graph theory applications in cyber security
|
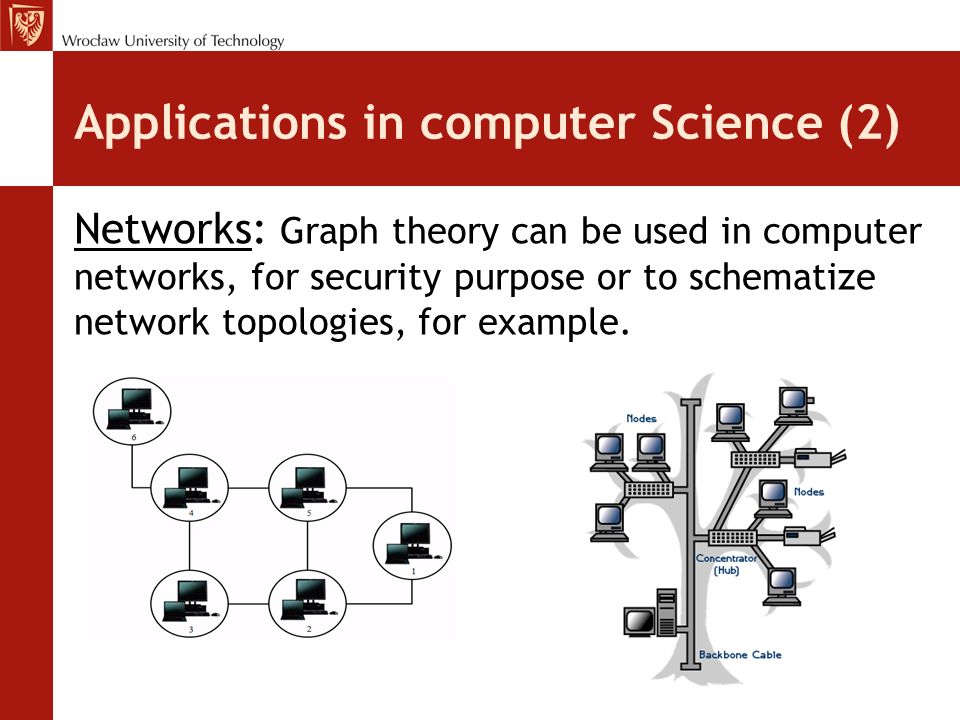
Graph Theory Applications in Network Security 1 INTRODUCTION 2
In this paper we review some of the key applications of graph theory in network security. We first cover some algorithmic aspects |
|
Scenario Graphs Applied to Network Security
Through a detailed concrete example we show how we can model a computer network and generate and analyze attack graphs automatically. The attack graph we |
|
A NOVEL APPROACH OF MOBILE SECURITY ROBOTICS MOVED
31 juil. 2018 and computer science [4] [5]. However it is become a significant filed of robotic application in our daily life. Graph theory has the ... |
|
Network Security Using Graph Theory
also define an adjacency matrix attack graph to analyze and locate potential risks to This is because many applications obfuscate their tra?c using ... |
|
Network Security Using Graph Theory
also define an adjacency matrix attack graph to analyze and locate potential risks to This is because many applications obfuscate their tra?c using ... |
|
Probabilistic prediction of the behaviour of cyber attackers
highly used in cyber security as a powerful way to find understanding and deep research about probability and graph theory is made as well as Bayesian. |
|
A Comprehensive Survey about Graph Theory Applications in
20 fév. 2020 Graph theory applications in the computer science field. ... Uses of Graph Algorithms/Concepts in Network Security Monitoring. |
|
Graph Theory Applications in Network Security
University of South Australia - Cyber Security & Digital Forensics Workshops September 2015. Graph Theory Applications in Network Security. |
|
Applied graph theory to security: A qualitative placement of security
23 sept. 2020 The rise of edge computing enables local network management. Services are no longer clustered inside the cloud but rather spread all over the ... |
|
PDF A Review on Graph Theory in Network and Artificial Intelligence
The Bipartite Graph is constructed as follows. Fig-2. 2. Application of Graph Theory in Computer science. 2.1 Computer Network Security. |
|
A Study of Graph Theory Applications in IT Security - ResearchGate
2 fév 2021 · This study focused on two parts; the first is to review the most important applications of the graph theory in the field of network security |
|
Graph Theory Applications in Network Security - arXiv
16 nov 2015 · In this paper we review some of the key applications of graph theory in network security We first cover some algorithmic aspects then present |
