insider threat pdf
|
Insider Threat Mitigation Guide
insider-threat.pdf. 16Department of Homeland Security. (n.d.). Insider Threat Mitigation: What is an Insider Threat? Retrieved from cisa.gov/insider-threat ... |
|
SureView® Insider Threat
SureView Insider Threat (SVIT) has been identifying and stopping threats from within for government and Fortune. 100 customers for more than 15 years. |
|
2022 COST OF INSIDER THREATS GLOBAL REPORT
Companies spend the most on containment of the insider security incident. An average of $184548 is spent to contain the consequences of an insider threat. The |
|
Insider Threat Mitigation for U.S. Critical Infrastructure Entities
Mar 19 2564 BE Insider threats are trusted individuals in an organization who may use their authorized access to facilities |
| Preventive and protective measures against insider threats |
| Radioactive |
|
Insider Threat Potential Risk Indicators (PRI) - JOB AID
Visit CDSE's Insider Threat. Toolkit for additional training and resources at https://www.cdse.edu/Training/Toolkits/Insider-Threat-Toolkit/. pdf. HOME. NEXT. |
|
Fortinet
Espionage. To understand malicious insider threats it is important to look at the underlying motivations of insiders. Our survey panel considers fraud (55%) |
|
Combating the Insider Threat
May 2 2557 BE 1 Insider threats |
|
NITTF-Insider-Threat-Guide-2017.pdf
INSIDER THREAT PROGRAMS. ARE BETTER POSTURED TO. DETER DETECT |
|
CCDCOE
This study focuses on the threat to information security posed by insiders (i.e. insider threat) as the recent cases of Edward Snowden |
|
Insider Threat Mitigation Guide
insider-threat-maturity-report-2019.pdf. Insider Threat Mitigation Guide. Cybersecurity and Infrastructure Security Agency. |
|
Combating the Insider Threat
2 mai 2014 An insider threat is generally defined as a current or former ... 3 http://www.cis.aueb.gr/Publications/Security%20Project%202014.pdf. |
|
CCDCOE
Insider threat has to in particular |
|
Insider Threat Awareness (INT101) Student Guide
