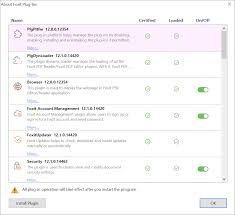
 Foxit PDF Reader 12.1_Manual
Foxit PDF Reader 12.1_Manual
Foxit's website to download the latest version of Foxit PDF Reader for free. ... For Windows 10 click Start > Foxit PDF Reader folder > Uninstall Foxit PDF ...
 Foxit PDF Editor Quick Guide
Foxit PDF Editor Quick Guide
Windows 11 10
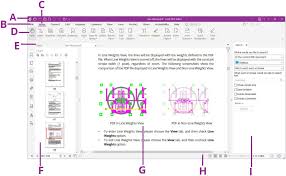 Foxit PDF Editor User Manual 11.2
Foxit PDF Editor User Manual 11.2
This software is provided "as is" without express or implied warranty and with no claim as to its suitability for any purpose. Page 3. Foxit PDF Editor.
 Stow MA
Stow MA
Use the table below to find the email address of your cell phone. For example if your cell phone carrier is AT&T your email address is
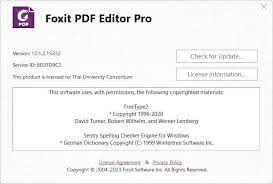 การติดตั้งและ Activate โปรแกรม Foxit PDF Editor Pro 12
การติดตั้งและ Activate โปรแกรม Foxit PDF Editor Pro 12
สามารกรอก e-mail NU. แล้วคลิกที่ช่อง Password. หรือ คลิก Logo. Microsoft ก็ได้. Page 6. จัดทำโดย กองบริการเทคโนโลยีสารสนเทศและ
 Developing Plug-ins for Foxit Reader/PhantomPDF
Developing Plug-ins for Foxit Reader/PhantomPDF
Display a PDF document in an external window using the “Document” sample plugin. Page 32. Foxit PhantomPDF Plug-in SDK. Developing Plugins. 32. Event
 Foxit Reader Deployment and Configuration
Foxit Reader Deployment and Configuration
•. Windows 7 (32-bit & 64-bit). •. Windows 8 Full Version. •. Windows 10. •. Microsoft Office® 2007 or later version (required for some PDF creation features).
 Town of Wareham
Town of Wareham
The following fee schedule has been adopted by the Wareham Conservation Commission under the Wareham Wetland Protective By-Law Division VI as a fee
 Foxit PhantomPDF Editor Helps you to Manage Better PDF Documents
Foxit PhantomPDF Editor Helps you to Manage Better PDF Documents
• For personal PC please go to here to download the installation package After installation
 Foxit PhantomPDF Deployment and Configuration.pdf
Foxit PhantomPDF Deployment and Configuration.pdf
Windows 10. • Microsoft Office® 2007 or later version (required for some Go to Foxit Knowledge Base to download the corresponding version of XML Editor based.
 Foxit MobilePDF Crack Free Download [Win/Mac]
Foxit MobilePDF Crack Free Download [Win/Mac]
NetElement supports PDF files Internet Explorer for Android and other smart devices. It provides a simple and comfortable user interface
 Foxit advanced pdf editor 3.10 key
Foxit advanced pdf editor 3.10 key
System Requirements: Before starting Foxit PDF Editor Crack Free Download [OS]: Windows XP / Vista / 7/8 / 8.1 / 10 [RAM]: 512 MB of RAM required.
 Foxit advanced pdf editor 3.1 serial key
Foxit advanced pdf editor 3.1 serial key
Foxit Advanced PDF Editor free download merges and splits text. have shared all the information about the Foxit Pdf Editor Crack for PC that you needed.
 A Complete Guide to Editing PDFs
A Complete Guide to Editing PDFs
There are dozens of tools that allow you to edit a PDF on Windows; In additional to Acrobat Reader Foxit Reader is a free and popular PDF editing tool.
 Adobe acrobat xi software download for windows 10
Adobe acrobat xi software download for windows 10
Otherwise take a look around for some faster programs like Foxit's free PDF reader.Adobe Reader XI is software which can read PDF files.
 How to add tick mark in foxit reader
How to add tick mark in foxit reader
25 Jun 2014 Foxit Phantom PDF Business 10 Software For Windows quantity . ... Foxit PhantomPDF Business v11.0.0.49893 + Crack Download : .
 Foxit phantompdf 7.3.4.311 activation key
Foxit phantompdf 7.3.4.311 activation key
You can also create PDF files from Microsoft Visio using Foxit PhantomPDF Download from nitroflare.com Foxit Phantom Crack Windows Key > drivers.
