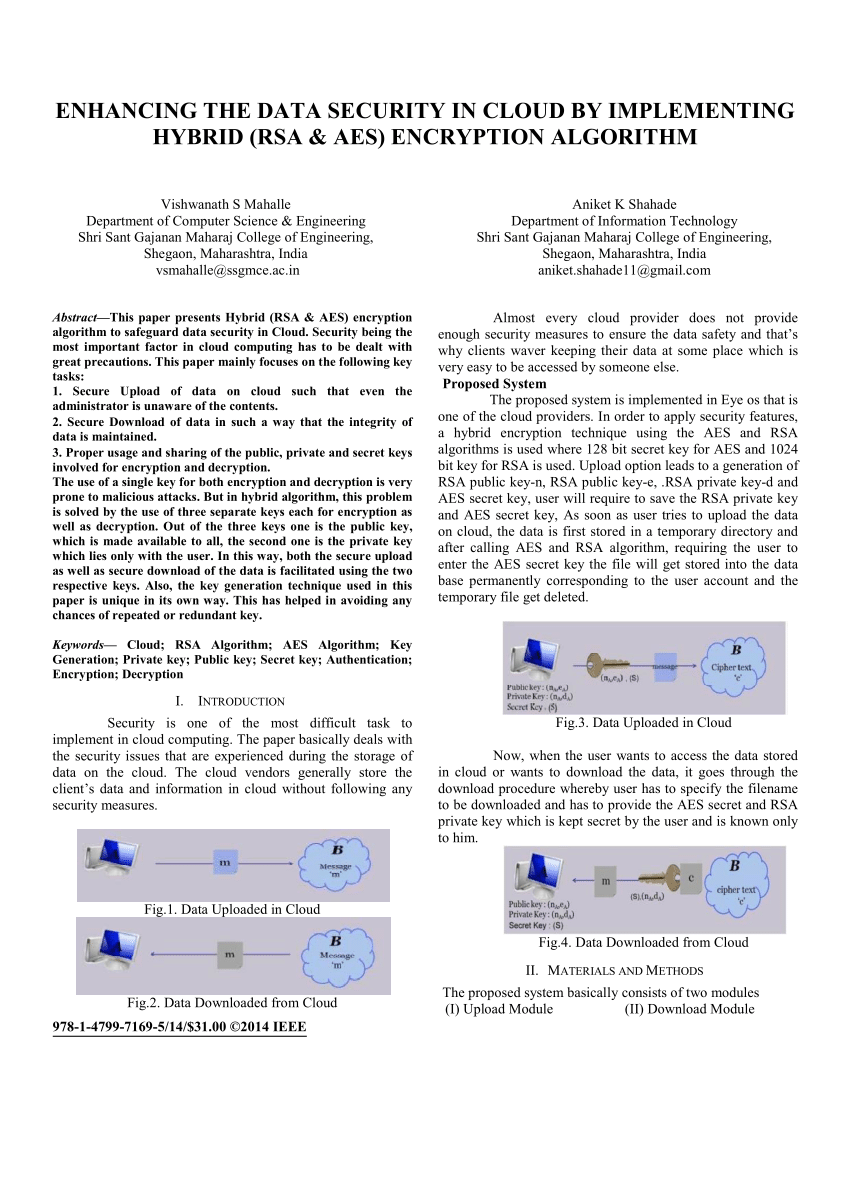
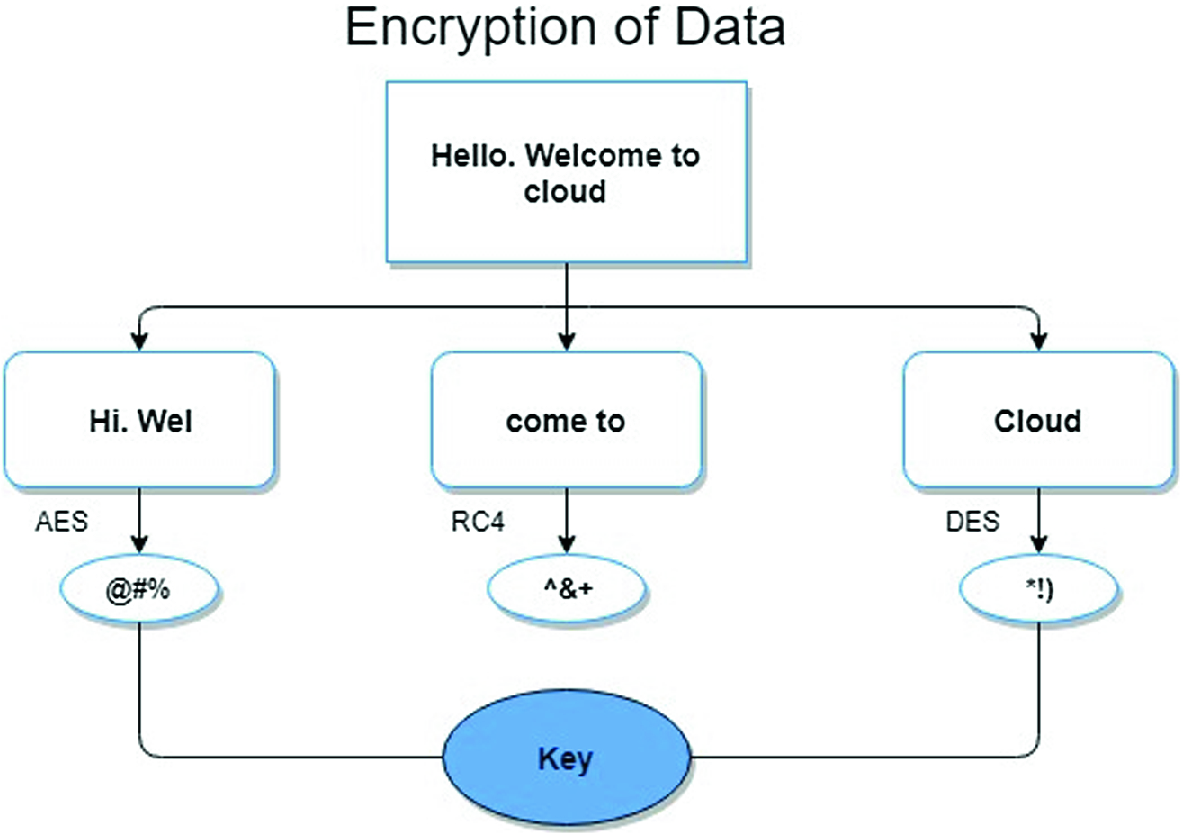
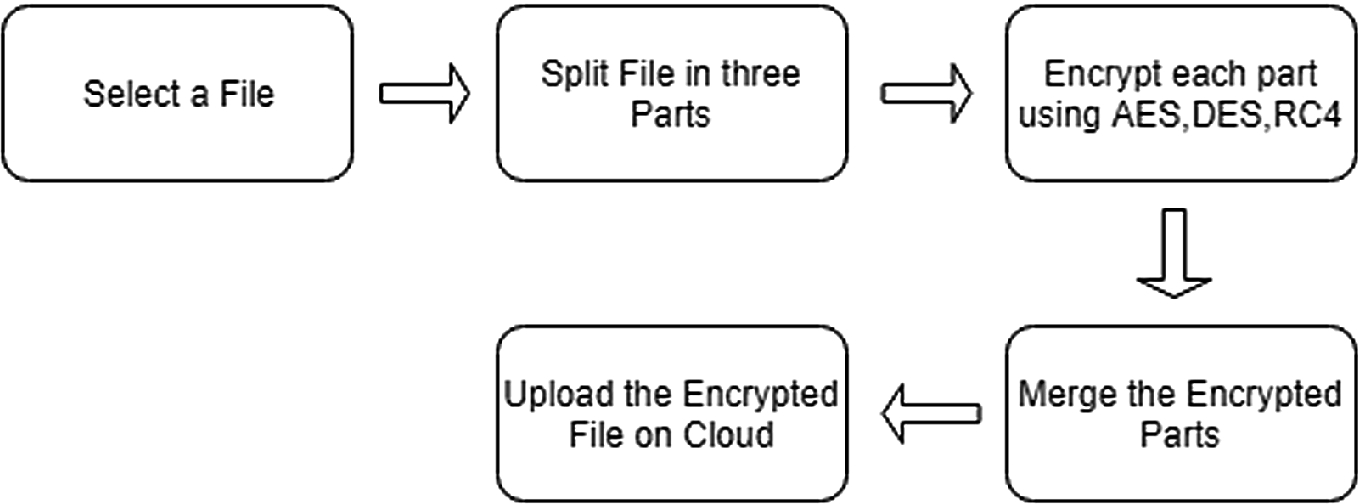
google cloud encryption algorithm
|
Cloud Sync White Paper - Based on DSM 6.1
Data Encryption Algorithm between a Synology NAS and cloud storage in real-time instantly delivering ... Google Drive (including Dropbox for Business)1. |
|
Encryption at Rest in Google Cloud Platform - Dito
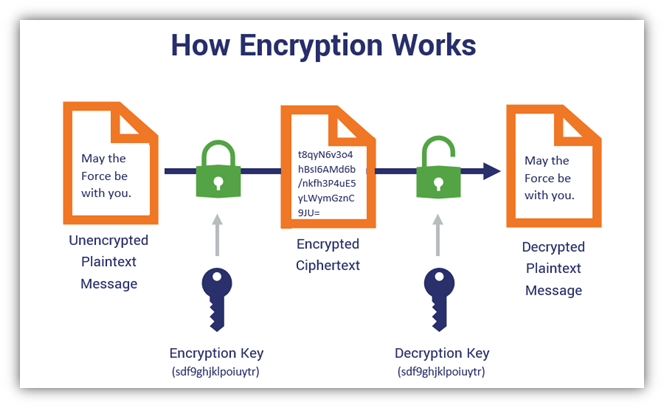
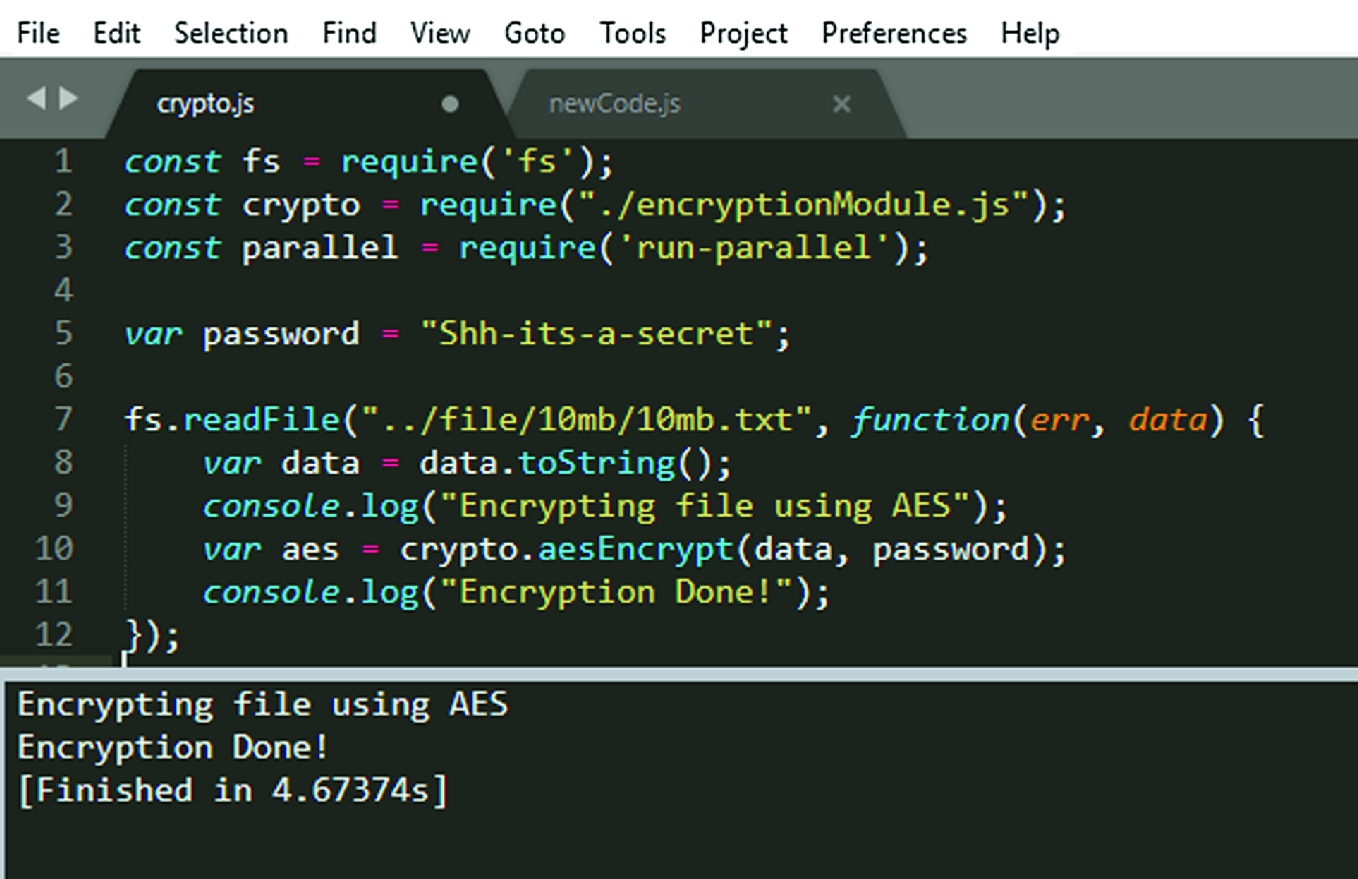
The encryption algorithm used is public such as the Advanced Encryption Standard (AES) but execution depends on a key which is kept secret To decrypt the |
|
(PDF) Encryption at Rest in Google Cloud Platform - Academiaedu
When the service providers are used for both cryptographic operations and storage then there is a huge threat of unauthorized access or usage of data We |
|
Using Encryption Algorithm to enhance the Data Security in Cloud
PDF On May 7 2015 Zaid Kartit and others published Using Encryption Algorithm to enhance the Data Security in Cloud storage Find read and cite all |
|
