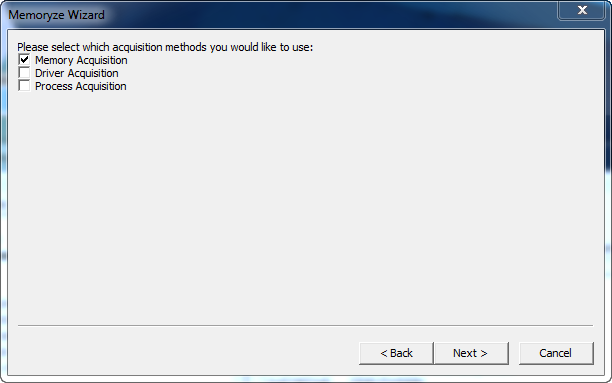
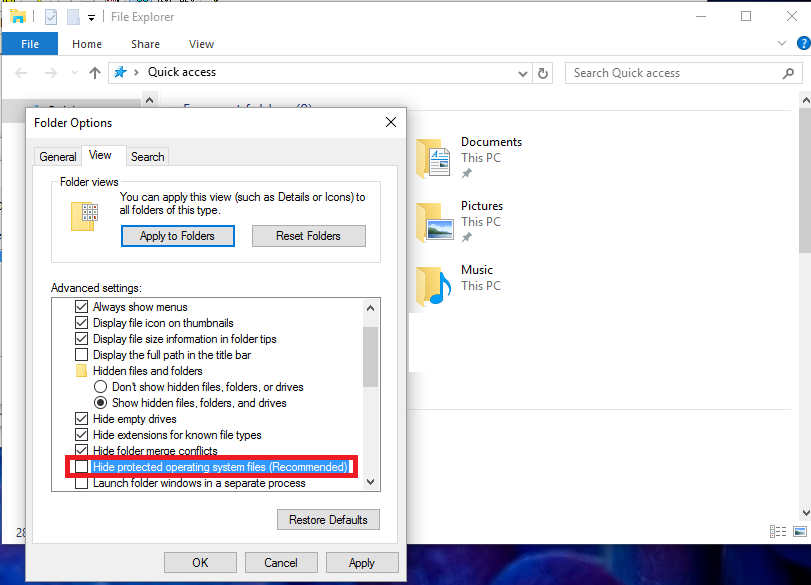
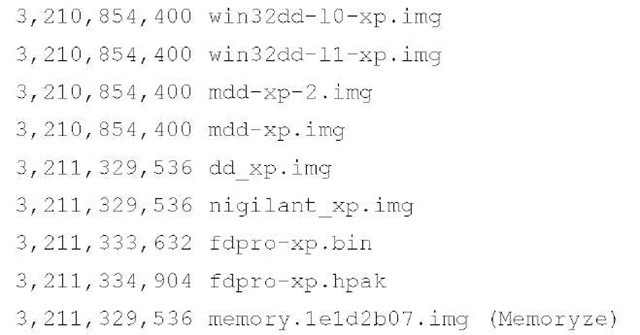
mac memoryze
|
「証拠保全ガイドライン 第9版」
2023/02/20 同社で開発されている Memoryze. という解析ツールの GUI フロントエンドとして使 ... ・Mac/iPhone保全・解析ツール. Digital Collector(旧MacQuisition) ... |
|
Testing Memory Forensics Tools for the Macintosh OS X Operating
2018/03/31 (sumueri.com/software/recon) Mandiant Mac. Memoryze. (www.fireeye.com/ services/ freeware / memoryze. html) |
|
個別調査分析2 サイバーセキュリティ
- Memoryze for Mac: Mac 用の Memoryze。機能は少なくなっている。 - Orochi: Orochi は、フォレンジック・メモリー・ダンプを共同で解析するためのオープンソースの. |
|
Hunting Mac Malware with Memory Forensics
◇ Mac Memoryze (Mandiant). ◇ 10.7+ guests in VMware Fusion. ◇ Fully supported by Apple. Page 11. #RSAC. Previous Efforts before Volatility Support. ◇ |
|
Contents
Mac OS X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 514 · Example Output Mac Memoryze . |
|
A Brief Survey of Memory Analysis Tools
unencrypted information passwords |
|
Comparison of Acquisition Software for Digital Forensics Purposes
This research presents five acquisition software such as FTK Imager Belkasoft. RAM Capturer |
|
Forensisk analys av volatilt minne från operativsystemet OS X
2015/04/23 Tabell 27: Öppnade wordfilen Mandiant Memoryze |
|
ANALYSIS AND DESIGN OF DIGITAL FORENSICS AND INCIDENT
2019/06/27 Don not run MAC times altering programs. • Acquisition should be ... CommandHistory: 0x61e68 Application: Memoryze.exe Flags: Allocated. |
|
Hacking the running Linux kernel
2020/06/02 2.4.10 Memoryze [22] ... • Mac OSX: Macintosh Operating System X. • Mach-O: Mach Object. • MD5 ... |
|
A Brief Survey of Memory Analysis Tools
unencrypted information passwords |
|
Hunting Mac Malware with Memory Forensics
Detect Mac kernel rootkit techniques with memory forensics Mac Memoryze (Mandiant) ... Matthieu Suiche - Mac OS X Physical Memory Analysis [1]. |
|
On the Viability of Memory Forensics in Compromised Environments
May 28 2015 source memory acquisition framework for Mac OS X. In a survey of kernel ... Mandiant Memoryze Destroying the KDBG Owner Tag had no impact on ... |
|
Forensisk analys av volatilt minne från operativsystemet OS X
undersökningsmetoder av det volatila minnet för Mac-datorer med OS X. Tabell 26: Startade processer Mandiant Memoryze |
|
Testing Memory Forensics Tools for the Macintosh OS X Operating
Mar 31 2018 Sumuri. Forensics. RECON. (sumueri.com/software/recon) |
|
State of the Hack
