host header injection owasp
|
Less Known Web Application Vulnerabilities
NoSQL Injection*. •. XML External Entities*. •. XPATH Injection*. •. LDAP Injection*. •. Web Cache Deception Attack*. •. Host Header Injection*. |
|
Less Known Web Application Vulnerabilities
Speaker @ Defcon OWASP |
|
HTTP SECURITY HEADERS (Protection For Browsers)
Can be used maliciously for a clickjacking attack or loading a malicious website inside the frame. Prevention: • Frame busting. • X-Frame-Option Header |
|
OWASP Top 10 2017
13.11.2017 ?. Injection can sometimes lead to complete host takeover. The business impact depends on the protection needs of your application and data. |
|
OWASP Plan - Strawman
11.11.2010 ?. ?Analysis of HTTP POST DDOS attack ... capabilities of host => higher lethality. ... ?Slowloris used time-delayed HTTP headers to. |
|
Application Security Verification Standard 4.0 - Final
OWASP's Stance on ASVS Certifications and Trust Marks . Description of the half-open Attack . ... V14.4 HTTP Security Headers Requirements . |
|
Xavier Mertens - OWASP Belgium Chapter - May 2017
22.05.2017 ?. or the Bad. Xavier Mertens - OWASP Belgium Chapter - May 2017 ... is used to pivot further to internal hosts.” ... Host Headers Attack. |
|
Testing Guide
Testing for Command Injection (OTG-INPVAL-013) At The Open Web Application Security Project (OWASP) we're ... ded in the HTTP 1.1 Host: header [1]. |
