http response splitting payload github
|
HTTP Request Smuggling in 2020 – New Variants New Defenses
“Technical Note: Detecting and Preventing HTTP Response Splitting and HTTP Request how I implemented my payloads is available in SafeBreach Labs' GitHub. |
|
HTTP Request Smuggling in 2020
However HTTP Request Smuggling payloads can get blocked as HTTP. Response Splitting attacks… • Variant 1 with SP (payload) is blocked by two rules: 921130 |
|
Karate
2 abr de 2020 Karate github.com/intuit/karate ... Given path response.id ... Payload assertion in one line. Second HTTP call using response data. |
|
AWS Lambda - Developer Guide
Request and response payloads . version or split traffic between two versions. ... assign a dedicated HTTP endpoint to your Lambda function. |
|
AWS Step Functions - Developer Guide
Starting a State Machine Execution in Response to Amazon S3 Events . and let Step Functions progress to the next state after it gets an HTTP response. |
|
DETECT BYPASS VULNERABILITIES IN CELLULAR ISP
30 dic de 2015 HTTP request or inserting a malicious payload into the web application. ... Response Splitting HTTP Request Smuggling and HTTP Response ... |
|
SDN Framework
In order to receive a response from the switch create an event handler that Next |
|
Scarecrow: Deactivating Evasive Malware via Its Own Evasive Logic
payload-agnostic such that it is able to deactivate highly obfuscated zero-day evasive HTTP response from the non-existent domain it exits without. |
|
SSRF bible. Cheatsheet
statuses 300305 |
|
AWS Command Line Interface - User Guide for Version 2
18 sept de 2019 AWS CLI GitHub repository You can view and fork the source code for the AWS CLI ... values exactly as received in the HTTP query response. |
|
Hacktricks/crlf-0d-0amd at master - GitHub
HTTP Response Splitting Description Since the header of a HTTP response and its body are separated by CRLF characters an attacker can try to inject |
|
HTTP Response Splittingbb at master · 1N3/IntruderPayloads - GitHub
A collection of Burpsuite Intruder payloads BurpBounty payloads fuzz lists malicious file uploads and web pentesting methodologies and checklists |
|
Http-response-splitting · GitHub Topics
To associate your repository with the http-response-splitting topic visit your repo's landing page and select "manage topics " Learn more Footer © 2023 |
