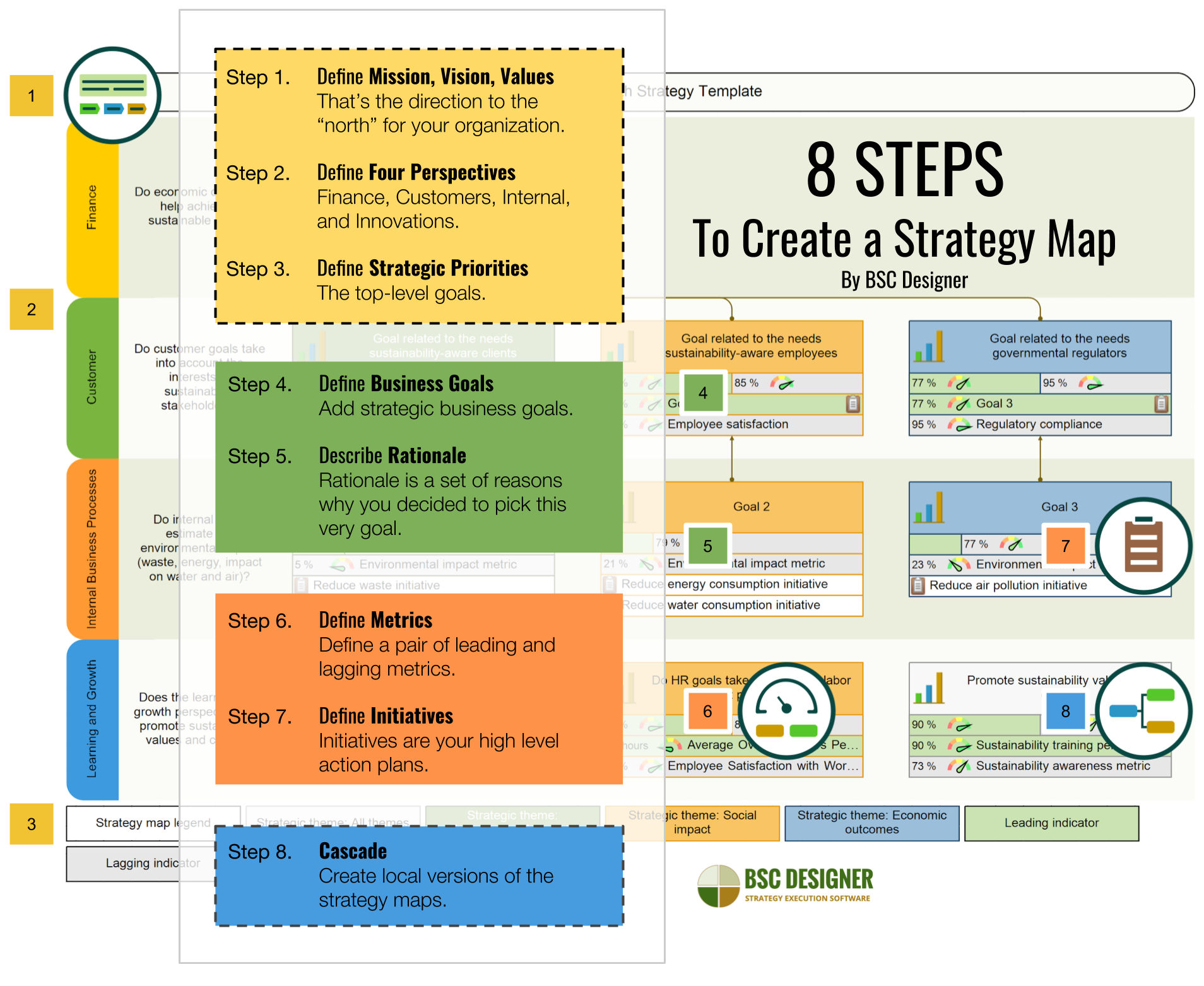
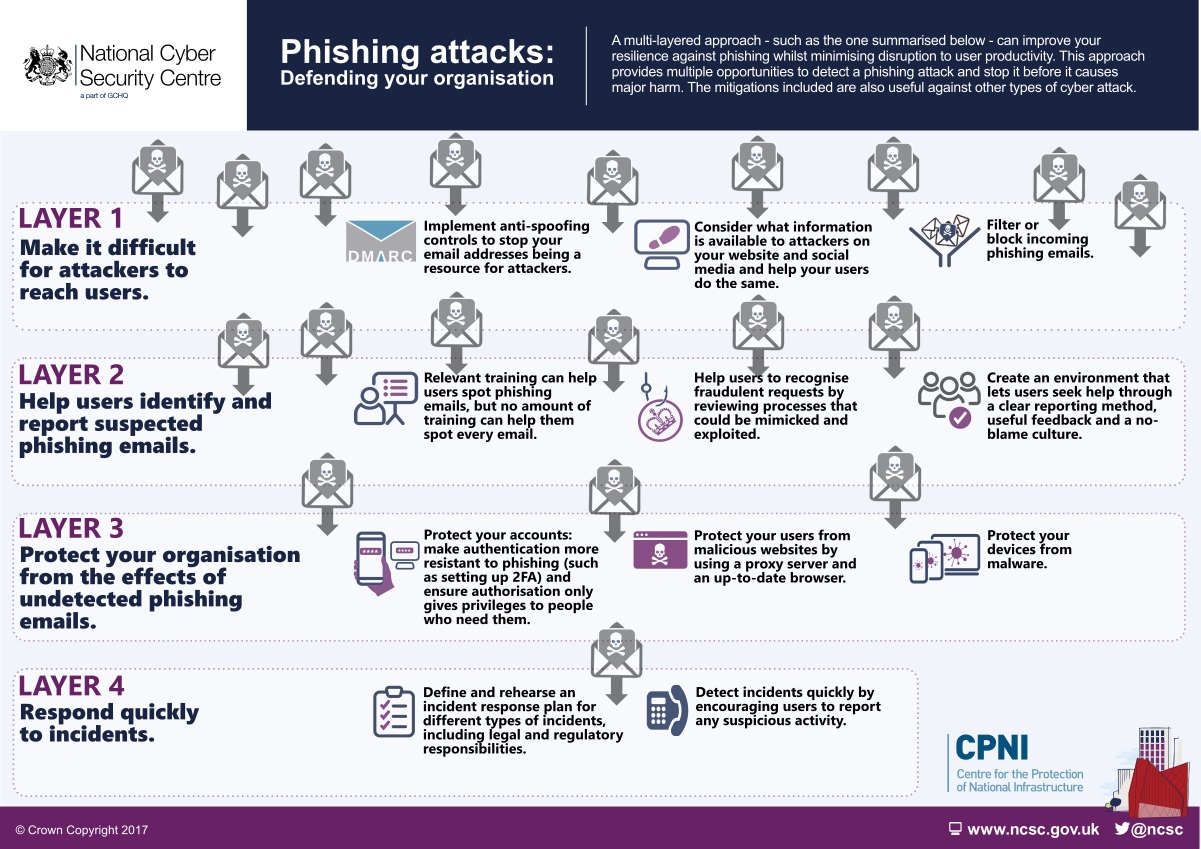
p7 design and implement a security policy for an organisation
|
Designing an effective information security policy for exceptional
The research problem was to investigate how to design effective information security policies for exceptional situations in an organization. Employees need |
|
Computing
18 May 2018 organisational policy. P7 Design and implement a security policy for an organisation. P8 List the main components of an. |
|
Higher Nationals Internal verification of assessment decisions
P7 Design and implement a security policy for an organisation. P8 List the main components of an organisational disaster recovery. |
|
POLICY P7.1.10 ORGANISATIONAL RISK MANAGEMENT
20 Aug 2019 Internal audit; j. Financial management including procurement activities; k. ICT security controls and objectives (including cyber security); ... |
|
Cybersecurity in the EU Common Security and Defence Policy (CSDP)
States and international organisations play a key role in developing norms. The role of the states is prominent also in implementing and enforcing cybernorms. |
|
Higher Nationals Internal verification of assessment decisions
P7 Design and implement a security policy for an organisation. P8 List the main components of an organisational disaster recovery. |
|
Unit 5: Security
P7 Design and implement a security policy for an organisation. P8 List the main components of an organisational disaster recovery plan justifying the reasons |
|
SECURITY
12 Aug 2019 P7 Design and implement a security policy for an organisation. P8 List the main components of an organisational disaster recovery plan. |
|
Publication 1075 - Tax Information Security Guidelines
AU-1: Audit and Accountability Policy and Procedures coordination among organizational entities and compliance to implement all applicable security ... |
|
BTEC HNCD Computing
Pearson BTEC Level 5 Higher National Diploma in Computing (Security) Institution of Engineering and Technology (IET) ... P7 Design and implement a. |
|
NIST Cybersecurity Framework Policy Template Guide
Security Assessment and Authorization Policy Security Awareness and Training Policy ID AM-2 Software platforms and applications within the organization are inventoried Acceptable Use of Information Technology Resource Policy Access Control Policy Account Management/Access Control Standard Identification and Authentication Policy Information |