Contact Information: ? https://www.linkedin.com/in/charlescarmakal. ? Free tools: ? Redline. ? IOC Editor / Finder. ? Memoryze / Memoryze for Mac. |
|
MEMORY FORENSIC: ACQUISITION AND ANALYSIS OF MEMORY
It is written in Python and supports Microsoft Windows Mac OS Xand Linux MANDIANT Memoryze |
|
Holmes: A Data Theft Forensic Framework
case [1] Memoryze [2] |
|
Mac OS X Forensics - Joaquin Moreno Garijo
Some investigators prefer to use Volatility whereas others prefer to use Memoryze. 2.3 Malware. During a forensics analyser the auditors might find a specific |
|
Redline User Guide Release 2.0
Analyze memory images from Mandiant Memoryze™. Redline can analyze data with Indicators of This audit returns all the groups present in a Mac OS X host. |
|
Mac RAM Analysis - Champlain College
17 juil 2012 · For this project two different RAM dump tools were used; Mac Memory Reader and Mandiant's Mac Memoryze A MacBook pro was provided to the LCDI |
|
Mac Memoryze - Download
18 jan 2015 · Live memory forensics analysis tool Mac Memoryze is a free OS X utility designed to analyze your Mac's live memory and detect potential errors |
|
Bringing Mac Memory Forensics to the Mainstream
Mac Memoryze (Mandiant) Ma4hieu Suiche -? Mac OS X Physical Memory Analysis [1] Physical-?Memory-?Analysis-?slides pdf |
|
Testing Memory Forensics Tools for the Macintosh OS X Operating
31 mar 2018 · The forensic community has developed tools to acquire physical memory from Apple's Macintosh computers but they have not much been tested This |
|
Kakuseru-Note memorization app on the App Store
1 jan 2023 · You can memorize vocabulary words text photos and Pdf !! Mac: Requires macOS 11 0 or later and a Mac with Apple M1 chip or later |
|
Hunting Mac Malware with Memory Forensics
Showcase Mac memory analysis capabilities ? Detect Mac kernel rootkit techniques with memory forensics Mac Memoryze (Mandiant) Analysis-slides pdf |
|
The Art of Memory Forensics - Detecting Malware and Threats in
%2520Linux |
|
11 bonnes raisons de choisir le Mac en entreprise - Computacenter
Le Mac en entreprise (PDF) Raison n° 1 Une puce surpuissante La puce Apple M1 fait toute la différence avec ces technologies sur mesure sa vitesse de |
|
Mac OS X Forensics - Joaquin Moreno Garijo
4 mar 2015 · tool called Mac Memoryze [61] that can extract and process the memory if we write the word ” pdf ” it shows the last open PDF files in |
|
NAJI Anas - DGSSI
permettra pas de voir l'adresse MAC du serveur au niveau des points 34 ou 5 l'adresse MAC du client ne peut pas être lue MANDIANT Memoryze ? DumpIt |
