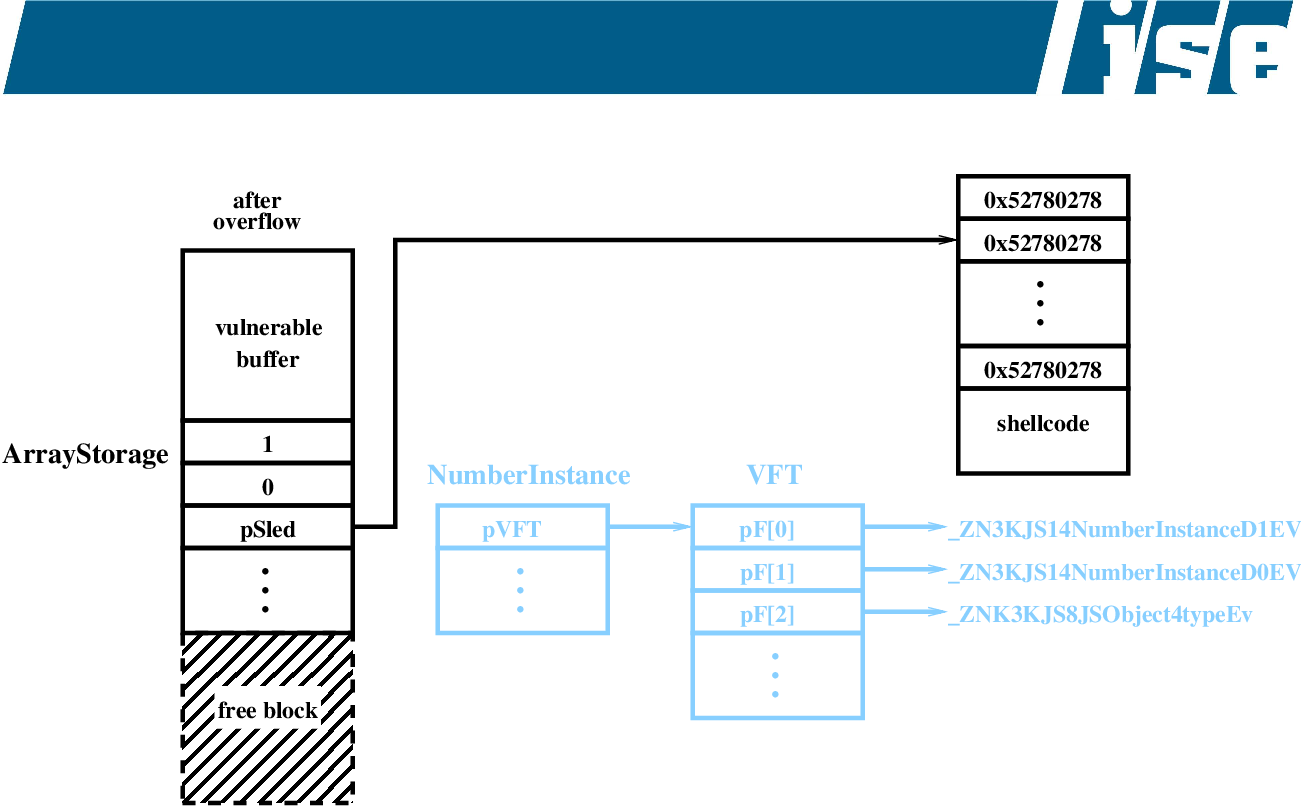
heap overflow
|
Exploitation avancée de buffer overflows -
28 juin 2002 Dans certains cas on peut s'arranger en modifiant le shellcode : le serveur UW imapd possédait une vulnérabilité de type stack overflow dans la ... |
|
Engineering Heap Overflow Exploits with JavaScript
Many buffer and integer overflow vulnerabilities allow for a somewhat arbitrary set of values to be written at a relative offset to a pointer on the heap. |
|
BuFFER OVERFLOW
BUFFER OVERFLOW. 2 février 2012. GERMON RAPHAËL – XPOSÉ - IR3 locale paramètres |
|
Out-of-bounds Read Use After Free and Heap-based Buffer
1 août 2023 memory vulnerability (CWE-416) and a heap-based buffer overflow vulnerability (CWE-122) have been found in CX-Programmer. Malicious users ... |
|
Discovering and exploiting a kernel pool overflow on modern
13 juil. 2021 □ Buffer overflow 101. □. Controlled memcpy size. □. Controlled content. Dest: pool (heap) buffer. Page 31. 31 / 68. 3131. |
|
TailCheCk: A Lightweight Heap Overflow Detection Mechanism with
10 juil. 2023 A heap overflow vulnerability occurs when a program written in an unmanaged language such as C or C++ accesses a memory location beyond an ... |
|
Provably-Secure Remote Memory Attestation for Heap Overflow
this class of exploits is classically embodied in the buffer overflow attack many other instantiations exist |
|
Automated Exploitable Heap Layout Generation for Heap Overflows
9 août 2023 Nevertheless AEG is still unsatisfac- tory for heap overflows. To achieve control flow hijacking using a heap overflow |
|
Support tool CX-Drive for inverter/servo heap-based buffer overflow
24 avr. 2023 □Overview. CX-Drive a support tool for inverters/servos |
|
Heap and BSS Overflow Ⅰ
22 janv. 2005 ○ "heap-based overflow" refers to both heap and data/bss sections. Page 7. CH Ro.oT. 2005-01-22. Heap and BSS (cont.) ○ Heap. ○ Dynamically ... |
