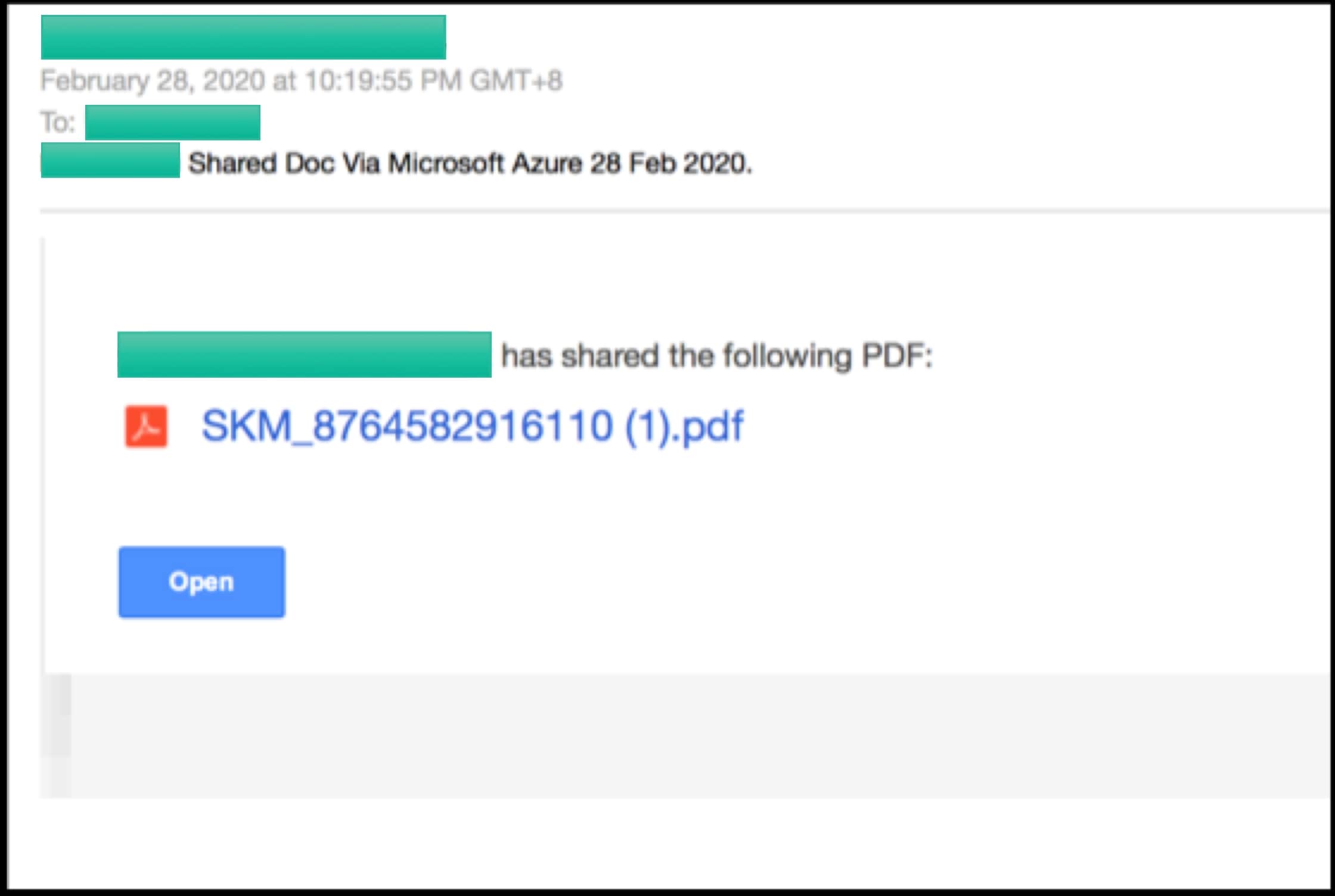
phishing pdf
|
Lhameçonnage
L'hameçonnage (phishing) est une technique frauduleuse qui consiste à voler des données https://www.imperva.com/docs/Imperva-HII-phishing-made-easy.pdf. |
|
PHISHING.pdf
PHISHING (hameçonnage - filouterie) : C'est une technique frauduleuse permettant de voler des L'attaque nommée Phishing est organisée à grande échelle. |
|
Phishing
Lors d'une attaque par phishing les criminels ont recours à de faux courriels ou à des sites Internet piratés pour tenter de subtiliser des. |
|
Phishing and Spoofed Email Investigations & Incident Response
22 oct. 2021 Why Phishing Emails are Dangerous? ... Attackers can re-use the hacked email for a new phishing attack ... malicious pdf file in a. |
|
Understanding phishing techniques
Phishing is a type of social engineering attack often used to steal user data /dam/Deloitte/uk/Documents/risk/deloitte-uk-risk-gdpr-six-months-on.pdf. |
|
Homoglyph a avancé des attaques par phishing - Cisco
Ce document décrit l'utilisation des caractères de homoglyph dans des attaques par phishing avancées et comment se rendre compte de ces derniers ? à l'aide |
|
ENISA ETL2020 - Phishing
spear phishing are major attack vectors of other threats such as https://www.imperva.com/docs/Imperva-HII-phishing-made-easy.pdf. |
|
Spear Phishing: Top Threats and Trends
29 mai 2021 Almost all of the attacks that fall into this category will include a malicious URL. Although phishing emails are nothing new hackers have ... |
|
Phishing.pdf
15 déc. 2013 Phishing is a psychological attack used by cyber ... spear phishing the cyber attackers research their ... PackageTracking.pdf (91 kb). |
|
Phishing - National Institute of Standards and Technology
