insider threat indicators
|
Insider Threat Potential Risk Indicators (PRI) - JOB AID
Individuals at risk of becoming insider threats and those who ultimately cause significant harm |
|
Cyber Awareness Challenge 2022 Insider Threat
and mitigating the risks associated with insider threats. Their activities include: • Proactively identifying insiders who exhibit potential risk indicators |
|
The Insider Threat and Its Indicators
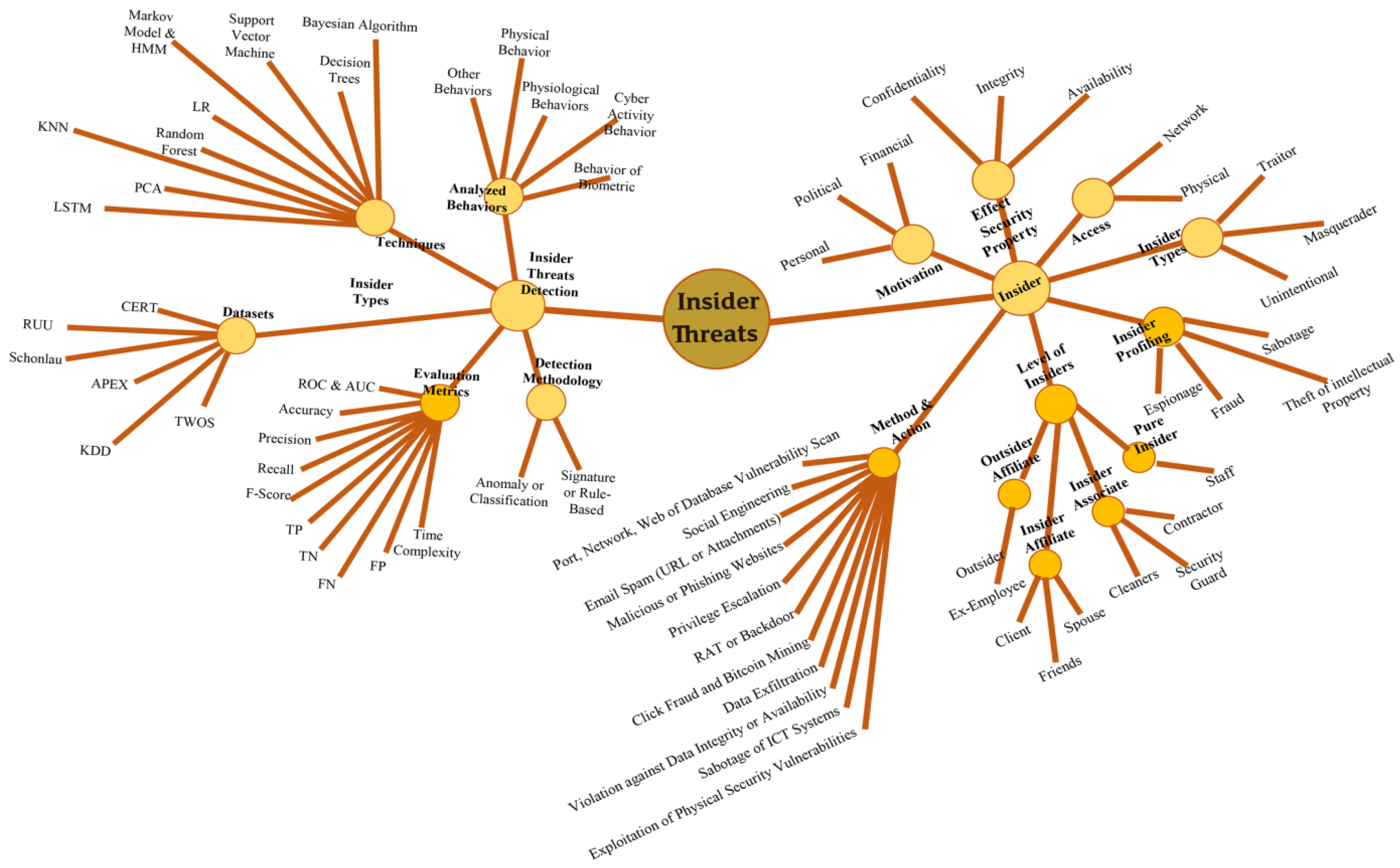
Indicators of a potential insider threat can be broken into four Keep in mind that not all insider threats exhibit all of these behaviors and not all ... |
|
Insider Threat Indicators in User Activity Monitoring Job Aid
Reporting Insider. Threat Indicators is required under. Executive Order. 13587 DoD Directive. 5205.16 and the. National Industrial. Security Program. REPORT. |
|
Insider Threat
While not all of these behaviors are definitive indicators that the individual is an insider threat reportable activities should be reported before it is too |
|
An Insider Threat Indicator Ontology
The insider threat community currently lacks a standardized method of expression for indicators of potential malicious insider activity. We believe that |
|
An Ontology for Insider Threat Indicators--Development and
threat indicator ontology. Our ontology is intended to serve as a standardized expression method for potential indicators of malicious insider activity |
|
An Insider Threat Indicator Ontology
The insider threat community currently lacks a standardized method of expression for indicators of potential malicious insider activity. We believe that |
|
Insider Threat Mitigation Guide
indicators of potential risks. 5. An Incident Response Plan in case of an insider threat incident. 6. A committee of stakeholders for program governance and. |
|
An Ontology for Insider Threat Indicators--Development and
threat indicator ontology. Our ontology is intended to serve as a standardized expression method for potential indicators of malicious insider activity |
|
The Insider Threat and Its Indicators
Indicators of a potential insider threat can be broken into four categories--indicators of: recruitment information collection information transmittal and |
|
Insider Threat Potential Risk Indicators (PRI) - JOB AID - CDSE