|
Graph Theory Applications in Network Security - Academiaedu
In this paper we review some of the key applications of graph theory in network security We first cover some algorithmic aspects then present network |
|
Scenario Graphs Applied to Network Security
We call this set of counterexamples a scenario graph In this chapter we present two different algorithms for producing scenario graphs and explain how scenario |
|
Graph Theory and Cyber Security - IEEE Xplore
This paper is a guide for the applied m who would like to know more about netw cryptography and cyber security based of g The paper gives a brief overview of |
|
Graph Theory Applications in Network Security
13 juil 2017 · Graph theory has become a very critical component in many applications in the computing field including networking and security Unfortunately |
|
Graph Theory Applications in Network Security - Semantic Scholar
15 nov 2015 · Some of the key applications of graph theory in network security are reviewed followed by some algorithmic aspects then network coding and |
|
Graph Theory Applications in Network Security - PDF Free Download
Graph Theory Applications in Network Security Jonathan Webb1 Fernando Docemmilli2 and Mikhail Bonin3 Theory Lab - Central Queensland University Wayville |
|
A Cybersecurity Knowledge Graph Completion Method Based on
16 déc 2022 · Abstract: The application of cybersecurity knowledge graphs is attracting increasing attention How- ever many cybersecurity knowledge |
|
Network Security Using Graph Theory
This is because many applications obfuscate their tra?c using unregistered port numbers or payload encryption In this paper we propose the use of Tra?c |
|
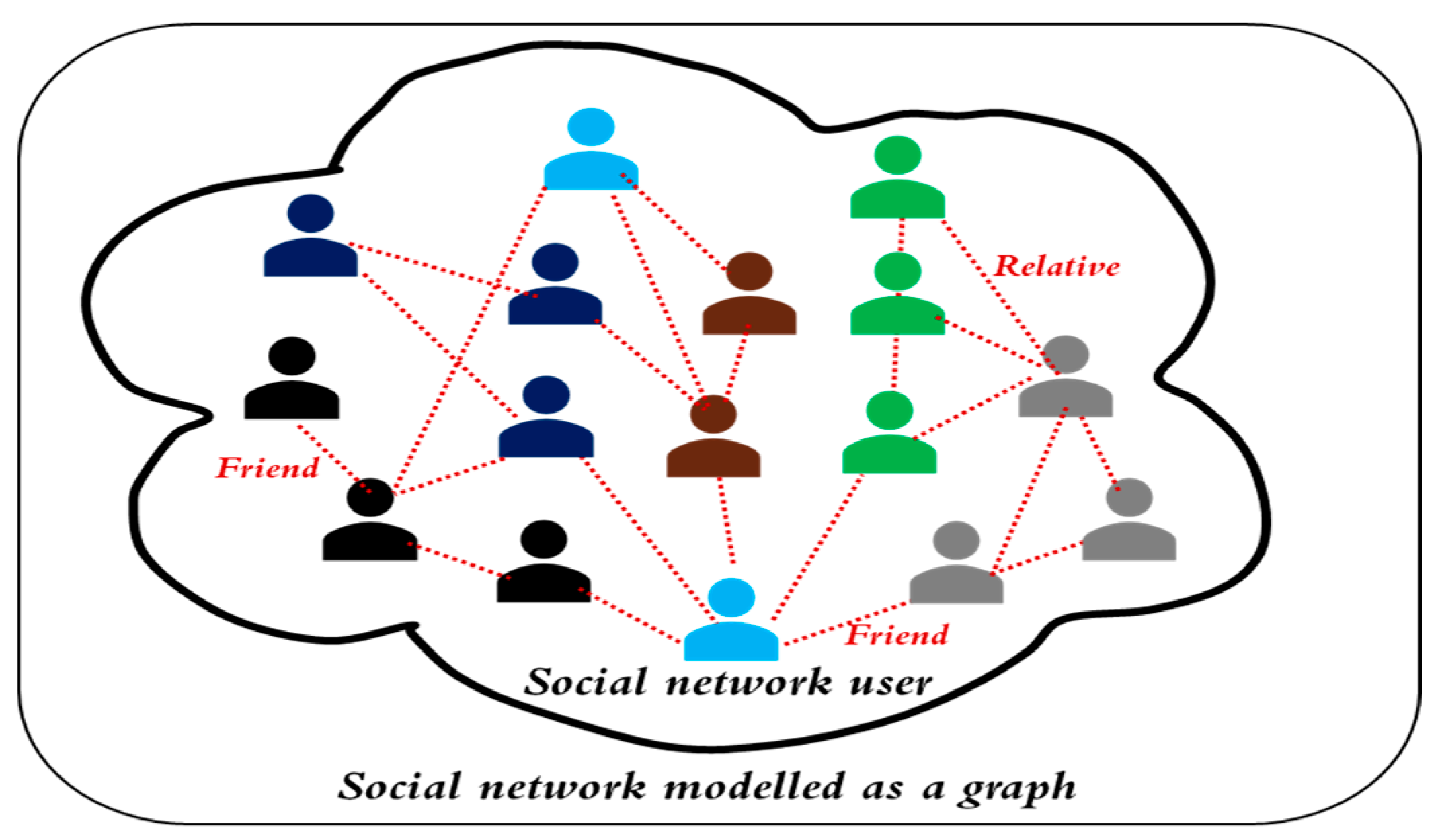
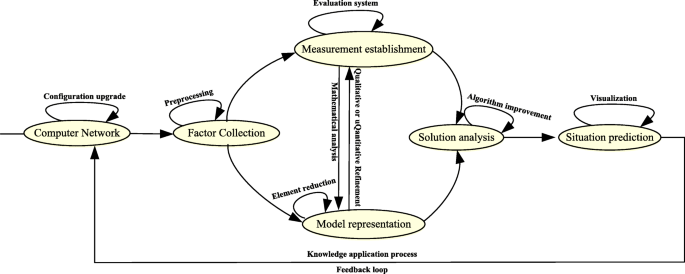
Cybersecurity through Network and Graph Data
4 déc 2022 · Graph (as discussed in chapter 4) depict the relationships between various entities • A graph is comprised of nodes and links (or |
|
Graph Theory Applications in Network Security - PDF Free Download
Graph Theory Applications in Network Security Jonathan Webb1 In this paper we explore applications of graph theory in cellular networks with an |
How is graph theory used in cyber security?
For monitoring network activities, we present the concept of Traffic Dispersion Graphs which can help easy identification of access patterns over a network. We also define an adjacency matrix attack graph to analyze and locate potential risks to protect critical network systems against multi step attacks.What are 3 applications of graph theory?