Feb 17 2022 · A phishing attack is an attempt by criminals to trick you into sharing information or taking an action that gives them access to your accounts your computer or even your network It’s no coincidence the name of these kinds of attacks sounds like fishing The attack will lure you in using some kind of bait to fool you into making a mistake |
|
CYBERSECURITY AWARENESS MONTH 2021: DO YOUR PART &# - CISA
Phishing attacks use email or malicious websites to infect your machine with malware and viruses to collect personal and financial information Cybercriminals attempt to lure users to click on a link or open an attachment that infects their computers creating vulnerabilities for criminals to use to attack |
|
Phishing (General Security Postcard) - CISA
Jun 24 2021 · Phishing is a form of social engineering that uses email or malicious websites to solicit personal information or to get you to download malicious software by posing as a trustworthy entity Types of Phishing Spearphishing: Phishing targeted at an individual by including keyinformation about them |
|
What You Need to Know About Social Engineering & Phishing
Phishing is a form of social engineering in which an attacker masquerades as a trustworthy entity and tries to persuade scare or threaten the recipient to take a specific action or reveal personal information that leads to a security compromise |
|
Understanding phishing techniques - Deloitte US
Phishing is one of the oldest types of cyberattacks dating back to the 1990s Despite having been around for decades it is still one of the most widespread and damaging cyberattacks Two key consequences of phishing are: Financial loss Data loss and legal lawsuits |
What is phishing and phishing?