|
Best Practices for Implementing a Security Awareness Program
Security is one of the most important challenges modern organisations face Security is about protecting organisational assets including personnel data equipment and networks from attack through the use of prevention techniques in the form of vulnerability testing/security policies and detection techniques |
|
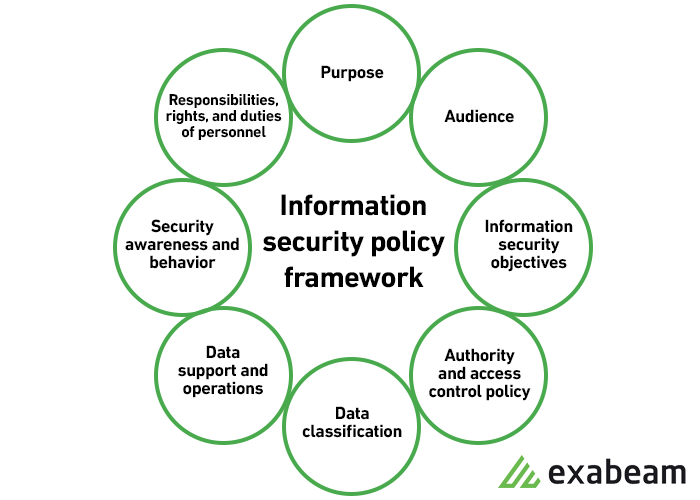
Security Policy Framework - United Nations
A Policy is the basis of institutional consistency in managing security processes or issues and lays down principles for the achievement of one or more goals UNSMS Policies are issued following endorsement of the IASMN and approval by the HLCM They are compiled in the Security Policy Manual (SPM) also known as the “blue book” |
|
Best Practices for Implementing a Security Awareness Program
A robust and properly implemented security awareness program assists the organization with the education monitoring and ongoing maintenance of security awareness within the organization This guidance focuses primarily on the following best practices: |
|
Security Policies - University of Cambridge
Megacorp Inc security policy 1 This policy is approved by Management 2 All sta shall obey this security policy 3 Data shall be available only to those with a eed-to-know" 4 All breaches of this policy shall be reported at once to Security This sort of thing is common but is of little value to the engineer 3 |
What are some examples of information security policies?
- Industry standards or regulations related to background checks, privacy, and information security policies—e.g., FFIEC, SOX, HIPAA, NIST, ISO. Organization information security policy, risk assessment process, third-party service provider management and monitoring policy, and incident response plan Malware infections reduced over time.
How can a security awareness program help meet PCI DSS requirements?
- Ensuring staff is aware of the importance of cardholder data security is important to the success of a security awareness program and will assist in meeting PCI DSS Requirement 12.6. The first step in the development of a formal security awareness program is assembling a security awareness team.