|
Bugbounty-cheatsheet/crlfmd at master · EdOverflow - GitHub
A list of interesting payloads tips and tricks for bug bounty hunters - bugbounty-cheatsheet/crlf md at CRLF Injection HTTP Response Splitting |
|
CRLF (%0D%0A) Injection - HackTricks
An example of HTTP Response Splitting leading to XSS You can send the payload inside the URL path to control the response from the server: |
|
HTTP Response Splitting
HTTP Response Splitting is a protocol manipulation attack similar to The attack is valid only for applications that use HTTP to exchange data |
|
Attacking Websites: Detecting and Preventing HTTP Request
27 oct 2022 · This paper proposes a general solution to deal with various HTTP request smuggling attacks A reverse proxy implemented by Flask validates |
|
Web Application Firewall DRS rule groups and rules - Microsoft Learn
3 jan 2023 · This article provides information on Web Application Firewall DRS rule groups and rules |
|
CRLF injection attack Examples and Prevention - Wallarm
28 mar 2022 · HTTP Response Splitting infers the utilization of CRLF combination to separate a HTTP reaction header Information input that isn't killed |
|
Karate Test Automation Made Simple
Karate is the only open-source tool to combine API test-automation mocks performance-testing and even UI automation into a single unified framework |
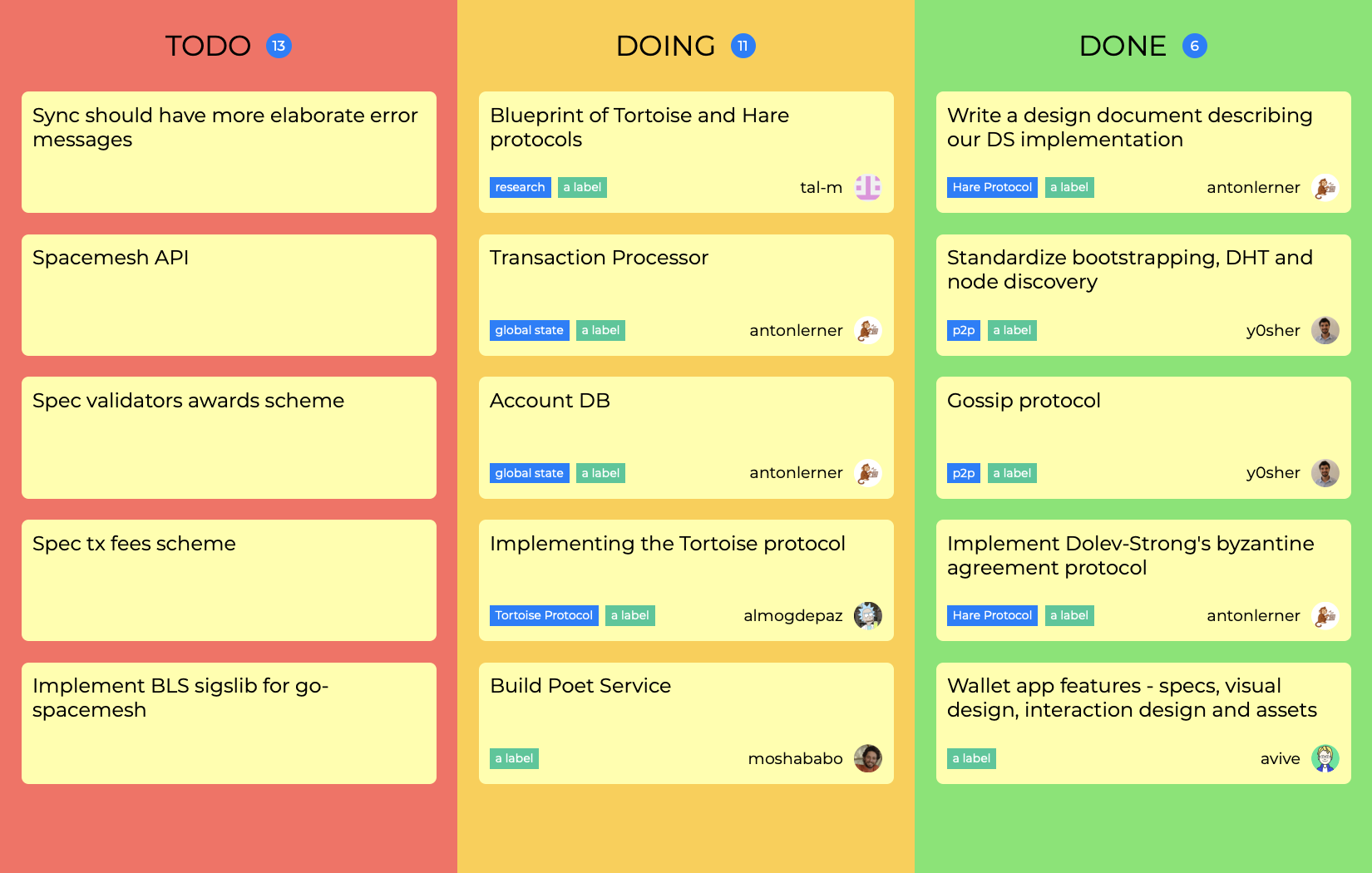
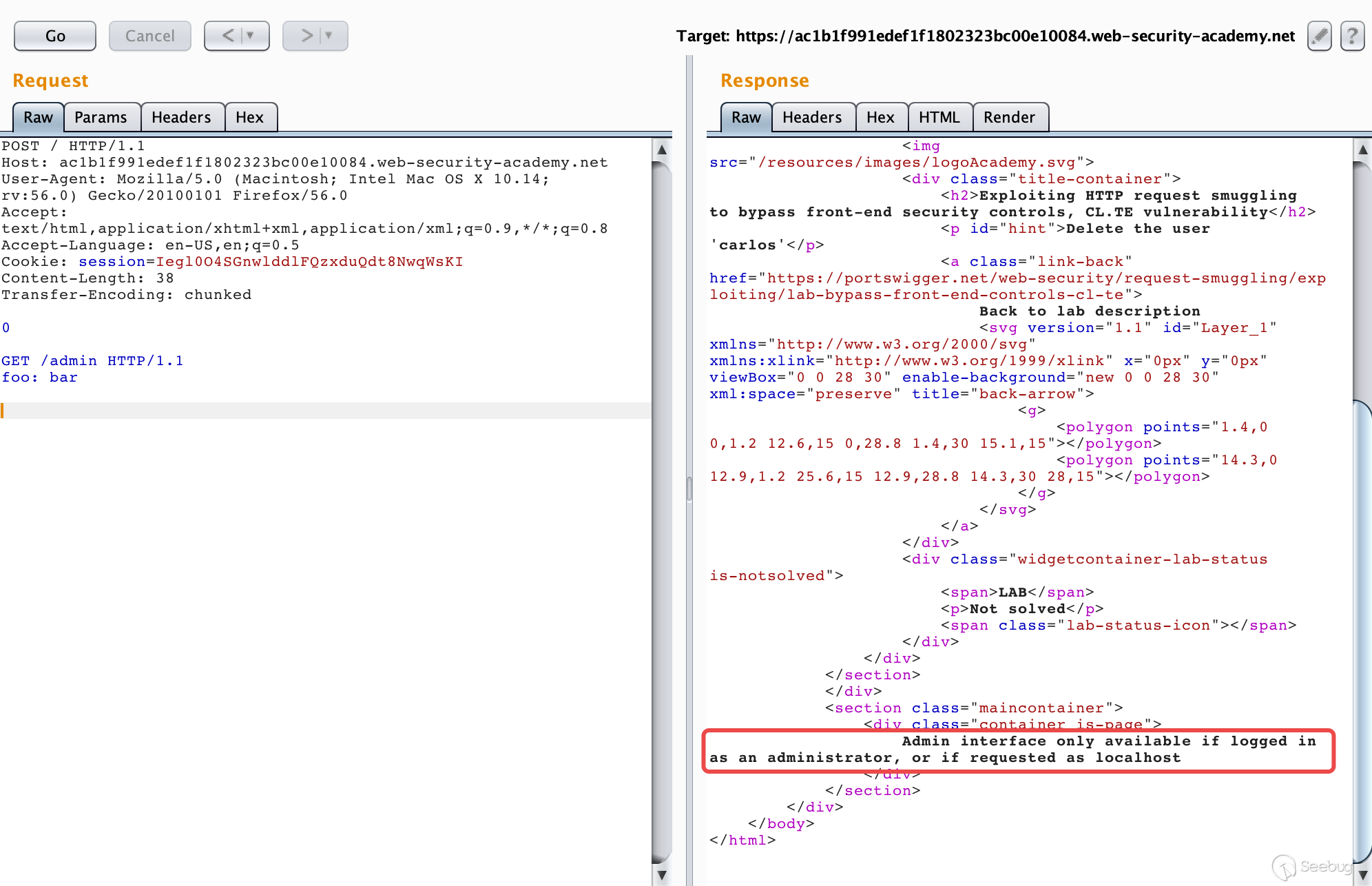
What is CRLF injection and HTTP response splitting vulnerability?
CRLF injection is a software application coding vulnerability that occurs when an attacker injects a CRLF character sequence where it is not expected. When CRLF injection is used to split an HTTP response header, it is referred to as HTTP Response Splitting.What is the risk of CRLF injection?
CRLF injections are vulnerabilities where the attacker is able to inject CR (carriage return, ASCII 13) and LF (line feed, ASCII 10) characters into the web application. This lets the attacker add extra headers to HTTP responses or even make the browser ignore the original content and process injected content instead.What is the CRLF character sequence?