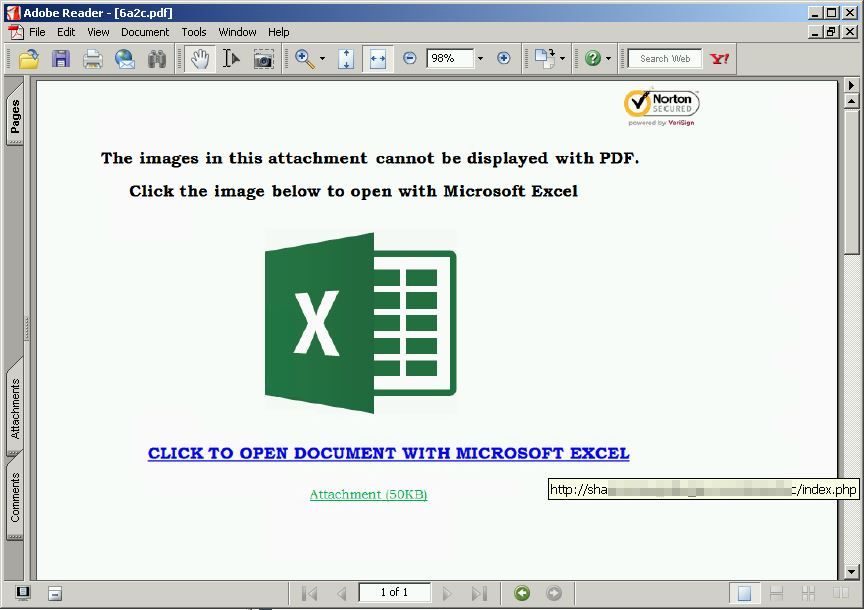
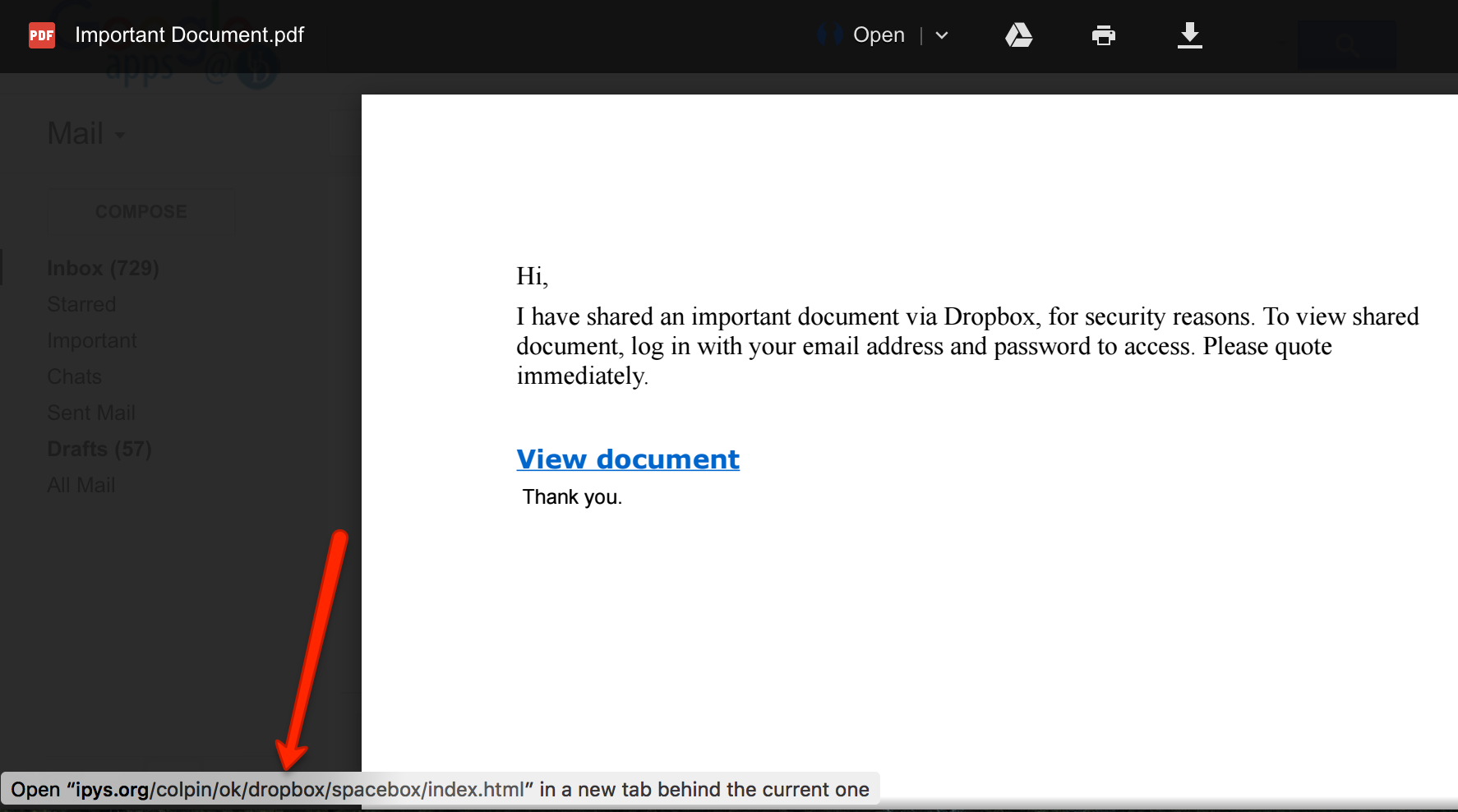
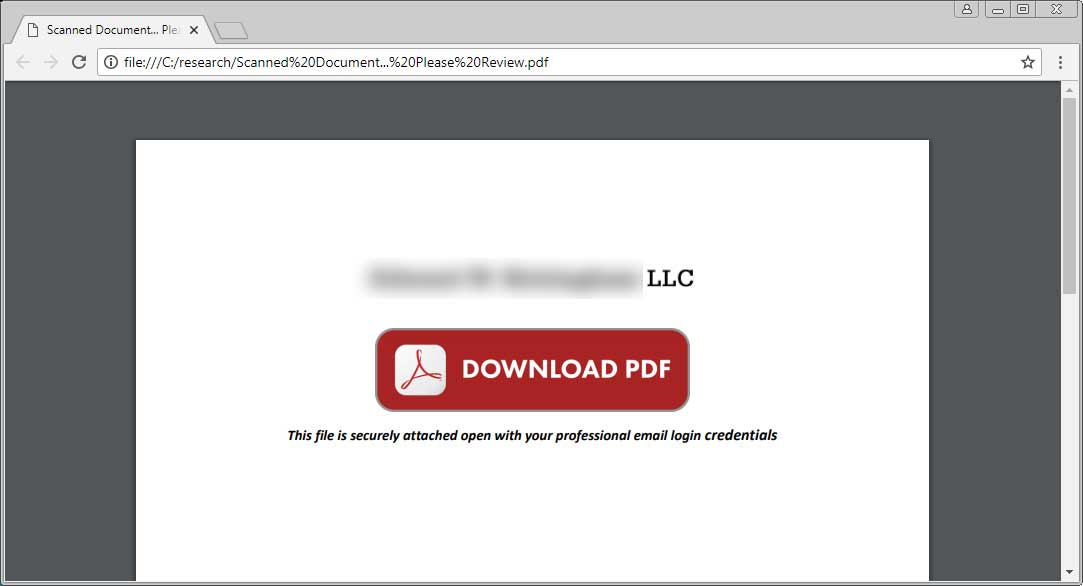
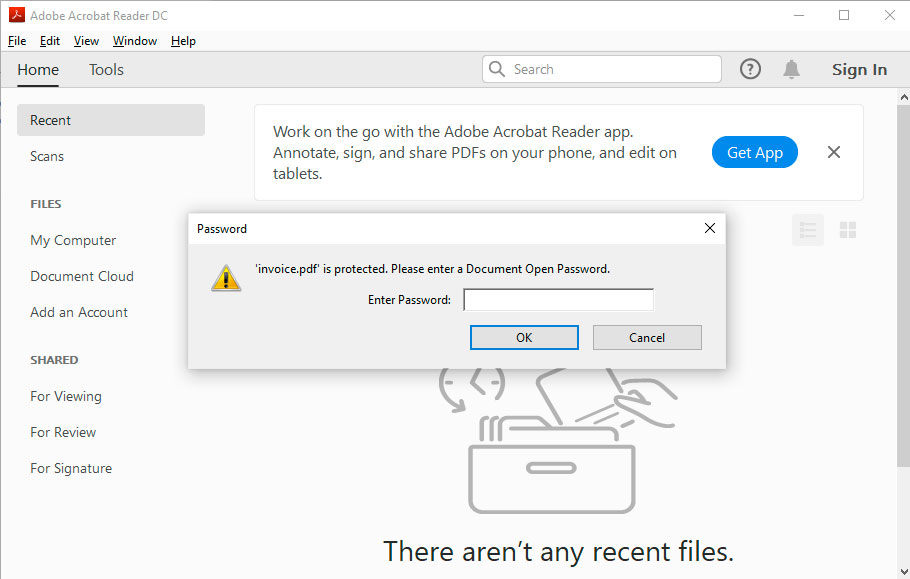