|
SSRF bible. Cheatsheet
HTTP CRLF injection unrestricted port and host (restricted by firewalls First look at slides 33-37 of ?SSRF attack and sockets presentation?. Examples. |
|
XML Based Attacks
Billion Laughs Attack / XML Bomb Server Side Request Forgery attack example: ... Content-Type header (1). HTTP Request: POST /update.php HTTP/1.1. Host: ... |
|
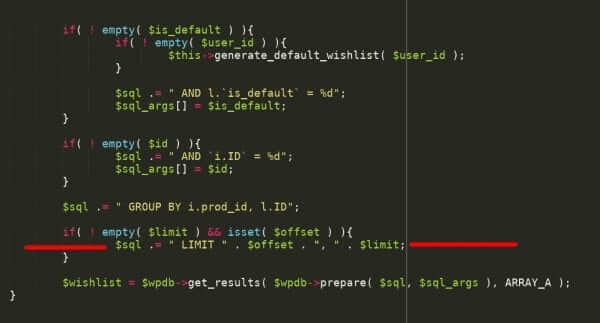
Testing for Host Header Injection - OWASP Foundation
Initial testing is as simple as supplying another domain (i e attacker com ) into the Host header field It is how the web server processes the header value |
|
Testing for Host Header Injection - WSTG - v42 OWASP Foundation
Initial testing is as simple as supplying another domain (i e attacker com ) into the Host header field It is how the web server processes the header value |
|
HTTP Headers - OWASP Cheat Sheet Series
In this cheat sheet we will review all security-related HTTP headers recommended configurations and reference other sources for complicated headers Security |
|
Session Fixation – the Forgotten Vulnerability? - OWASP Foundation
7 oct 2009 · http://www owasp Session Management not provided for HTTP (stateless) bakery http response splitting http header injection |
|
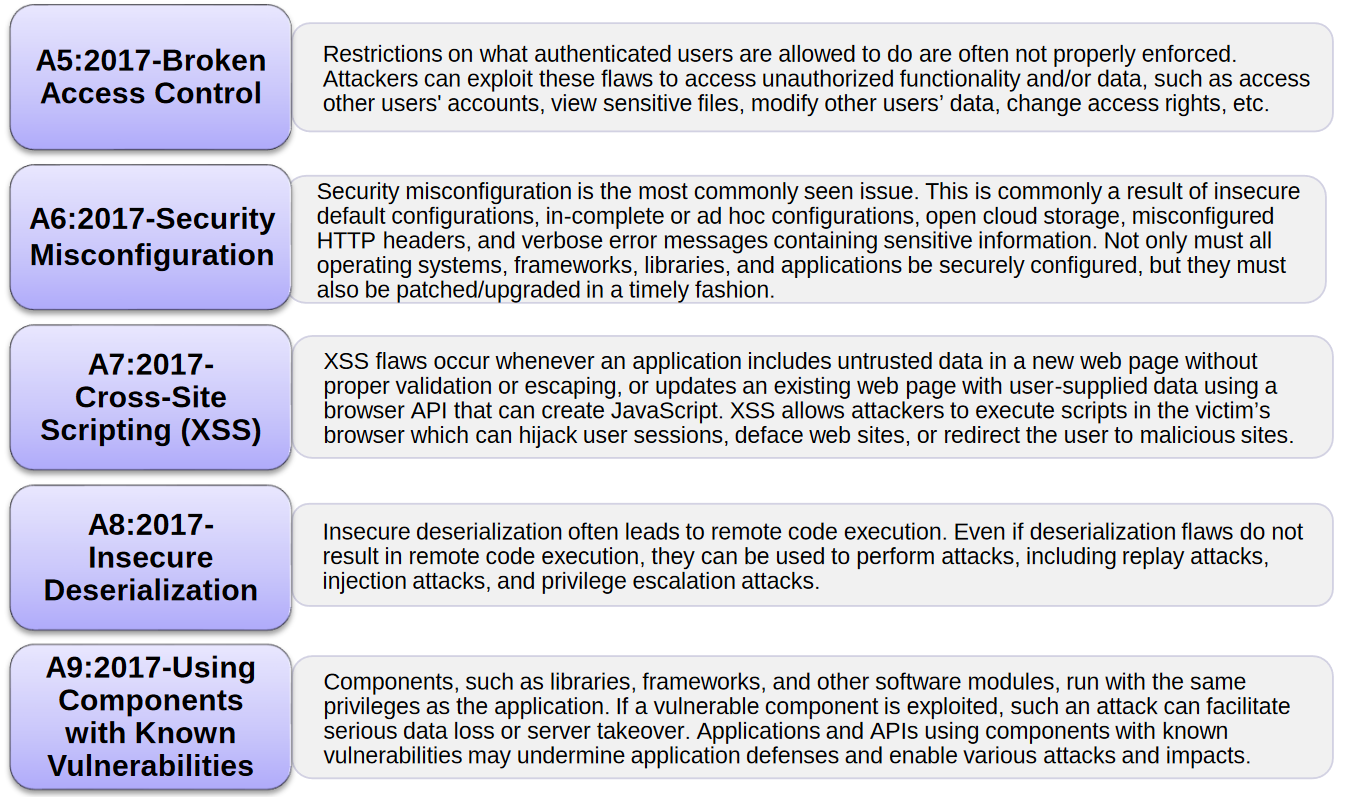
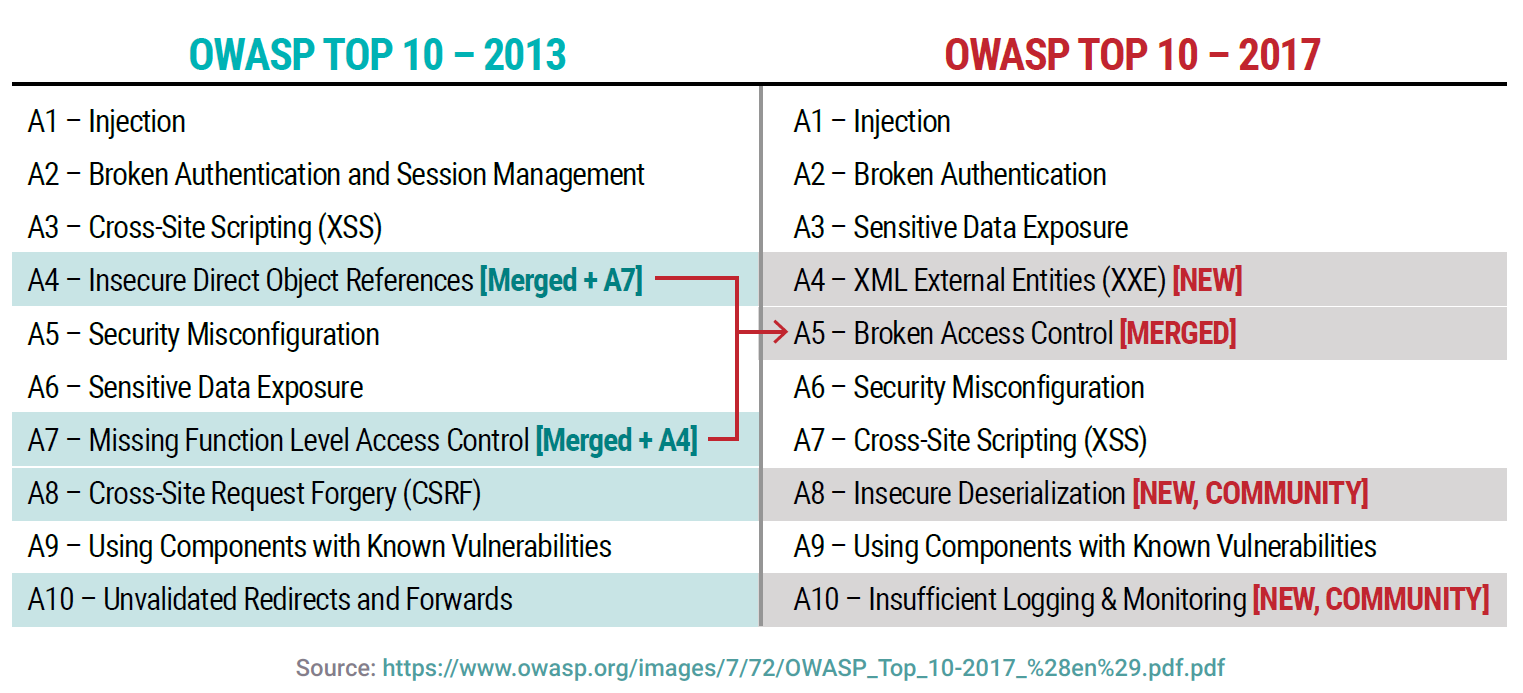
OWASP Top 10 - 2013