|
Automatically Assessing Crashes from Heap Overflows
It is important to decide whether a crash caused by heap overflow can be turned into an exploit. Efficient and effective assessment of exploitability of crashes |
|
Windows Heap Overflows
This presentation will examine how to exploit heap based buffer overflows on the Windows platform. Heap overflows have been well. |
|
Comprehensively and Efficiently Protecting the Heap ?
corrupting heap meta-data through a buffer overflow format string vulnerability |
|
Towards Efficient Heap Overflow Discovery
Aug 16 2017 Heap overflow is a prevalent memory corruption vulner- ability |
|
Analysis to Heap Overflow Exploit in Linux with Symbolic Execution
The existing automatic exploit generation technologies for buffer overflow find vulnerability trigger point and generate exploit by checking the control flow |
|
Engineering Heap Overflow Exploits with JavaScript
This paper presents a new technique for exploiting heap overflows in JavaScript interpreters. Briefly given a heap overflow |
|
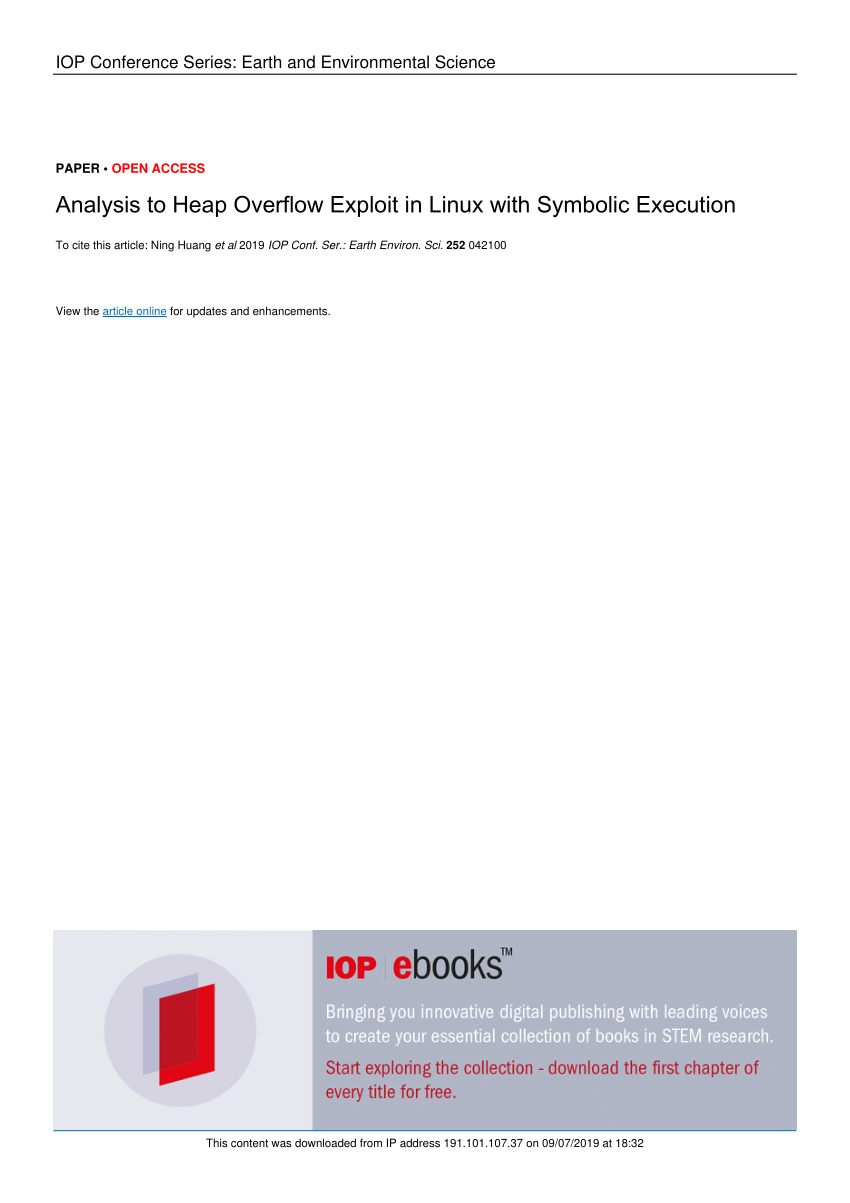
Heap Overflows Illustrated 1.0
A fake heap chunk header which is shifted into position via a heap overflow may be used to overwrite virtually any 4-byte word in memory. This attack uses |
|
Defeating Microsoft Windows XP SP2 Heap protection and DEP
The heap overflow exploitation scenario usually proceeds on like this: If during the buffer overflow the neighboring block exists and is free |
|
Heap Overflows and Double-Free Attacks
Heap Overflow. ?Overflowing buffers on heap can change pointers that point to important data. - Illegitimate privilege elevation: if program with overflow. |
|
Engineering Heap Overflow Exploits with JavaScript