|
Bringing Mac Memory Forensics to the Mainstream - The Volatility
Discuss the state of Volaylity's Mac support • Show the plugins most Mac Memoryze (Mandiant) Ma4hieu Suiche -‐ Mac OS X Physical Memory Analysis [1] |
|
Mac RAM Analysis - Champlain College
17 juil 2012 · Mandiant – Mac Memoryze 1 2 Field of Research For this project, two different RAM dump tools were used; Mac Memory Reader and |
|
User Guide - FireEye
MANDIANT Memoryze, formerly known as MANDIANT Free Agent, is a memory analysis tool Memoryze can not only acquire the physical memory from a |
|
Traitement des incidents - DGSSI
permettra pas de voir l'adresse MAC du serveur au niveau des points 3,4 ou 5 l' adresse MAC du client ne peut pas être lue MANDIANT Memoryze ▫ DumpIt |
|
New School Forensics - SANS Forensics
Hex editors, string extraction tools, search tools, and file carvers are all useful for extracting data ” -Mac Memory Reader help file Page 8 Mac Memoryze |
|
The Art of Memory Forensics - Zenk - Security
18 fév 2005 · which means you can access them from Windows, Mac OS X, or Linux analysis stations and process them with any tool Mandiant Memoryze: |
|
Mac OS X Forensics - Royal Holloway, University of London
Some investigators prefer to use Volatility whereas others prefer to use Memoryze 2 3 Malware During a forensics analyser, the auditors might find a specific |
|
Redline User Guide - FireEye
Analyze memory images from Mandiant Memoryze™ Redline can Mac hosts collect numerous amounts of log files containing all sorts of information about |







![PDF] Comparison of Acquisition Software for Digital Forensics PDF] Comparison of Acquisition Software for Digital Forensics](https://image.slidesharecdn.com/bheuharuyama20120309eyesonly-130703222755-phpapp01/95/onebyte-modification-for-breaking-memory-forensic-analysis-10-638.jpg?cb\u003d1372890695)








![PDF] Comparison of Acquisition Software for Digital Forensics PDF] Comparison of Acquisition Software for Digital Forensics](https://1.bp.blogspot.com/-4wh-PbX2ui4/V1eCHDRF7MI/AAAAAAAAA0s/5imGlvWIXB8w60gQ1SIwVar1CisFY-pCwCLcB/s1600/Screen%2BShot%2B2016-06-07%2Bat%2B10.24.35%2BPM.png)





![PDF] Robust bootstrapping memory analysis against anti-forensics PDF] Robust bootstrapping memory analysis against anti-forensics](https://image.slidesharecdn.com/bheuharuyama20120309eyesonly-130703222755-phpapp01/95/onebyte-modification-for-breaking-memory-forensic-analysis-35-638.jpg?cb\u003d1372890695)