Modern Applications of Graph Theory discusses many cutting-edge applications of graph theory, such as traffic networks, navigable networks and optimal routing for emergency response, and graph-theoretic approaches to molecular epidemiology.What are the applications of graph theory in the field of Internet?
In the real world, graph theory is used in the internet field, Google maps/ Yahoo maps, social media, web Page searching, City Planning, Traffic Control, Transportation & Navigation, Travelling Salesman Problems, GSM mobile phone networks, Map coloring, timetable scheduling etc.What are real life applications of graph theory?
Airline Scheduling (Flow problems) Directions in a map (Shortest path) Solving Sudoku's puzzles (Graph coloring) Search Engine Algorithms (PageRank algorithm) Social Media Marketing (Community detection)
|
Graph Theory and Cyber Security - IEEE Xplore
Keywords - data security; graph theory; net security; attack tree theory?", and other one asked me:" Has grap applied to cyber security?" Graphs are discrete |
|
Network Security Using Graph Theory - IJIET
Assuming that not many diverse applications use the same port number, port- based TDGs can be used in order to identify the type of application utilizing a given |
|
ON ATTACK GRAPH MODEL OF NETWORK SECURITY - Journal
Keywords: Attack graph model; Network security ACM Classification Keywords: C 2 Computer-communication networks; G2 2 Graph Theory; G2 3 Applications |
|
An Introduction to Graph Theory for Security People Who - Events
The application of graphs in a security context Summary A Little More Advanced Graph Theory You'll often called a directed network or a directed graph, |
|
Graph Theory - inventions
20 fév 2020 · Graph Theory Applications in Computer Science and Uses of Graph Algorithms /Concepts in Network Security Monitoring We can use GT |
|
GRAPH THEORY IN COMPUTER SCIENCE - Progressive
Keywords: Graphs, network, application of graphs, graph algorithms, bipartite graph etc INTRODUCTION Graph how graph theory is utilized in various computer applications History of Graph theory Computer Network Security A team of |
|
An Application of Graph Theory in Cryptography
Analysis of cryptographic security leads to using theoretical computer science especially complexity theory The actual implementation of cryptosystems, and the |


.jpg)