host header injection payloads
|
Hunting Asynchronous Vulnerabilities
•Quality of Payload is crucial. •Environment-?insensitive SMTP HEADER INJECTION ... <?xml-stylesheet type="text/xml" href="http://xsl.evil.net/a.xsl"?>. |
|
Code Injection Vulnerabilities in Web Applications - Exemplified at
of some payload types without eliminating the actual vulnerability. the HTTP body (as POST parameters) or the HTTP header (i.e. |
|
Web Application Firewall Bypassing –
Understands HTTP traffic better than traditional firewalls A user is in control of the following HTTP Headers: ... SQL Injection payload found:. |
|
SSRF bible. Cheatsheet
statuses 300305 |
|
Security Assessment AppCheck Labs
13-Jun-2019 HTTP Header Injection . ... A SQL Injection vulnerability was detected by injecting a payload designed ... Each injected payload is designed. |
| EXPLOITING CORS MISCONFIGURATIONS |
|
Remote Code Execution with EL Injection Vulnerabilities
29-Jan-2019 First test case help us to understand Expression language. We can see an error messages and stack trace which help us to develop our payload. |
|
Injection Attacks Reloaded: Tunnelling Malicious Payloads over DNS
13-Aug-2021 show how to construct malicious payloads to launch injection ... tions [57] LDAP injections [58] |
|
XML Based Attacks
SQL Injection. Classic example: http://target.com/login.php?user=admin&pass=a'+or+'1'='1. Equivalent XML Payload: <?xml version="1.0" encoding="UTF-8"?>. |
|
GIAC
20-Dec-2015 Blind code injection (Ruby's open());. • Host header attacks. Instead of developing the attack methods from scratch the ActiveScan++. |
|
How to identify and exploit HTTP Host header vulnerabilities
When probing for Host header injection vulnerabilities the first step is to the target application while potentially injecting a payload via the port |
|
HTTP Host header attacks Web Security Academy - PortSwigger
Attacks that involve injecting a payload directly into the Host header are often known as "Host header injection" attacks Off-the-shelf web applications |
|
Testing for Host Header Injection - OWASP Foundation
Initial testing is as simple as supplying another domain (i e attacker com ) into the Host header field It is how the web server processes the header value |
|
AllAboutBugBounty/Host Header Injectionmd at master - GitHub
Attacks that involve injecting a payload directly into the Host header are often known as "Host header injection" attacks |
|
Host Header Attacks Learn AppSec Invicti
What is a Host header attack? HTTP Host header attacks are any attacks performed by manipulating the value of the Host header in an HTTP request |
|
All You should know about HTTP Host Header Injection
16 jui 2022 · An HTTP Host header attack is a type of attack where the attacker sends a request to a server with a fake Host header |
|
HTTP Host Header Attacks - CQR Company
17 fév 2023 · HTTP Host Header Attacks refer to a type of web application attack where an attacker manipulates the Host header field in an HTTP request to |
|
Host header Injection - HTTP Host header attacks What is the HTTP
Attacks that involve injecting a payload directly into the Host header are often known as "Host header injection" attacks Off-the-shelf web applications |