How do you create a security awareness plan?
- Identify compliance or audit standards that your organization must adhere to. Identify security awareness requirements for those standards. Identify organizational goals, risks, and security policy. Identify stakeholders and get their support. Create a baseline of the organization’s security awareness.
What is the PCI Security Standards Council?
- The PCI Security Standards Council is an open global forum that is responsible for the development, management, education, and awareness of the PCI Data Security Standard (PCI DSS) and other standards that increase payment data security.
|
Implementation of information security policies in public organizations:
The security measures that will be implemented affect and are affected by a number of processes in the business The purpose of designing security processes is |
|
Unit 5: Security
Security is about protecting organisational assets, including personnel, data, equipment and implementing contingency plans and devising security policies and procedures This unit security Among the topics included in this unit are Network Security design and operational P7 Design and implement a security |
|
Design and Implement database Security Policies in an - TechWell
Design of Database Security Policy in Enterprise Systems Authored: Simplify the security policy implementation process across organization for various |
|
Network Security: Policies and Guidelines for Effective Network
procedures to implement and enforce a security plan that includes the general organizational policies as well as any additional policies necessary to maintain |
|
POLICY P7110 ORGANISATIONAL RISK MANAGEMENT
20 août 2019 · organisational arrangements for designing, implementing, monitoring, reviewing and Policy P5 1 3 Information Security Management |
|
A Model for Monitoring End-User Security Policy Compliance
1 juil 2017 · organisations have implemented information security policies to manage It is crucial that organizations design effective information security awareness P7- Saud Al-otaibi is an IT professional with 15+ years in the field of |
|
Quality Assurance Policy - IIA Australia