 Remote Access VPN Administration Guide R80.10
Remote Access VPN Administration Guide R80.10
6 Mar 2018 To search for text in all the R80.10 PDF documents download and extract the ... Use Shift-Control-F in Adobe Reader or Foxit reader.
 Download lagu moonlight xxtenations mp3
Download lagu moonlight xxtenations mp3
PC or Computer with operating systems such as Windows 7 8
 Foxit PDF IFilter 3.1.1 User Manual
Foxit PDF IFilter 3.1.1 User Manual
Chapter 4 - Foxit PDF IFilter for Microsoft SQL Server . which You fail to pay Foxit the invoice within ten (10) days after the prior.
 Download Foxit PDF Editor Pro 121115289 Free Full Activated
Download Foxit PDF Editor Pro 121115289 Free Full Activated
Free download Foxit PDF Editor Pro 12 1 1 15289 full version standalone offline installer for Windows PC Foxit PDF Editor Pro Overview
 Foxit Advanced PDF Editor 120212465 Download For Windows PC
Foxit Advanced PDF Editor 120212465 Download For Windows PC
Download Foxit Advanced PDF Editor latest full version w/o crack for Windows 10 Windows 7 Windows Vista Windows XP PC This is an offline installer
 Téléchargement gratuit de PDF Reader & PDF Viewer Foxit Software
Téléchargement gratuit de PDF Reader & PDF Viewer Foxit Software
Foxit PDF Reader pour Windows Mac et davantage Une alternative de lecteur de PDF à Adobe Reader The best PDF reader free download
 Foxit PDF Editor Pro v112253575 Full version - 4DOWNLOAD
Foxit PDF Editor Pro v112253575 Full version - 4DOWNLOAD
5 oct 2022 · It can convert PDF files to Microsoft Word documents Excel and other popular document formats The software also features multiple language
 Télécharger Foxit PDF Editor Pro 121215332 Multilingual
Télécharger Foxit PDF Editor Pro 121215332 Multilingual
Évaluer: 1 2 3 4 5 4?37 Voted · Système opérateur: Windows · Classer: · Mise à jour: April 13 2023 · Posté par: Foxit Corporation · Taille: 837 MB · Télécharger:
 Foxit PDF Editor Download (2023 Latest) - FileHorse
Foxit PDF Editor Download (2023 Latest) - FileHorse
19 avr 2023 · Download Foxit PDF Editor for Windows PC from FileHorse 100 Safe and Secure ? Free Download (32-bit/64-bit) Latest Version 2023
 Download Foxit PDF Editor Pro 12 Full Patch Keygen - CahDroid
Download Foxit PDF Editor Pro 12 Full Patch Keygen - CahDroid
4 mar 2023 · Free Download Foxit PDF Editor Pro 12 Full Version Offline Installer - PDFs Operating System Windows 7/8/10/11Processor Pentium IV or
 Foxit Advanced PDF Editor v305 Free Download
Foxit Advanced PDF Editor v305 Free Download
Windows 7 (32-bit 64-bit) · Windows 8 x Full Version · Windows 10 · Microsoft Office® 2007 or later version (required for some PDF creation features) · Verified
6 March 2018
Administration Guide
REMOTE ACCESS VPN
R80.10
Classification: [Protected]
© 2018 Check Point Software Technologies Ltd.
All rights reserved. This product and related documentation are protected by copyright and distributed under licensing restricting their use, copying, distribution, and decompilation. No part of this product or related documentation may be reproduced in any form or by any means without prior written authorization of Check Point. While every precaution has been taken in the preparation of this book, Check Point assumes no responsibility for errors or omissions. This publication and features described herein are subject to change without notice.RESTRICTED RIGHTS LEGEND:
Use, duplication, or disclosure by the government is subject to re strictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS252.227
-7013 and FAR 52.227-19.TRADEMARKS:
Refer to the
Copyright page http://www.checkpoint.com/copyright.html for a list of our trademarks. Refer to the Third Party copyright notices http://www.checkpoint.com/3rd_party_copyright.html for a list of relevant copyrights and third-party licenses.Important Information
Latest Software
We recommend that you install the most recent software release to stay up-to-date with the latest functional improvements, stability fixes, security enhancements and protection against new and evolving attacks.Check Point R80.10
For more about this release, see the R80.10
home pageLatest Version of this Document
Download the latest version of this document
To learn more, visit the Check Point Support Center http://supportcenter.checkpoint.com.Feedback
Check Point is engaged in a continuous effort to improve its documentation.Please help us by sending your comments
mailto:cp_techpub_feedback@checkpoint.com?subject=Feedback on Remote AccessVPN R80.10 Administration Guide.
