how to hack two factor authentication
|
Eleven Ways to Defeat Two-Factor Authentication
More on this later. We need to understand some basic concepts to better understand hacking 2FA. Introduction to Two-Factor Authentication |
|
12 Ways to Hack 2FA - by Roger A. Grimes Data-Driven Defense
But MFA isn't unhackable. First we need to understand some basic concepts to better understand hacking MFA. Introduction to Multi-Factor Authentication |
|
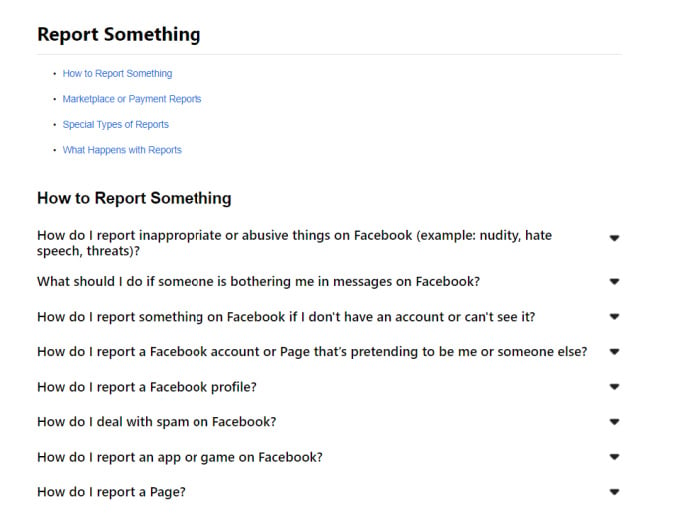
202109171300_NCSAM 21_Utilizing Two Factor Authorization
Two Factor Authentication (2FA) is process in which a user must provide two different types of the advanced nature of hacking can be cracked. |
|
12+ Ways to Hack Multi-Factor Authentication
Ways to Hack MFA? All multi-factor authentication (MFA) mechanisms can be compromised and in some case |
|
Teaching Case Employing two factor authentication mechanisms: A
This case study examines the life of a digital native who has her online accounts hacked passwords reset |
|
Hacking Multifactor Authentication
Wrote free 12 Ways to Hack 2FA ebook. • https://info.knowbe4.com/12-way-to-hack-two-factor-authentication. •. Helped develop the Multifactor Authentication |
|
Spade_Doc_Data Privacy.psd
There Are 12+ Ways To Hack Two-Factor & Multi-Factor Authentication. All forms of multi-factor and two-factor authentication can be hacked. |
|
12 Ways to Hack MFA
Introduction to Multi-Factor Authentication. •. Location behavior |
|
View The Email to Get Hacked: Attacking SMS-Based Two-Factor
Aug 11 2019 Additionally |
|
A Usability Study of Five Two-Factor Authentication Methods
Aug 13 2019 Two-factor authentication (2FA) defends against account com- promise. ... know if people hack your credit cards |
|
12 Ways to Hack 2FA - KnowBe4
But MFA isn't unhackable First we need to understand some basic concepts to better understand hacking MFA Introduction to Multi-Factor Authentication |
|
12+ Ways to Hack Multi-Factor Authentication - KnowBe4
All multi-factor authentication (MFA) mechanisms can be compromised and in some cases it's as simple as sending a traditional phishing email This white paper |
|
Many Ways to Hack Multi-Factor Authentication
Solution: Never answer the questions with the real answers! Unfortunate that means you have to record them somewhere else just like passwords (password managers |
|
The many ways to hack 2FA - ResearchGate
To read the full-text of this research you can request a copy directly from the author Request full-text PDF |
|
(PDF) Two-factor authentication: is the world ready? - ResearchGate
two-factor authentication (2FA) 2FA is an enhanced authentication mechanism for protecting users that have their password stolen either by leaking a server's |
|
The many ways to hack 2FA - ScienceDirectcom
This article shows how it's possible to hack MFA and gives many examples of For example no matter how you authenticate to a website (eg 1FA 2FA or |
|
View The Email to Get Hacked: Attacking SMS-Based Two-Factor
11 août 2019 · We describe a detailed account of a phishing attack that mimics the Gmail confidential mode to obtain the OTP sent via SMS as part of a 2FA |
|
Hacking Multifactor Authentication Wiley Online Books
2 oct 2020 · Protect your organization from scandalously easy-to-hack MFA security “solutions” Multi-Factor Authentication (MFA) is spreading like |
|
TWO-FACTOR AUTHENTICATION PREVENTS HACKERS FROM
Even if a hacker knows a username and password “2FA” will help to block them out Here's how two-factor authentication works in its simplest form |
|
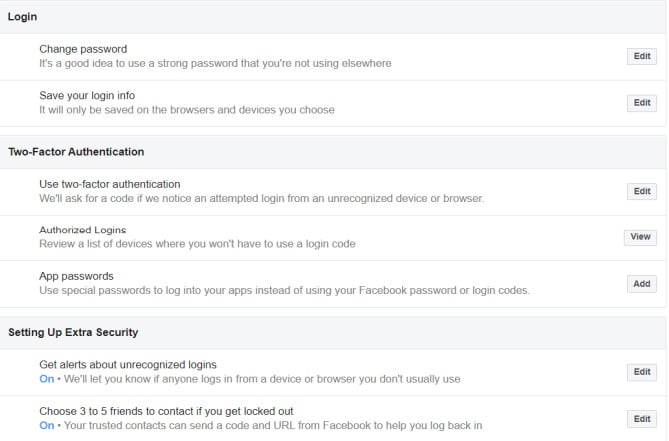
