 Google Hacking for Penetration Testers
Google Hacking for Penetration Testers
…multiple live security camera views… …and historical records of recorded video feeds. Even doofus hackers know how to use default passwords to get… Thanks to.
 FREE-FALL: HACKING TESLA FROM WIRELESS TO CAN BUS
FREE-FALL: HACKING TESLA FROM WIRELESS TO CAN BUS
A Wi-Fi SSID Tesla Service
 Certified Blackhat- Methodlogy to Unethical hacking (1)
Certified Blackhat- Methodlogy to Unethical hacking (1)
know the target systems is the first process in ethical hacking. Social such as an e-mail attachment or pdf and has the ability to make its. “signature ...
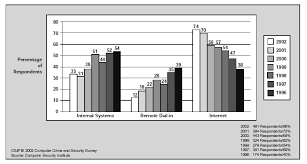 Black Hat
Black Hat
to learn a certain number of MAC addresses per port. Upon detection of an invalid MAC the switch can be configured to block only the offending MAC or just
 Business Hall
Business Hall
https://encrypted-tbn2.gstatic.com/images?q=tbn:ANd9GcQhgBfCt--hmvC3xfEEDxTdL-6toGD7lwuJr7NqpOiFLnKtCbBkPAKDYYrR
 Rocking the pocket book: Hacking chemical plants for competition
Rocking the pocket book: Hacking chemical plants for competition
pdf. [34] Jason Larsen. “Miniaturization”. In: Black Hat USA (2014). http://http://blackhat.
 Hacking VoIP Exposed
Hacking VoIP Exposed
SIP extensions are useful to an attacker to know for performing Application specific attacks (hijacking voicemail brute forcing
 A Pictures Worth - Digital Image Analysis and Forensics Version 2
A Pictures Worth - Digital Image Analysis and Forensics Version 2
pdf. Page 23. N. Krawetz. A Picture's Worth... 23 of 43. Copyright 2007-2008 Hacker Factor Solutions presented at Black Hat Briefings DC 2008. Figure 23 ...
 Black Hat Go
Black Hat Go
Jun 27 2019 isn't Learning to Program Elegantly with Go—this is Black. Hat Go. WHY USE GO FOR HACKING? Prior to Go
 Making money on the Web the black hat way
Making money on the Web the black hat way
Contributing author of "Hacking. Exposed: Web Applications." 2. Page 9. © 2008 WhiteHat Security Inc. WhiteHat
 Becoming a Black Hat Hacker
Becoming a Black Hat Hacker
There are many ways you can learn computer systems programming
 Google Hacking for Penetration Testers
Google Hacking for Penetration Testers
…multiple live security camera views… …and historical records of recorded video feeds. Even doofus hackers know how to use default passwords to get… Thanks to.
 Black Hat Hacker White Hat Hacker Gray Hat Hacker
Black Hat Hacker White Hat Hacker Gray Hat Hacker
Black-hat Hackers are also known as an Unethical Hacker or a Security Cracker. These people hack the system illegally to steal money or to achieve their own
 Untitled
Untitled
“Gray Hat Hacking Second Edition takes a very practical and applied approach to learning how to attack computer systems. The authors are past Black Hat
 Top Ten Web Attacks
Top Ten Web Attacks
Net-Square. BlackHat Asia 2002 Singapore Increased —web hacking“ activity. • Worms on the web. ... OS vendors learning from past mistakes (?).
 Hacking a Professional Drone
Hacking a Professional Drone
The goal of this talk is to give insights into the security of. Unmanned Aerial Vehicles (UAVs) and to show that professional.
 Blackhat-Hacking.pdf
Blackhat-Hacking.pdf
Blackhat Hacking. How to hack and not get caught. Brady Bloxham. Silent Break Security Know your network. – That means monitor the traffic.
 $atellite Hacking for Fun & Pr0fit!
$atellite Hacking for Fun & Pr0fit!
Full Disclosure / White Hat! ? Freelance research / training / lecturing Hacking a Bird in The Sky. ? Old Skewl ... You've got to know how to grab it.
 Hacking Databases for Owning your Data
Hacking Databases for Owning your Data
Database vulnerabilities affect all database vendors I know it's old news but guess what? it's still a big issue
 Phishing with Super Bait
Phishing with Super Bait
WhiteHat Security is a leading provider of web application a URL the hacker can redirect any end user though Lycos directory to their fraudulent page.
[PDF] learn by doing: google docs unit 6
[PDF] learn c programming for beginners pdf
[PDF] learn c sharp tutorialspoint
[PDF] learn cbse class 9 math
[PDF] learn cisco network administration in a month of lunches
[PDF] learn cisco networking basics
[PDF] learn cisco networking pdf
[PDF] learn clojure
[PDF] learn cobol in 21 days pdf
[PDF] learn coding from scratch pdf
[PDF] learn data cleaning in r
[PDF] learn english grammar in tamil
[PDF] learn english grammar in tamil language
[PDF] learn english grammar step by step pdf