Searching in Multiple PDFs
To search for text in all the R80.10 PDF documents, download and extract the complete R80.10 documentation package Use Shift-Control-F in Adobe Reader or Foxit reader.Revision History
Date Description
6 Mar 2018 Added list of allowed logical operators for SCV RegMonitor expressions ("SCV Checks" on page 86)
Deleted obsolete global SCV parameters
(enable_status_notifications, status_notifications_timeout, scv_policy_timeout_hours, enforce_ip_forwarding, block_scv_client_connections Addition of CLI commands ("VPN CLI Commands" on page 159).16 May 2017 First release of this document
Important Information
Remote Access VPN Administration Guide R80.10 | 4SmartConsole Toolbars
For a guided tour of SmartConsole, click What's New in the left bottom corner of SmartConsole.Global Toolbar (top left of SmartConsole)
Description and Keyboard Shortcut
The main SmartConsole Menu
The Objects menu.
Also leads to the Object Explorer Ctrl+E
Install policy on managed gateways
Ctrl+Shift+Enter
Navigation Toolbar (left side of SmartConsole)
Description and Keyboard Shortcut
Gateways & Servers configuration view
Ctrl+1
Security Policies Access Control view
Security Policies Threat Prevention view
Ctrl+2
Logs & Monitor view
Ctrl+3
Manage & Settings view - review and configure the Security ManagementServer settings
Ctrl+4
Command Line Interface Button (left bottom corner of SmartConsole)Description and Keyboard Shortcut
Open a command line interface for management scripting and API F9 What's New Button (left bottom corner of SmartConsole)Description and Keyboard Shortcut
Open a tour of the SmartConsole
Important Information
Remote Access VPN Administration Guide R80.10 | 5 Objects and Validations Tabs (right side of SmartConsole)Description
Objects Manage security and network objects
Validations Validation warnings and errors
System Information Area (bottom of SmartConsole)
Description
Task List Management activities, such as policy installation tasks Server Details The IP address of the Security Management ServerConnected
Users The administrators that are connected to the Security Management ServerContents
Important Information ................................................................................................... 3
SmartConsole Toolbars ............................................................................................ 4
Check Point VPN.......................................................................................................... 12
IPsec VPN ................................................................................................................ 12
Remote Access VPN ................................................................................................ 12
VPN Connectivity Modes ................................................................................................ 12
Sample Remote Access VPN Workflow
.......................................................................... 13VPN Components .................................................................................................... 14
Understanding the Terminology ............................................................................. 14
Establishing a Connection between a Remote User and a Security Gateway .......... 14Getting Started with Remote Access ........................................................................... 16
Overview of the Remote Access Workflow .............................................................. 16
Basic Gateway Configuration .................................................................................. 16
Including Users in the Remote Access Community ................................................. 17 Configuring User Authentication ............................................................................. 18
Configuring VPN Access Rules for Remote Access ................................................. 18Deploying Remote Access Clients
........................................................................... 19Check Point Remote Access Solutions ........................................................................ 20
Secure Remote Access
............................................................................................ 20Types of Solutions ................................................................................................... 20
Client-Based vs. Clientless ............................................................................................ 20
Secure Connectivity and Endpoint Security.................................................................... 21
Remote Access Solution Comparison ..................................................................... 21
Summary of Remote Access Options
...................................................................... 24SSL Network Extender .................................................................................................. 24
Capsule Workspace for iOS ........................................................................................... 24
Capsule Workspace for Android .................................................................................... 24
Capsule Connect for iOS ................................................................................................ 25
Capsule VPN for Android
............................................................................................... 25Check Point VPN Plugin for Windows 8.1 ....................................................................... 25
Check Point Capsule VPN for Windows 10 ..................................................................... 25
Check Point Mobile for Windows ................................................................................... 25
Endpoint Security VPN ................................................................................................... 26
Endpoint Security VPN for Mac ...................................................................................... 26
Endpoint Security Suite ................................................................................................. 26
SecuRemote .................................................................................................................. 27
Configuring Policy
for Remote Access VPN ................................................................ 28Configuring Remote Access Policy .......................................................................... 28
Creating and Configuring the Security Gateway...................................................... 28
Defining a Remote Acce
ss Community .................................................................... 28Defining Access Control Rules ................................................................................ 29
Access Roles for Remote Access ............................................................................ 29
Creating Access Roles for Remote Access and VPN Clients .......................................... 29
Policy Definition for Remote Access ....................................................................... 30
Modifying Encryption Properties for Remote Access VPN ...................................... 30Installing the Policy ................................................................................................. 31
IPsec and IKE for Remote Access ........................................................................... 31
User and Client Authentication for Remote Access .................................................... 32
Client-Security Gateway Authentication Schemes .................................................. 32Digital User Certificates ................................................................................................ 32
Pre-Shared Secret ......................................................................................................... 33