Policy Reference No P7: Approval Authority: Board of Directors and Education Committee Current Version: May 2017 - It includes course design, staff development and the collection and use of feedback from candidates that strategies are implemented to improve organisational performance Privacy Security Policy |
|
Interpreting the management of information systems security - CORE
by reviewing the analysis, design and management of computer based information The advances in new technology and the emergent organisational forms introduce formal system to the local conditions, it tends to impose inappropriate rules and May p7 Mintzberg, H (1983a) Structures in fives: designing effective |
![PDF] Six Design Theories for IS Security Policies and Guidelines PDF] Six Design Theories for IS Security Policies and Guidelines](https://d3i71xaburhd42.cloudfront.net/ba10336227f13ffbb856cc23decffda1804ed13b/3-Figure1-1.png)
![PDF] Six Design Theories for IS Security Policies and Guidelines PDF] Six Design Theories for IS Security Policies and Guidelines](https://i1.rgstatic.net/publication/303061017_Information_Security_Policy_Development_and_Implementation_A_content_analysis_approach/links/5820468008ae12715afbaefd/largepreview.png)


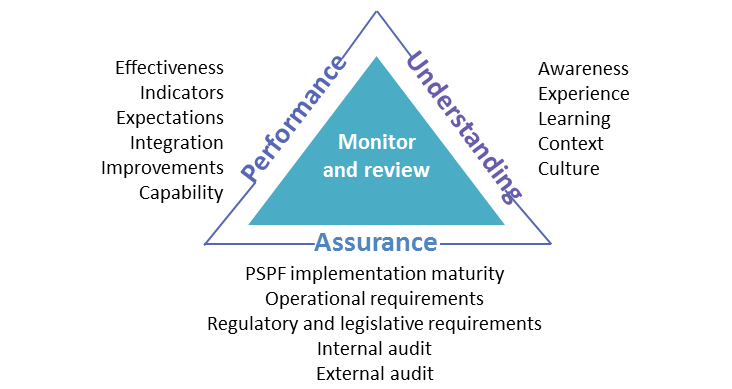
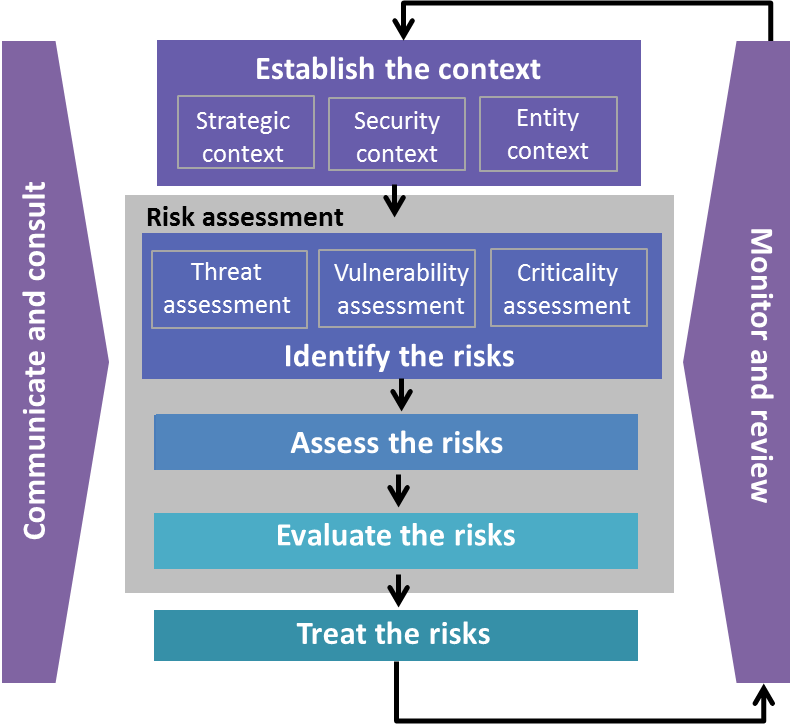



![42 Information Security Policy Templates [Cyber Security] ᐅ 42 Information Security Policy Templates [Cyber Security] ᐅ](https://www.adp.com/-/media/usa-2015/about-adp/data-security/overview/adp-data-security-protection-new.svg?h\u003d380\u0026w\u003d460\u0026la\u003den\u0026hash\u003dAE1FA7E4760226FC23400EA024DB5F0AAAAE2065)

![Evaluation of the WFP Gender Policy (2015-2020) [EN/AR/FR] - World Evaluation of the WFP Gender Policy (2015-2020) [EN/AR/FR] - World](https://www.solarwindsmsp.com/sites/solarwindsmsp/files/blog/2019/10/1910_BP_Types_Network_Security_720x356_v1_BT.png)





![42 Information Security Policy Templates [Cyber Security] ᐅ 42 Information Security Policy Templates [Cyber Security] ᐅ](https://d3i71xaburhd42.cloudfront.net/ba10336227f13ffbb856cc23decffda1804ed13b/13-Table4-1.png)
![PDF] Six Design Theories for IS Security Policies and Guidelines PDF] Six Design Theories for IS Security Policies and Guidelines](https://upload.wikimedia.org/wikipedia/en/3/31/Process_data_model_security_management.jpg)