This paper presents a new technique for exploiting heap overflows in JavaScript interpreters. Briefly given a heap overflow |
|
(PDF) Buffer Overflow Attack –Vulnerability in Heap - ResearchGate
16 déc 2022 · Buffer overflow is used by hackers to exploit a computer application system This attack is called an input validation attack where the hacker |
|
Heap Overflows and Double-Free Attacks
Heap Overflow ?Overflowing buffers on heap can change pointers that point to important data - Illegitimate privilege elevation: if program with overflow |
|
Buffer Overflow Attacks: Detect Exploit Prevent - Zenk - Security
For example a Buffer Overflow vulnerability has been found in X pdf a PDF displayer for Unix-based systems While the vulnerability is very interesting |
|
Windows Heap Overflows
This presentation will examine how to exploit heap based buffer overflows on the Windows platform Heap overflows have been well |
|
Les buffer overflowspdf - X-Files
Un buffer overflow est une faute d'implémentation consistant à déborder de la mémoire allouée pour une opération • La plupart des BO dus au programmeur |
|
Buffer Overflow Attack
Buffer overflow can happen on both stack and heap The ways to exploit them are quite different In this chapter we focus on the stack-based buffer |
|
CS 356 – Lecture 21 and 22 Buffer Overflow
A buffer overflow also known as a buffer overrun is defined in the NIST Glossary of Key Information Security Terms as follows: |
|
Buffer overflow
A buffer overflow occurs when a program or process attempts to write more data http://www-inst eecs berkeley edu/~cs161/fa08/papers/stack_smashing pdf |
|
Buffer Overflows - UCSB Computer Science
Buffer Overflow: happens when a program attempts to write data outside of the memory allocated for that data – Usually affects buffers of fixed size |
|
Buffer Overflow Attack and Defense Techniques - KoreaScience