Injection can sometimes lead to complete host takeover Consider the business value of the affected data and the platform running the interpreter All data |
|
Testing Guide - OWASP Foundation
Manual reviews are particularly good for testing whether people Four examples of the HTTP response headers are shown below |
|
OWASP TESTING GUIDE
security test for a SQL injection vulnerability for example a black box test might involve Four examples of the HTTP response headers are shown below |
|
OWASP Top 10 - 2017
Injection vulnerabilities are often found in SQL LDAP XPath or NoSQL queries OS commands XML parsers SMTP headers expression languages and ORM queries |
|
OWASP Top 10 2017
13 nov 2017 · Injection vulnerabilities are often found in SQL LDAP XPath or NoSQL queries; OS commands; XML parsers SMTP headers expression languages |
|
OWASP Testing Guide v2
vulnerabilities such as SQL Injection by code inspection and penetration ual host we are referring to is embedded in the HTTP 1 1 Host: header [1] |
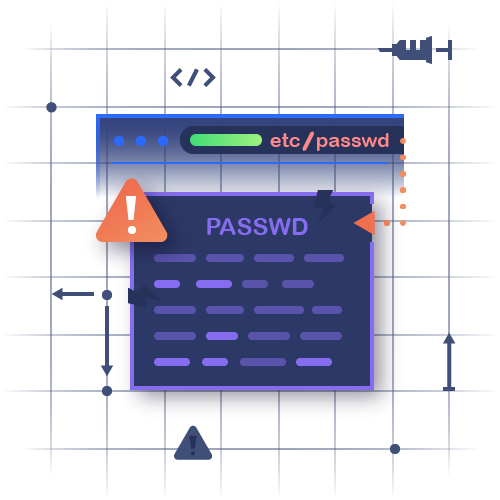
What is HTTP Host header injection?
What is a Host header injection? The HTTP host header injection is an attack in which a malevolent actor tampers with the host header in a client request. This misleads the virtual host or intermediary system to serve poisoned content to the client in the response.What is the vulnerability of Host header injection?