Narrator: Welcome to the Insider Threat Awareness course. Benjamin Bishop Gregory Allen. Justice |
|
INSIDER THREAT PROGRAM MATURITY FRAMEWORK
24 oct. 2018 In furtherance of our joint efforts to mitigate insider threats the National Insider Threat Task Force. (NITTF) |
|
La menace interne
1 janv. 2019 «Cybersecurity Insiders 2019 Insider Threat Report» 2019. ... /uploads/sites/3/2019/03/BetterCloud-State-of-Insider-Threats-2019-FINAL.pdf. |
|
NITTF-Insider-Threat-Guide-2017.pdf
INSIDER THREAT PROGRAMS. ARE BETTER POSTURED TO. DETER DETECT |
|
National Insider Threat Policy and the Minimum Standards
effectiveness of insider threat programs to protect classified national security information. (as defined in Executive Order 13526; hereinafter classified |
|
INSIDER THREAT PROGRAM (ITP) FOR INDUSTRY JOB AID
pdf and CSA-provided guidance to supplement unique CSA mission requirements and Industrial Security Letters (ISL) that can be accessed via the DCSA Industry |
|
Common Sense Guide to Mitigating Insider Threats Sixth Edition
the Common Sense Guide are authored by the CERT National Insider Threat Center. 15000 PDF files and more than 20 |
|
Insider Threat Mitigation Guide - CISA
This Insider Threat Mitigation Guide is an evolution in the series of resources CISA makes default/files/3597_layout_insider_threat_roadmap_0424 pdf |
|
Insider Threat Tip Card - CISA
Expresses interest in matters outside the scope of their duties • Shows signs of drug or alcohol abuse financial difficulties gambling illegal activities |
|
(PDF) Defining the Insider Threat - ResearchGate
15 jan 2023 · the best approach for detecting particular types of insiders In this paper we propose a de?nition of an insider that can be extended across |
|
(PDF) Insider threats in Cyber Security: The enemy within the gates
PDF Insider threats have become reality for civilian firms such as Tesla which experienced sabotage and intellectual property theft and Capital One |
|
Insider-threats-manualpdf - USDA Food Safety and Inspection Service