Individuals at risk of becoming insider threats and those who ultimately cause significant harm often exhibit warning signs or indicators PRI include a wide |
|
Cyber Awareness Challenge 2022 Insider Threat
We detect insider threats by using our powers of observation to recognize potential insider threat indicators These include but are not limited to: • |
|
Insider Threat
While each insider threat may have different motivation the indicators are generally consistent Potential Espionage Indicators • Repeated security violations |
|
Insider Threat Potential Risk Indicators (PRI) Job Aid
All organizations are vulnerable Potential Risk Indicators Most insider threats exhibit risky behavior prior to committing negative workplace events If |
|
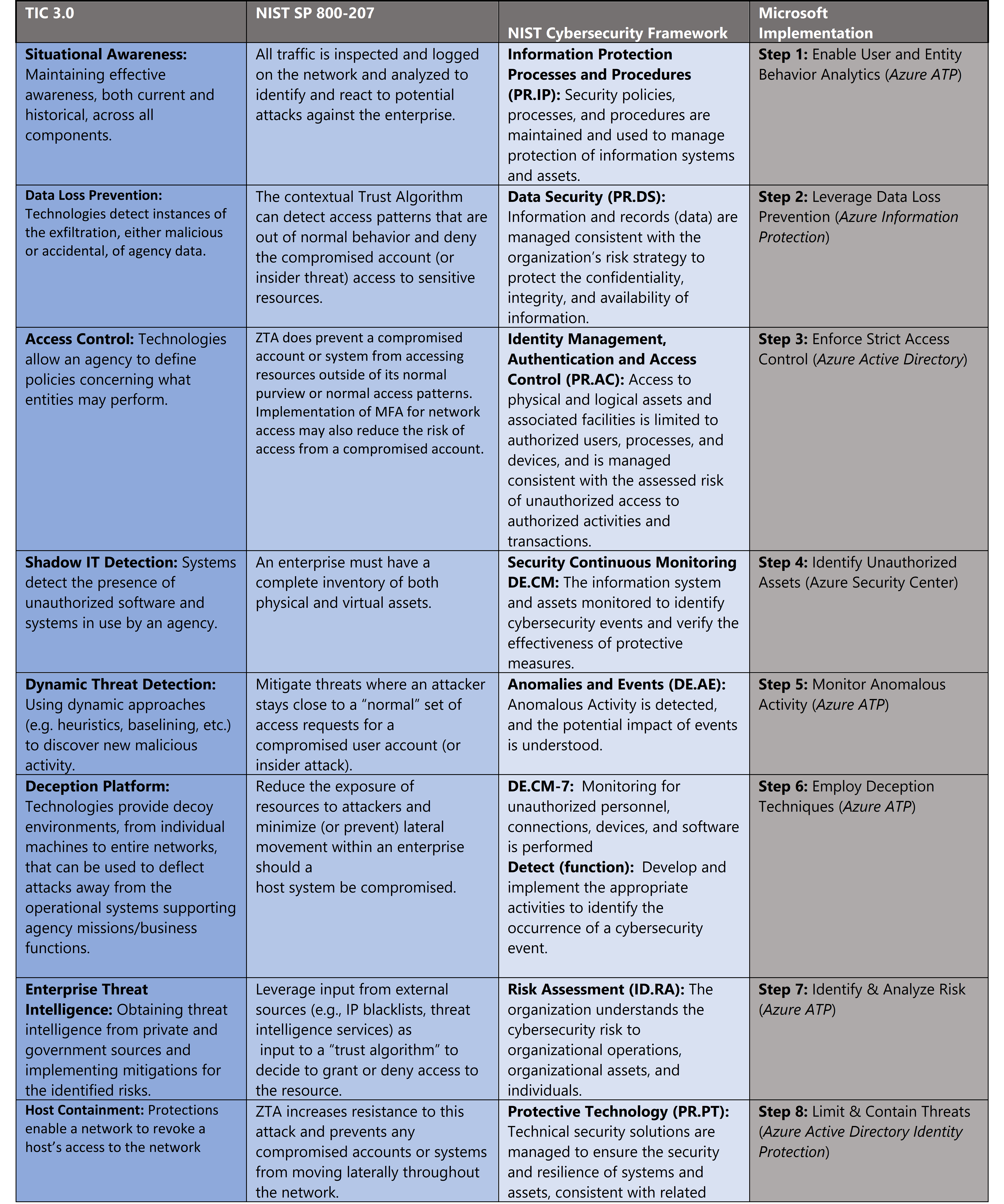
Insider Threat Mitigation Guide - CISA
Costs-of-Insider-Threats-in-this-New-Infographic pdf as the broad range of insider threat indicators discussed in Chapter 4 of this Guide |
|
Insider Threat Detection Study CCDCOE
Most importantly when analysed and handled properly these indicators act as precursors that accompany different threats Early or timely detection allows to |
|
Managing insider threat EY
Other common insider threat indicators include: • Attempts to bypass security controls • Requests for clearance or higher-level access without need |
|
INSIDER THREAT PROGRAM MATURITY FRAMEWORK
insider threats ME15: Employs behavioral science methodologies to help identify indicators of potential insider threats ME16: Employs risk scoring |
|
INSIDER THREAT - DNIgov
This guide supersedes the previous insider threat program guides issued by the NITTF and NCSC including the NITTF's 2014 “Guide to Accompany the National |
|
The Dynamic Nature of Insider Threat Indicators Request PDF
Insider threat indicators are not equally indicative of potential insider threat activity Indicator risk assessments depend not only on the number of |
What are the indicators of an insider threat?
There are clear warning signs of an insider threat, such as unusual login behavior, unauthorized access to applications, abnormal employee behavior, and privilege escalation.What are the top 5 indicators of an insider threat actor?
They could very well become compromised by a malicious third-party that then uses the trusted insider's level of access to move laterally through the network.
Types of Insider Threats.