HTTP Host header attacks exploit vulnerable websites that handle the value of the Host header in an unsafe way. If the server implicitly trusts the Host header, and fails to validate or escape it properly, an attacker may be able to use this input to inject harmful payloads that manipulate server-side behavior.How can we mitigate Host header injection?
In some cases Host header injection is mitigated by prohibiting tampering of Host header.
Host header injection can be mitigated by rejecting any request that doesn't match the target domain. Validating Host header to ensure that the request is originating from that target host or not.- Injection is an attacker's attempt to send data to an application in a way that will change the meaning of commands being sent to an interpreter. For example, the most common example is SQL injection, where an attacker sends “101 OR 1=1” instead of just “101”.
|
Less Known Web Application Vulnerabilities
Web Cache Deception Attack • Host Header Injection • HTTP Header Injection • HTTP Parameter Pollution • DNS Rebinding • Server Side Template |
|
Less Known Web Application Vulnerabilities
Web Cache Deception Attack* • Host Header Injection* • HTTP Header Injection* • HTTP Parameter Pollution* • DNS Rebinding* • Client Side Template |
|
OWASP RUBY ON RAILS SECURITY GUIDE - OWASP Foundation
Header Injection 3 HTTP is a stateless protocol, sessions make it stateful This attack focuses on fixing a user's session id known to the attacker, and forcing |
|
HTTP SECURITY HEADERS (Protection For Browsers)
I'll explain some of the different HTTP response headers that a web server can include in a This header prevents MiTM attack against compromised Certificate |
|
OWASP Web Application Security
OWASP Top 10 - Most exploited vulnerabilities of the year HTTP Response Headers Injection ○ Over 90 of the website are vulnerable for injections |
|
SSRF bible Cheatsheet
First look at slides 33-37 of SSRF attack and sockets presentation Examples statuses 300,305,306,307 or by http response splitting/http header injection |
|
OWASP Top 10 - OWASP Foundation
Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when HTTP headers, and verbose error messages containing sensitive information |
|
Developers mistake is Attackers Paradise Introduction and
Number Vulnerability Name Categories 1 Autocomplete not disabled 16 SQL Injection Input Validation Host Header Poisoning with XSS contd |
|
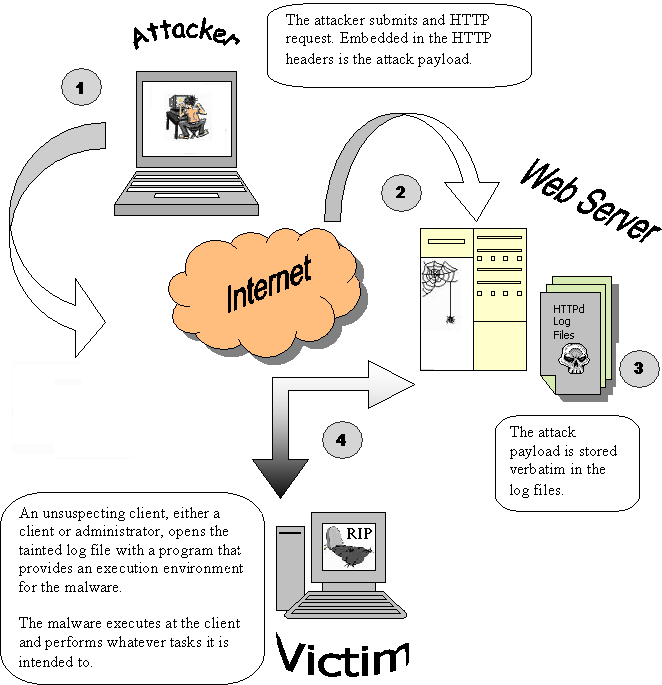
E-Mail Header Injections An Analysis of the World Wide - CORE
HTTP Header Injection vulnerability [20] The vulnerability exists in the reference implementation of the built-in “mail” functionality in popular languages like PHP, |
|
Web Application Vulnerability Report 2019 - HubSpot
Host Header Injection Directory Listing TLS/SSL Vulnerabilities WordPress Vulnerabilities Web Server Vulnerabilities and Misconfigurations Conclusion |