penetration testing framework pdf
| A Framework for the Regulatory use of Penetration Testing in the |
|
Testing Guide
Security Tests Integrated in Development and Testing Workflows. Security Test Data Analysis and Reporting. 7 - 21. 2. The OWASP Testing Framework. Overview. |
|
Penetration Testing Frameworks and methodologies: A comparison
In addition two frameworks OWASP's Testing Guide and. Information System Security Assessment Framework (ISSAF) |
|
Technical guide to information security testing and assessment
http://csrc.nist.gov/drivers/documents/FISMA-final.pdf. Open Source Security Testing Methodology Manual (OSSTMM).4 Because there are numerous reasons. |
|
Information Systems Security Assessment Framework (ISSAF) draft 0.2
9 jan. 2019 2005 Open Information Systems Security Group. STEP ONE: NETWORK AUTHENTICATION CREDENTIALS GATHERING AS AN OUTSIDER PENETRATION TESTER. |
|
PENETRATION TESTING
Web Application Penetration Test. These tests focus on the various vulnerabilities found in web application components; including frameworks server software |
|
OSSTMM 3 – The Open Source Security Testing Methodology Manual
14 déc. 2010 This is a methodology to test the operational security of physical locations human interactions |
|
Buyers Guide Cyber Security Penetration Testing Services Framework
This Framework has been set up in order to streamline the process for police forces and other agencies of procuring Pen Test suppliers for their. |
|
TIBER-EU Framework - Services Procurement Guidelines
TIBER-EU facilitates RT testing for entities which are active in more than one Management System (ISMS) with a bespoke security control framework and. |
|
Joint Advice of the European Supervisory Authorities
10 avr. 2019 cyber resilience testing framework may vary both between and within sectors depending on i) the cyber security maturity level of the market ... |
|
Penetration Testing Guidance - PCI Security Standards Council
Penetration Testing Components: Understanding of the different components that make up a penetration test and how this differs from a vulnerability scan including scope application and network-layer testing segmentation checks and social engineering Qualifications of a Penetration Tester: |
|
Penetration Testing Guidance - PCI Security Standards
The Penetration Testing Execution Standard Documentation Release 1 1 As the standard does not provide any technical guidelines as far as how to execute an actual pentest we have also created a technical guide to accompany the standard itself The technical gude can be reached via the link below: • PTES Technical Guidelines |
|
OWASP Web Application Penetration Checklist - OWASP Foundation
The penetration test starts by gathering all possible information available regarding the infrastructure and applications involved This stage is paramount as without a solid understanding of the underlying technology involved sections may be missed during the testing phase The test should follow all the different phases described below |
|
IT Security Procedural Guide: Conducting Penetration Test
repeatable framework for conducting penetration test activities 1 2 Scope The requirements outlined within this guide apply to any internal or external organizations who are involved in penetration testing of GSA information systems and data 1 3 Policy Penetration testing is addressed in CIO 2100 1 as stated in the following paragraphs: |
|
The OWASP Testing Project
penetration testing to testing integrated in the software development life cycle Many industry experts and those responsible for software security at some of the largest companies in the world are validating the Testing Framework presented as OWASP Testing Parts 1 and 2 |
|
Le d-ib td-hu va-top mxw-100p>Penetration Testing - Penetration Testing Services
Penetration Testing Components: Understanding of the different components that make up a penetration test and how this differs from a vulnerability scan including scope application and network- layer testing segmentation checks and social engineering |
What is the scope of a penetration test?
- When access to the CDE is obtained as a result of the testing, the scope of the penetration test may allow the tester to continue exploring inside the network and further the attack against other systems within the CDE, and may also include testing any data-exfiltration prevention (data-loss prevention) controls that are in place.
What should be included in a penetration test report?
- 5.1 Identified Vulnerability Reporting Penetration test reports should include a discussion of the steps, vectors, and exploited vulnerabilities that lead to penetration during testing for which remediation and retesting are required.
Is penetration testing a science?
- Penetration testing will never be an exact science where a complete list of all possible issues that should be tested can de defined. Indeed penetration is only an appropriate technique to test the security of web applications under certain circumstances.
How to ensure a robust approach to penetration testing?
- Therefore, a robust approach to penetration testing is recommended to satisfy this requirement by actively attempting to identify routes and paths from networks outside the CDE into the CDE. All segmentation methods need to be specifically tested.