Expressing thoughts or fantasies considering the use of violence to address a real or perceived grievance threat or provocation Research methods to plan the |
|
Managing insider threat EY
What is insider threat? An insider threat is when a current or former employee contractor or business partner who has or had authorized |
|
The Insider Threat: An Introduction to Detecting and Deterring - FBI
The Insider Threat: An Introduction to Detecting and Deterring an Insider Spy This brochure serves as an Download insider_threat_brochure pdf — 714 KB |
|
The CERT® Guide to Insider Threats - Pearsoncmgcom
We have the largest collection of detailed insider threat case files that we know of in the world At the time of this publication we had more than |
|
Insider Threat Detection Study CCDCOE
This study focuses on the threat to information security posed by insiders (i e insider threat) as the recent cases of Edward Snowden Chelsea Manning and |
|
Common Sense Guide to Prevention and Detection of Insider Threats
In 2005 the first version of the Commonsense Guide to Prevention and Detection of Insider Threats was published by Carnegie Mellon University's CyLab |
|
Managing insider threat EY
In order to mitigate this risk organizations should establish a program to protect their critical assets from insider threats Depending on the |
|
The CERT® Guide to Insider Threats - Pearsoncmgcom
Practice 9: Consider Insider Threats in the Software We have the largest collection of detailed insider threat case files that we know of in the world |
|
Insider Threat Detection Study CCDCOE
Insider threat has to in particular be explored as most security Good Privacy - Program often used for signing and encrypting texts emails and files |
|
Common Sense Guide to Prevention and Detection of Insider Threats
problems regarding insider threat is the absence in many organizations of an extensive insider threat data from more than 150 case files of crimes |
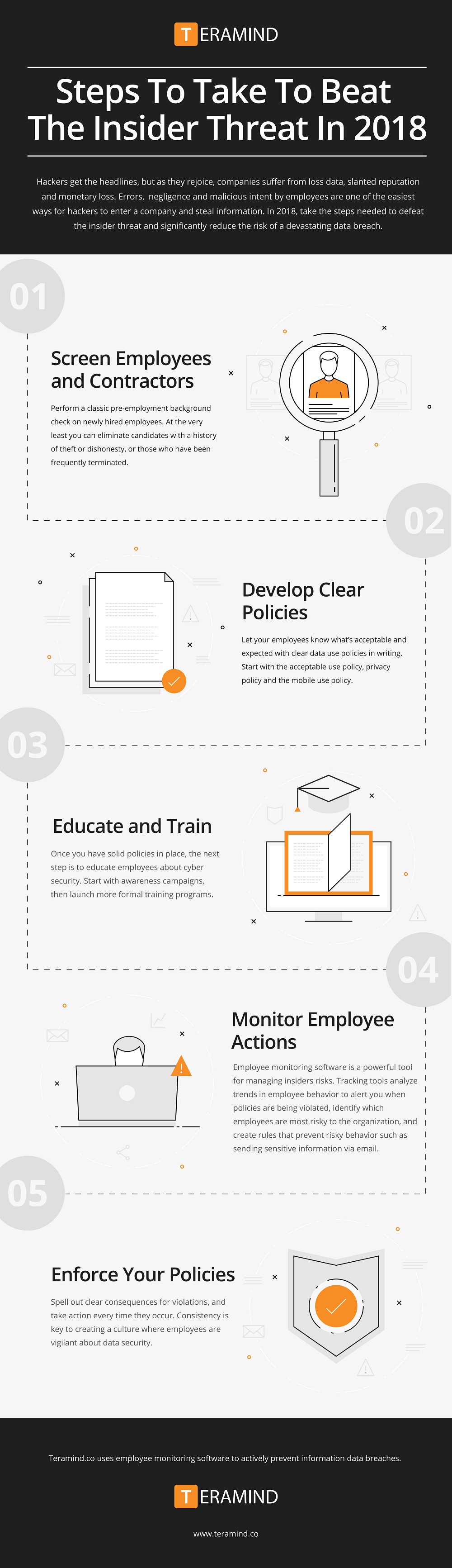
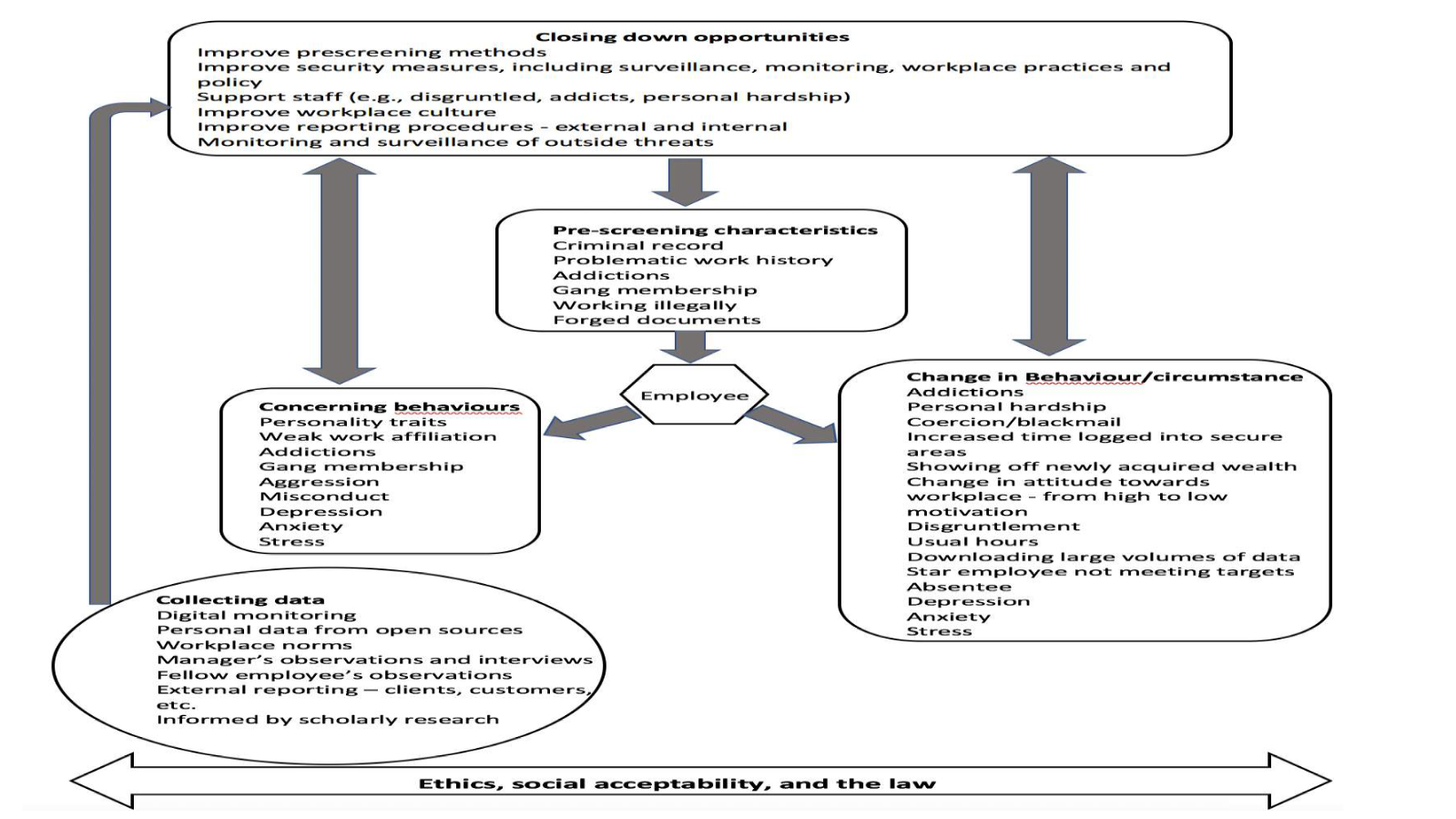
What is an insider threat?