20 déc 2021 · Buffer overflows are a common occurrence in most organizations today and weakness is created by the vulnerability in cases where memory near a |
|
Heap Overflows Illustrated 10
A fake heap chunk header which is shifted into position via a heap overflow may be used to overwrite virtually any 4-byte word in memory This attack uses |
|
Heap Overflow on Metadata
Heap Overflow on Metadata Software Security The heap is pool of memory used for dynamic allocations at runtime: ○ malloc() grabs memory on the heap |
|
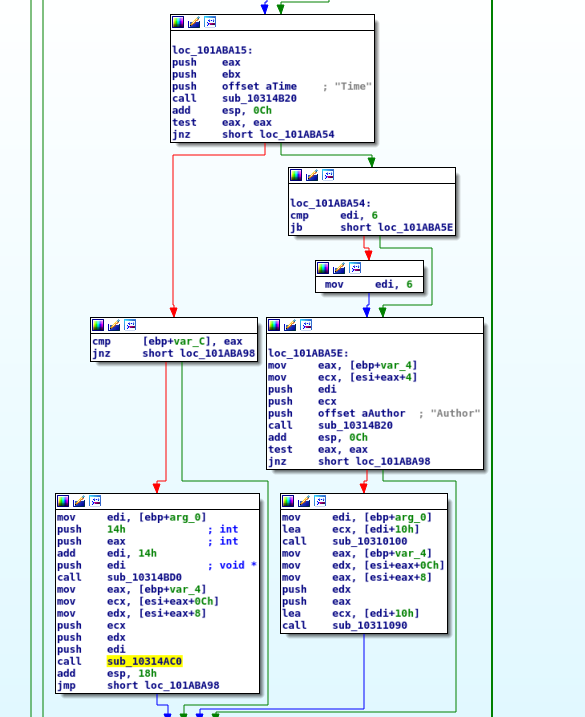
Windows Heap Overflow Exploitation
The vulnerability that we'll exploit together today is a 'heap' overflow vulnerability that's occuring in a custom heap built by the application The vulnerable software |
|
Windows Heap Overflows
This presentation will examine how to exploit heap based buffer overflows on the Windows platform Heap overflows have been well documented on *nix |
|
Prospector: accurate analysis of heap and stack overflows by means
In this paper, we address the problem of polymorphic buffer overflow attacks on heap and stack Given their long history and the wealth of counter-measures, it is |
|
Heap Overflows and Double-Free Attacks
Heap Overflow ◇Overflowing buffers on heap can change pointers that point to important data - Illegitimate privilege elevation: if program with overflow |
|
Defeating Microsoft Windows XP SP2 Heap protection and DEP
singly-linked lookaside list Fig 4 Heap Overflow Let`s take a look at this pretty simple example of a vulnerable function: |






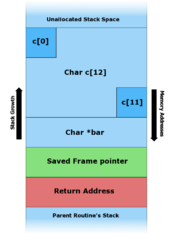
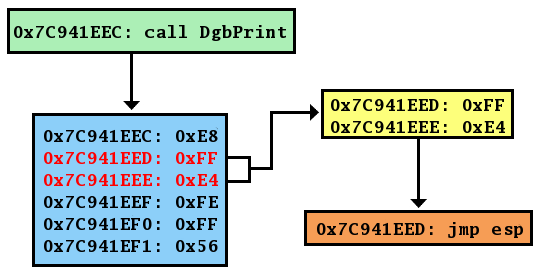






![Wrozlurg: [Z486Ebook] Free PDF Windows Exploitation Course: Stack Wrozlurg: [Z486Ebook] Free PDF Windows Exploitation Course: Stack](https://samsclass.info/127/proj/p7-heap5.png)