In the HTTP protocol, the CR-LF sequence is always used to terminate a line. A CRLF Injection attack occurs when a user manages to submit a CRLF into an application. This is most commonly done by modifying an HTTP parameter or URL.- Carriage return line feed not only marks where a new HTTP header begins or ends, but it also tells the user where a line begins or ends in a file or a block of text. The operating systems also use these CRLF characters. CR and LF are used to end lines in Windows, but only LF is used in UNIX/Linux.
|
Introduction - Black Hat
“Technical Note: Detecting and Preventing HTTP Response Splitting and HTTP how I implemented my payloads is available in SafeBreach Labs' GitHub |
|
SSRF bible Cheatsheet
HTTP response encapsulation into XML formatted response Console PHP ( require dlopen, but not exec): https://github com/dhotson/fdopen-php Basically restrictions which you may find in SSRF exploitation can be split into two groups: |
|
Your Cache Has Fallen: Cache-Poisoned Denial-of - CPDoS
Web caching enables the reuse of HTTP responses with the aim to reduce the number of is successful, the response splitting attack exploits a parsing issue in the origin zon S3, Github Pages, Gitlab Pages, Google Storage and Heroku As with the first error code 413 Payload Too Large for oversized headers and this |
|
Practical Web Cache Poisoning: Redefining - PortSwigger
poisoning caches - you can also use HTTP Response Splitting and Request Exploiting an unkeyed input isn't always as easy as pasting an XSS payload wordlist by downloading and scouring the top 20,000 PHP projects on GitHub for |
|
Cached and Confused: Web Cache Deception in the Wild
file in return, and treat the HTTP response accordingly (e g , web caches may cache poisoning attack is malicious payload injection and not private data |
|
HTTP REQUEST SMUGGLING - CGISecurity
We describe a new web entity attack technique – “HTTP Request Smuggling request/response sequencing which can allow for credential hijacking and other Splitting, for example, to be effective HRS does not require the existence of an Now let's see how the W/S interprets the same payload, once it has been |
|
CODDLE: Code-Injection Detection With Deep Learning - IEEE Xplore
20 sept 2019 · For more information, see http://creativecommons org/licenses/by/4 0/ 128617 proposed, by using an autoencoder for dynamic response anomaly recognition Dataset of XSS payloads was taken from the GitHub repos- itory [50] masquerade the injection splitting the operator with escape characters |