. Malicious. Lack of Training. Inefficient Workflows. Workplace Dissatisfaction. Financial Troubles.What are the 3 phases of insider threat?
The key steps to mitigate insider threat are Define, Detect and Identify, Assess, and Manage.
. Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an organization or insider threat team.- Risk indicators include security and compliance violations, unauthorized use or disclosure, and any inappropriate efforts to view or obtain protected information outside one's need to know.
|
Insider Threat Potential Risk Indicators (PRI) Job Aid - CDSE
Anyone can be a potential insider threat All organizations are vulnerable Potential Risk Indicators Most insider threats exhibit risky behavior prior to committing |
|
Insider Threat
examples While not all of these behaviors are definitive indicators that the individual is an insider threat, reportable activities should be reported before it is too |
|
Seven Non-Technical Indicators That Might - CommsNet Group
According to the Insider Threat division of CERT, there is a strong link between negative behaviour (personal disposition) and malicious activity In fact, those that |
|
An Ontology for Insider Threat Indicators - SEI Digital Library
Abstract—We describe our ongoing development of an insider threat indicator ontology Our ontology is intended to serve as a standardized expression method |
|
Insider Threat Detection Study - NATO Cooperative Cyber Defence
For every indicator, we assess its relevance to each of the insider profiles Most importantly, when analysed and handled properly, these indicators act as |
|
Insider Threat Mitigation Guide - CISA
indicators of potential risks 5 An Incident Response Plan in case of an insider threat incident 6 A committee of stakeholders for program governance and |
|
Managing insider threat - EY
media, and demonstrating ties to high-risk personnel or outside parties Other common insider threat indicators include: • Attempts to bypass security controls |
|
An Insider Threat Indicator Ontology - DTIC
We believe that communicating potential indicators of malicious insider activity in a consistent and commonly accepted language will allow insider threat programs |
|
Insider Threats
Not every person who exhibits one or more of these indicators is involved with illicit behavior, but most of the persons who have been involved with espionage |