More than a Password - CISA
Multifactor Authentication; Two Step Authentication; 2-Step Verification; Two Factor Users who enable MFA are significantly less likely to get hacked |
Is it easy to hack 2 factor authentication?
2FA uses exactly two factors, while MFA can use two or more. By requiring multiple factors for authentication, 2FA and MFA make it harder to gain unauthorized access to a system because guessing a password is no longer enough. However, depending on the factors used, it still may be possible to bypass MFA security.Can I bypass 2 factor authentication?
Password reset
One of the easiest and, therefore, most common ways to bypass two-factor authentication is by simply utilizing the password reset function of websites and applications.Can Google 2FA be hacked?
Usually 2FA security codes are sent to the user's phone via SMS, but this also carries a security risk. Hackers can sometimes engineer an attack on your phone company and thus compromise SMS-based one-time-passwords (OTPs).- External authenticator apps like Microsoft Authenticator or Google Authenticator don't use codes, so no codes can be intercepted.
|
Eleven Ways to Defeat Two-Factor Authentication - KnowBe4
But 2FA isn't unhackable • More on this later We need to understand some basic concepts to better understand hacking 2FA Introduction to Two-Factor |
|
12 Ways to Hack 2FA - KnowBe4
What is a Data-Driven Defense Evangelist? Page 6 • Multi-Factor Authentication Intro • Hacking MFA • Defending Against MFA |
|
Hacking 2FA REV3_UNLINKED - US Datavault
overall security defense Do You Know the 12+ Ways to Hack 2FA? All multi- factor authentication (MFA) mechanisms can be compromised, and in some case, |
|
Teaching Case Employing two factor authentication mechanisms: A
This case study examines the life of a digital native who has her online accounts hacked, passwords reset, and is locked out of important online resources |
|
How to Attack Two-Factor Authentication Internet Banking
To bet- ter be prepared for what the future might bring, we try to predict how hacking tools might evolve We briefly survey the state-of-the-art tools developed by |
|
PDF :9 - Centerpoint IT
All forms of multi-factor and two-factor authentication can be hacked This can even be done by a hacker simply sending you a phishing email How can you |
|
View The Email to Get Hacked: Attacking SMS-Based Two-Factor
19 août 2019 · We describe a detailed account of a phishing attack that mimics the Gmail confidential mode to obtain the OTP sent via SMS as part of a 2FA login |
|
TeleSign 2FA Infographic
old or repeated passwords that are easily hacked YOUR OWN to steal or hack, but 2FA can help protect you from a potentially devastating account breach |


![PDF] View The Email to Get Hacked: Attacking SMS-Based Two-Factor PDF] View The Email to Get Hacked: Attacking SMS-Based Two-Factor](https://i.pcmag.com/imagery/articles/07eNfkqOzVEr9QFJPzpQ180-1..1569470587.jpg)


![PDF] View The Email to Get Hacked: Attacking SMS-Based Two-Factor PDF] View The Email to Get Hacked: Attacking SMS-Based Two-Factor](https://www.securitynewspaper.com/snews-up/2020/09/mfa.jpg)

![PDF] View The Email to Get Hacked: Attacking SMS-Based Two-Factor PDF] View The Email to Get Hacked: Attacking SMS-Based Two-Factor](https://cdn.thewirecutter.com/wp-content/uploads/2019/10/5cheapish-digital-security-lowres-4636.jpg)





![Web Hacking 101 by Peter Yaworski [Leanpub PDF/iPad/Kindle] Web Hacking 101 by Peter Yaworski [Leanpub PDF/iPad/Kindle]](https://office-watch.com/fredagg/uploads/two-factor-authentication-straight-talk-microsoft-office-25041.png)