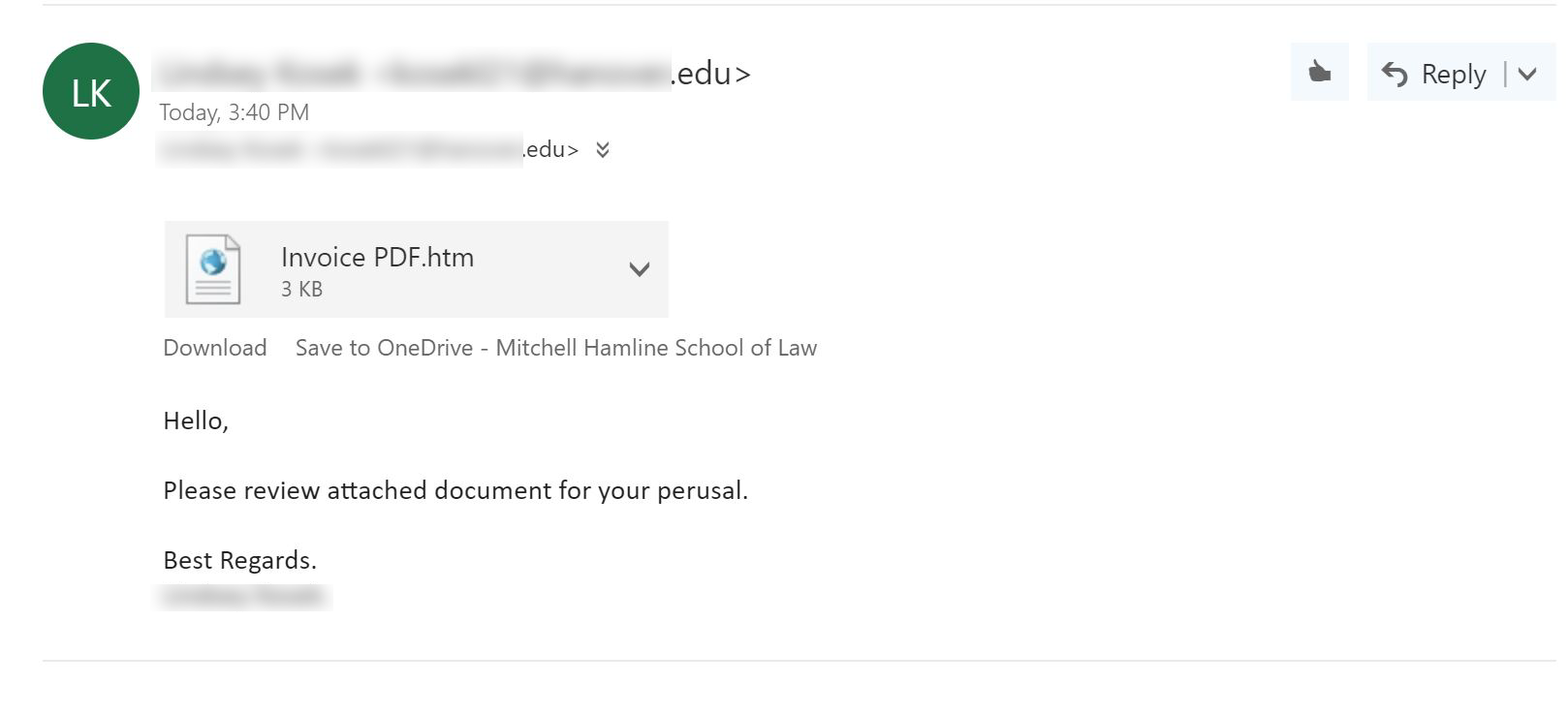
- Phishing is by far the most common form of social engineering attack and is carried out by email. A phishing email aims to trick the target into revealing sensitive information or taking an action that then compromises security.
