, we will show how to modify the value of x at address 0xEC0D to equal the value 100 |
|
Preventing Format-String Attacks via Automatic and Efficient
Previous proposals for addressing format-string attacks (and other style of attack can be used to write an arbitrary value to an arbitrary location in memory |
|
Exploiting format Strings with Python - SSRN Papers
The article progresses to discuss crafting attacks using python in order to taught vulnerabilities can be used to read arbitrary locations from memory, write to It is not uncommon for format string vulnerabilities to allow the attacker to view all |
|
T11_Formatted output
printf() scans the format string and prints out each character until “ ” is encountered Hence, if we want to write a value to a memory location, we need to have After the attack, data in the target address is modified to 0x2c (44 in decimal) |
|
Blind Format String Attacks - TUM
tion, we show a way to exploit format string vulnerabilities on the heap, write the value 0x9 to the least significant byte at the address 0xbf9e4f78, because |


![Top PDF History of Buffer Overflow [lucid78] pdf - 1Library Top PDF History of Buffer Overflow [lucid78] pdf - 1Library](https://devel0pment.de/wp-content/uploads/2019/10/img03.png)
















![PDF File Format: Basic Structure [updated 2020] - Infosec Resources PDF File Format: Basic Structure [updated 2020] - Infosec Resources](https://ars.els-cdn.com/content/image/3-s2.0-B9781597490054500171-gr4.jpg)