What is an Insider Threat? Insider threat is the potential for an insider to use their authorized access or understanding of an organization to harm that organization.What are 2 types of insider threats?
What are the Types of Insider Threats?
Unintentional Threat. Intentional Threats - The intentional insider is often synonymously referenced as a “malicious insider.” Intentional threats are actions taken to harm an organization for personal benefit or to act on a personal grievance. Other Threats.What are the 3 phases of insider threat?
The key steps to mitigate insider threat are Define, Detect and Identify, Assess, and Manage.
. Threat detection and identification is the process by which persons who might present an insider threat risk due to their observable, concerning behaviors come to the attention of an organization or insider threat team.
|
Insider Threat Detection Study - NATO Cooperative Cyber Defence
Insider threat has to, in particular, be explored as most security frameworks http ://www rand org/content/dam/rand/pubs/reports/2007/R3782 pdf [Accessed 28 |
|
The enemy within: An insider threat management - ManageEngine
3 2 The breadth and scale of insider threats can be enormous www ictsecuritymagazine com/wp-content/uploads/2017-Data-Breach-Investigations- Report pdf |
|
Insider Threat Report: Trends and Analysis - Fortinet
The 2019 Insider Threat Report reveals the latest trends and challenges facing their organizations at risk, which is reactive and incurs valuable manual labor |
|
Insider Threat Mitigation Guide - CISA
content/dam/ey-sites/ey-com/en_gl/topics/assurance/assurance- pdf s/EY- managing-insider-threat pdf 16Department of Homeland Security (n d ) Insider Threat |
|
Insider Threats 101 What You Need to Know - CISA
Organizations of all sizes are vulnerable to an insider threat An insider threat is Retrieved from fbi gov/file-repository/making-prevention-a-reality pdf /view 2 |
|
INSIDER THREAT IN CIVIL AVIATION - IATA
awareness is included in this paper as well as in the IATA Security Management System (SeMS) Manual Objectives for Managing the Insider Threat |
|
The CERT® Guide to Insider Threats - Pearsoncmgcom
The CERT guide to insider threats : how to prevent, detect, and respond to information technology crimes (theft, sabotage, fraud) / Dawn Cappelli, Andrew |
| [PDF] Insider Threat - ENISA - europa.euwww.enisa.europa.eu › publications › at_download › fullReportFrom January 2019 to April 2020. Insider threat. ENISA Threat Landscape ... https ://enterprise.verizon.com/resources/reports/insider-threat-report.pdf');">PDF |
Insider Threat - ENISA - europaeu
From January 2019 to April 2020 Insider threat ENISA Threat Landscape https ://enterprise verizon com/resources/reports/insider-threat-report pdf 2 “Insider |
|
Detection and prediction of insider threats to cyber security - CORE
research questions: 1) what are the research trends in insider threat detection and pdf Accessed 10 Sept 2015 7 Hong J, Kim J, Cho J The trend of the |








![The 2018 Insider Threat Report [Infographic] - Business 2 Community The 2018 Insider Threat Report [Infographic] - Business 2 Community](https://www.ekransystem.com/sites/default/files/insider_Threat_Definition/figure-1.jpg)











![txt] Insider Threat: A Guide to Understanding Detecting and Defend txt] Insider Threat: A Guide to Understanding Detecting and Defend](https://www.dni.gov/files/NCSC/documents/nittf/20181030-NITTF_Framework-FAQs-image.png)