|
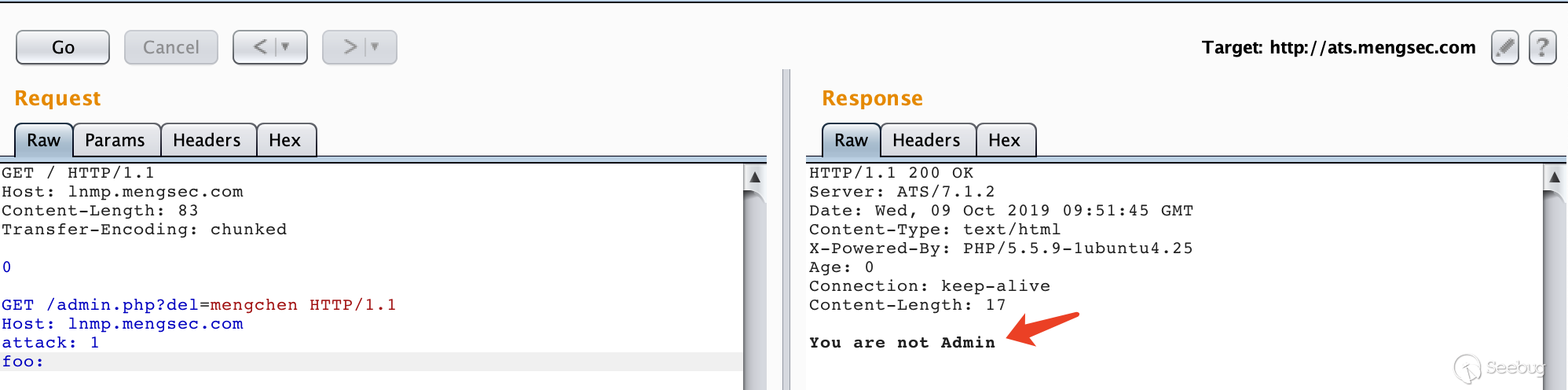
Host Header Injection Lead To Account Takeover - System Weakness
Hello amazing hacker Today I want to talk about one of my findings in a private pentest program that leads me to take over other user accounts with one |
|
HTTP Response Splitting
HTTP Response Splitting is a protocol manipulation attack similar to Message Headers – metadata that describes a request or response |
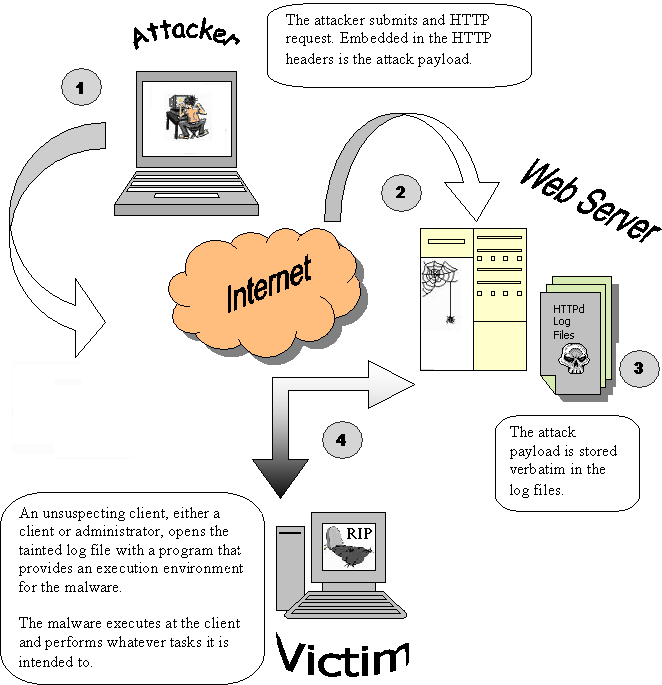
What is a Host header injection?
What is a Host header injection? The HTTP host header injection is an attack in which a malevolent actor tampers with the host header in a client request. This misleads the virtual host or intermediary system to serve poisoned content to the client in the response.How can we mitigate Host header injection?
To prevent HTTP Host header attacks, the simplest approach is to avoid using the Host header altogether in server-side code. Double-check whether each URL really needs to be absolute. You will often find that you can just use a relative URL instead.What is the impact of Host header injection vulnerability?
Impact. Tampering of Host header can lead to the following attacks: 1) Web Cache Poisoning-Manipulating caching systems into storing a page generated with a malicious Host and serving it to others.- Introduced in HTTP 1.1, a host header is a third piece of information that you can use in addition to the IP address and port number to uniquely identify a Web domain or, as Microsoft calls it, an application server. For example, the host header name for the URL http://www.ideva.com is www.ideva.com.
|
E-Mail Header Injections An Analysis of the World Wide - CORE
Inject the forms that sent us e-mails with malicious payloads, and generate an HTTP request to the corresponding URL to check if E-Mail Header Injection |
|
E-Mail Header Injections An Analysis of the World Wide Web by Sai
Inject the forms that sent us e-mails with malicious payloads, and generate an HTTP request to the corresponding URL to check if E-Mail Header Injection |
|
Less Known Web Application Vulnerabilities
Web Cache Deception Attack • Host Header Injection • HTTP Header Injection Attacker will use this payload O:7:"LogFile":1:{s:8:"filename";s:9:" htaccess";} |
|
Cracking the Lens: Targeting HTTPs Hidden Attack Surface
Instead, we're going to send payloads designed to make these systems contact us, and learn from the resulting DNS lookups and HTTP requests All the findings |
|
Countering Web Injection Attacks: A Proof of Concept - School of
Within this HTTP exploit the attacker smuggles the request using encapsulation techniques to embed a secondary HTTP header within the original HTTP payload , |
|
This could be the user input in header
HTTP Response Splitting The Attack • An HTTP message response includes two parts : – Message Headers – metadata that describes a request or response |
|
Code Injection Vulnerabilities in Web Applications - OPUS 4 – KOBV
vey of publicly documented XSS payloads which is structured according to our the HTTP body (as POST parameters), or the HTTP header (i e , the Cookie |