How common is PDF phishing?
- Over 5 million cases of phishing with PDF were analyzed for 2020 alone and the increase in the incidence compared to the total number of documents sent rose by 1160%. In particular: in 2019 the total number of files analyzed was 4.5 billion, of which about 411 thousand were found to be malware (0.009%).
Are your anti-phishing tips valid for phishing emails?
- The Anti-Phishing Working Group released a report that shows the number of phishing attacks increased by 46 per cent from Q4 in 2017 to Q1 2018. Phishing is a specific form of social engineering, so the prevention tips are valid for phishing emails.
What is SMS phishing?
- This is also known as ‘smishing’. This term was made up by combining SMS + ‘phishing’. In other words, it is ‘phishing’ – where fraudsters send you fake emails hoping to defraud you – but using text messages instead of emails.
|
Phishing - CORE
Mécanismes de Social Engineering (phishing) : étude technique et économique DEUSS Kelvin i Déclaration Ce travail de Bachelor est réalisé dans le cadre |
|
Le Phishing - Zenk - Security
Le terme anglais phishing est issu de l'an- glais fishing (pêche) écrit avec un ph, comme c'est souvent le cas dans le jargon des pirates informatiques |
|
Phishing (hameçonnage ou filoutage) - Economiegouvfr
L'hameçonnage (phishing en anglais) est une technique frauduleuse destinée à leurrer l'internaute pour l'inciter à communiquer des données personnelles |
|
Phishing - Les services de lÉtat dans la Vienne
Explications : L'attaque nommée Phishing est organisée à grande échelle En effet la technique déployée est réalisée à l'aide de courriels envoyés |
|
LE PHISHING
Sé cu rité du Système d'I nfo rm atio n Février 2015 Les risques de l'internet LE PHISHING SÉCURITÉ INFORMATIQUE DE LA MSA |
|
Le phishing par mobile - Lookout
Les appareils mobiles constituent pour les criminels auteurs d'attaques de phishing un nouvel angle d'attaque rentable En effet, les attaquants parviennent à |
|
Understanding phishing techniques - Deloitte
Phishing is a type of social engineering attack often used to steal user data, including /dam/Deloitte/uk/Documents/risk/deloitte-uk-risk-gdpr-six-months-on pdf |
|
Apprendre à reconnaître le phishing - CLCV
Une imitation soignée Un mail de phishing est envoyé par un pirate informatique , il imite un message qu'aurait pu envoyer un interlocuteur avec lequel on a l' |
| [PDF] Phishing Attacks Survey - MDPIwww.mdpi.com › pdf30 sept. 2020 · Abstract: Phishing attacks, which have existed for several decades and ... - Security-Threat-Report-2018.pdf');">PDF |
Phishing Attacks Survey - MDPI
30 sept 2020 · Abstract: Phishing attacks, which have existed for several decades and - Security-Threat-Report-2018 pdf (accessed on 15 December 2019) |
|
LES DANGERS DU PHISHING - Kaspersky
Dans une attaque de phishing, les cybercriminels créent de fausses adresses e- mail et des imitations de sites Web (semblables à des ressources populaires sur |