Performance Analysis of Encryption Algorithm in Cloud Computing
29 nov 2016 · In this research paper we have discussed the problem of data security in cloud and show performance analysis to enhance security in terms of |
|
Encryption Algorithm for Cloud Computing
This paper proposes a combined approach of Identity based and attribute based access policy for encryption technique of cloud storage which can be implementable |
|
Applying Encryption Algorithm for Data Security in Cloud Storage
Abstract *This paper proposes a simple secure and privacy-preserving architec- ture for inter-Cloud data sharing based on an encryption/decryption algorithm |
|
(PDF) Encryption at Rest in Google Cloud Platform - Academiaedu
View PDF International Journal of Computer Applications Performance Analysis of the Encryption Algorithms as Solution to Cloud Database Security |
|
Performance Analysis of Encryption Algorithm in Cloud Computing
29 nov 2016 · PDF Security is the most important factor in cloud computing for ensuring client data is placed on secure mode in the cloud |
|
Encryption Algorithm for Cloud Computing
algorithm for data security and privacy in cloud Storage with other existing algorithms Amazon?s S3 Google App Engine and Microsoft?s Azure etc Cloud |
|
Applying Encryption Algorithm for Data Security in Cloud Storage
algorithm for encryption/decryption for outsourcing data in cloud storage and then Examples include Google App Engine Force com and Microsoft Azure |
What is the encryption algorithm in GCP?
All data that is stored by Google is encrypted at the storage layer using the Advanced Encryption Standard (AES) algorithm, AES-256.What is AES-256 CBC?
Advanced Encryption Standard (AES) 256 is a virtually impenetrable symmetric encryption algorithm that uses a 256-bit key to convert your plain text or data into a cipher. That's a lot of jargon but don't despair—it gets a lot easier from here.How does Google use encryption?
Google encrypts data as it is written to disk with a per-chunk encryption key that is associated with a specific Access Control List (ACL). The ACL ensures that data in each chunk can only be decrypted by authorized Google services and employees.- Cloud Storage encrypts user data at rest using AES-256, in most cases using Galois/Counter Mode (GCM). There is no setup or configuration required, no need to modify the way you access the service, and no visible performance impact.
|
Analysis and Design of Authentication and Encryption Algorithms for
Amazon Elastic Compute Cloud (EC2) [6] and Google Compute Engine (GCE) [ 56] are two examples of IaaS Platform-as-a-Service (PaaS) provides pre- |
|
Cloud Data Security using Authentication and Encryption - CORE
Keywords : authentication, cloud, EAP-CHAP, encryption, rijndael algorithm GJCST-B For example: Drop Box, SkyDrive and Google drive Author α : M TECH |
|
Implementing various encryption Algorithms to provide the Data
Using encryption Algorithms to enhance the Data Security in Cloud Computing MANDEEP runtime of Google App Engine, i e JDK 1 6 Eclipse IDE Google |
|
A Secure Cloud Computing Model based on Data Classification
with different encryption algorithms, and the simulation results showed the storage providers are Google Docs, Dropbox, JustCloud, Mozy and Google Drive |