Other Authentication Methods ....................................................................................... 33
Multiple Login Options for R80.xx Gateways ........................................................... 33
Compatibility with Older Clients .................................................................................... 34
Configuring Multiple Log-in Options .............................................................................. 35
Multi-Factor Authentication with DynamicID ................................................................. 36
Internal User Database vs. External User Database
............................................... 38 Defining User and Authentication Methods in LDAP ............................................... 39Managing User Certificates
..................................................................................... 39Tracing the Status of User's Certificate ......................................................................... 40
Automatically Renewing a Users' Certificate ................................................................. 40
Revoking Certificates..................................................................................................... 40
For Internally Managed Users ....................................................................................... 40
For Users Managed in LDAP .......................................................................................... 41
Multiple Certificates per User ....................................................................................... 41
User Certificate Creation Methods when Using the ICA ................................................. 41
Creating Remote Access VPN Certificates for Users ..................................................... 41
Using Certificates Using Third Party PKI ....................................................................... 43
Using a Pre
-Shared Secret ..................................................................................... 44
NT Group/RADIUS Class Authentication Feature
.................................................... 45Granting User Access Using RADIUS Server Groups ..................................................... 45
Configuring Authentication for NT groups and RADIUS Classes .................................... 46Configuring RADIUS Objects ................................................................................... 46
Configuring RADIUS Settings for Users ......................................................................... 47
Completing RADIUS Authentication Configuration
........................................................ 48Working with RSA Hard and Soft Tokens ................................................................ 49
SecurID Authentication Devices ..................................................................................... 49
Enabling Hybrid Mode and Methods of Authentication ............................................ 49Defining User Authentication Methods in Hybrid Mode .................................................. 49
Office Mode ................................................................................................................. 51
The Need for Remote Clients to be Part of the LAN ................................................ 51
Office Mode ............................................................................................................. 52
How Office Mode Works .......................................................................................... 52
A Closer Look ................................................................................................................ 52
Assigning IP Addresses
........................................................................................... 54IP Pool ........................................................................................................................... 54
IP Assignment Based on Source IP Address .................................................................. 54
DHCP Server .................................................................................................................. 54
RADIUS Server .............................................................................................................. 54
Office Mode and Static Routes in a Non
-flat Network .................................................... 55IP Address Lease duration ...................................................................................... 55
Using Name Resolution
- WINS and DNS ................................................................ 55Anti-Spoofing .......................................................................................................... 55
Using Office Mode with Multiple External Interfaces .............................................. 56
Office Mode Per Site ................................................................................................ 56
Enabling IP Address per User ................................................................................. 57
DHCP Server .................................................................................................................. 57
ipassignment.conf File .................................................................................................. 58
Sample ipassignment.conf File ..................................................................................... 58
Office Mode Considerations
59IP Pool versus DHCP...................................................................................................... 59
Routing Table Modifications .......................................................................................... 59
Using the Multiple External Interfaces Feature ............................................................. 59
Configuring Office Mode .......................................................................................... 59
IP Pool Configuration ..................................................................................................... 59
Configuring IP Assignment Based on Source IP Address ............................................... 61
Office Mode through the ipassignment.conf File............................................................ 61
Subnet masks and Office Mode Addresses .................................................................... 62
Checking the Syntax ...................................................................................................... 62
DHCP Configuration
....................................................................................................... 63
Office Mode - Using a RADIUS Server ............................................................................ 64
Use First Office Mode IP ................................................................................................ 64
Desktop Security ......................................................................................................... 65
The Need for Desktop Security ............................................................................... 65
Desktop Security Solution ....................................................................................... 65
The Desktop Security Policy .......................................................................................... 66
quotesdbs_dbs20.pdfusesText_26[PDF] foxtel adults only channel
[PDF] foxtel adults only pin code
[PDF] foxtel free movies 2019
[PDF] foxtel iq3 rear connections
[PDF] foxtel movie guide
[PDF] foxtel movies
[PDF] foxtel music channels
[PDF] foxtel packages optus
[PDF] foxwoods outlets
[PDF] foyer george williams
[PDF] foyer le carilan geneva
[PDF] foyer myrjana
[PDF] foyers geneva
[PDF] fpca 2020