|
Penetration testing - ASIFMA
A Framework for the Regulatory use of Penetration Testing in org/ uploadedFiles/News/GFMA_in_the_News/2017/GFMA-Penetration-Testing- Principles pdf |
|
Penetration Testing Framework - InfoSecWriterscom
Penetration Testing Framework v0 21 Authors: Penetration Tests Reason for test from pentest co uk Manual sql input of previously reported vulnerabilities |
|
A guide for running an effective Penetration Testing - CREST
Some of the principle sources of material reviewed included: • The Open Source Security Testing Methodology Manual (OSSTMM) from The Institute for Security |
|
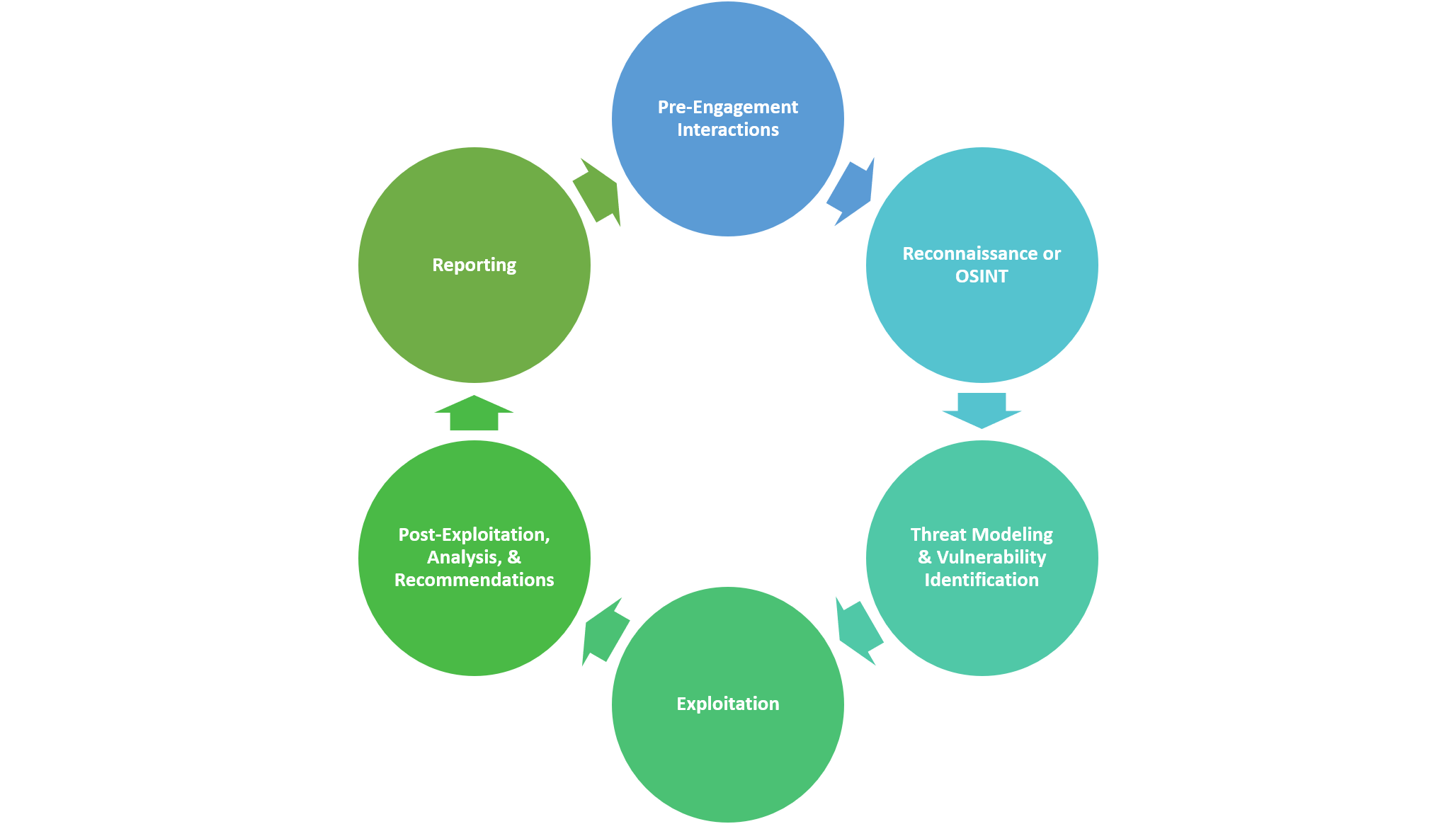
Overview of Penetration Testing Methodologies and Tools
Overview • What is penetration testing? • Vulnerability Assessment vs Pentesting • Pentesting Methodology • Pre-engagement Phase • Engagement Phase |
|
OWASP Testing Guide - OWASP Foundation
Security Tests Integrated in Development and Testing Workflows Security Test Data Fingerprint Web Application Framework (OTG-INFO-008) Fingerprint Web Application (OTG-INFO-009) Map Application Architecture (OTG-INFO-010) |
|
Web Application Penetration Testing Pdf - Infosec Resources
testing on the BestBank application Penetration testing methodology explained here lists out below phases: ▫ Information Gathering ▫ Vulnerability Testing |
|
PENETRATION TESTING - Core Sentinel
Penetration testing will reveal vulnerabilities that otherwise would not be discovered Open Source Security Testing Methodology Manual (“OSSTMM”) - A |
|
The Finest Penetration Testing Framework for Software - Black Hat
The Finest Penetration Testing Framework But, manually testing each attack is time consuming and annoying job Attack Vectors in SDN architecture |
|
Penetration Testing Automation System - UPCommons
The framework is used through the command line and the authors claim it has a better performance than the rest of current security frameworks Figure 2 3: PDF |
|
Study A Penetration Testing Model - BSI
6 1 Requirements for a Penetration Testing Methodology Manual verification of the remaining vulnerabilities, such as tests of buffer overflow exploits, etc |

![PDF] LIBRARY CISOs Guide to Penetration Testing A Framework to Pl PDF] LIBRARY CISOs Guide to Penetration Testing A Framework to Pl](https://imgv2-2-f.scribdassets.com/img/document/336195896/149x198/0c97e20ce2/1484071409?v\u003d1)
![PDF] LIBRARY HandsOn Web Penetration Testing with Metasploit Usin PDF] LIBRARY HandsOn Web Penetration Testing with Metasploit Usin](https://0.academia-photos.com/attachment_thumbnails/37184312/mini_magick20190304-7698-fjgcm9.png?1551747363)


![PDF] DOWNLOAD FREE Metasploit Penetration Testing Cookbook - Third Ed PDF] DOWNLOAD FREE Metasploit Penetration Testing Cookbook - Third Ed](https://blog.eccouncil.org/wp-content/uploads/2020/03/ECC-Infographic-july-03-2.jpg)